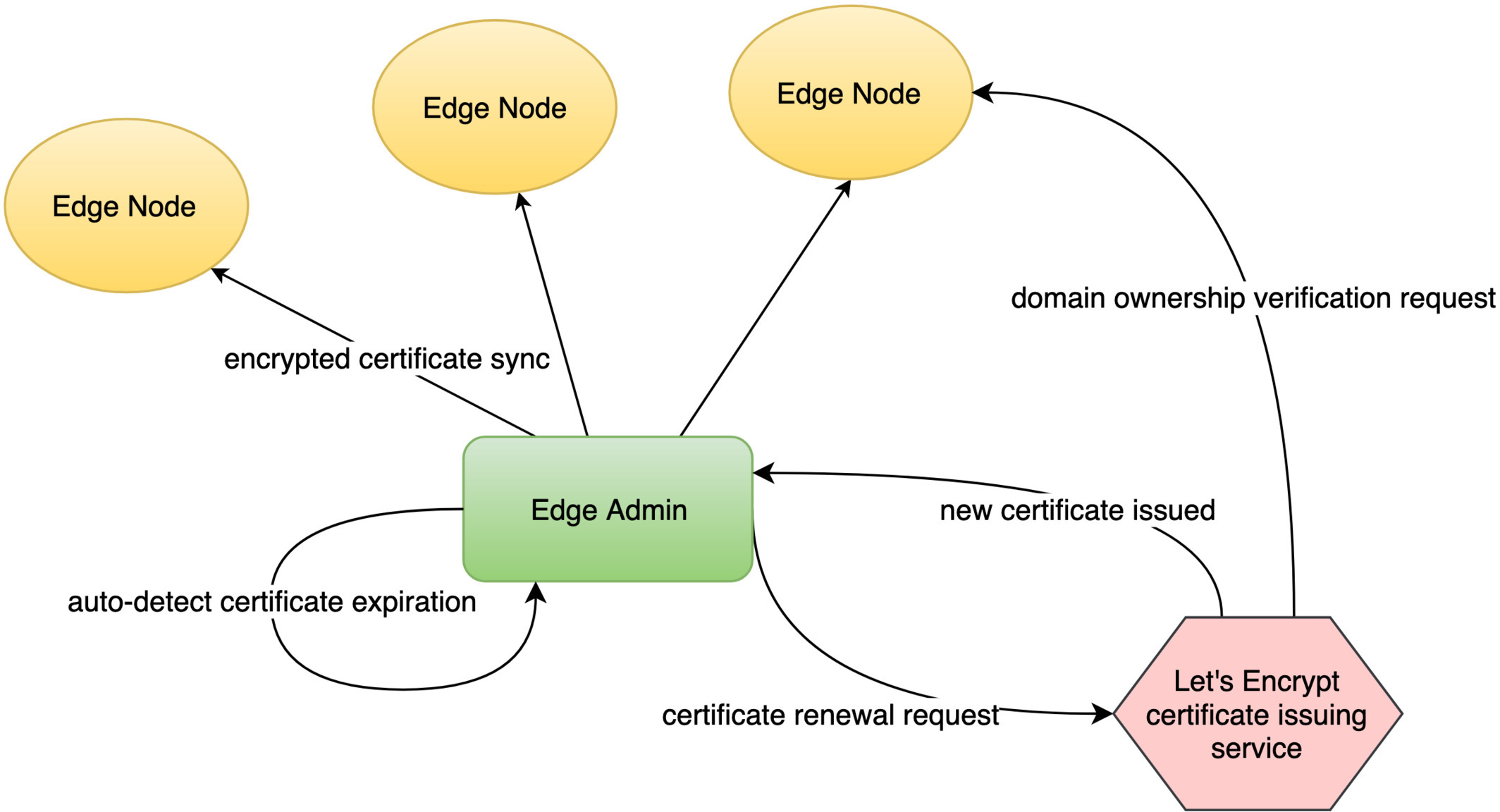
OpenResty Edge で Let's Encrypt を使用して無料の SSL 証明書を発行する
今回は、OpenResty Edge で Let’s Encrypt を使用して無料の SSL 証明書を自動的に発行する方法をご紹介いたします。
