デバッグシンボルが欠落した OpenResty/Nginx アプリケーションの分析(OpenResty XRay を使用)
このチュートリアルでは、デバッグシンボルのない OpenResty および Nginx アプリケーションを自動的に分析する方法をご紹介します。すべてのデバッグ情報がない場合でも、機械学習アルゴリズムを使用して実行可能ファイルを自動的に分析し、デバッグシンボルを再構築し、動的トレースを通じて深く包括的な分析を行うことができます。OpenResty XRay は、strip された実行可能ファイルからデバッグシンボルを生成する特別な能力を持っているため、デバッグシンボルが欠落していても、C 関数と Lua 関数のソースファイルやソースコード行に関連する情報を取得できます。
問題:アプリケーションにデバッグシンボルが欠落
OpenResty XRay が OpenResty または Nginx アプリケーションにおいて、デバッグシンボルのないプログラムを自動的に分析する方法をご紹介します。機械学習アルゴリズムを使用して実行可能ファイルを分析し、デバッグシンボルを再構築することができます。
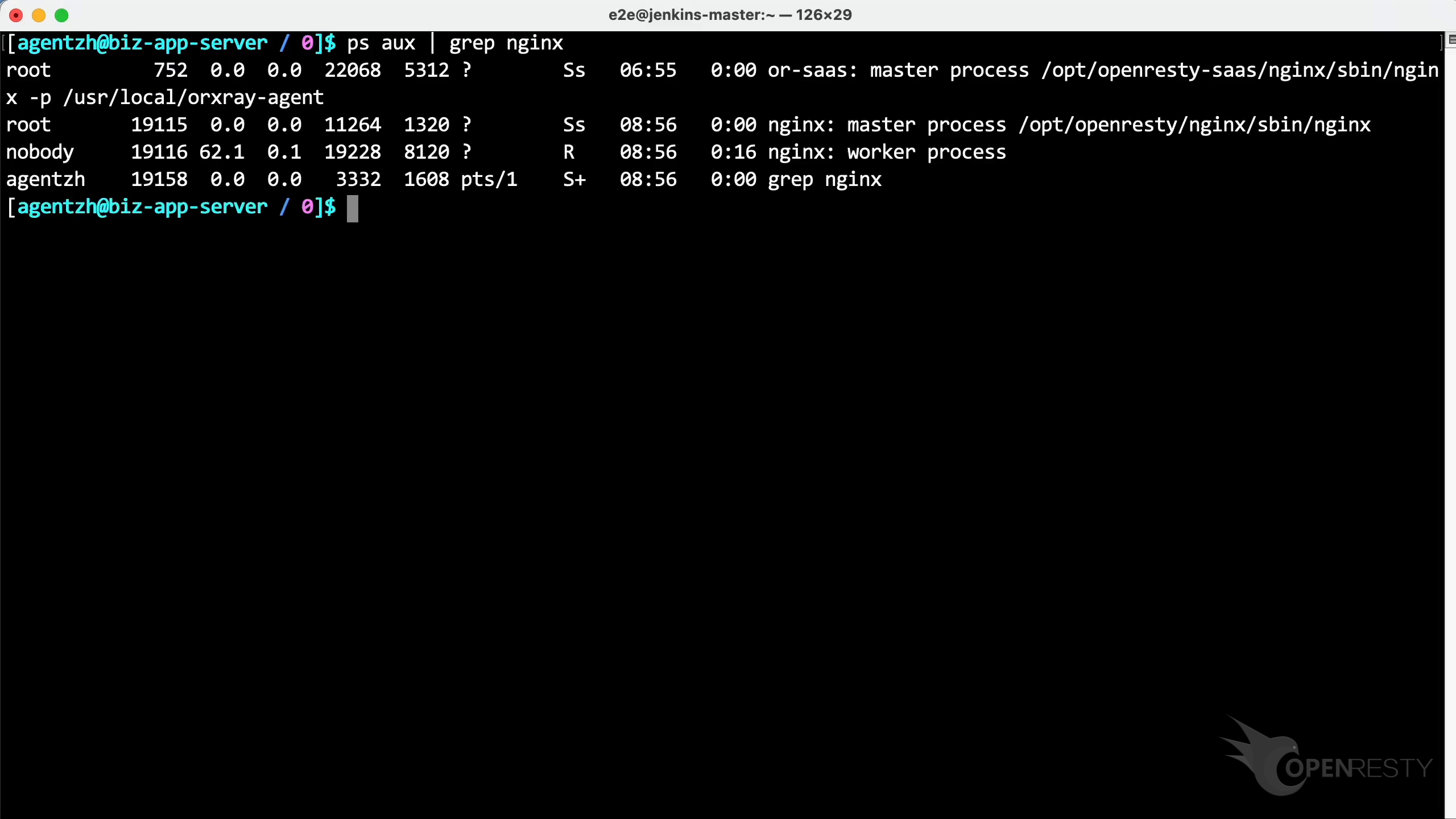
まず、ps コマンドを実行して、OpenResty または Nginx プロセスの詳細を確認しましょう。
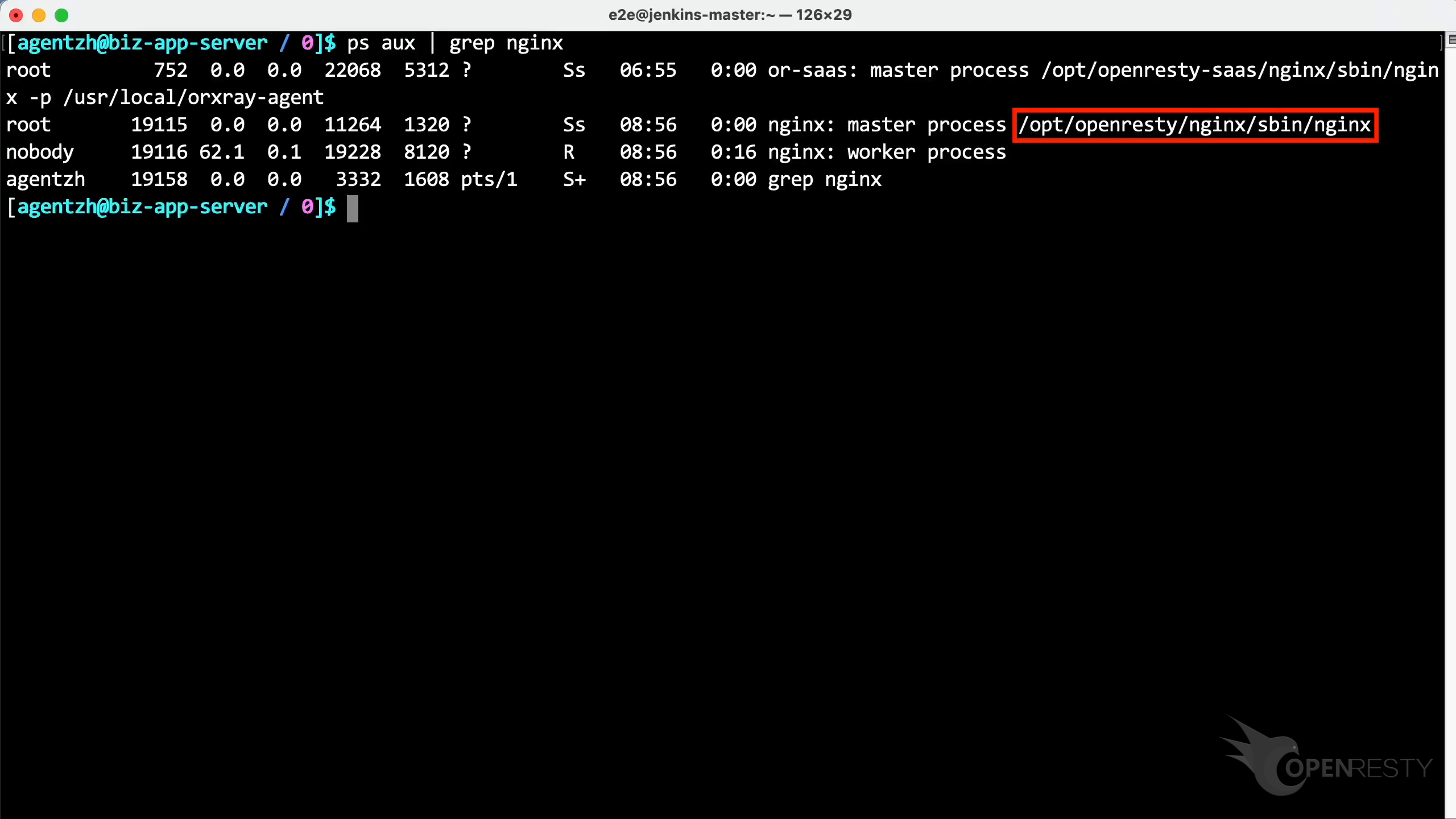
このプロセスの実行可能ファイルのパスが表示されています。この OpenResty はユーザーがソースコードからコンパイルしたものです。
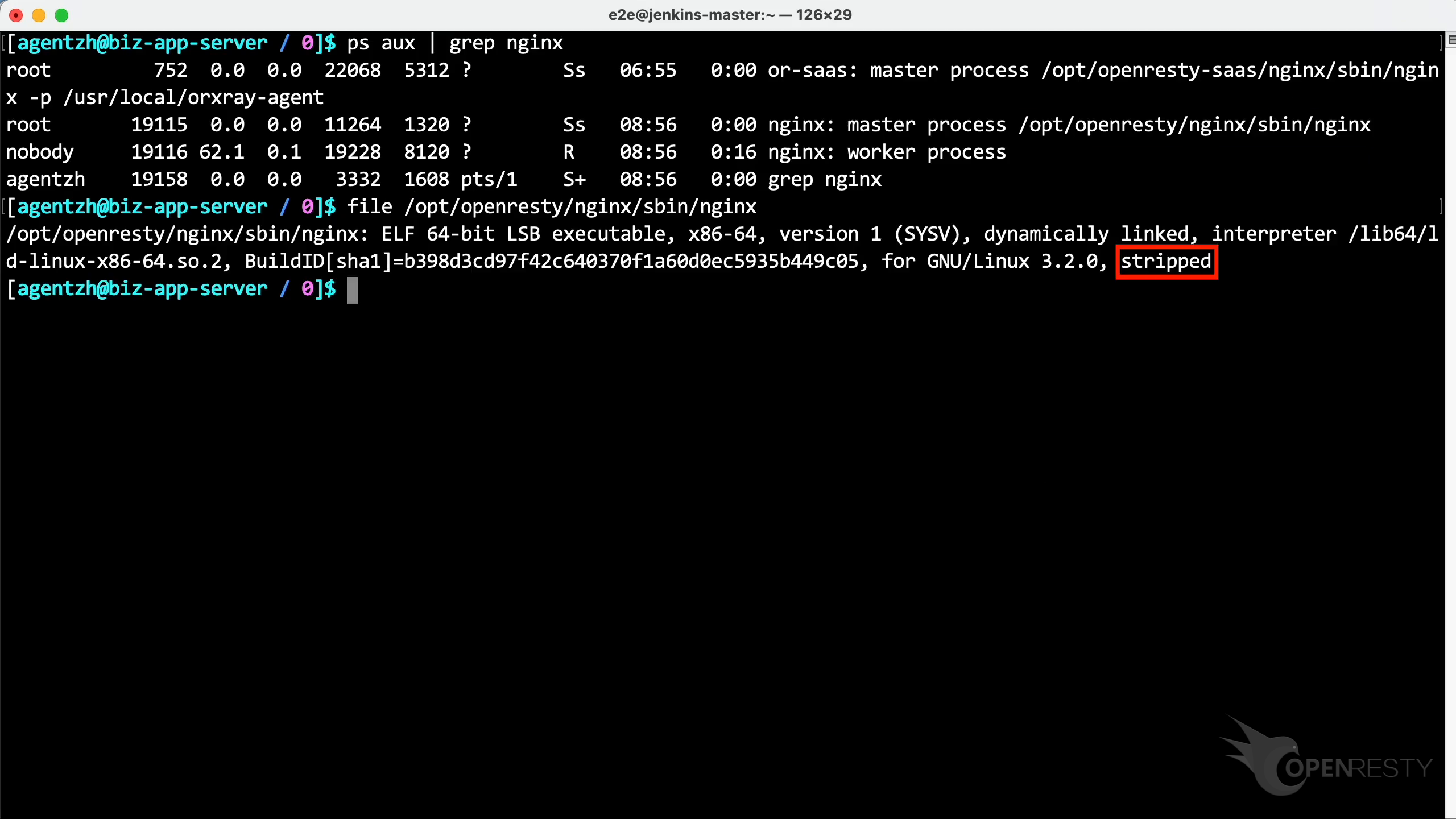
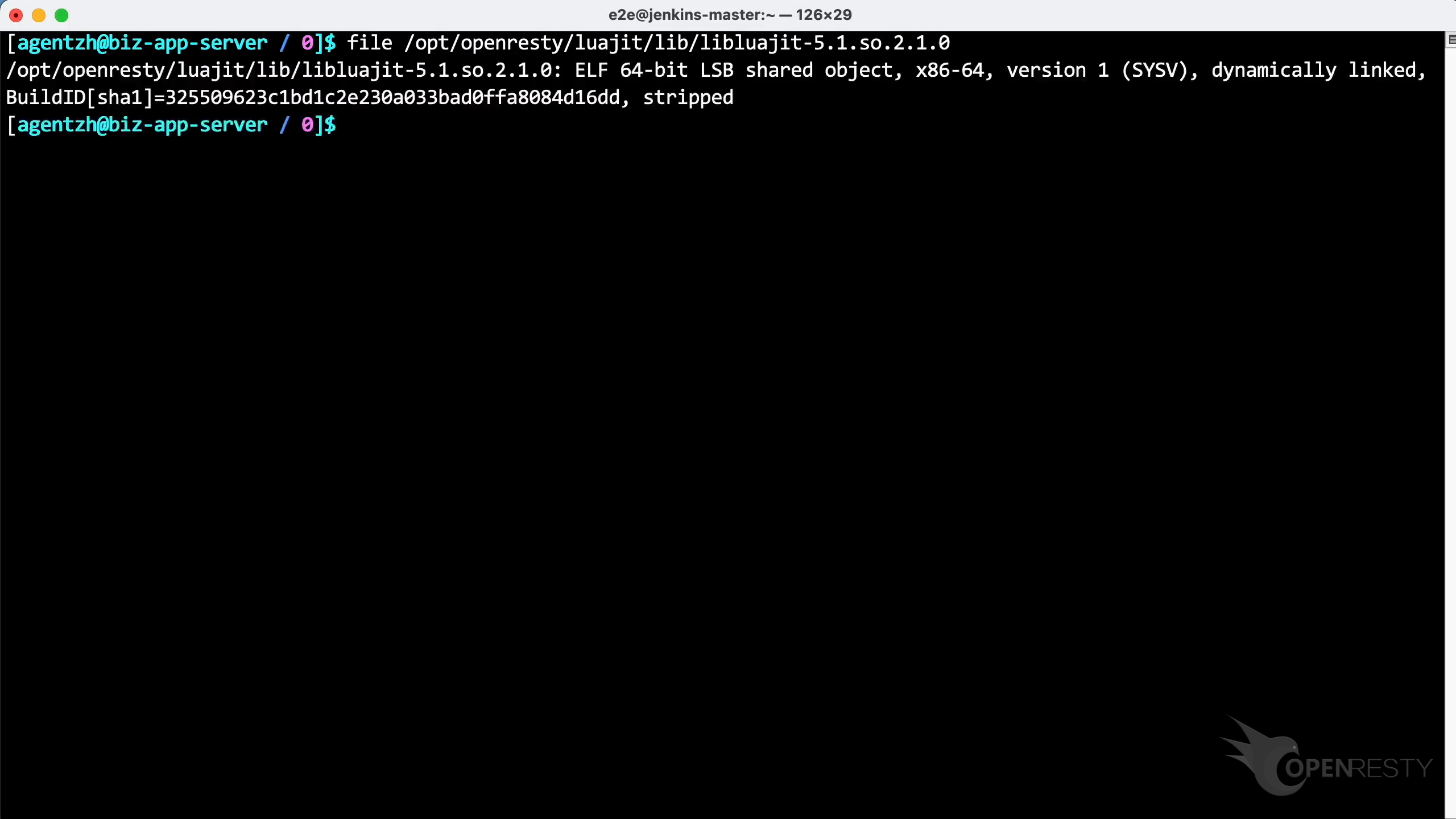
file コマンドを使用して、この実行可能ファイルを確認します。このファイルパスをコピーしてください。
ファイルが strip されており、デバッグシンボルやシンボルテーブルが一切ないことがわかります。また、このプログラムに対応するデバッグシンボルのインストールパッケージも見つかりません。
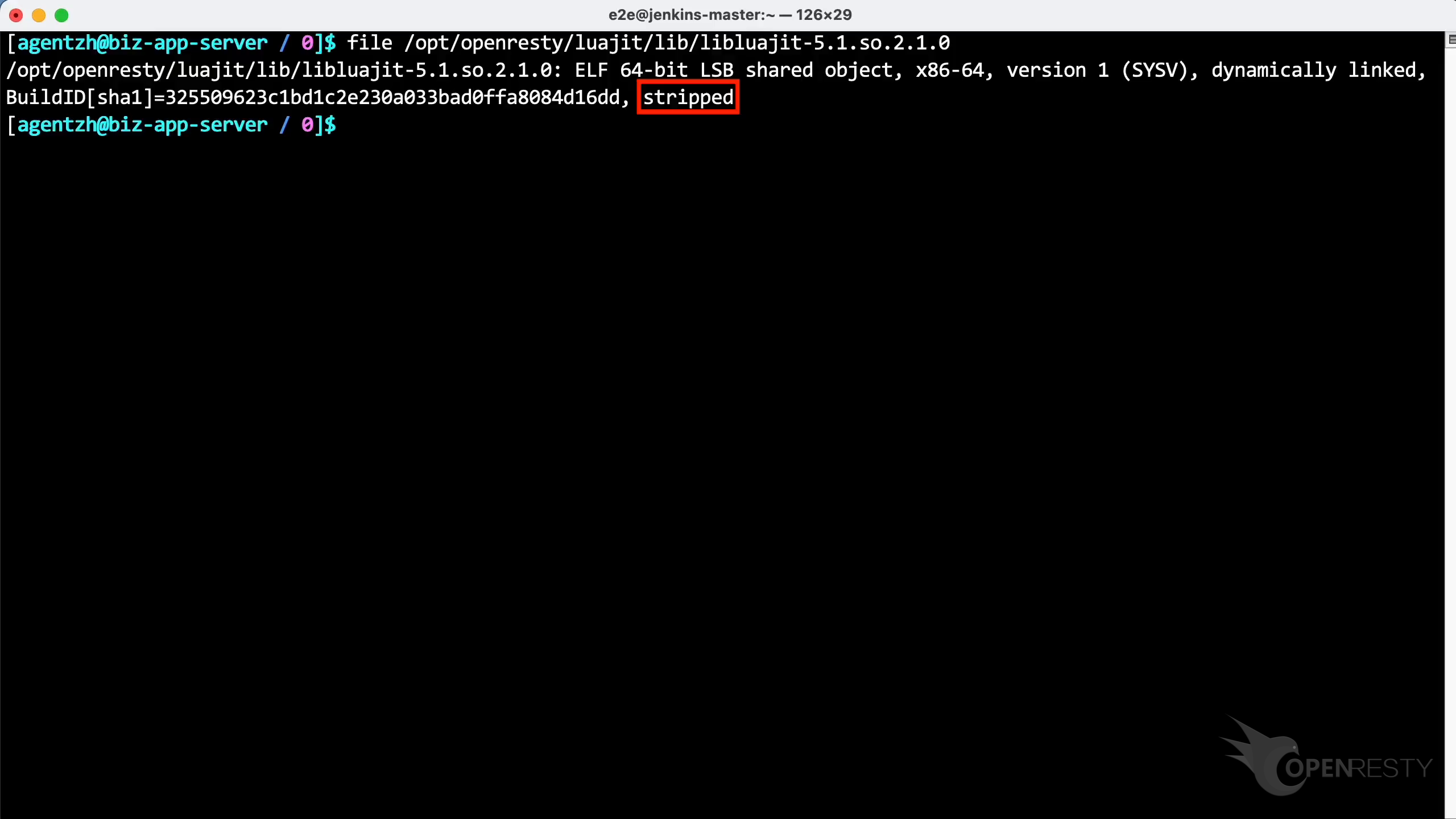
次に、file コマンドを使用して LuaJIT の動的リンクライブラリを確認します。