アプリケーションにワイルドカードドメインを追加する
いつものように、OpenResty Edge の Admin Web コンソールにアクセスしましょう。これはコンソールのサンプルデプロイメントです。各ユーザーは独自のローカルデプロイメントを持っています。
今回も test-edge.com ドメインのサンプルアプリケーションを使用します。
すでに SSL 用に 443 ポートでリッスンしていることがわかります。
このアプリケーションに入ります。
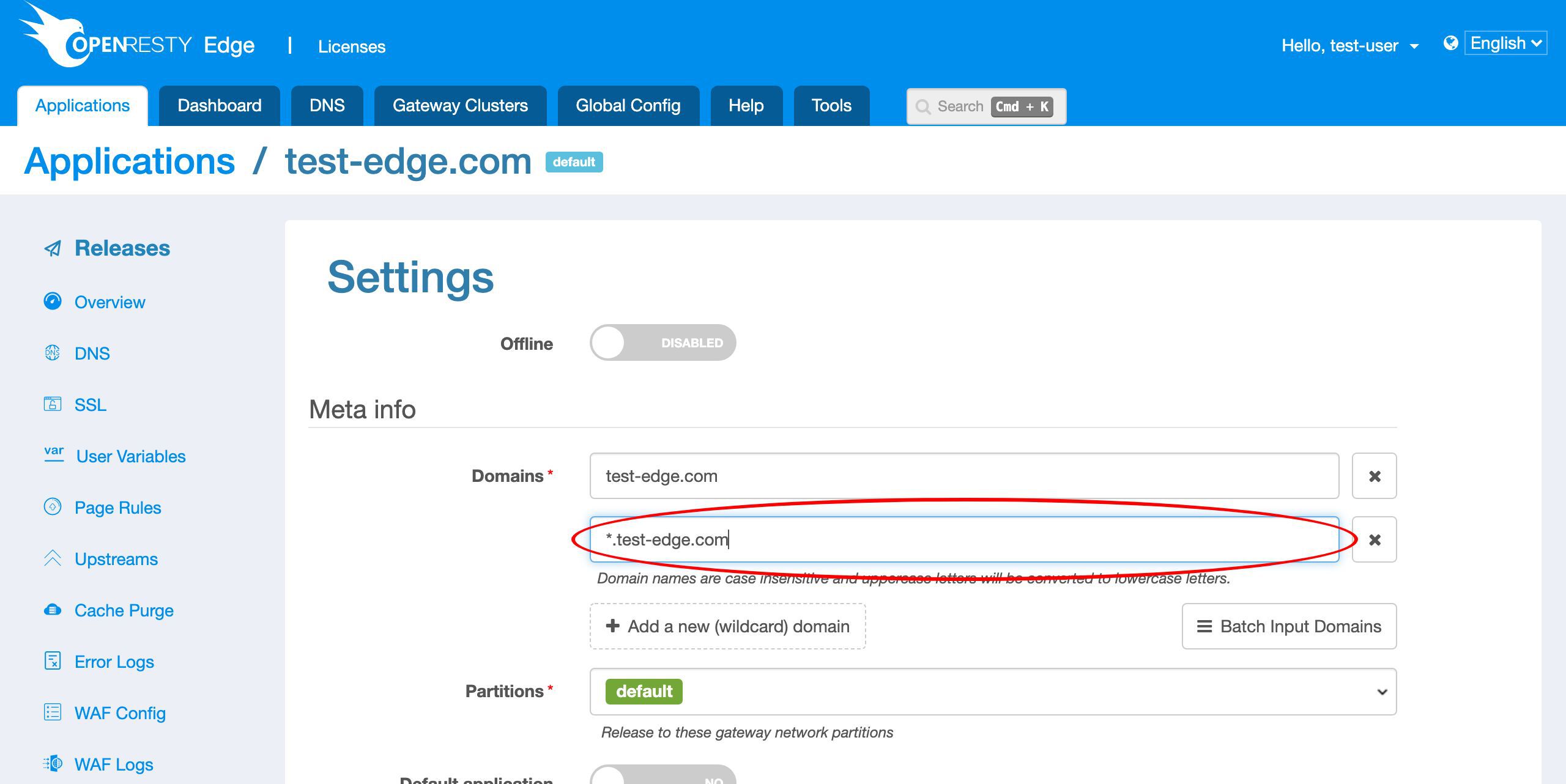
ここでは、サブドメインを使用してデモを行いたいので、まずアプリケーションの設定を調整する必要があります。
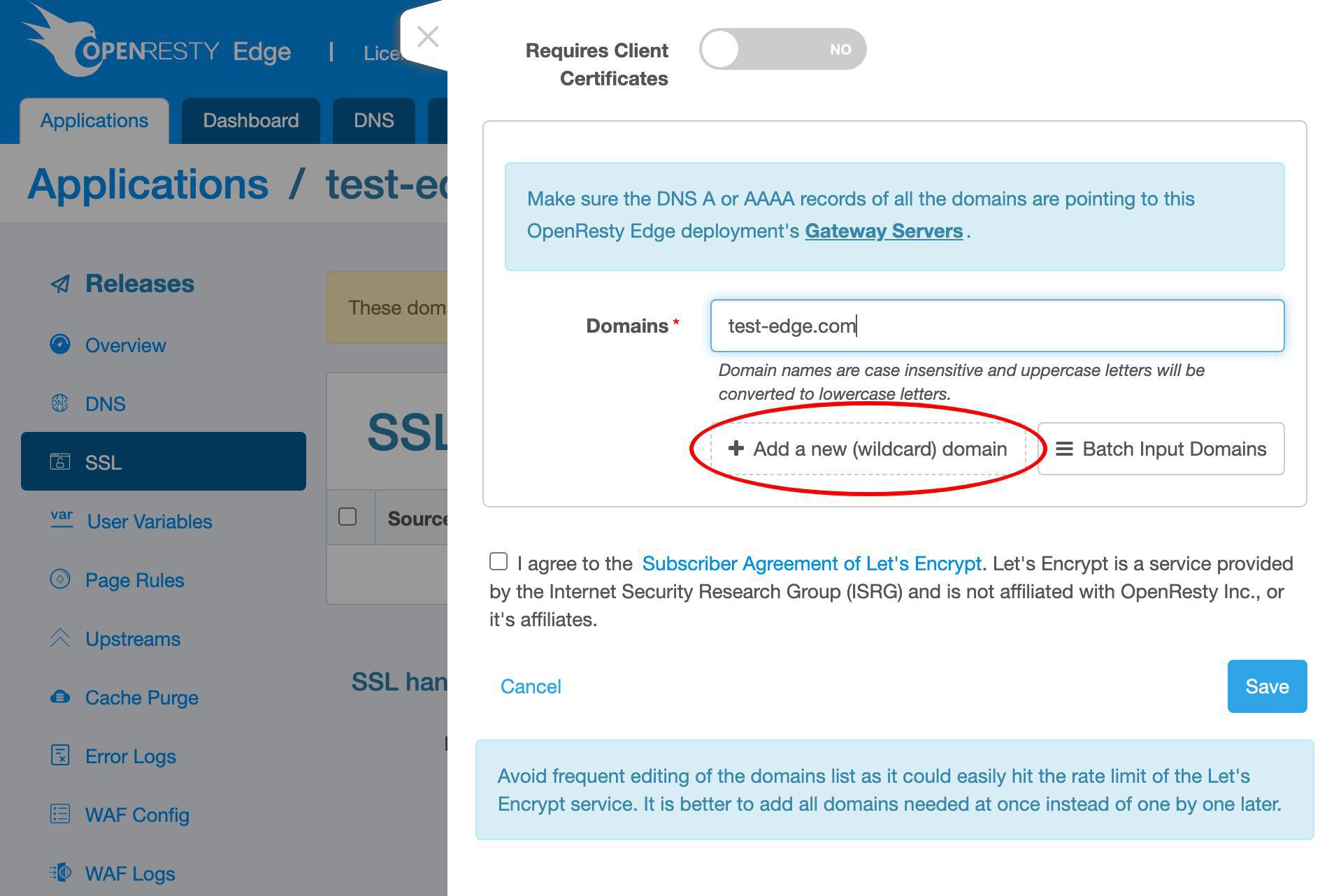
このアプリケーションに新しいワイルドカードドメインを追加しましょう。
保存します。
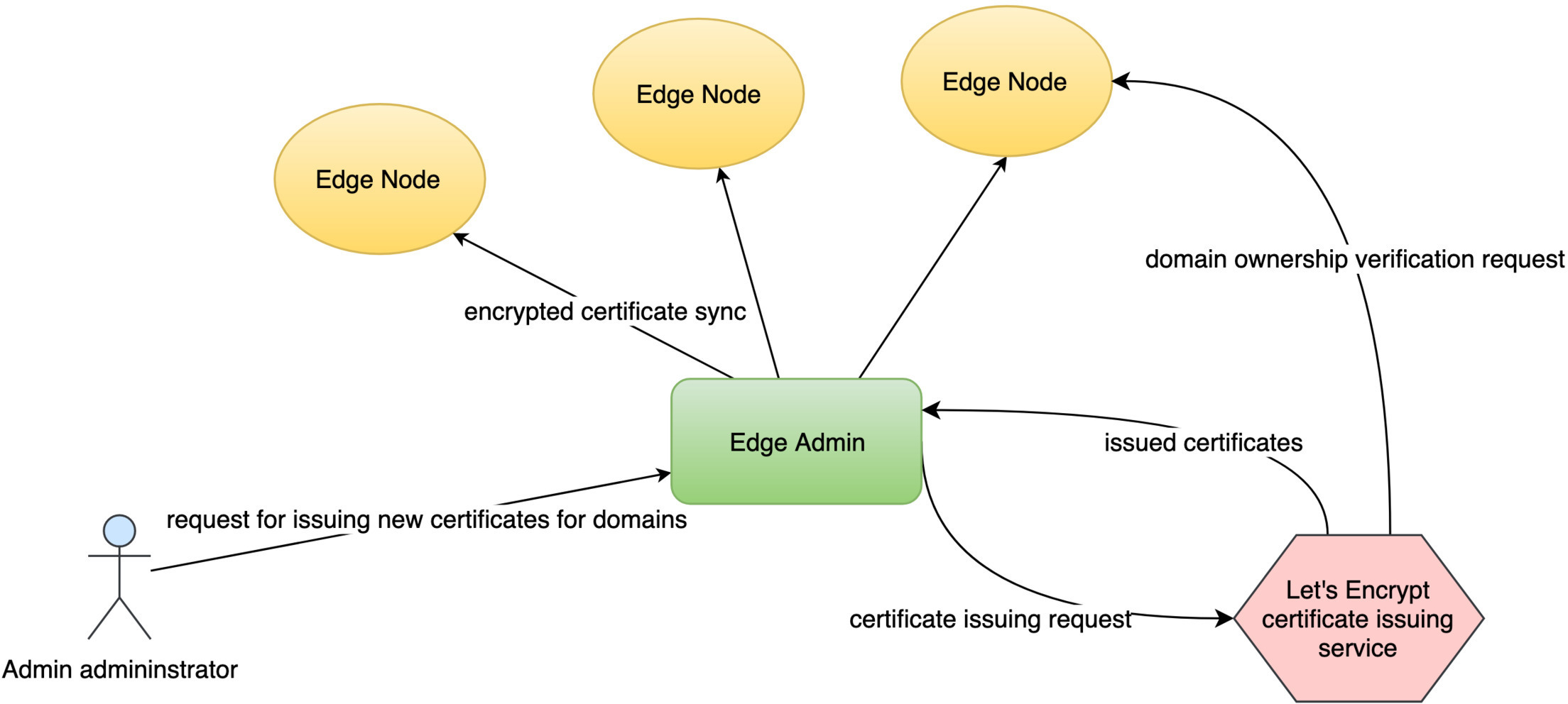
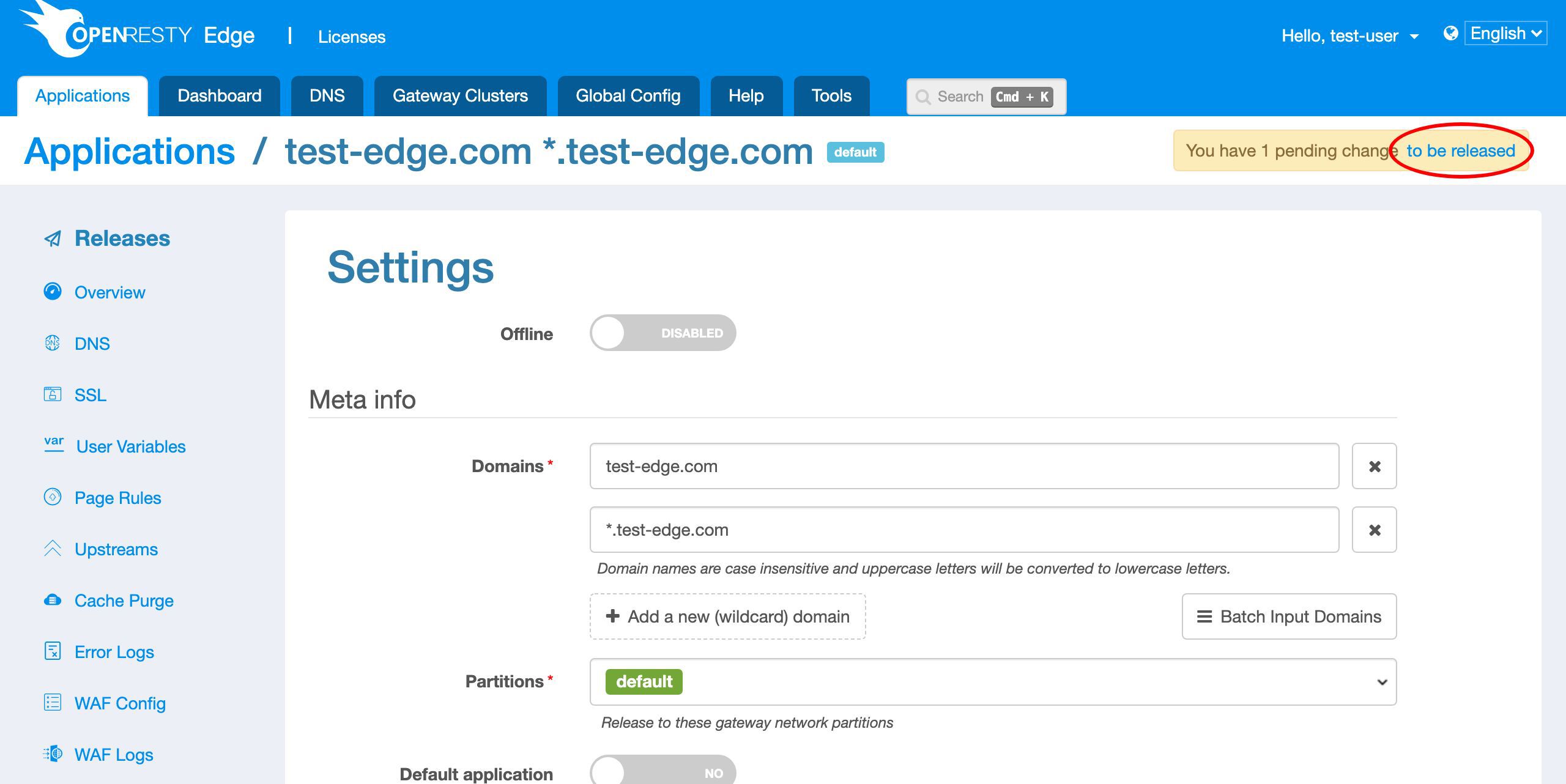