ここでも、LuaJIT ファイルのデバッグシンボルが欠落していることがわかります。
デバッグシンボルの自動分析と再構築
OpenResty XRay がこのような実行可能ファイルからデバッグシンボルを生成する特別な能力を持っているおかげで、動的トレースを通じて深く包括的な分析を行うことができます。
ブラウザで OpenResty XRay の Web コンソールを開きます。
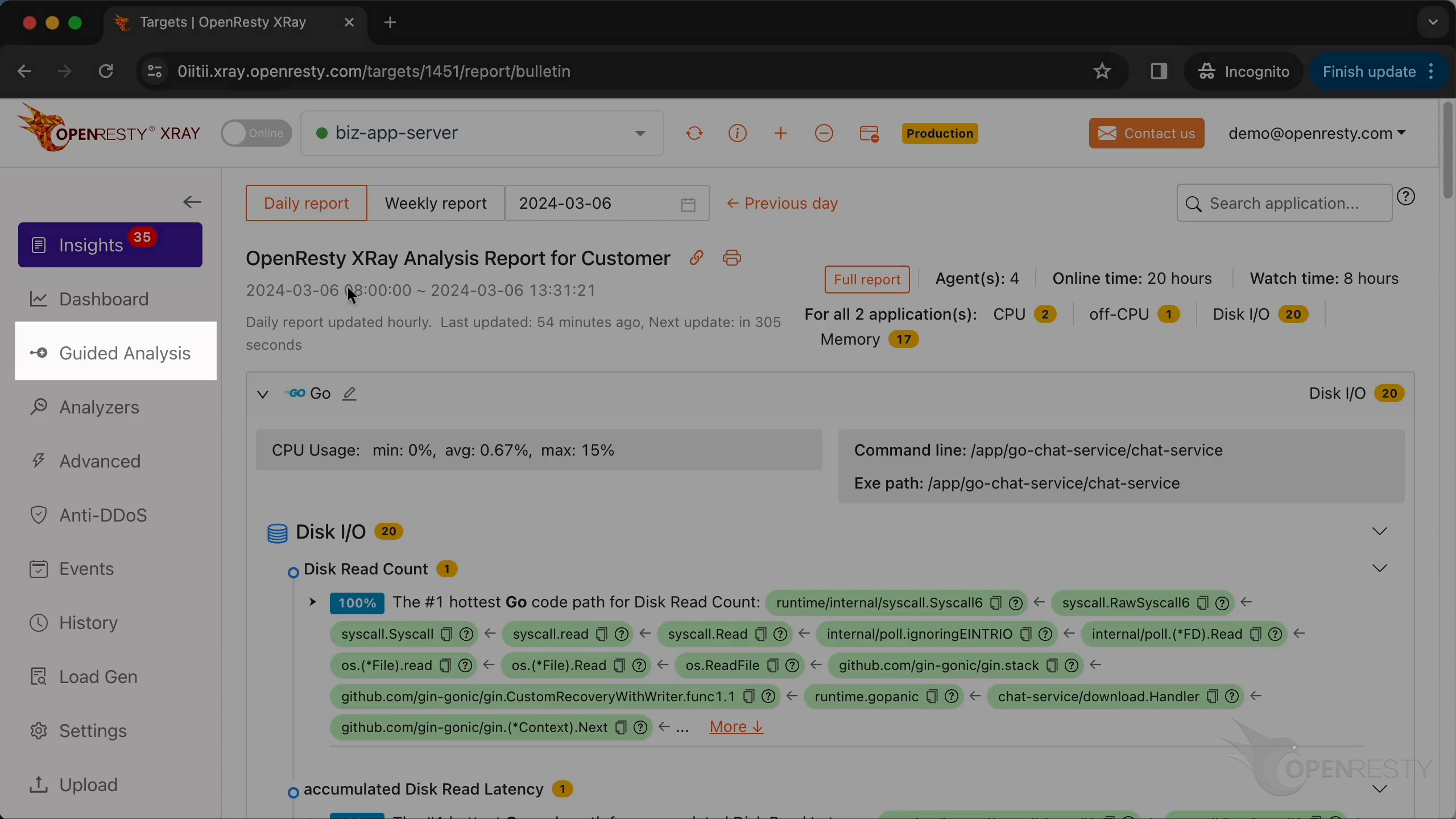
「Guided Analysis」ページに移動します。
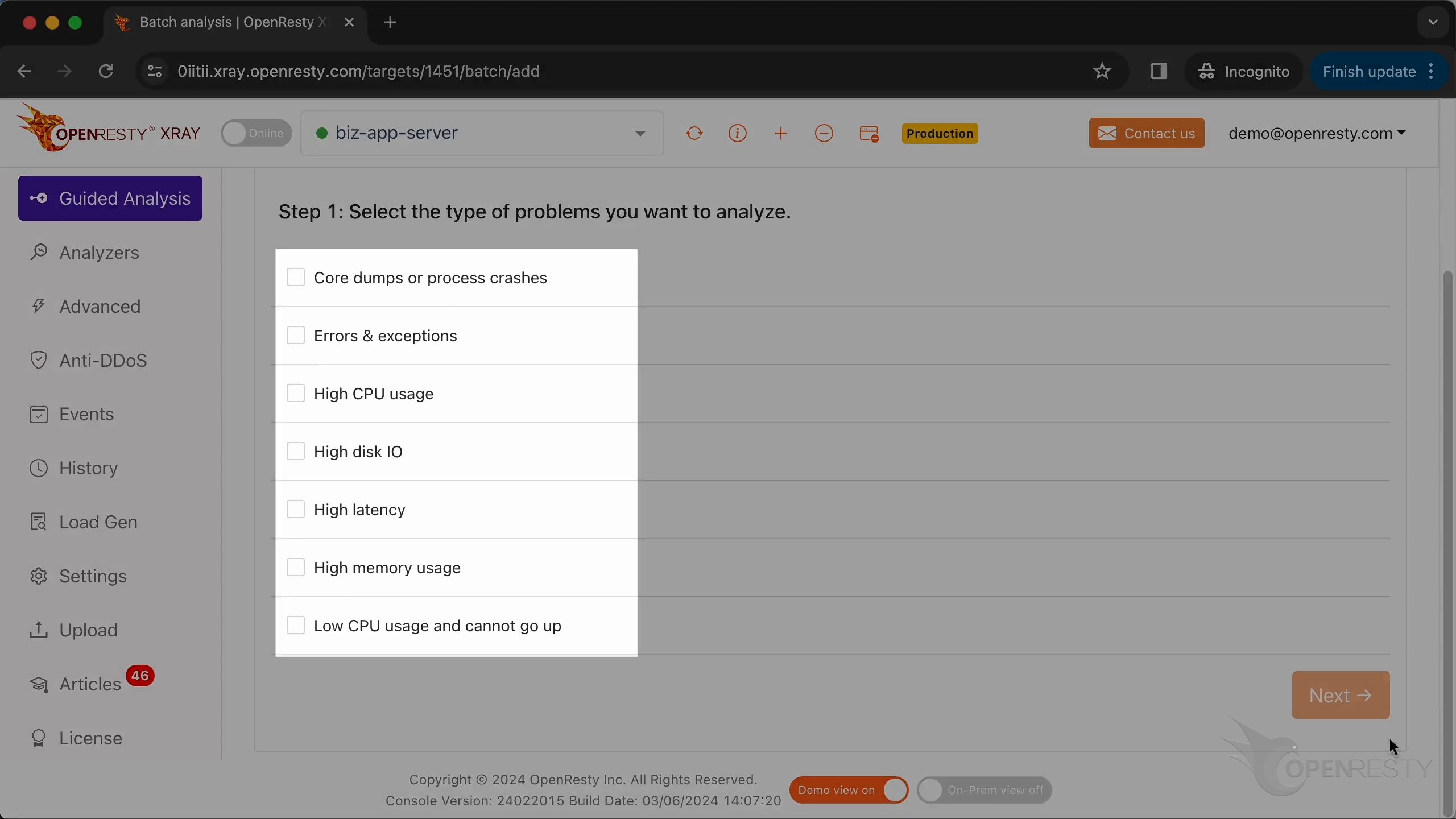
ここでは、システムが分析できる様々な種類の問題が表示されています。
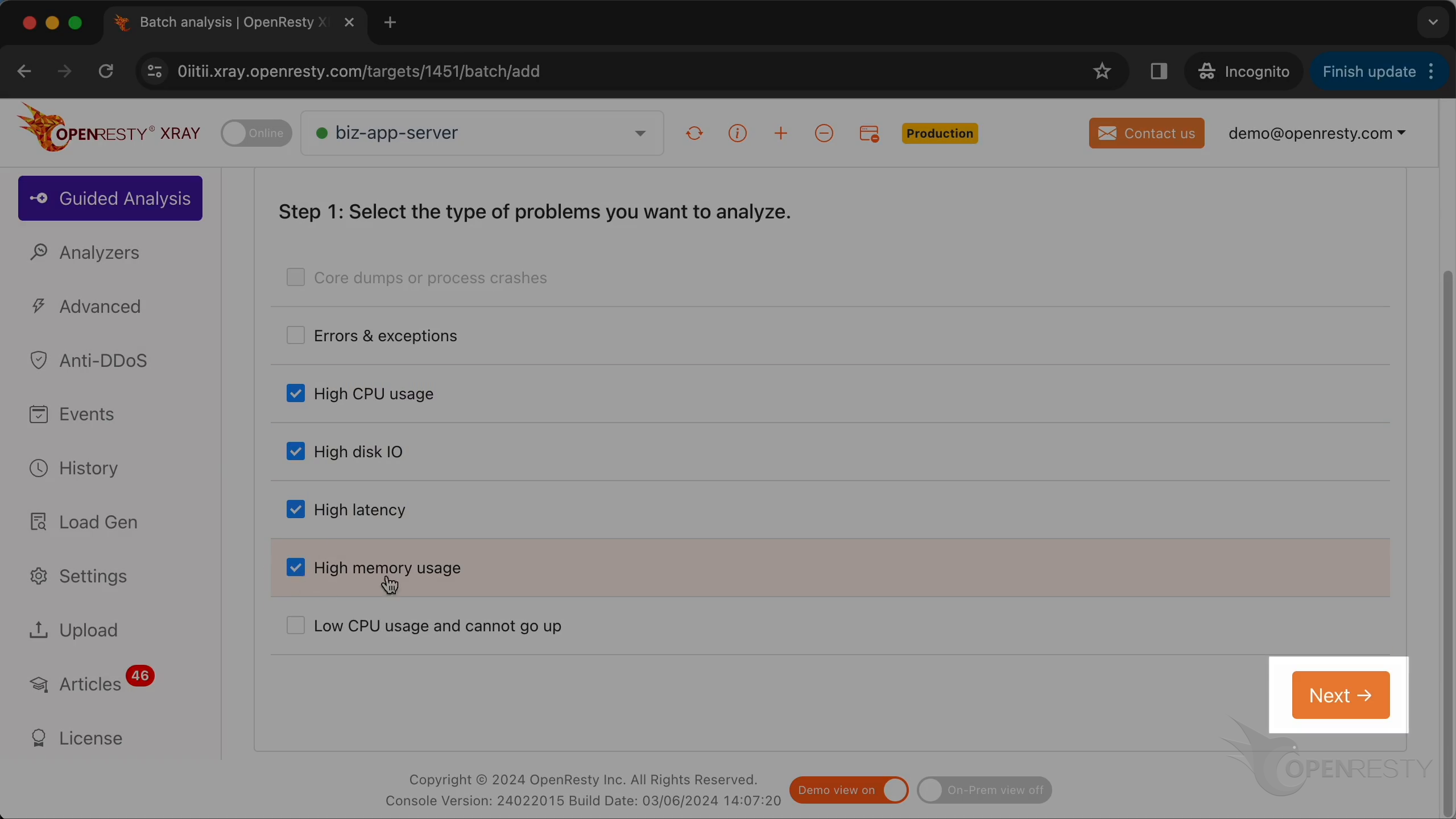
これら 4 種類の問題を選択します。
「Next」をクリックします。
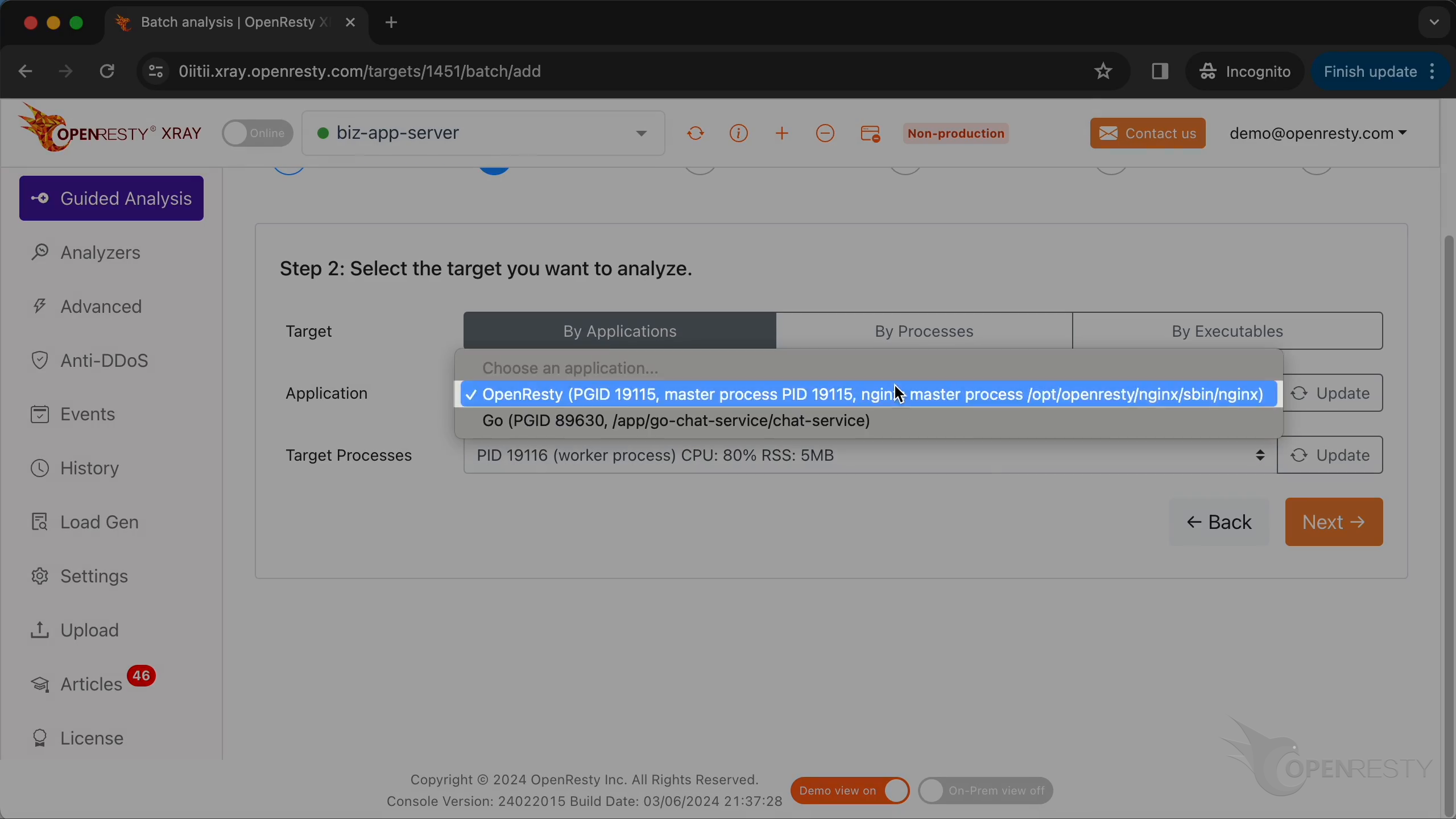
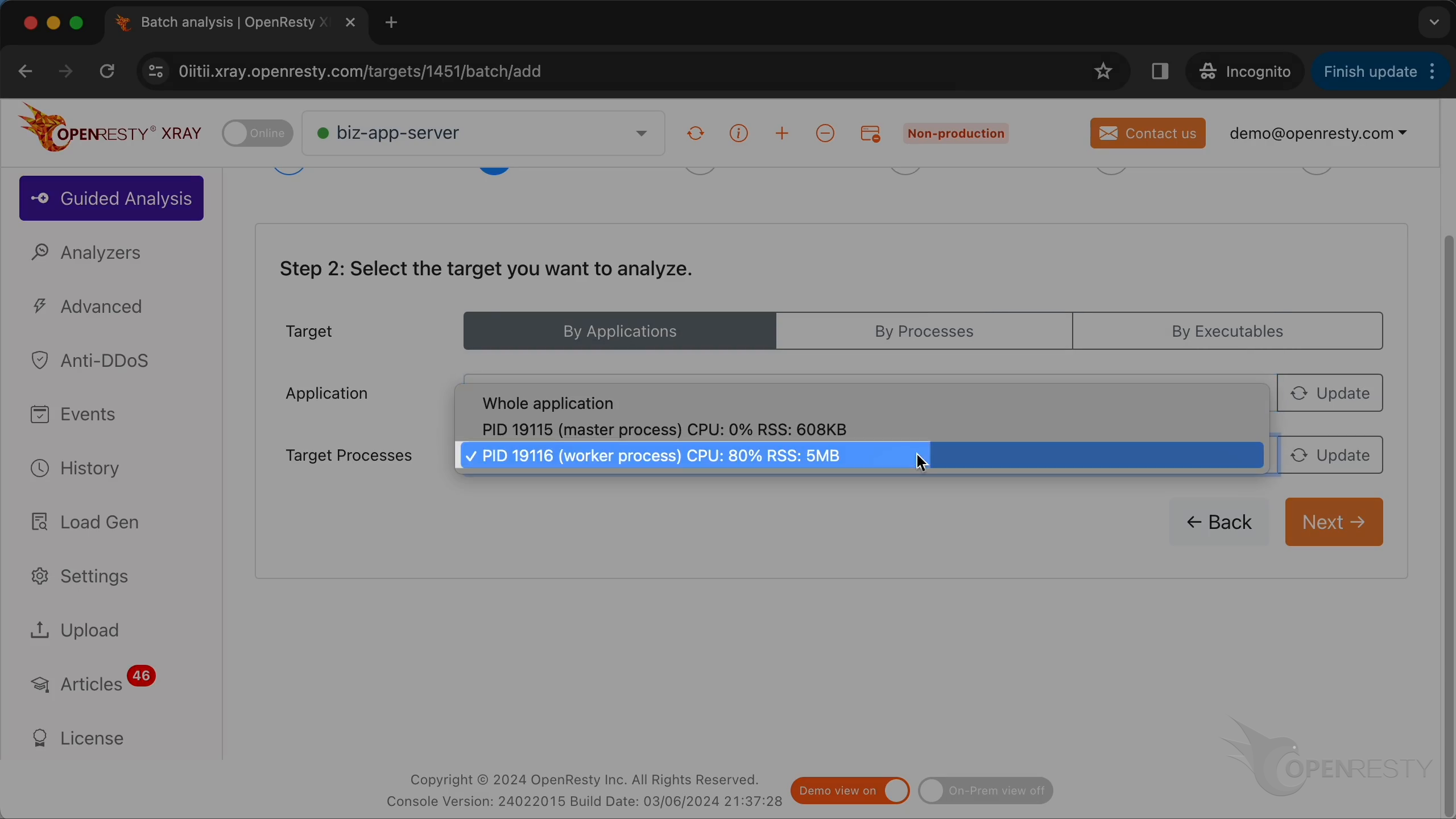
先ほどの OpenResty アプリケーションを選択します。
worker プロセスを選択します。