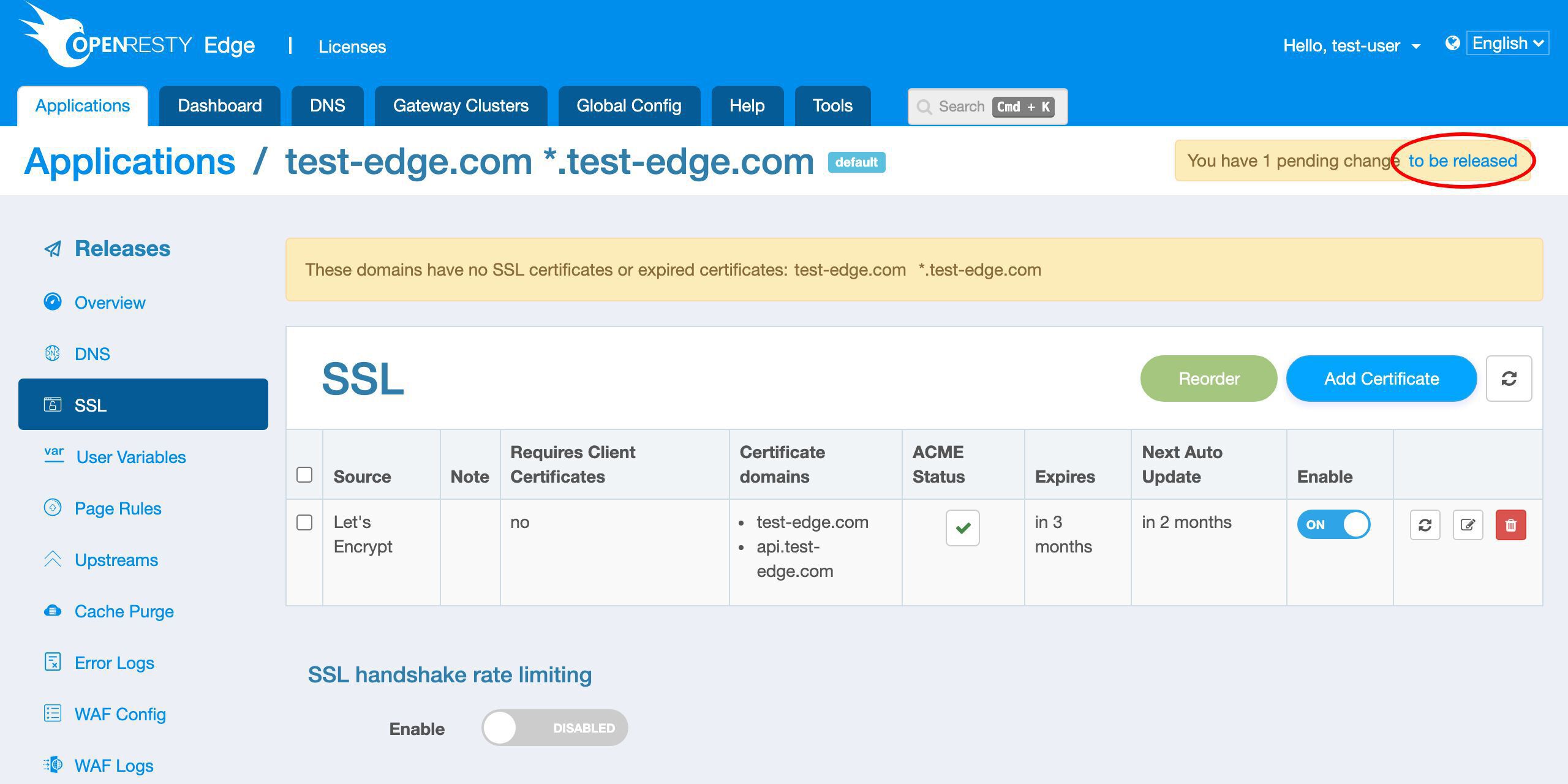
次に、ゲートウェイサーバーにプッシュします。Let’s Encrypt サーバーがドメインの所有権を確認する必要があるためです。
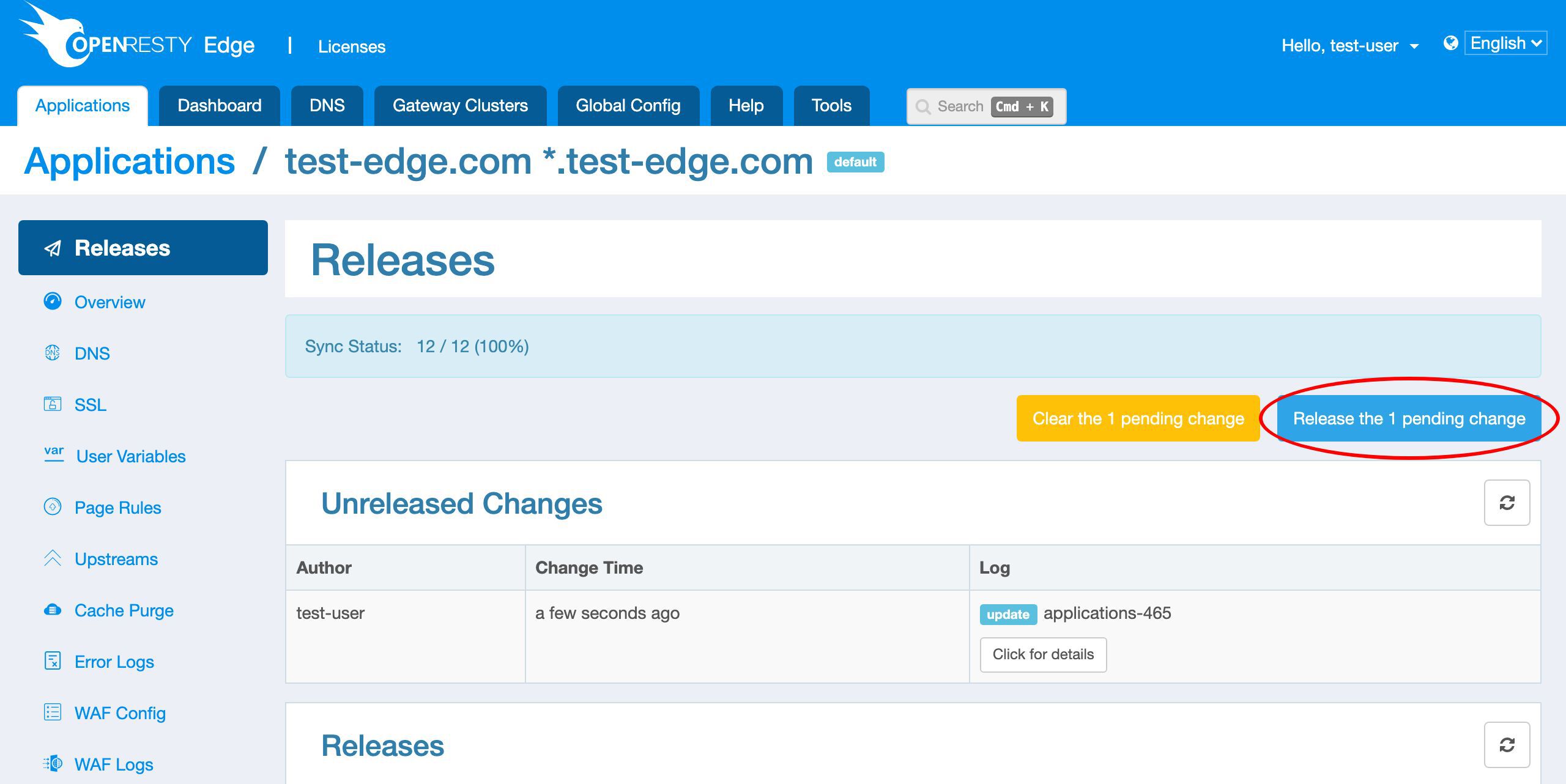