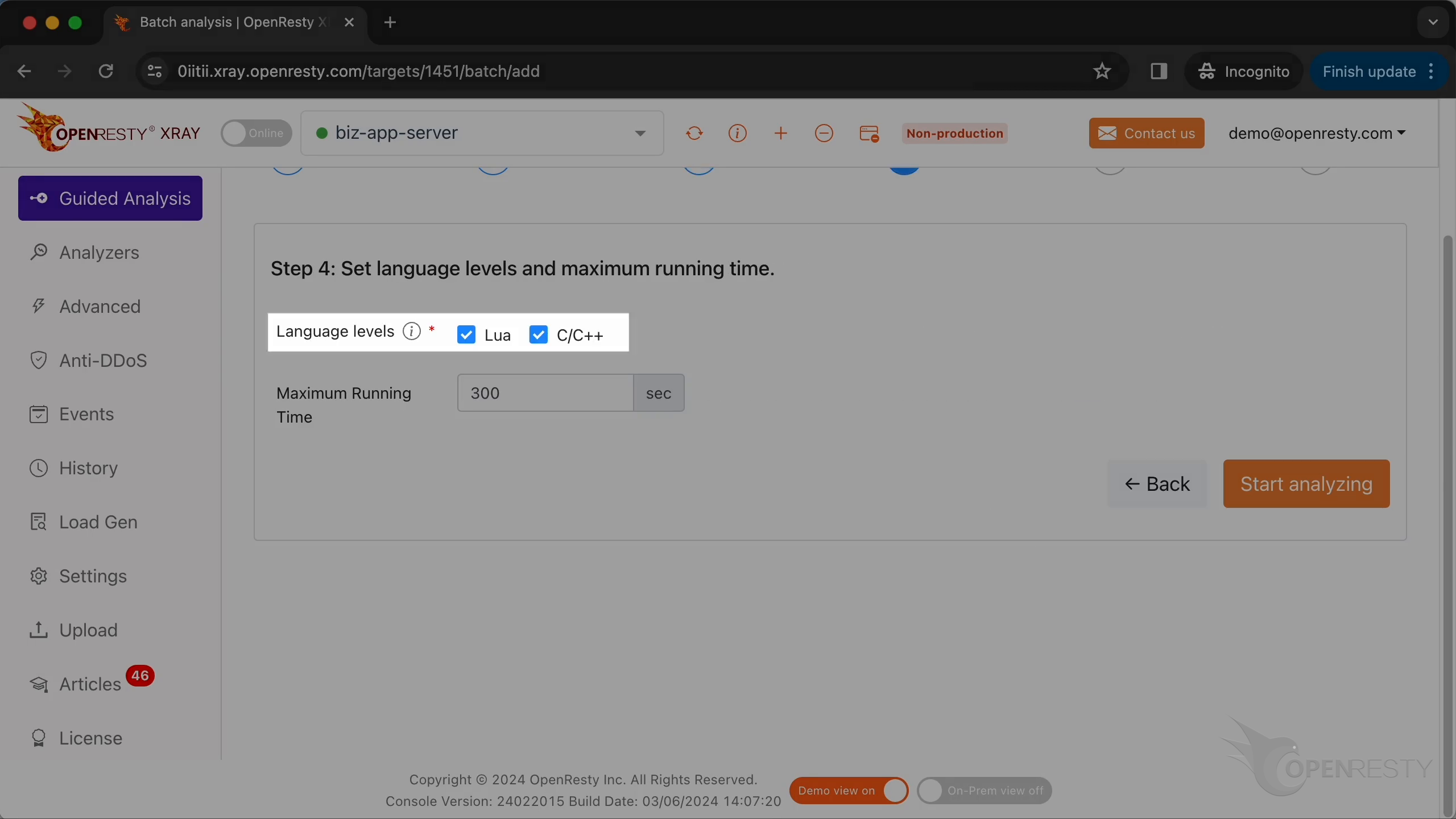
OpenResty XRay は複数の言語レベルを同時に分析できます。ここでは Lua と C/C++ の両方を選択したままにします。
分析を開始します。
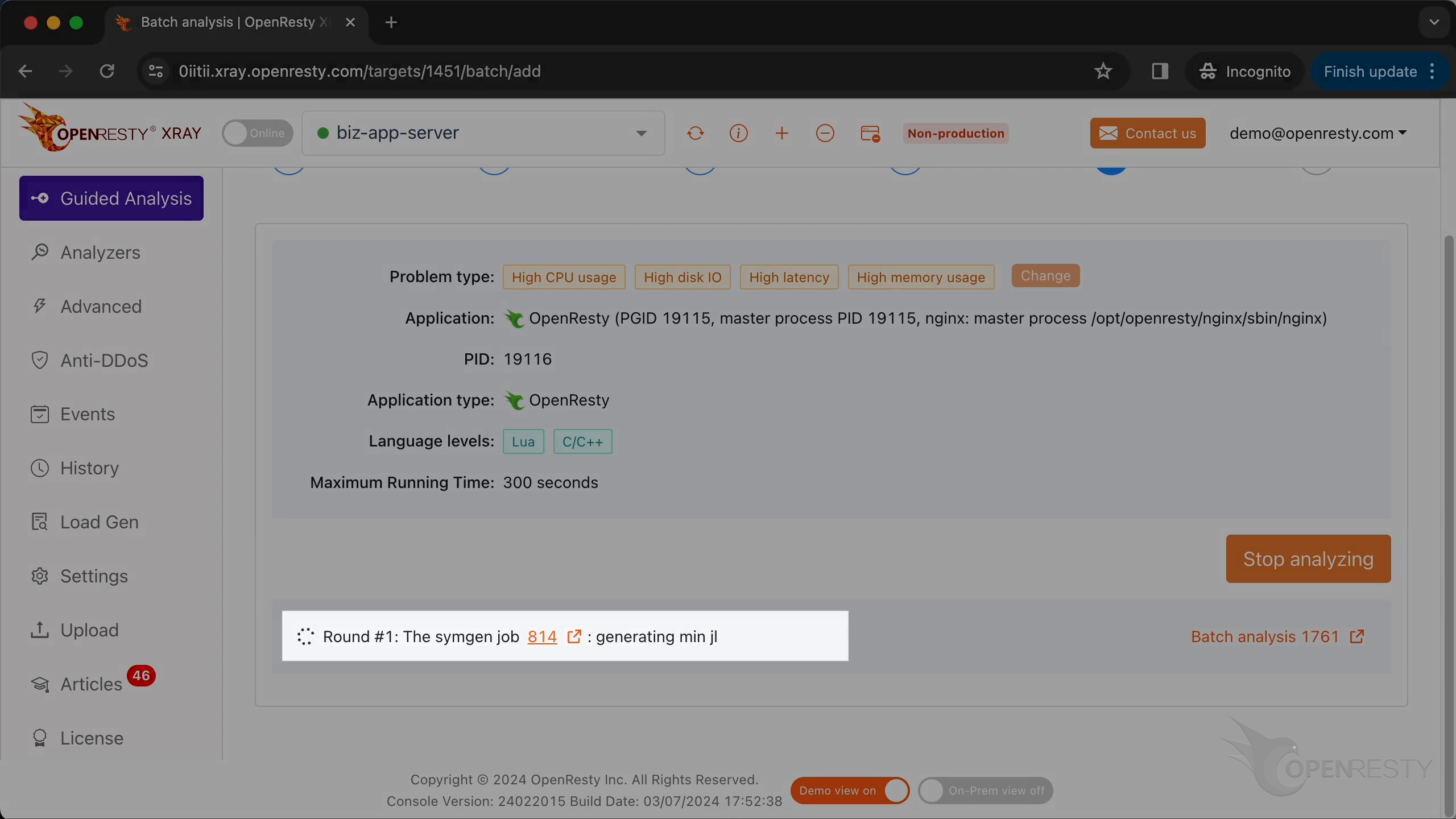
OpenResty XRay はまず、実行可能ファイルにデバッグシンボルが欠落しているかどうかをチェックし、自動的に再構築を試みます。シンボル再構築タスクが実行中です。
シンボルの再構築が成功すると、通常通りすべての関連アナライザーの実行を開始します。
分析を停止します。
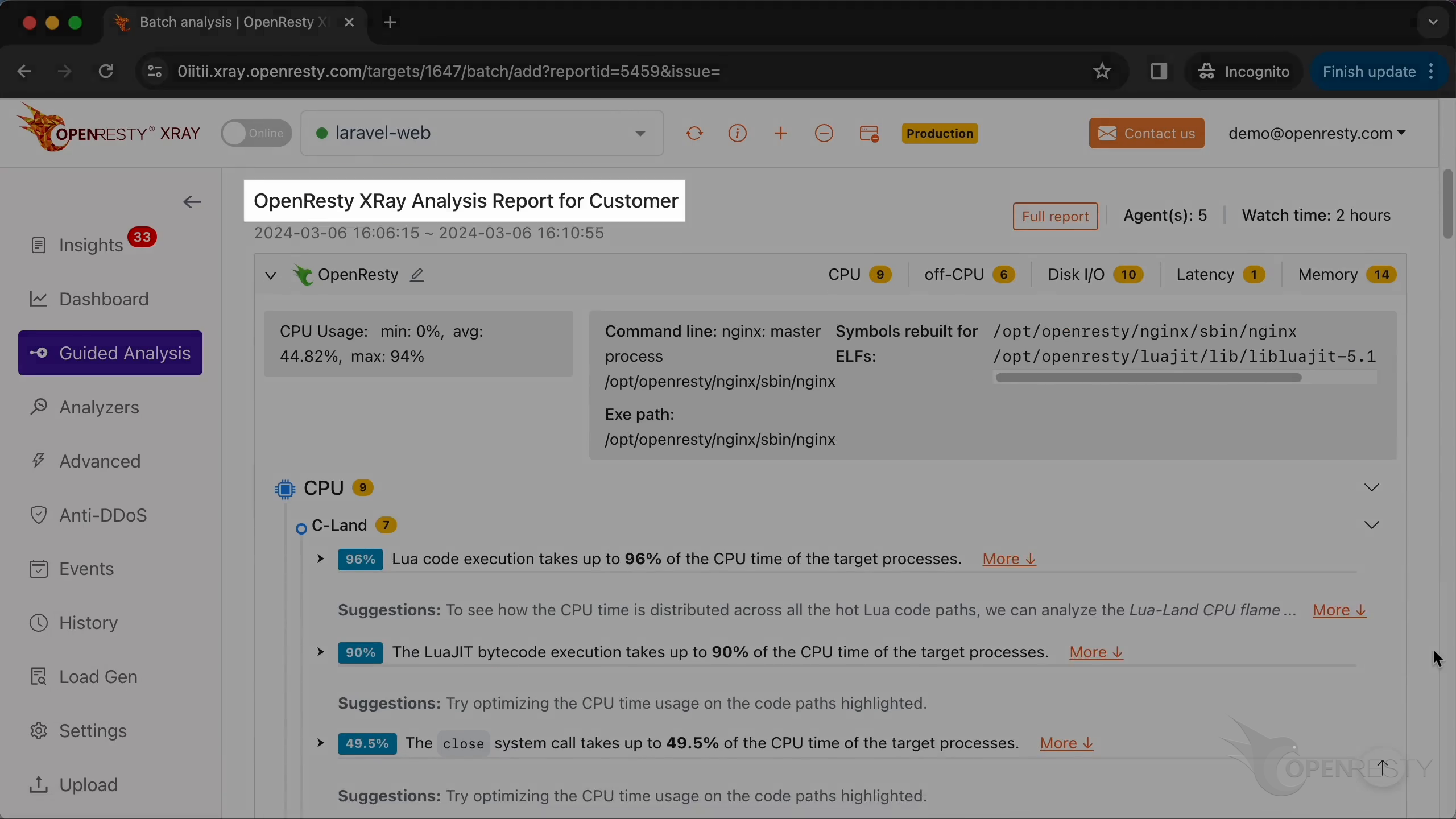
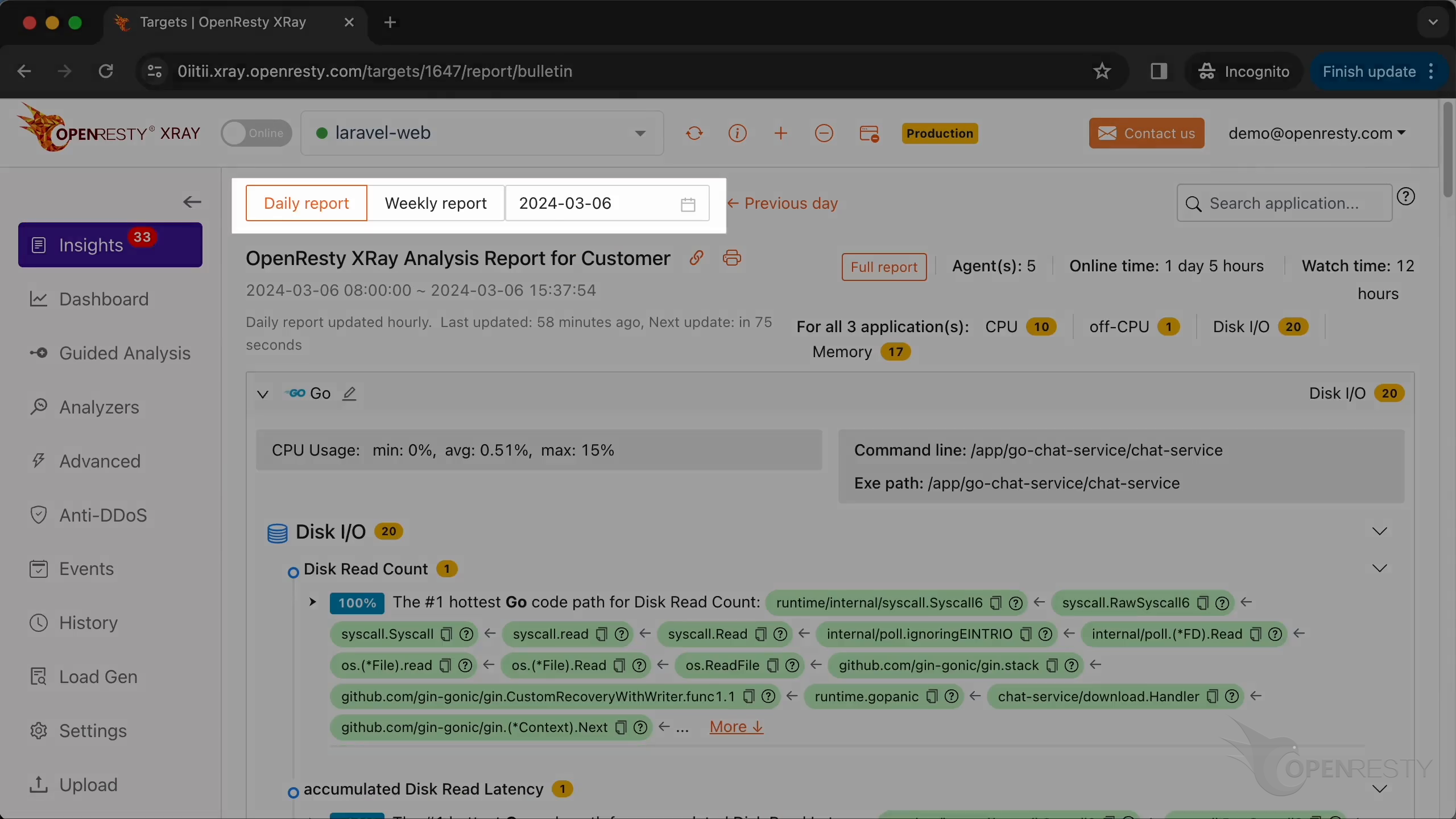
分析レポートが自動的に生成されたことがわかります。
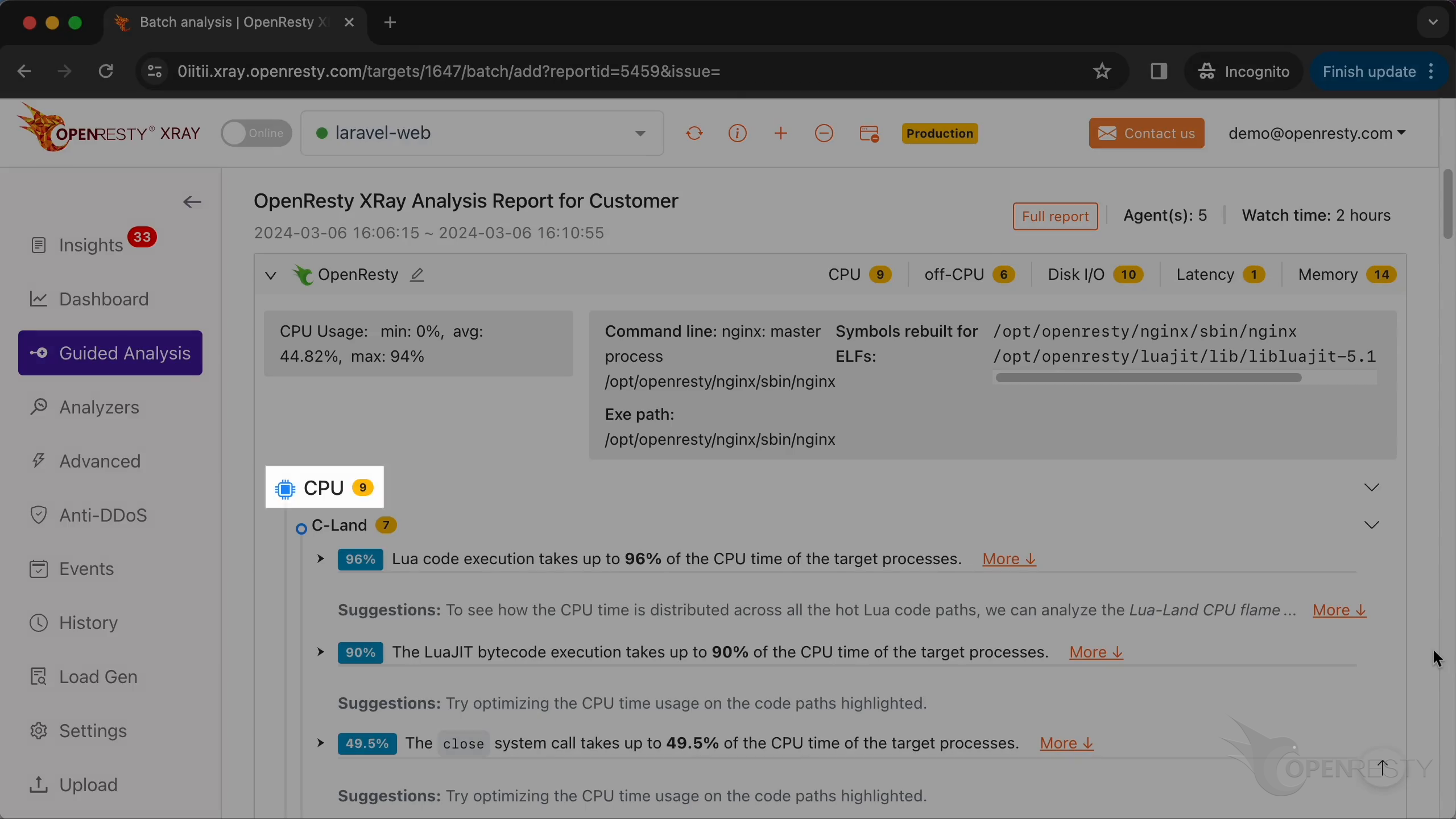
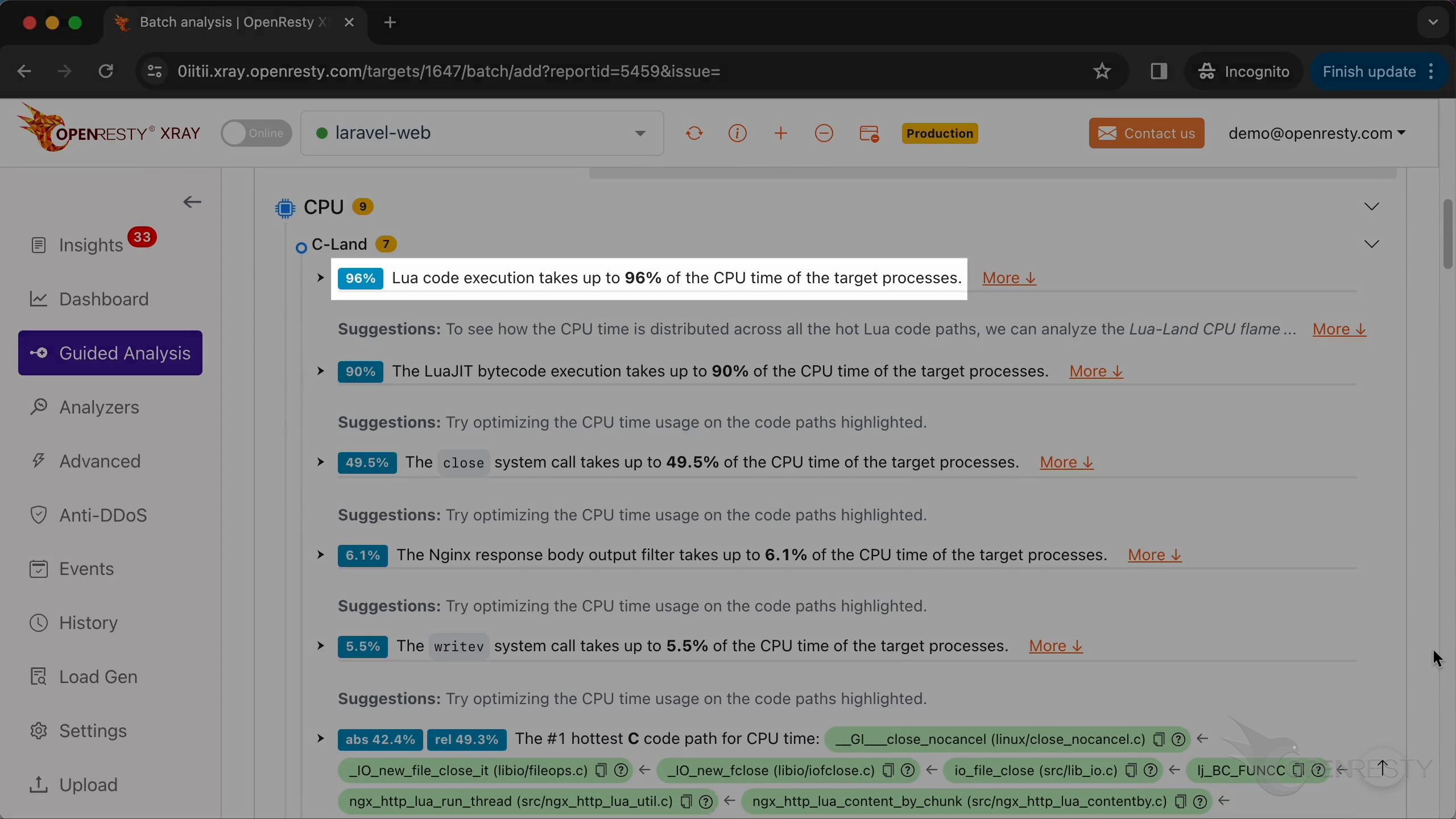
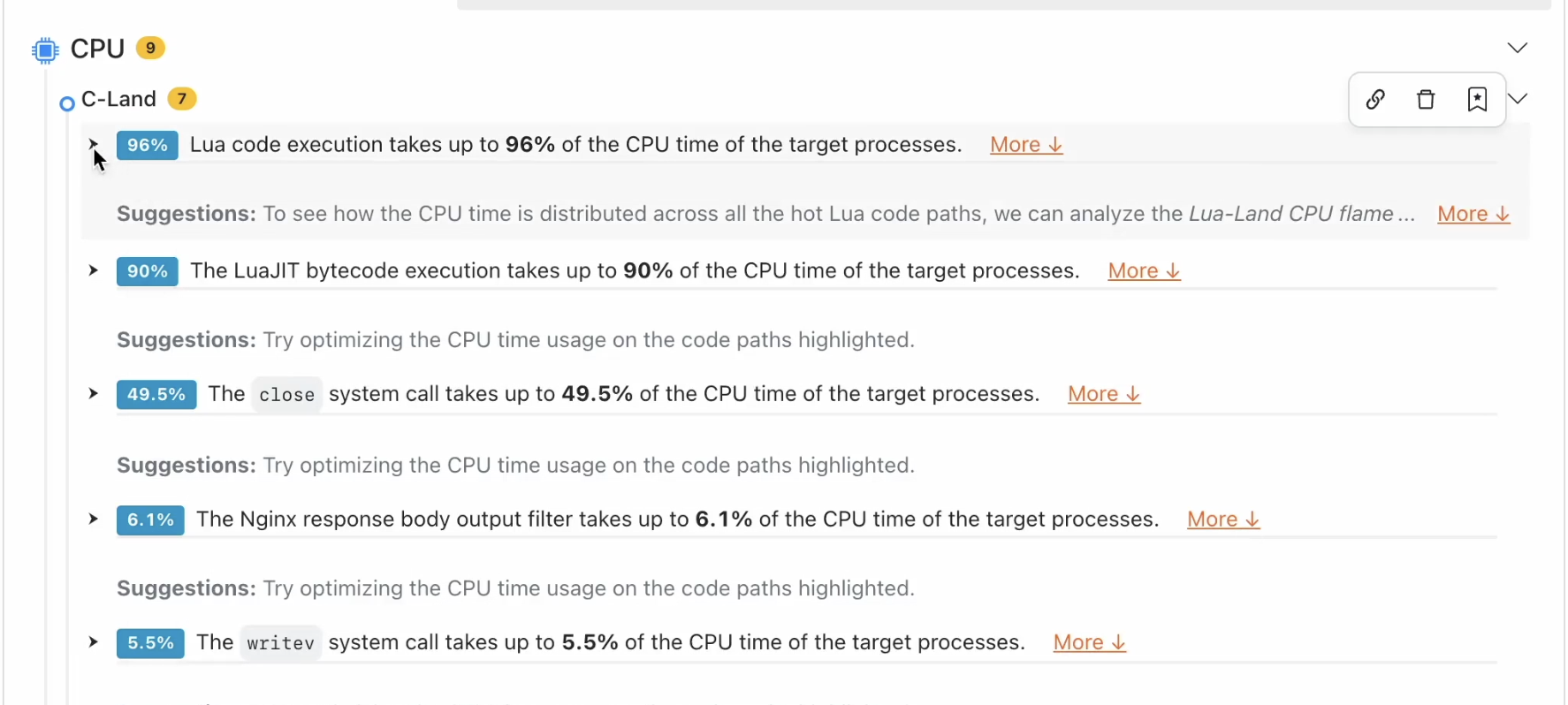
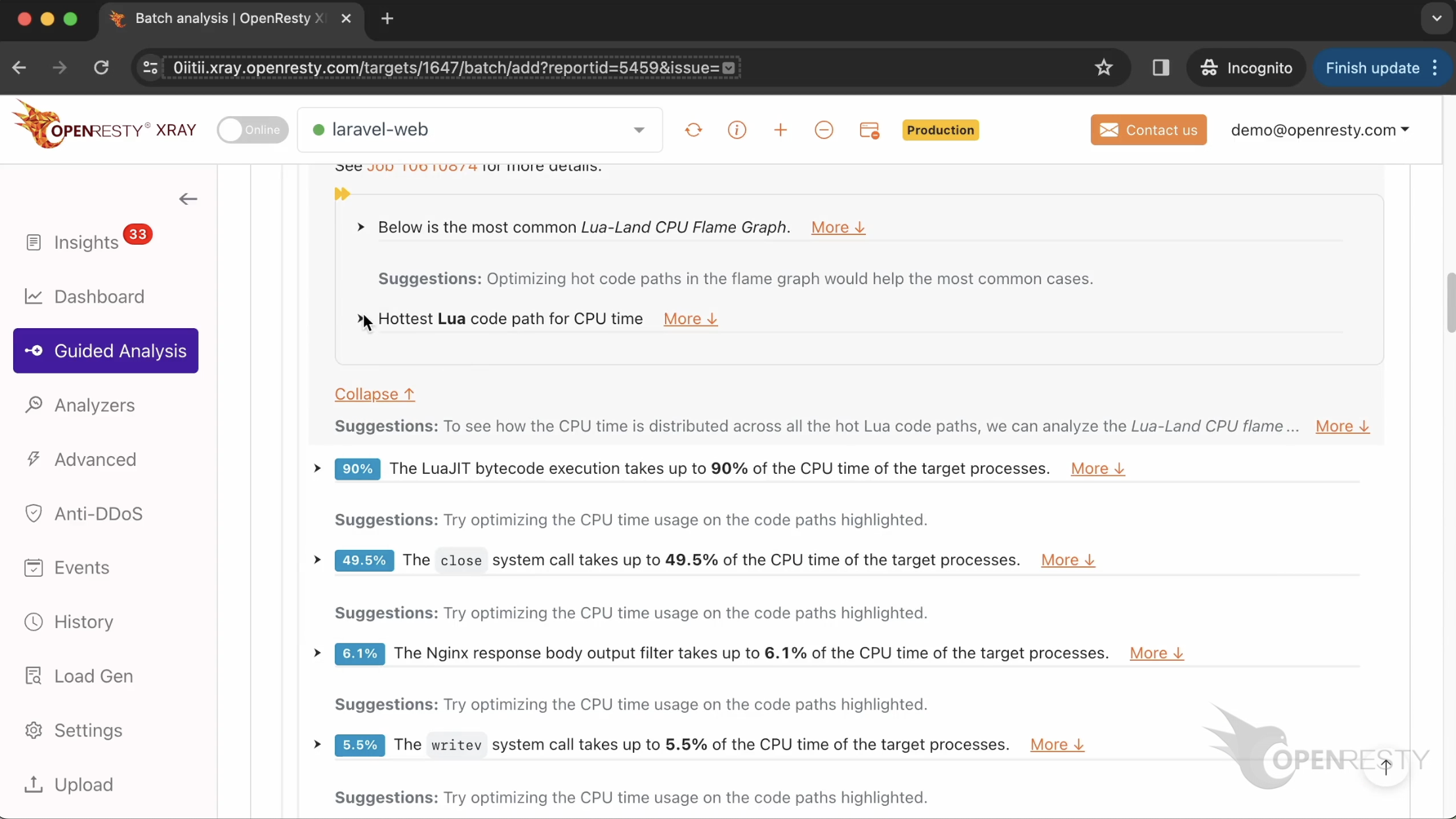
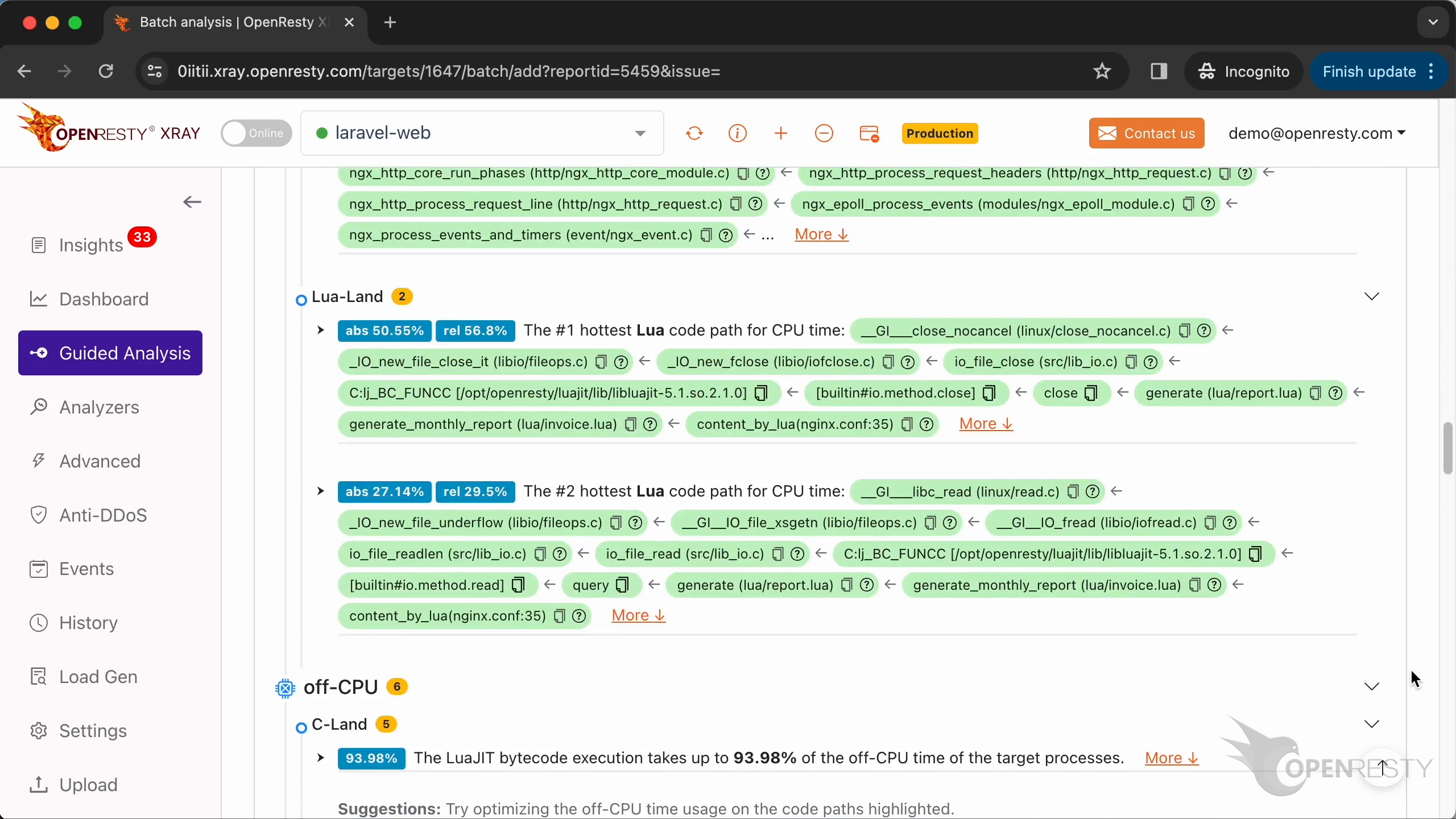
レポートの最初の部分は CPU 問題の分析結果です。
まず、Lua のパフォーマンスホットスポットを確認します。
詳細を表示するためにクリックします。
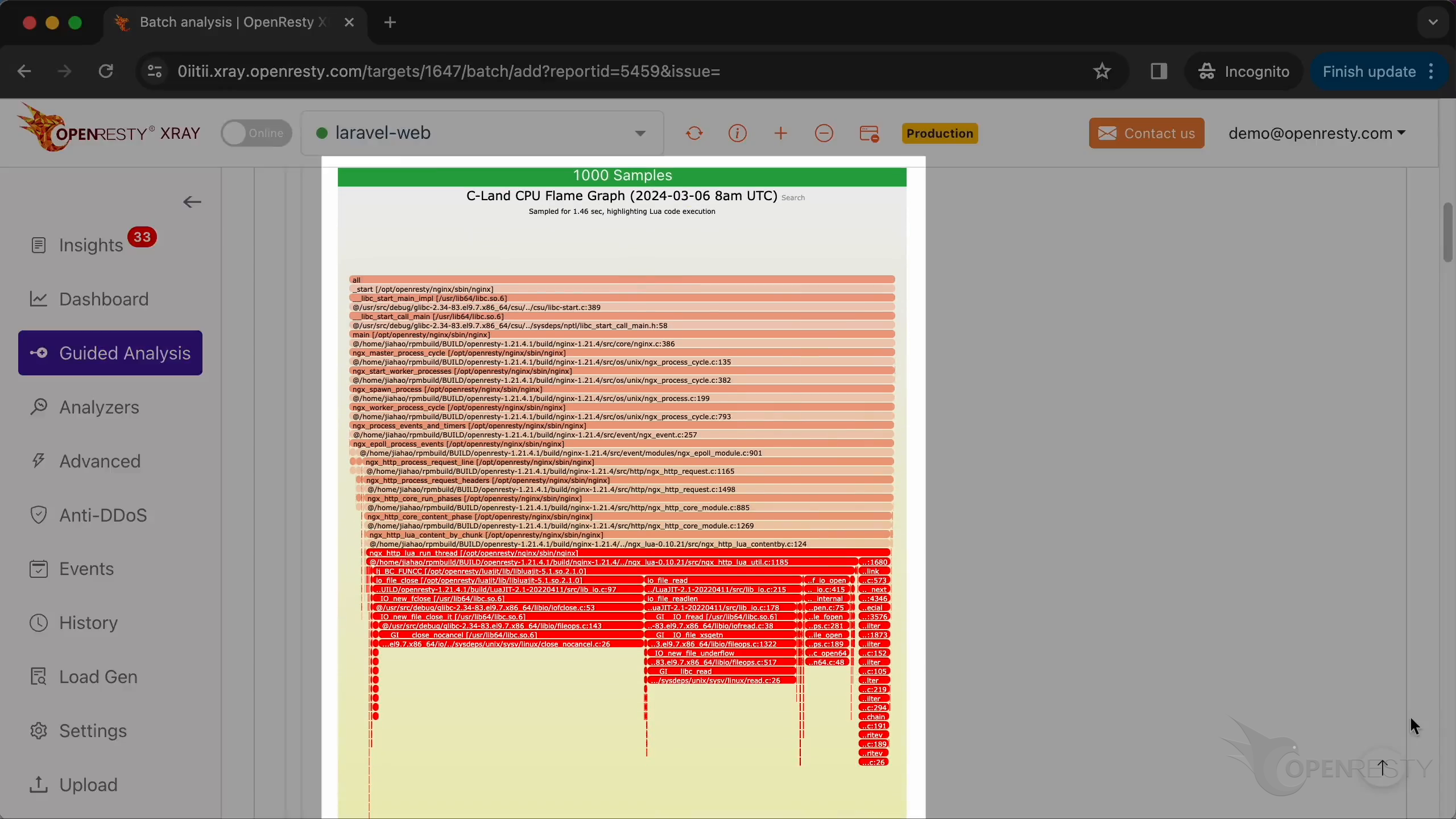
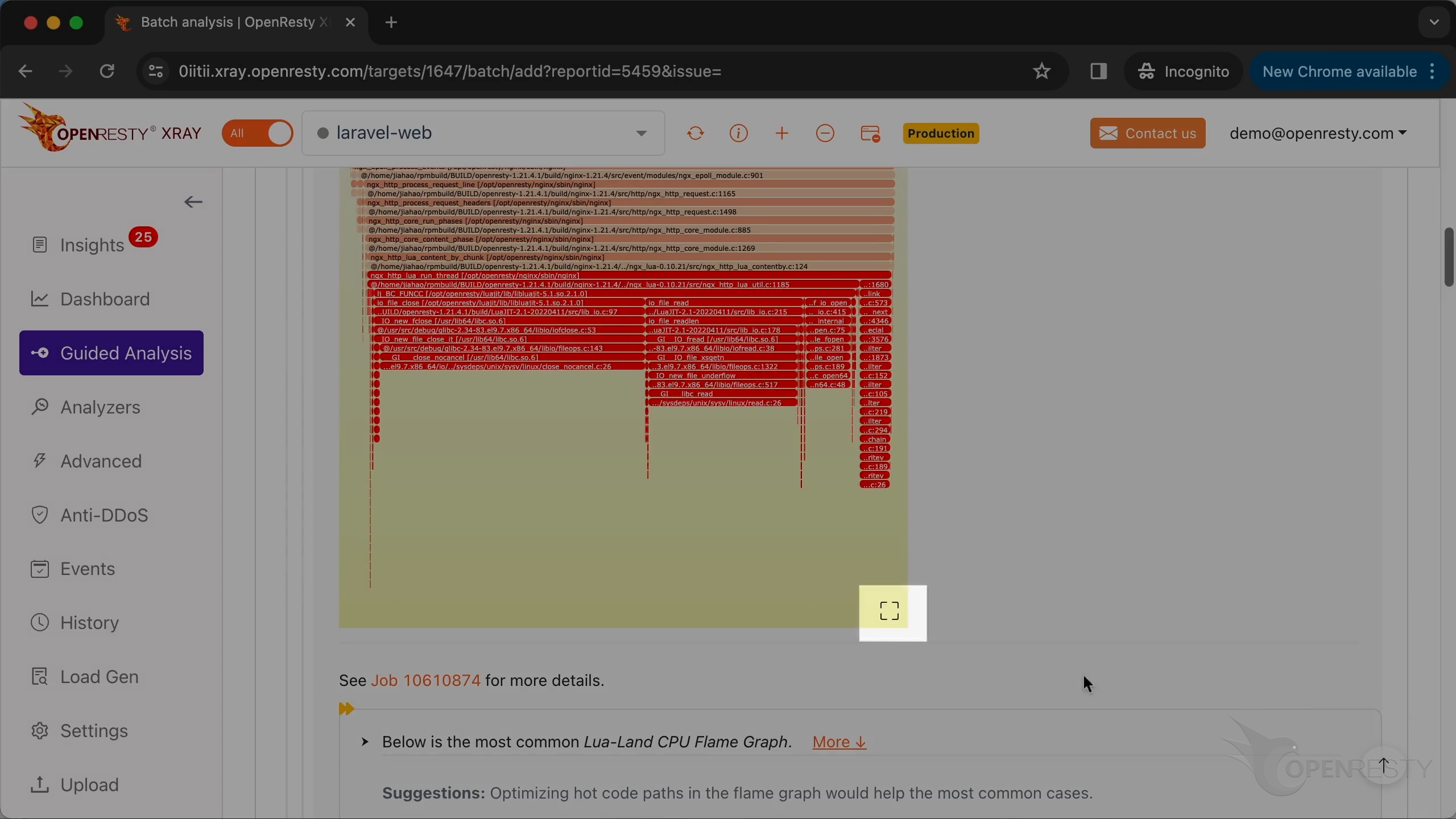
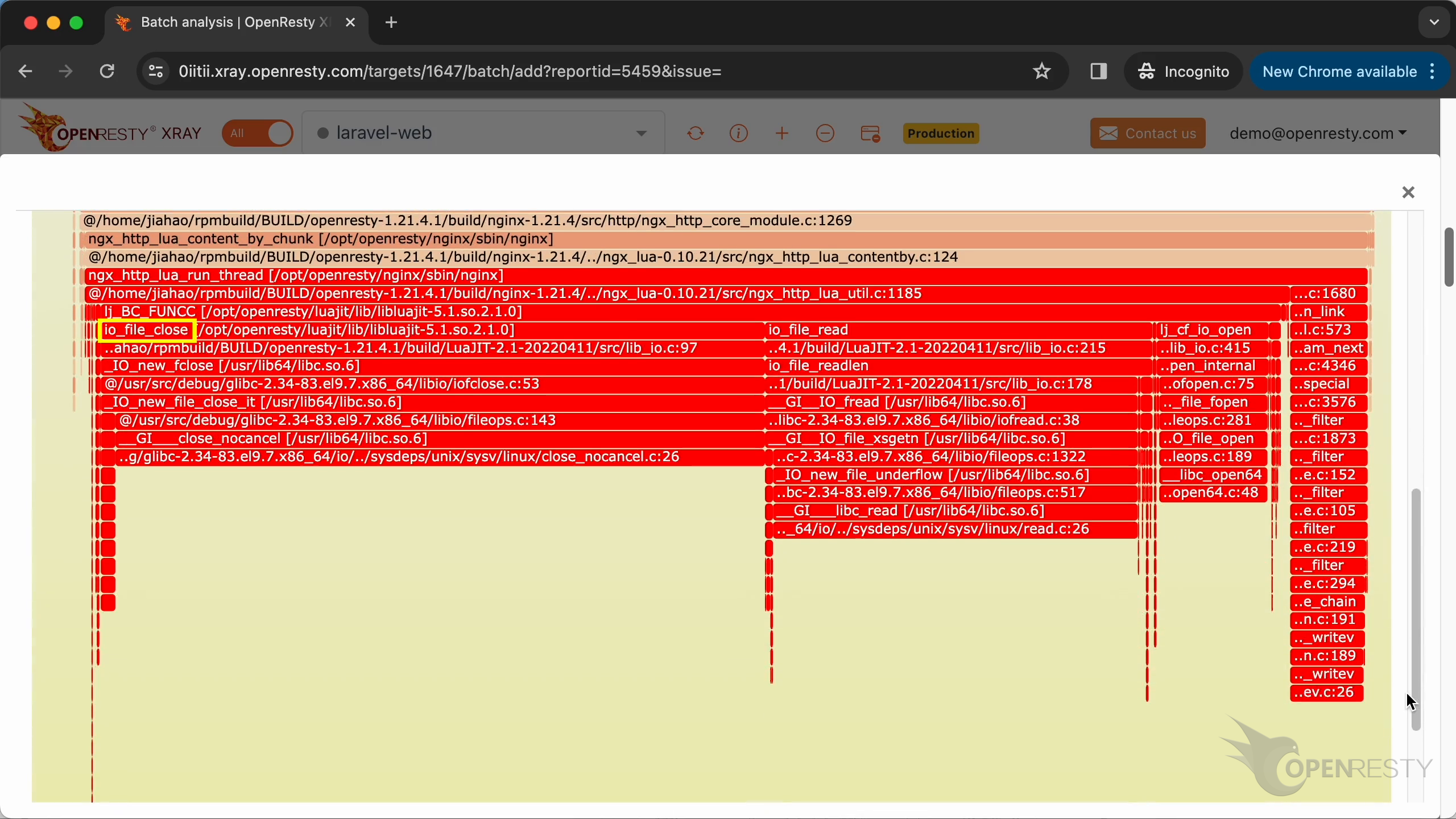
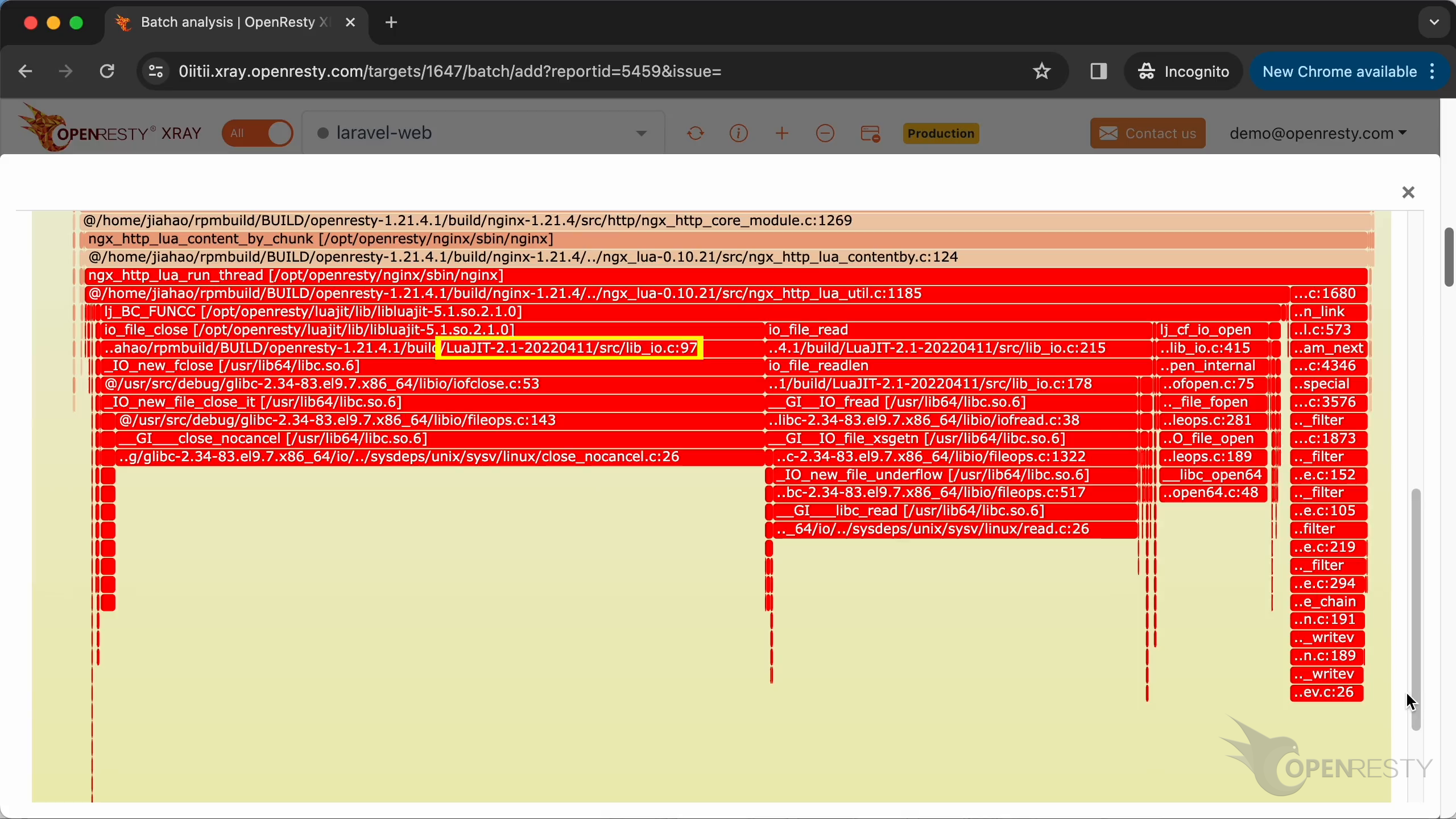
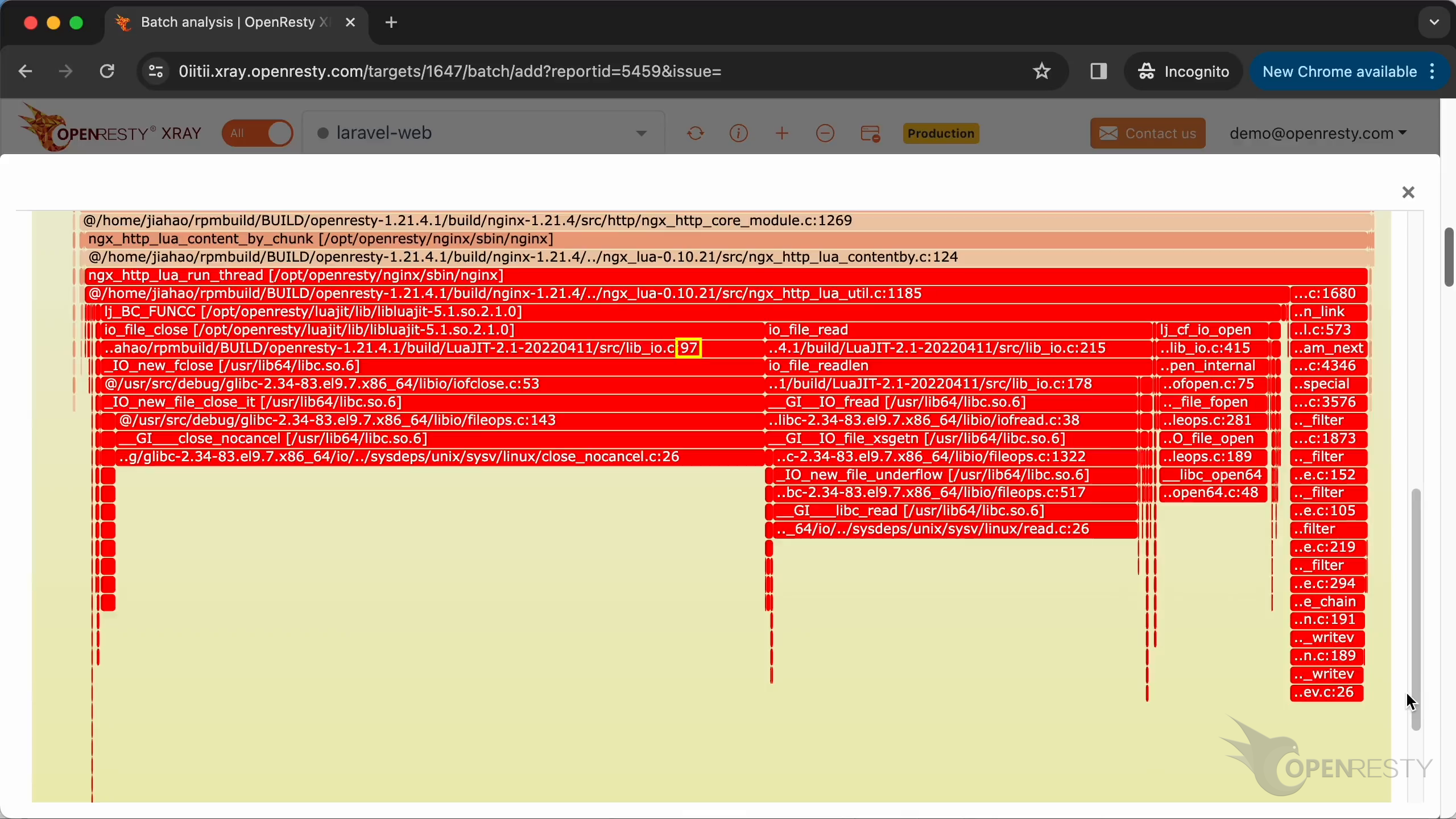
このホットコードパスは、C 言語レベルの CPU フレームグラフから自動的に導き出されたものです。
フレームグラフを拡大するためにクリックします。
インライン関数を含むすべての C 関数名が表示されています。
C ソースファイルの名前まで表示されています。
さらにソースコードの行番号まで!