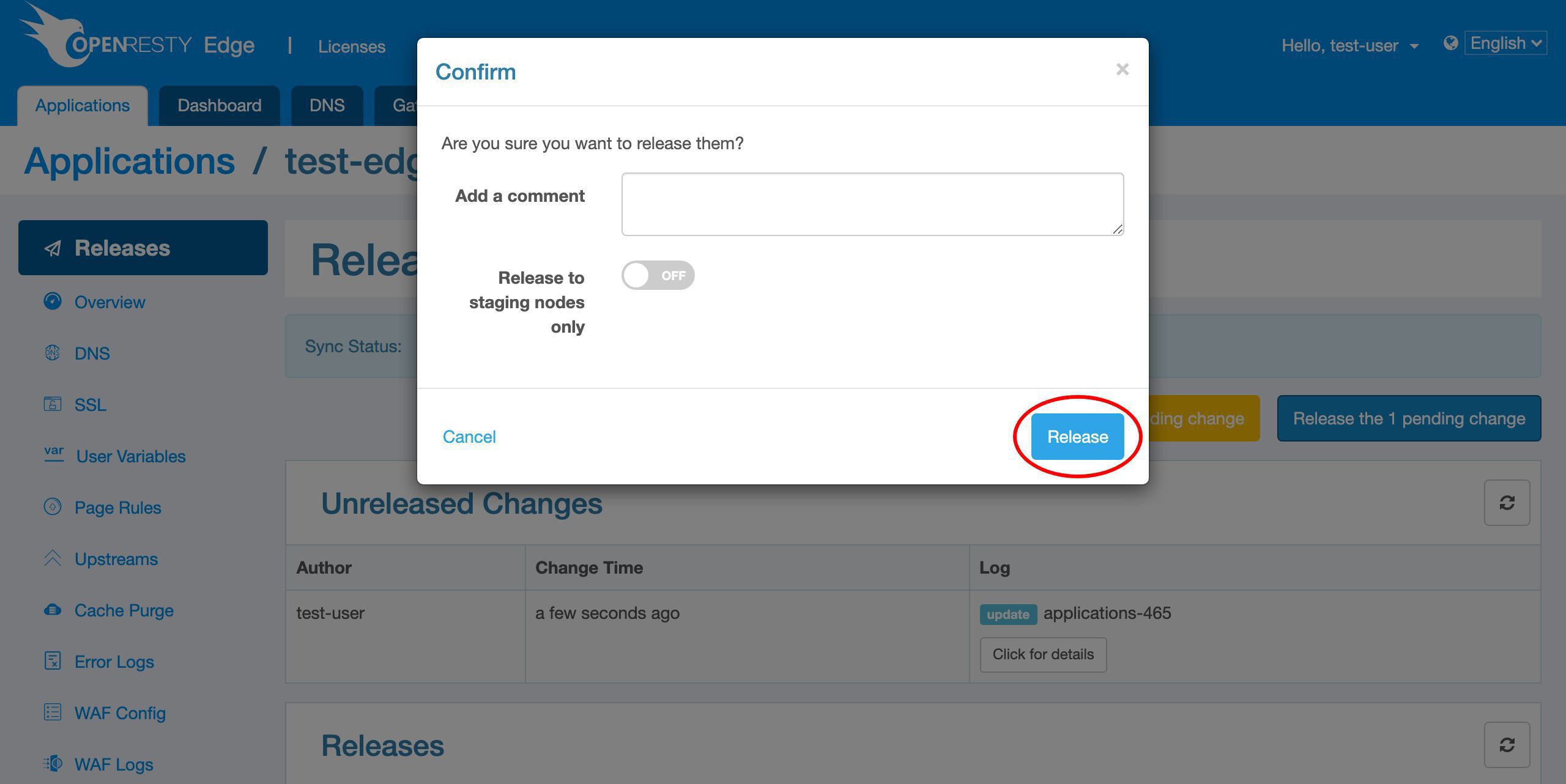
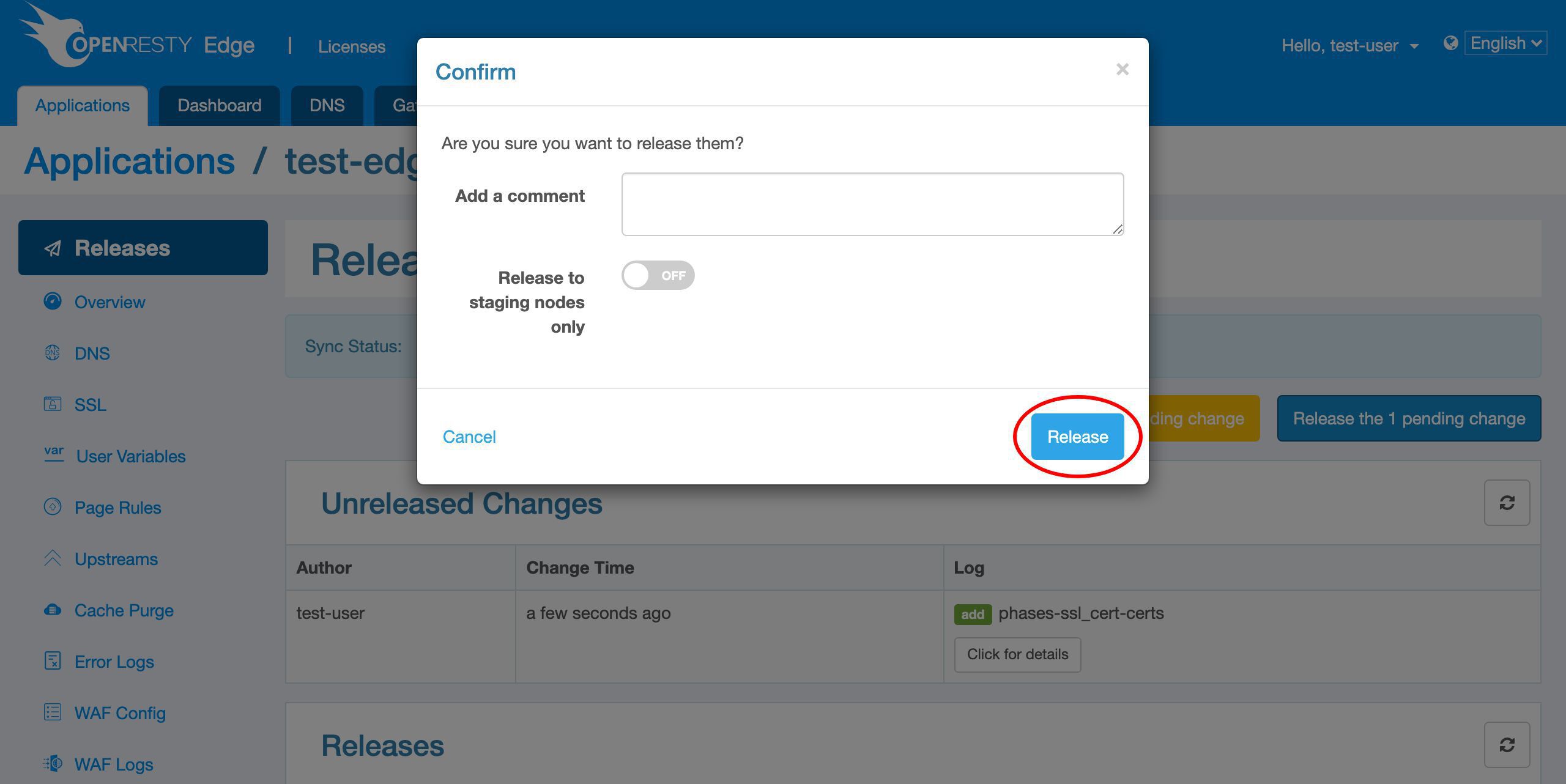
変更をリリースします。
リリースします!
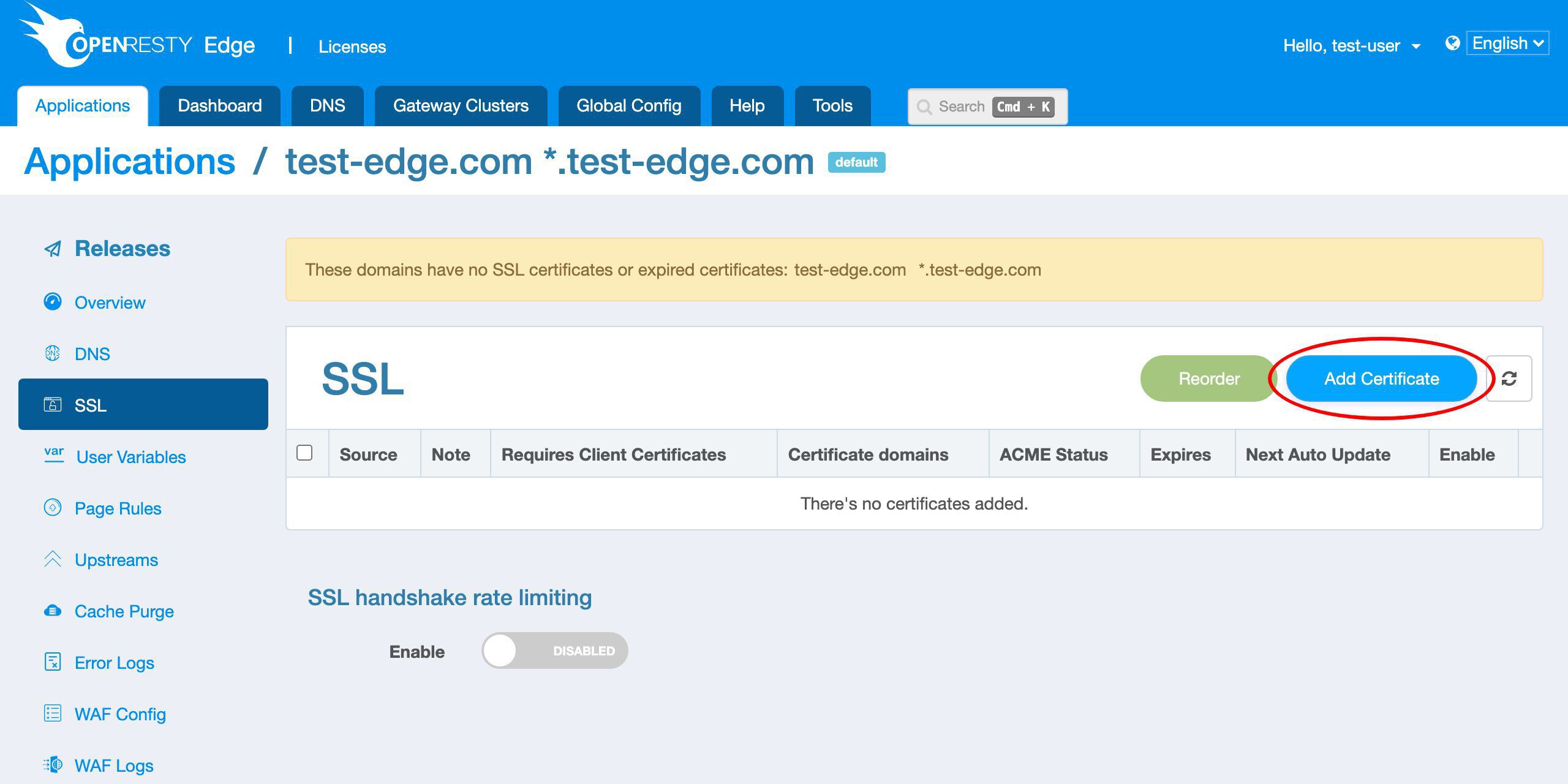