詳細を表示するためにクリックします。
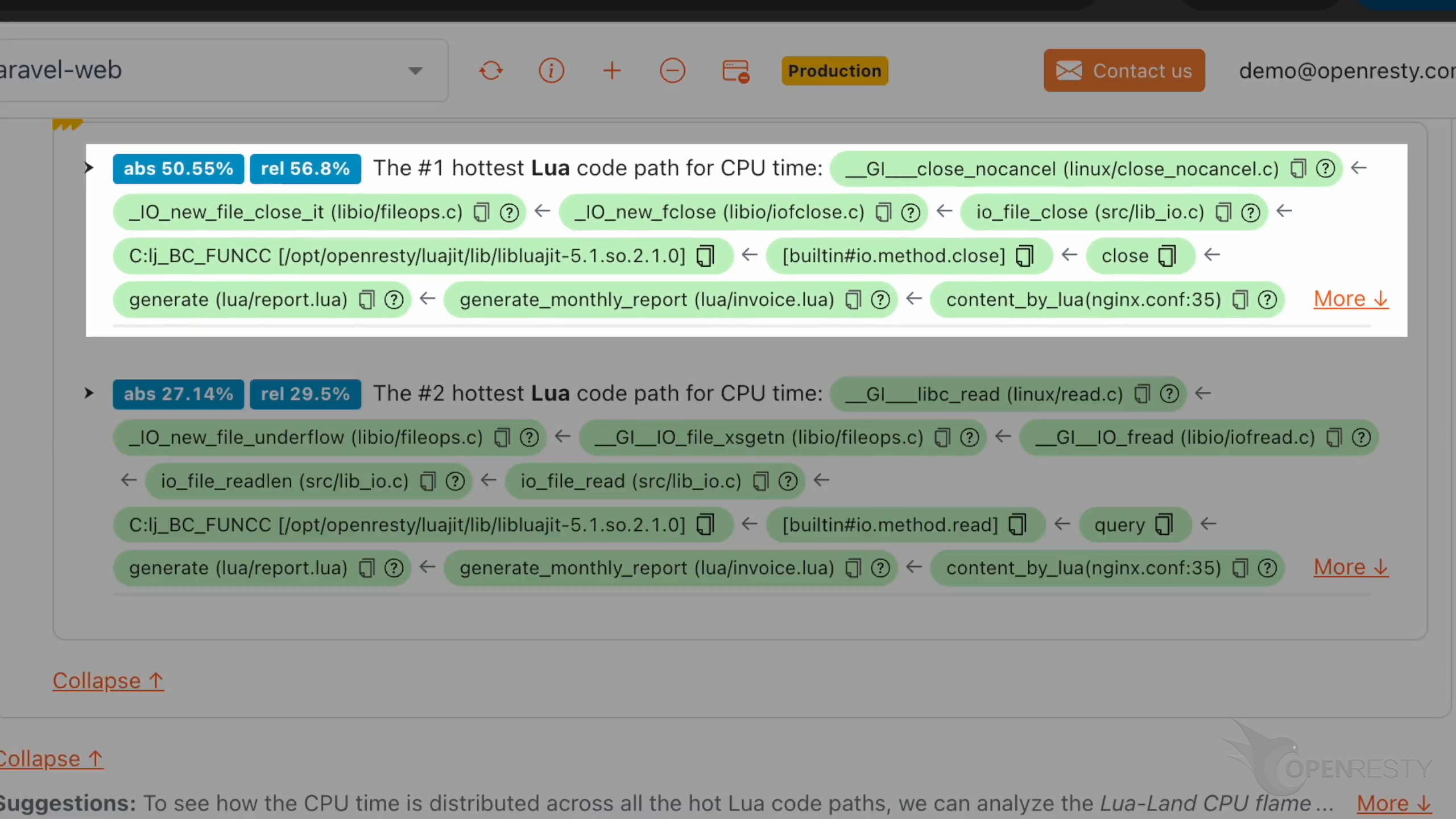
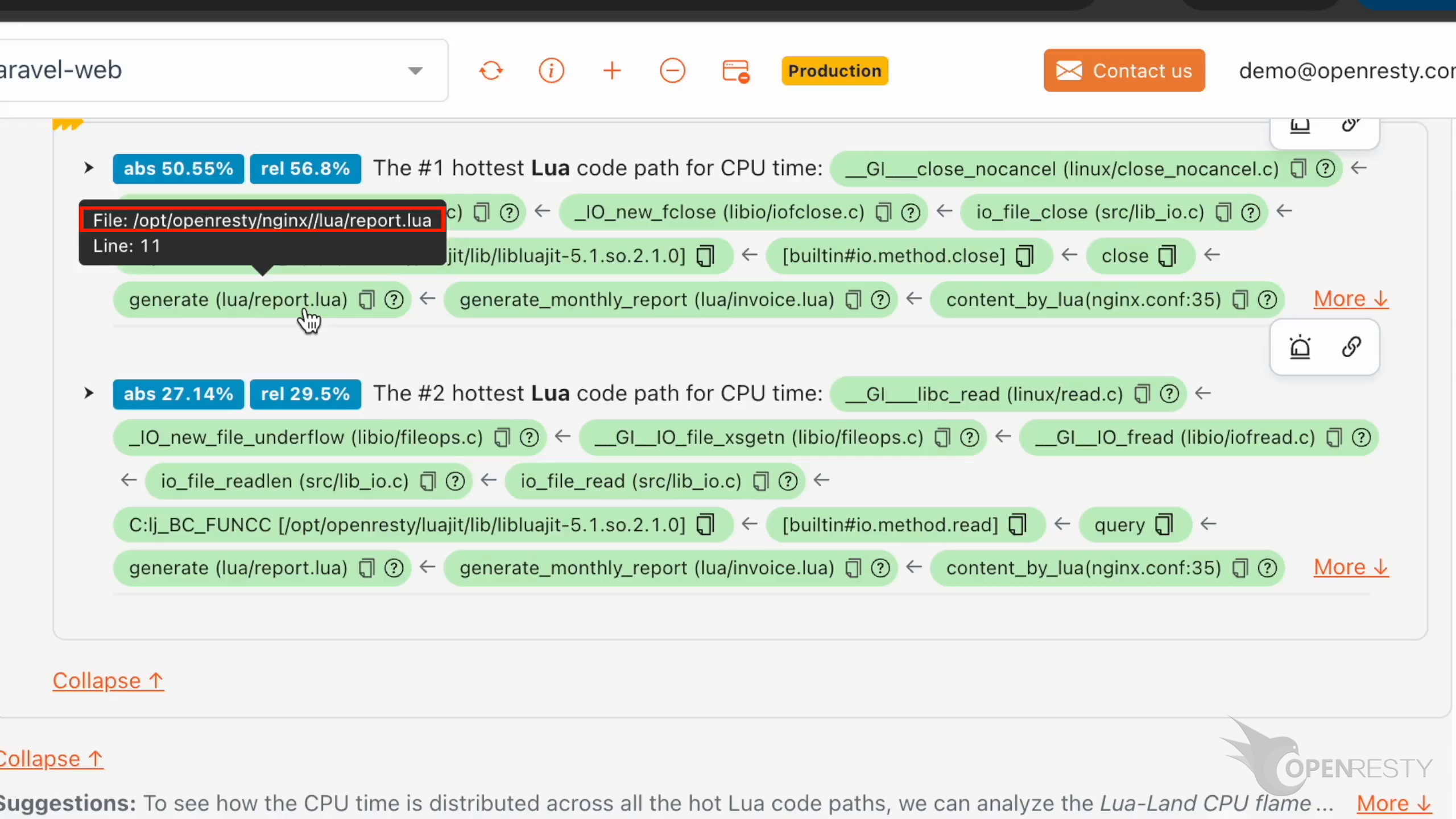
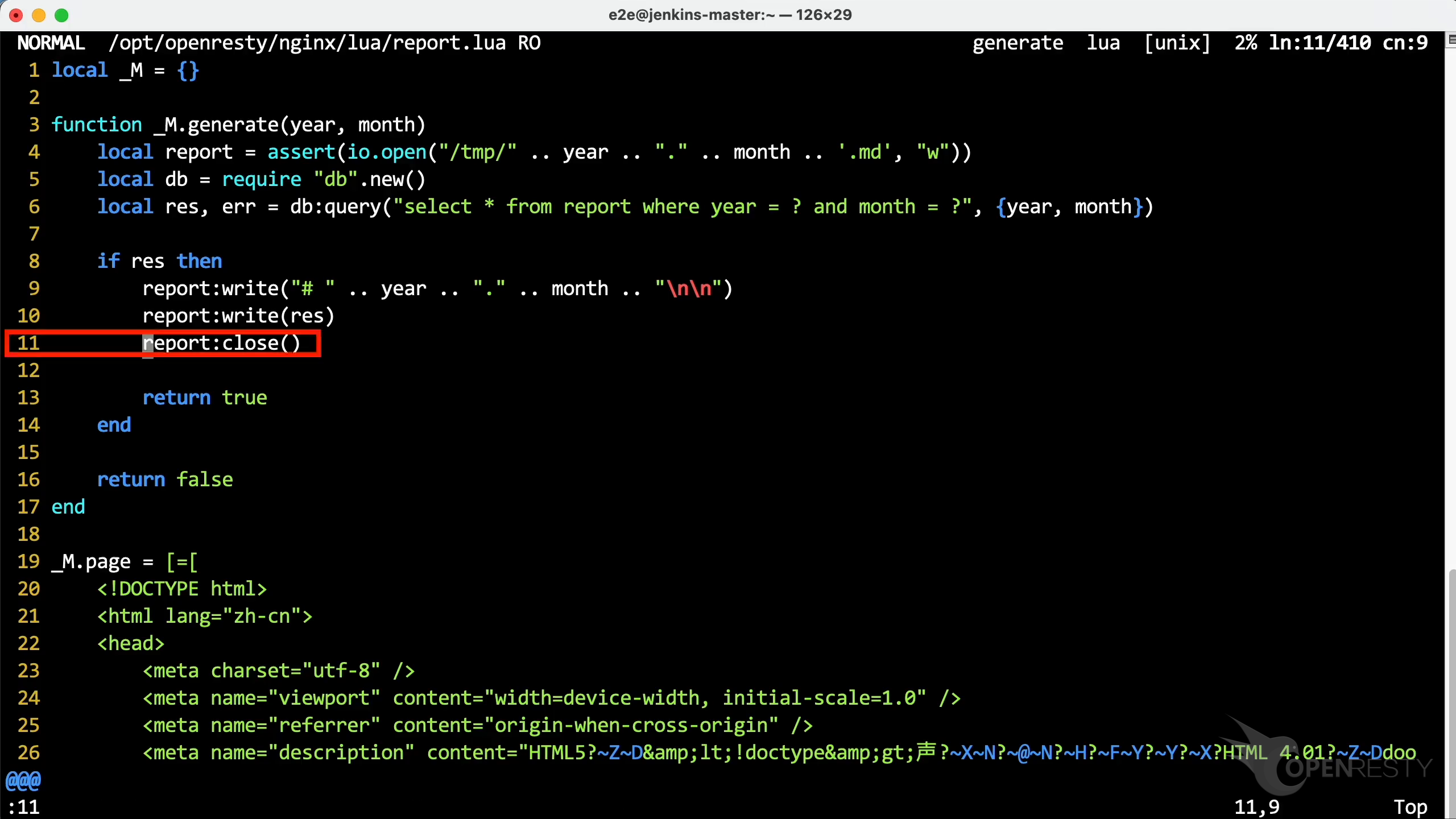
これは CPU 時間を最も多く占める Lua コードパスです。
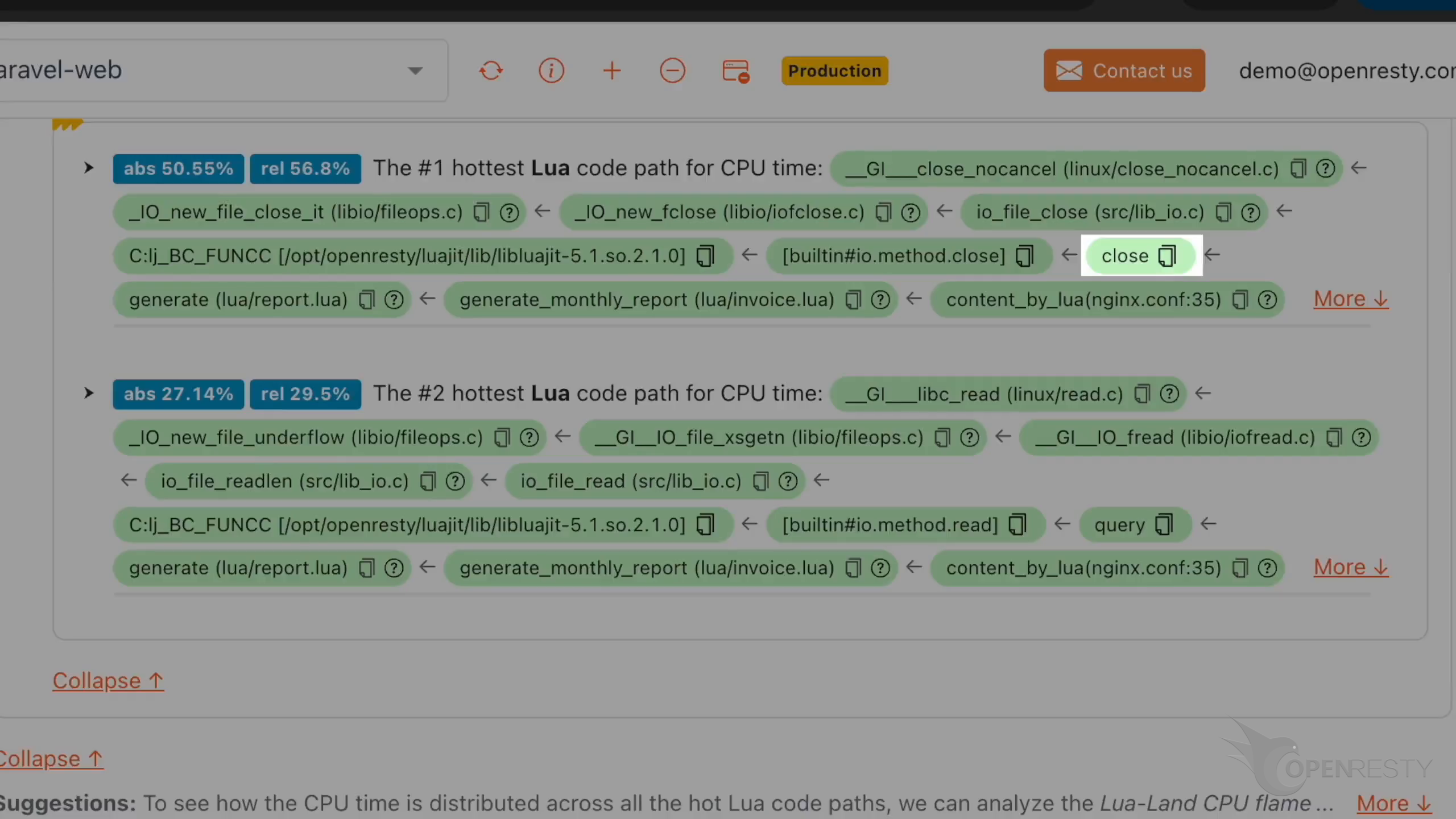
close 関数が generate 関数から呼び出されています。
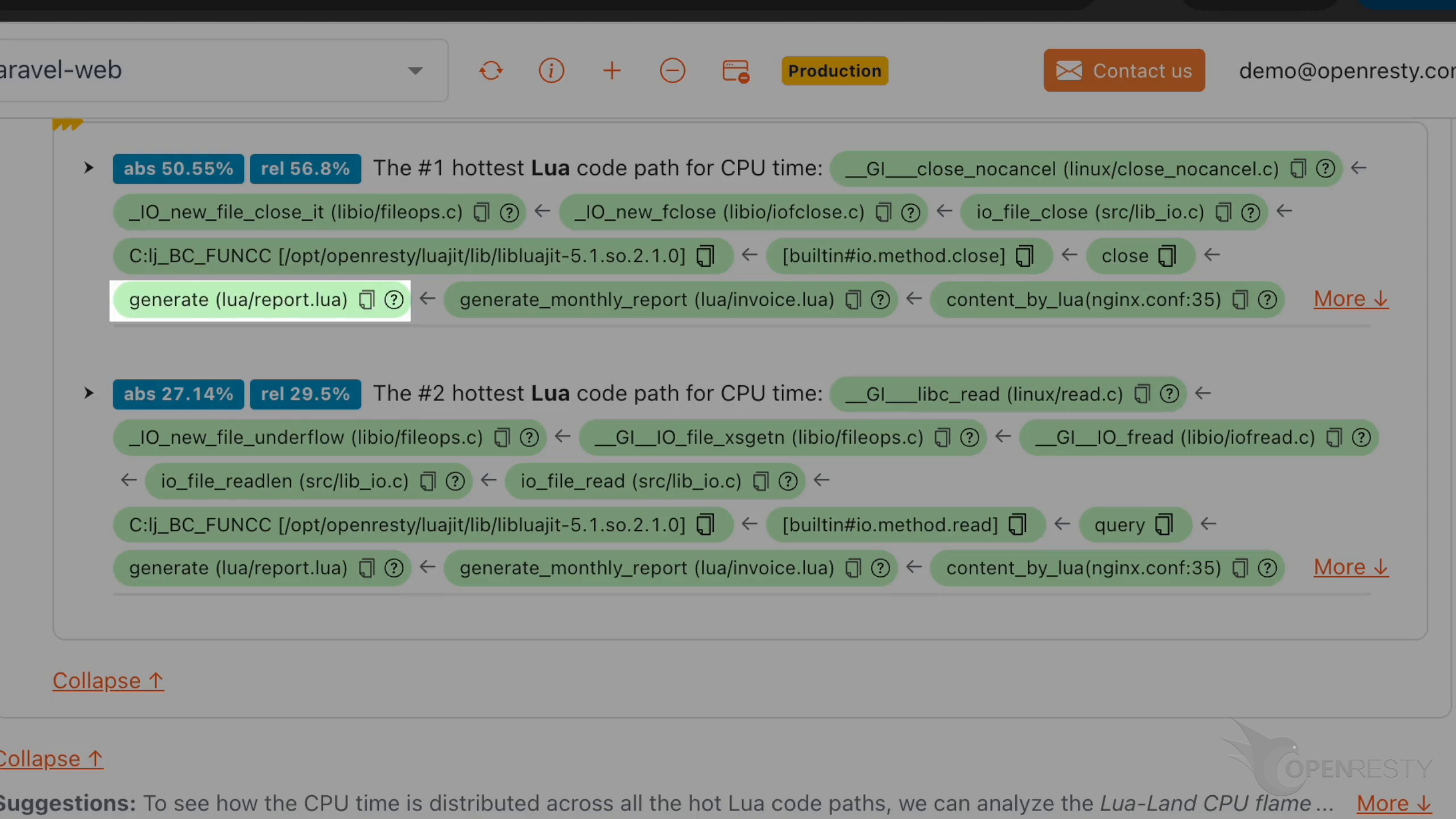
generate は Lua 関数で、Lua ソースファイル lua/report.lua で定義されています。
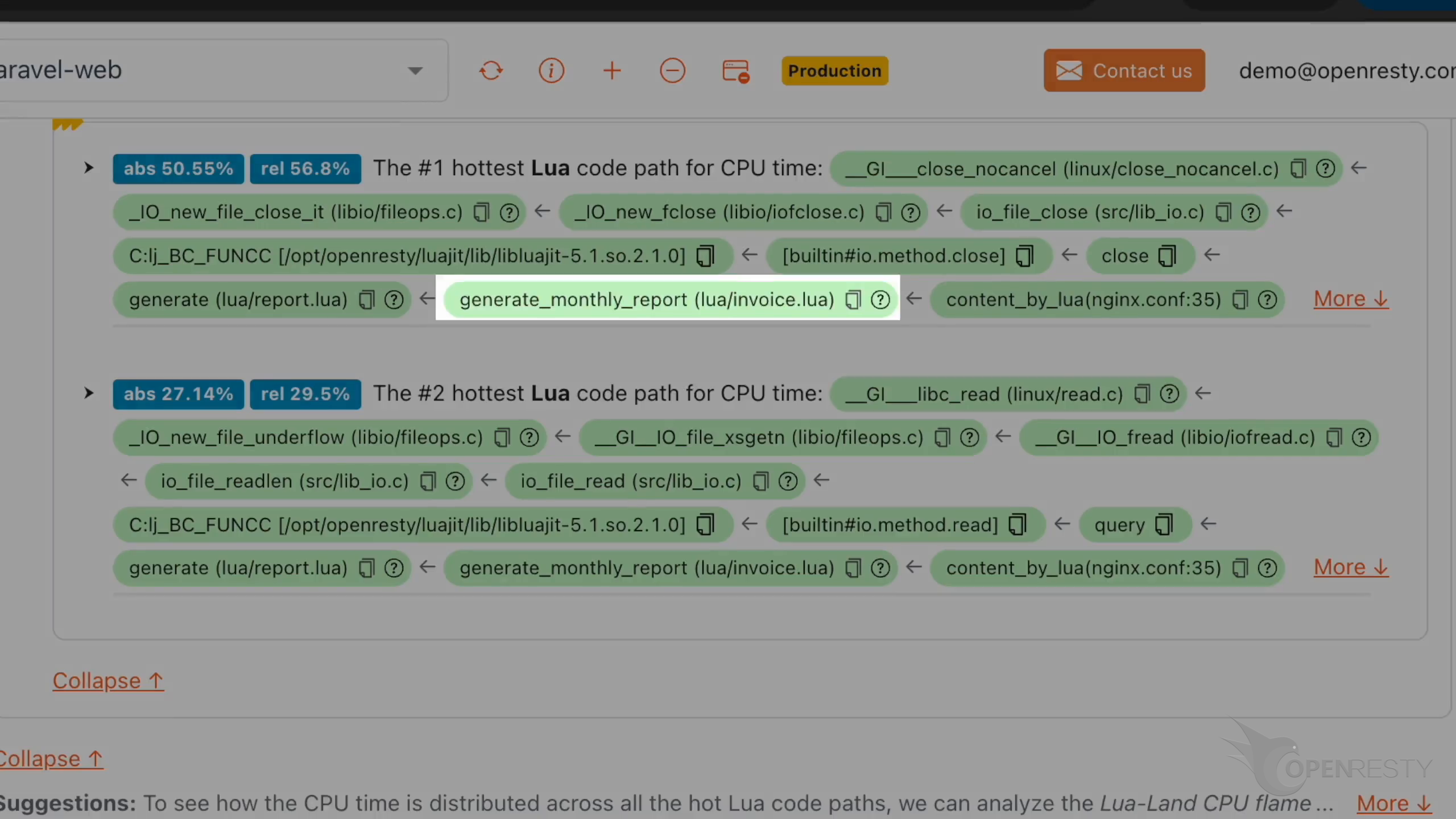
lua/invoice.lua ファイルで定義された generate_monthly_report が先ほどの generate 関数を呼び出しています。
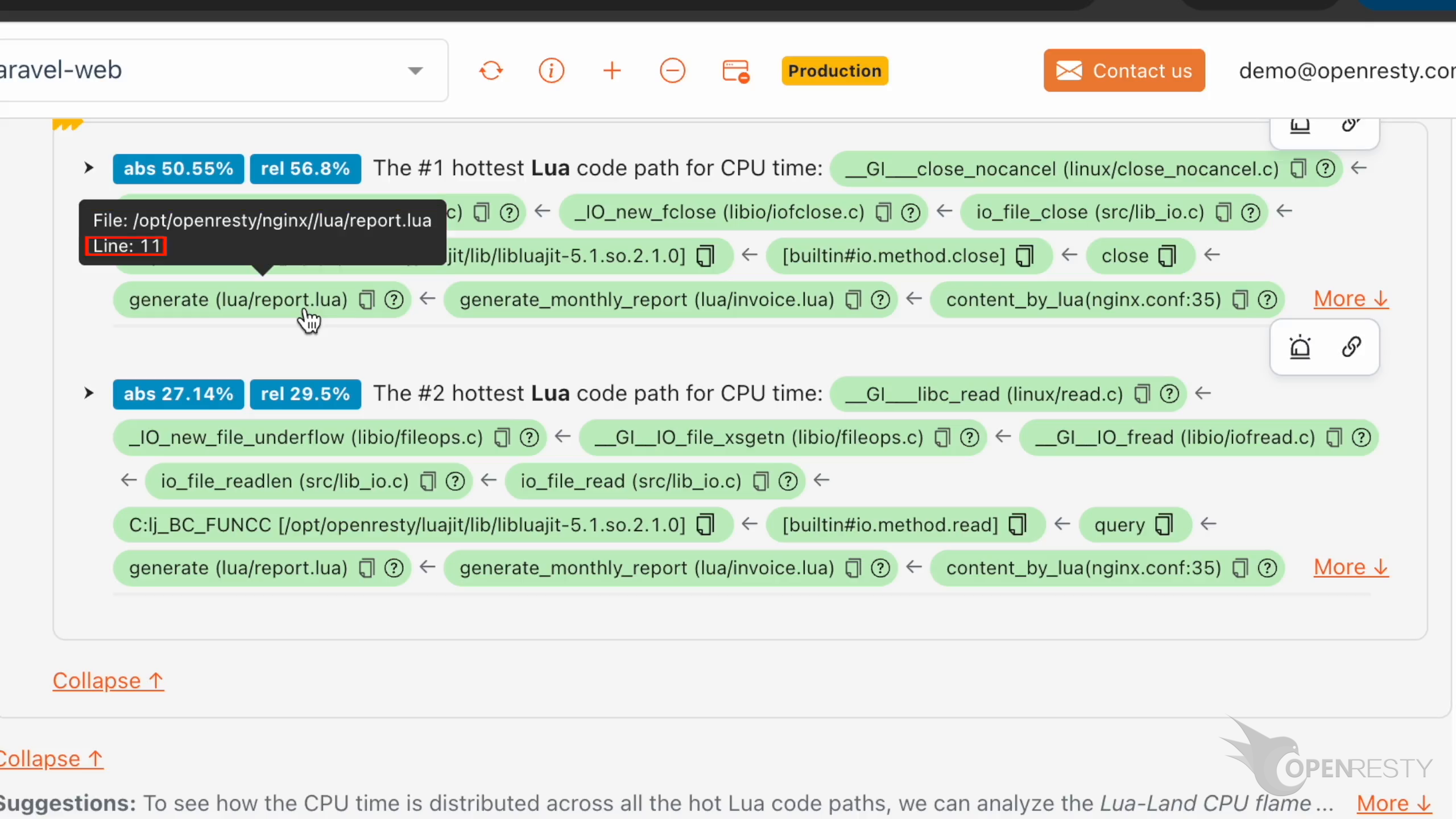
この generate 関数の緑色のボックスにマウスを合わせてみましょう。ツールチップに Lua ソースファイルの完全なパスが表示されます。
Lua ソースコードの行番号は 11 です。
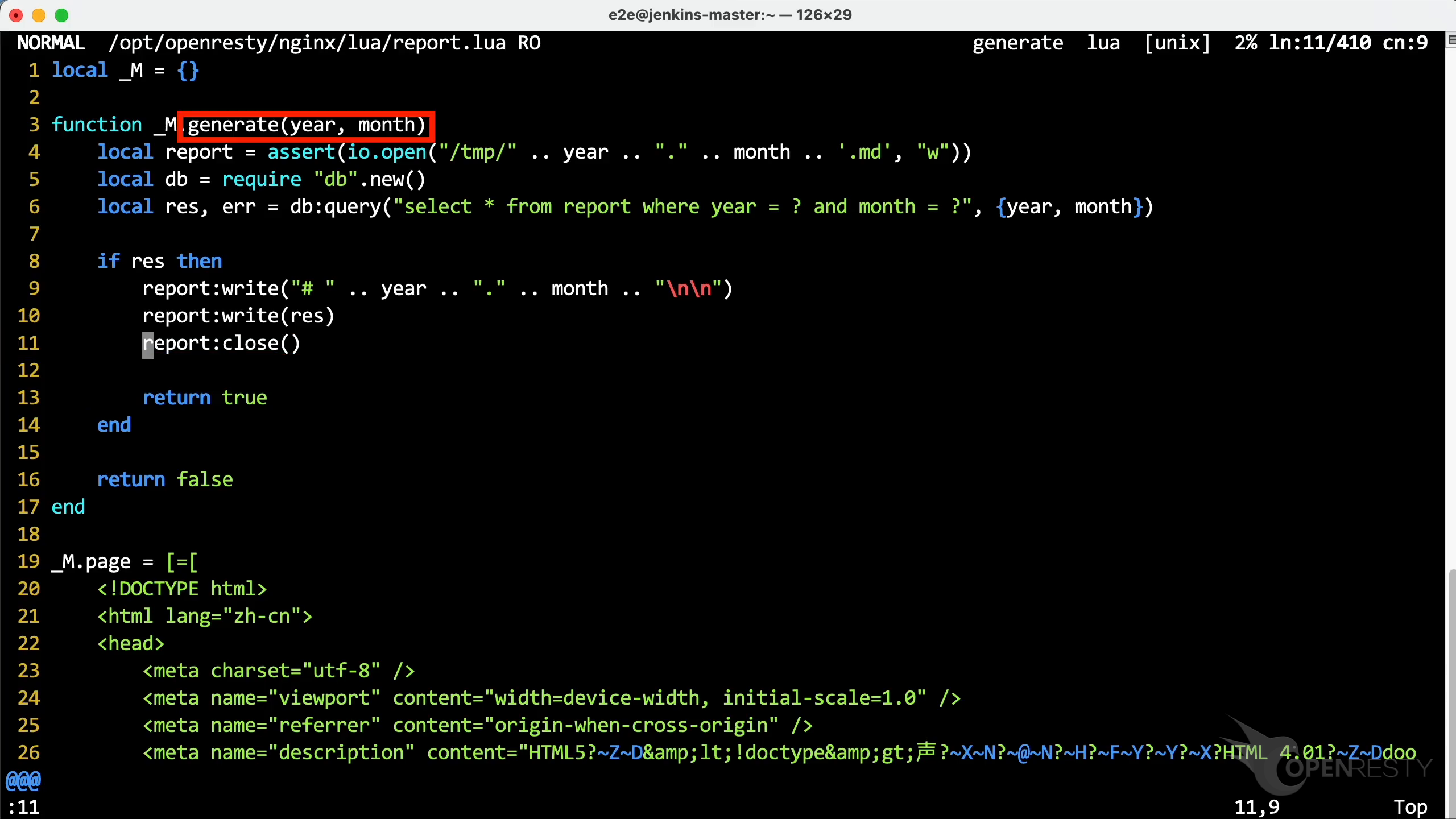
そのソースファイルのパスをコピーします。
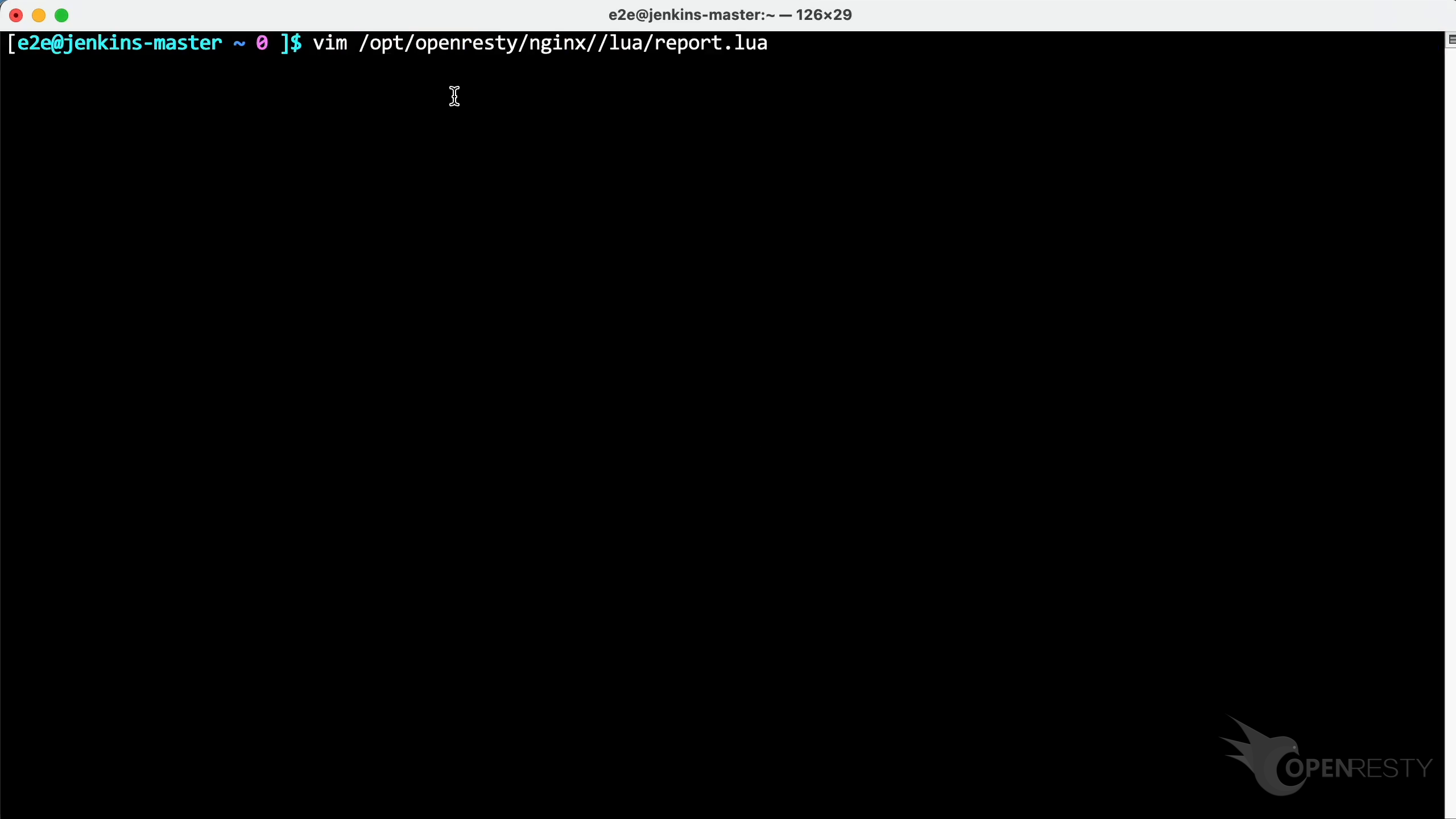
Vim エディタを使用してソースファイルを開き、Lua コードを確認します。お好みのエディタを使用していただいて構いません。
OpenResty XRay の提案に従って、11 行目にジャンプします。レポートで見た close 関数が確認できます。デバッグシンボルがなくても、ホットスポットとなっている Lua 関数とソースコード行の詳細情報を取得できています。