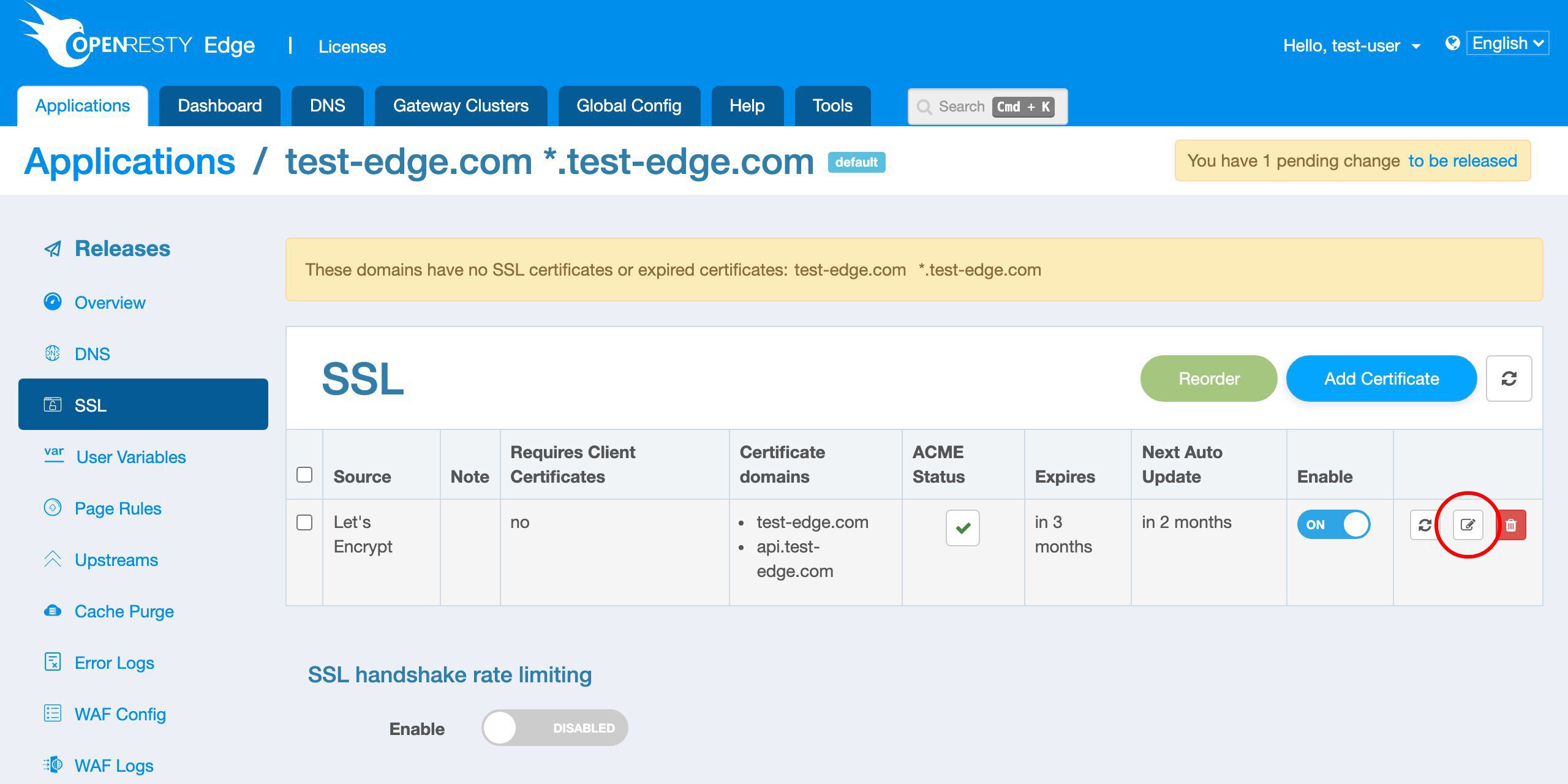
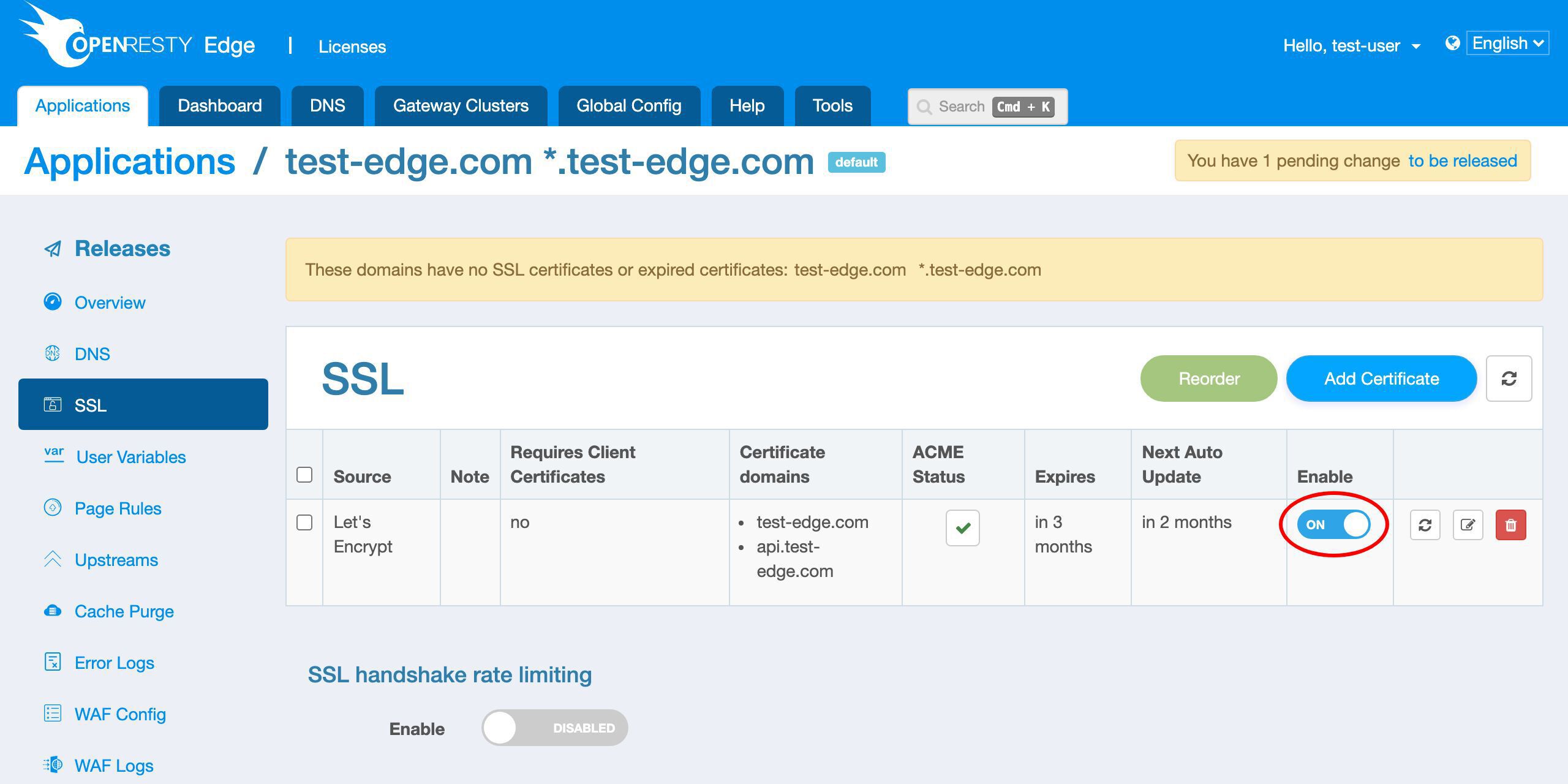
SSL 証明書を追加する
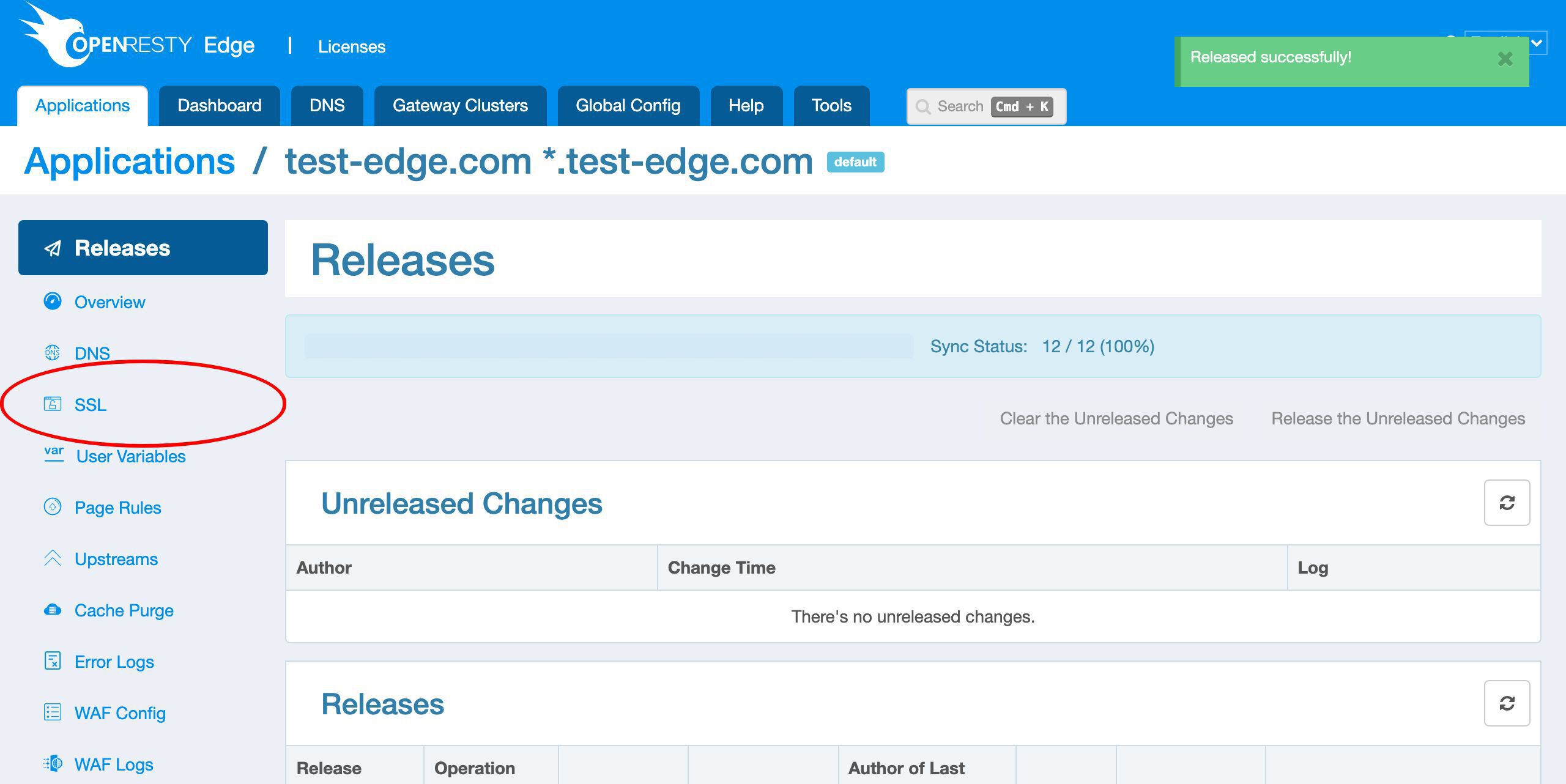
SSL ページに移動します。