generate 関数はデータベースのクエリとレポートの生成に使用されています。
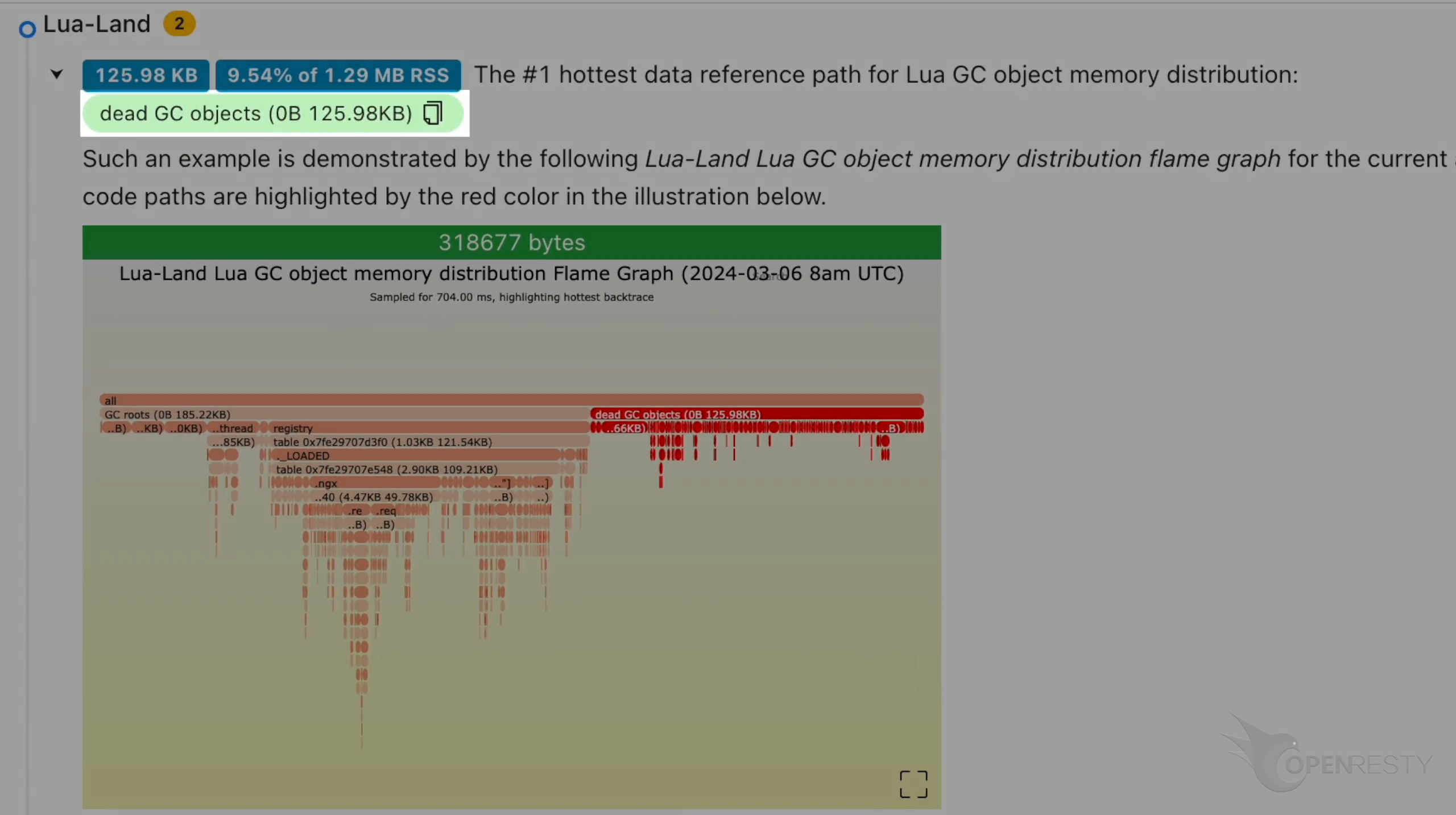
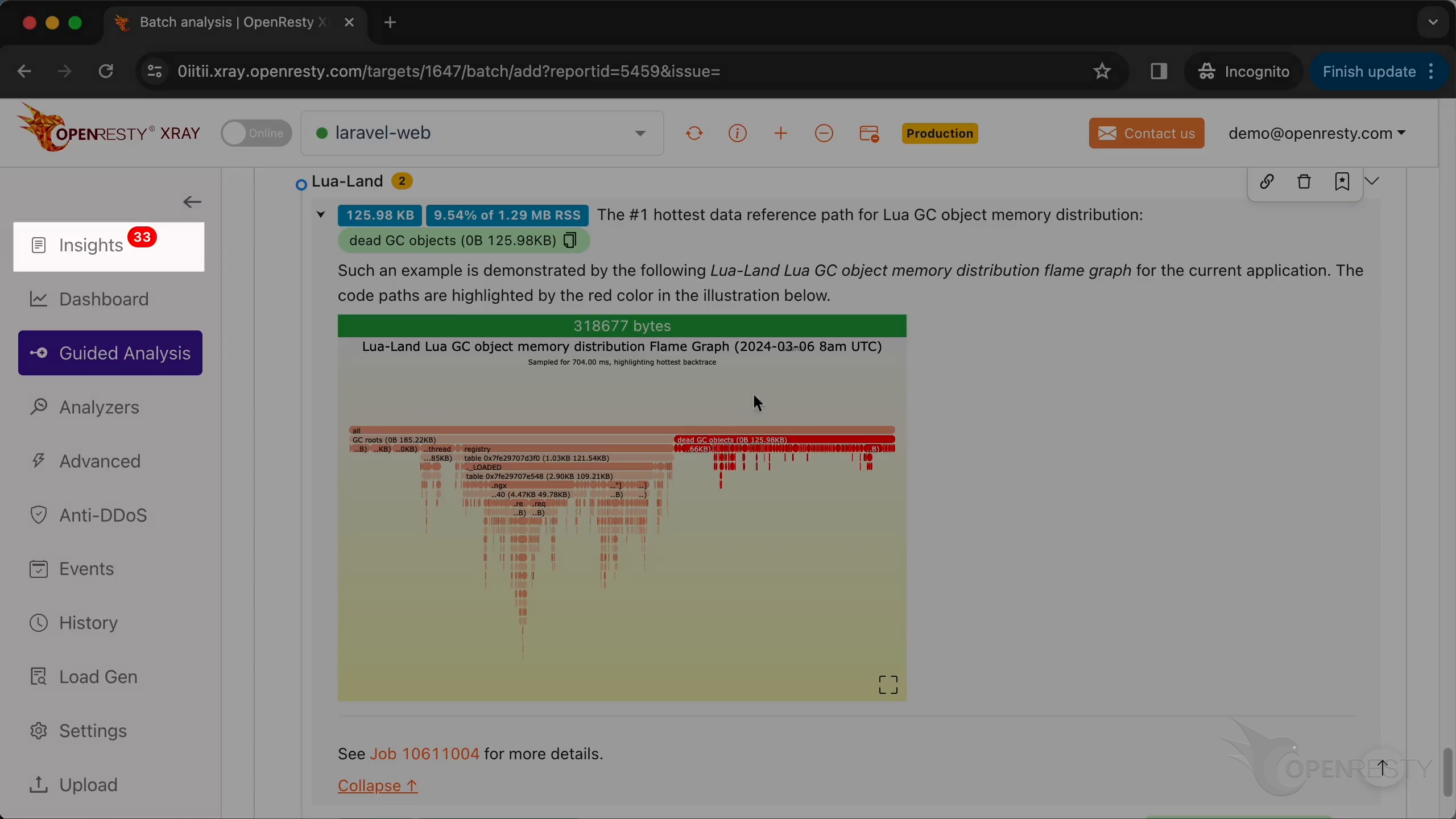
次に、レポートのメモリ分析部分を見てみましょう。
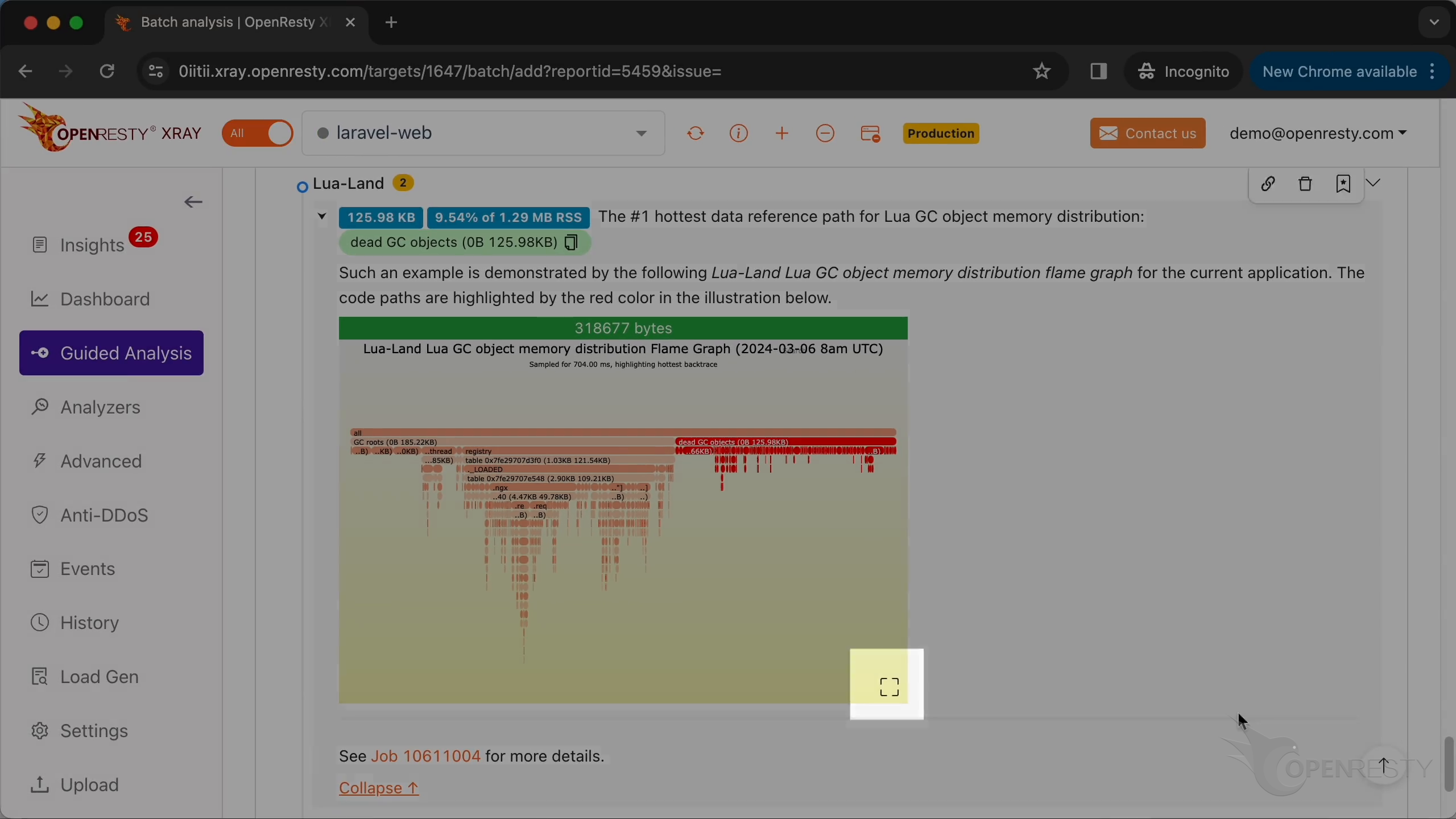
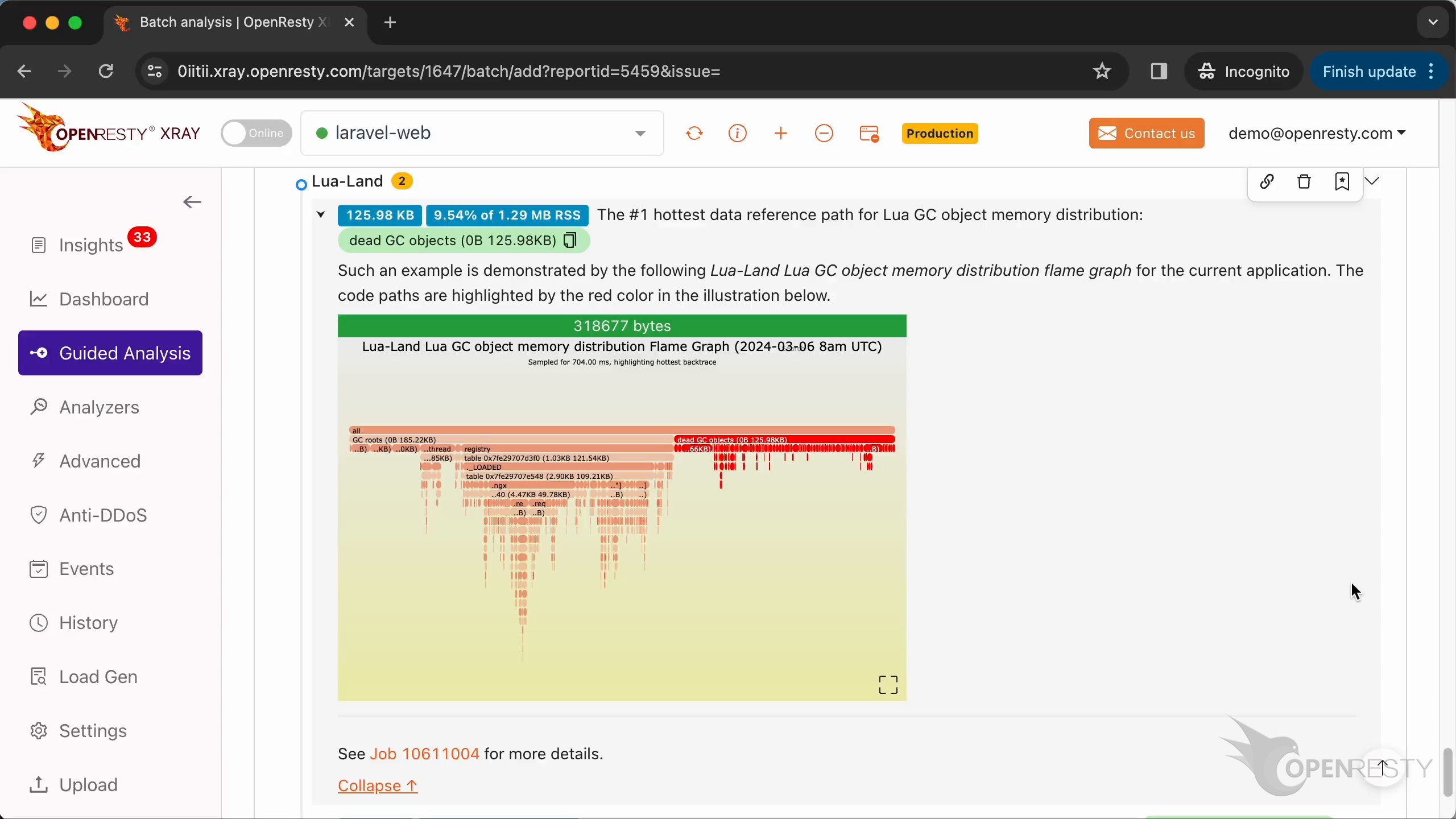
Lua 言語レベルの GC オブジェクト参照パスでは、メモリの大部分が LuaJIT ガベージコレクタによってまだ解放されていない死亡 Lua オブジェクトに占有されています。
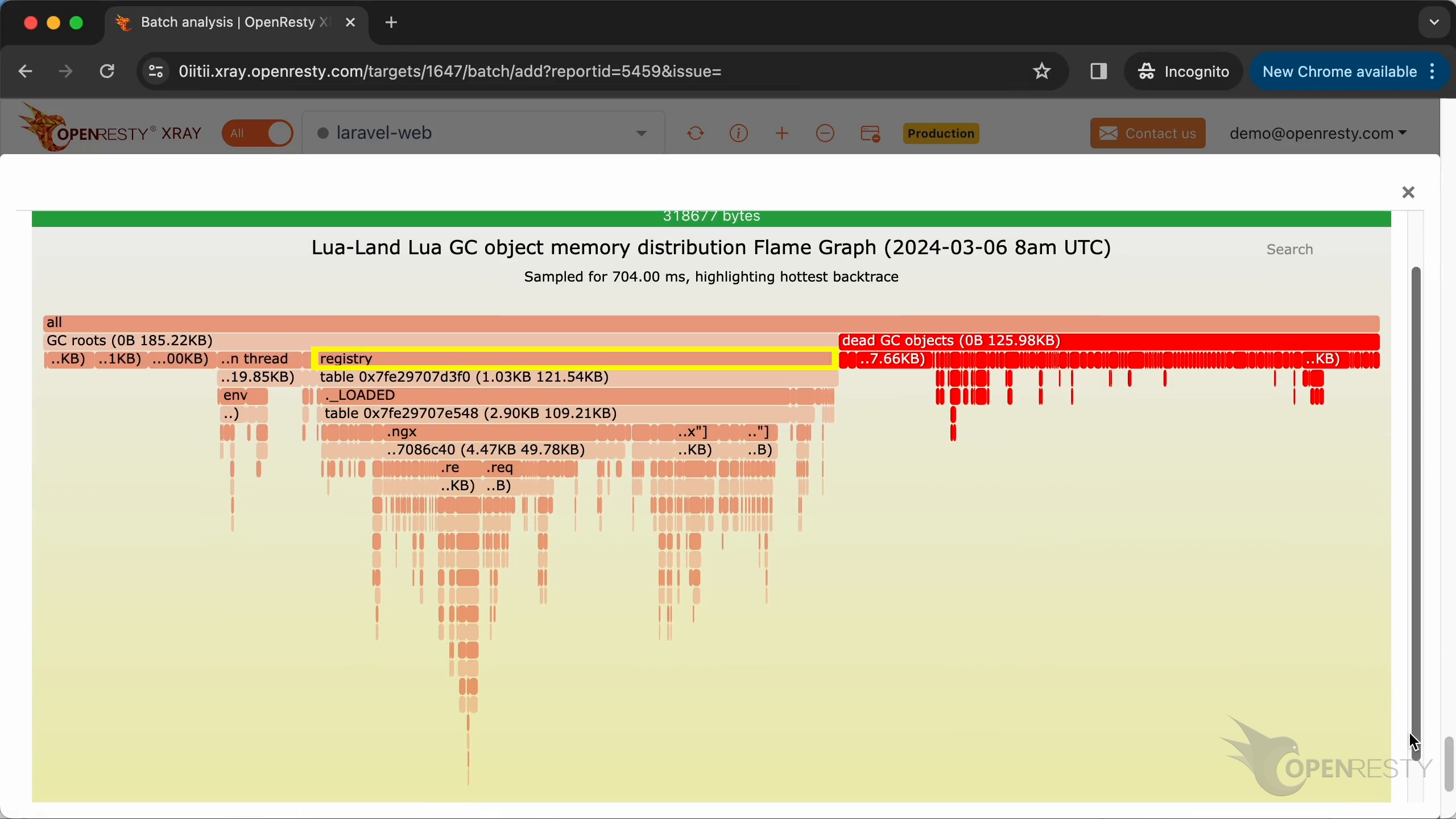
これを拡大表示するためにクリックします。
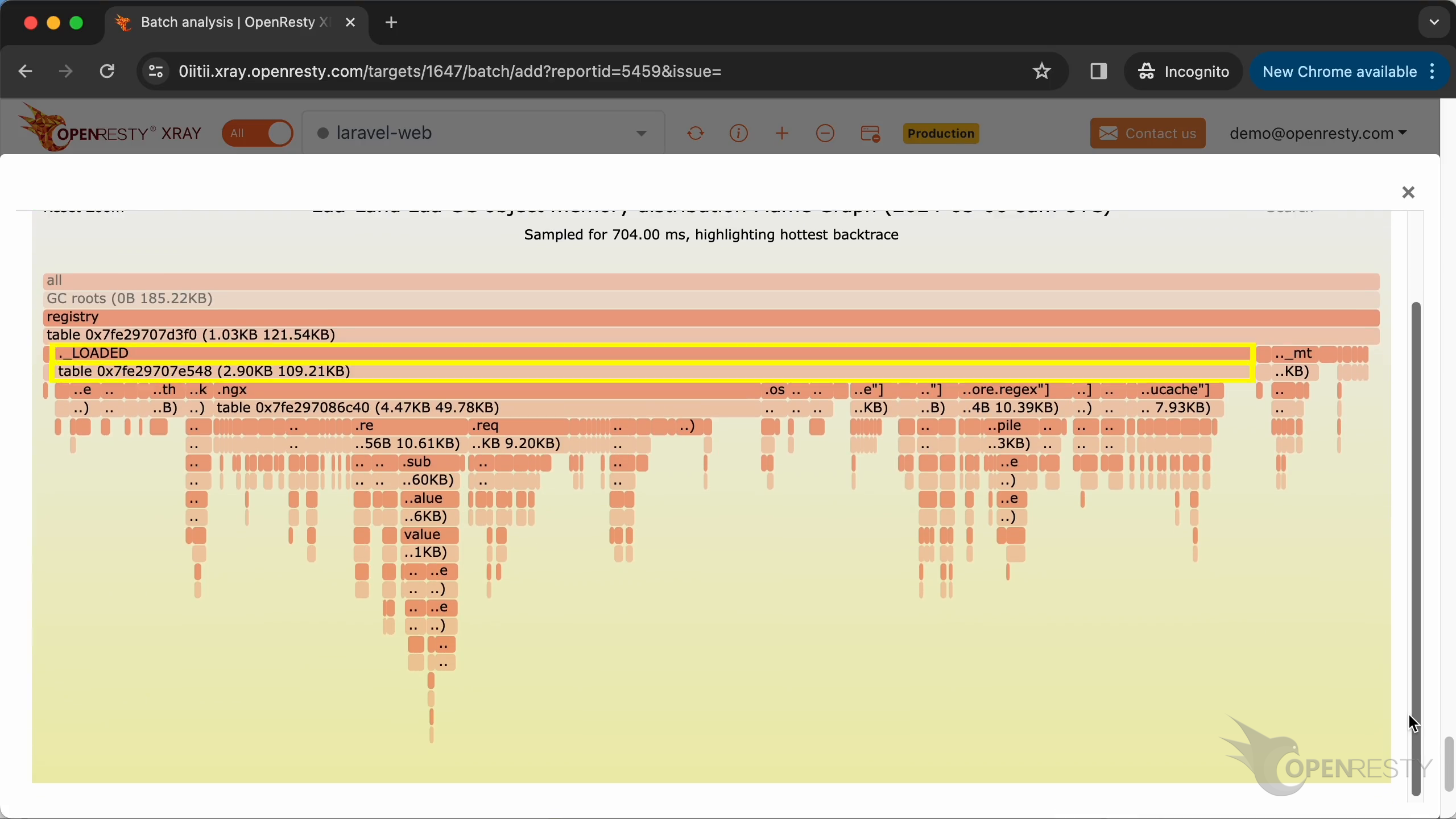
registry -> ._LOADED のデータ参照パスを拡大表示します。
このデータ参照パスの下で、table は現在の Lua アプリケーションで読み込まれているすべての Lua モジュールのデータ構造です。明らかに、これらの読み込まれた Lua モジュールも多くのメモリを占有しています。
完全自動化された分析とレポート
OpenResty XRay はオンラインプロセスを自動的に監視し、分析レポートを生成することができます。
「Insights」ページに切り替えてください。「Insights」ページでは、日次および週次のレポートを確認することができます。
したがって、「Guided Analysis」機能を必ずしも使用する必要はありません。もちろん、「Guided Analysis」はアプリケーションの開発やデモンストレーションに非常に有用です。
OpenResty XRay について
OpenResty XRay は動的トレーシング製品であり、実行中のアプリケーションを自動的に分析して、パフォーマンスの問題、動作の問題、セキュリティの脆弱性を解決し、実行可能な提案を提供いたします。基盤となる実装において、OpenResty XRay は弊社の Y 言語によって駆動され、Stap+、eBPF+、GDB、ODB など、様々な環境下で複数の異なるランタイムをサポートしております。
著者について
章亦春(Zhang Yichun)は、オープンソースの OpenResty® プロジェクトの創始者であり、OpenResty Inc. の CEO および創業者です。
章亦春(GitHub ID: agentzh)は中国江蘇省生まれで、現在は米国ベイエリアに在住しております。彼は中国における初期のオープンソース技術と文化の提唱者およびリーダーの一人であり、Cloudflare、Yahoo!、Alibaba など、国際的に有名なハイテク企業に勤務した経験があります。「エッジコンピューティング」、「動的トレーシング」、「機械プログラミング」 の先駆者であり、22 年以上のプログラミング経験と 16 年以上のオープンソース経験を持っております。世界中で 4000 万以上のドメイン名を持つユーザーを抱えるオープンソースプロジェクトのリーダーとして、彼は OpenResty® オープンソースプロジェクトをベースに、米国シリコンバレーの中心部にハイテク企業 OpenResty Inc. を設立いたしました。同社の主力製品である OpenResty XRay動的トレーシング技術を利用した非侵襲的な障害分析および排除ツール)と OpenResty XRay(マイクロサービスおよび分散トラフィックに最適化された多機能
翻訳
英語版の原文と日本語訳版(本文)をご用意しております。読者の皆様による他の言語への翻訳版も歓迎いたします。全文翻訳で省略がなければ、採用を検討させていただきます。心より感謝申し上げます!