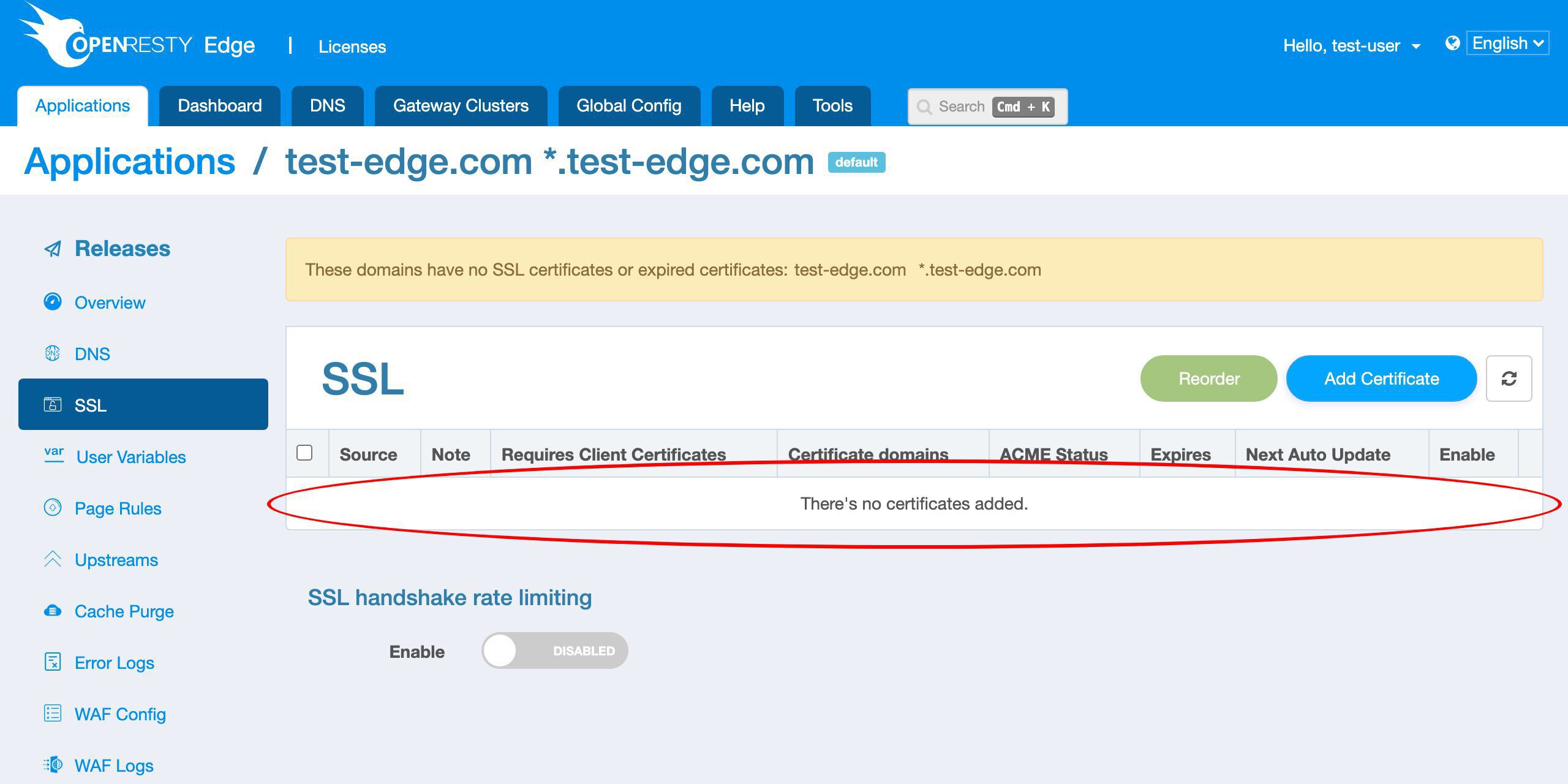
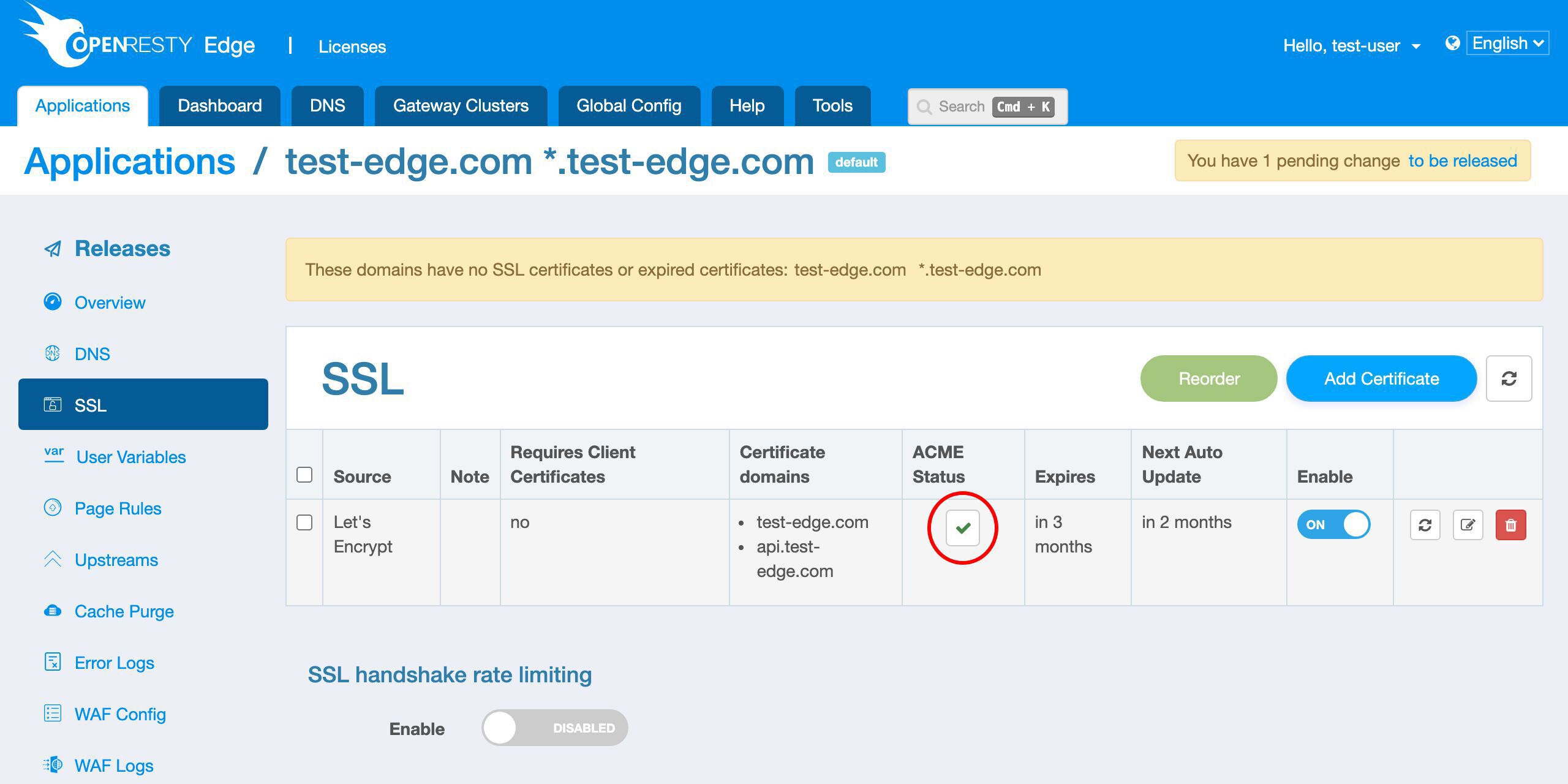
現時点では SSL 証明書が定義されていないことがわかります。
新しい証明書を追加しましょう。
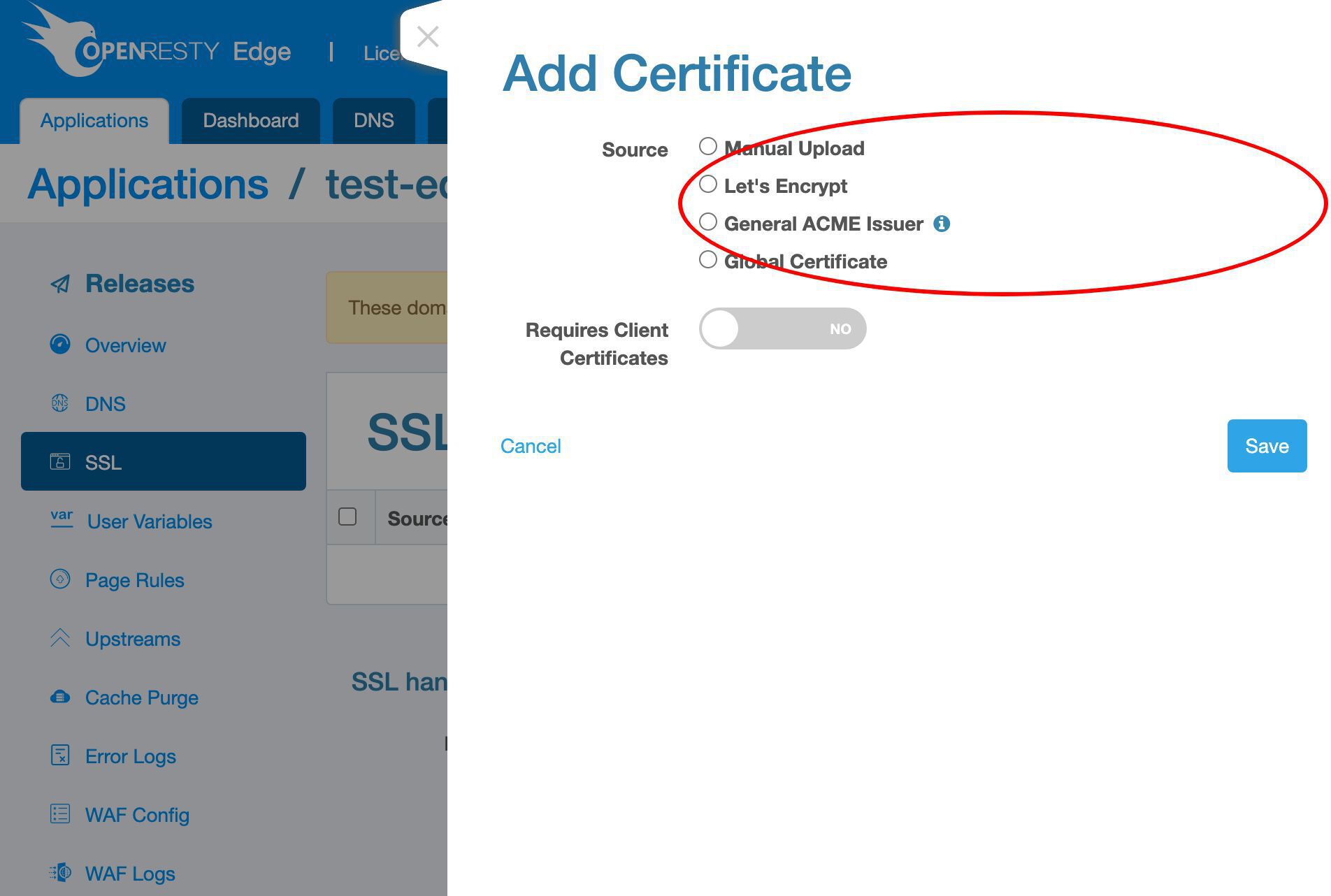
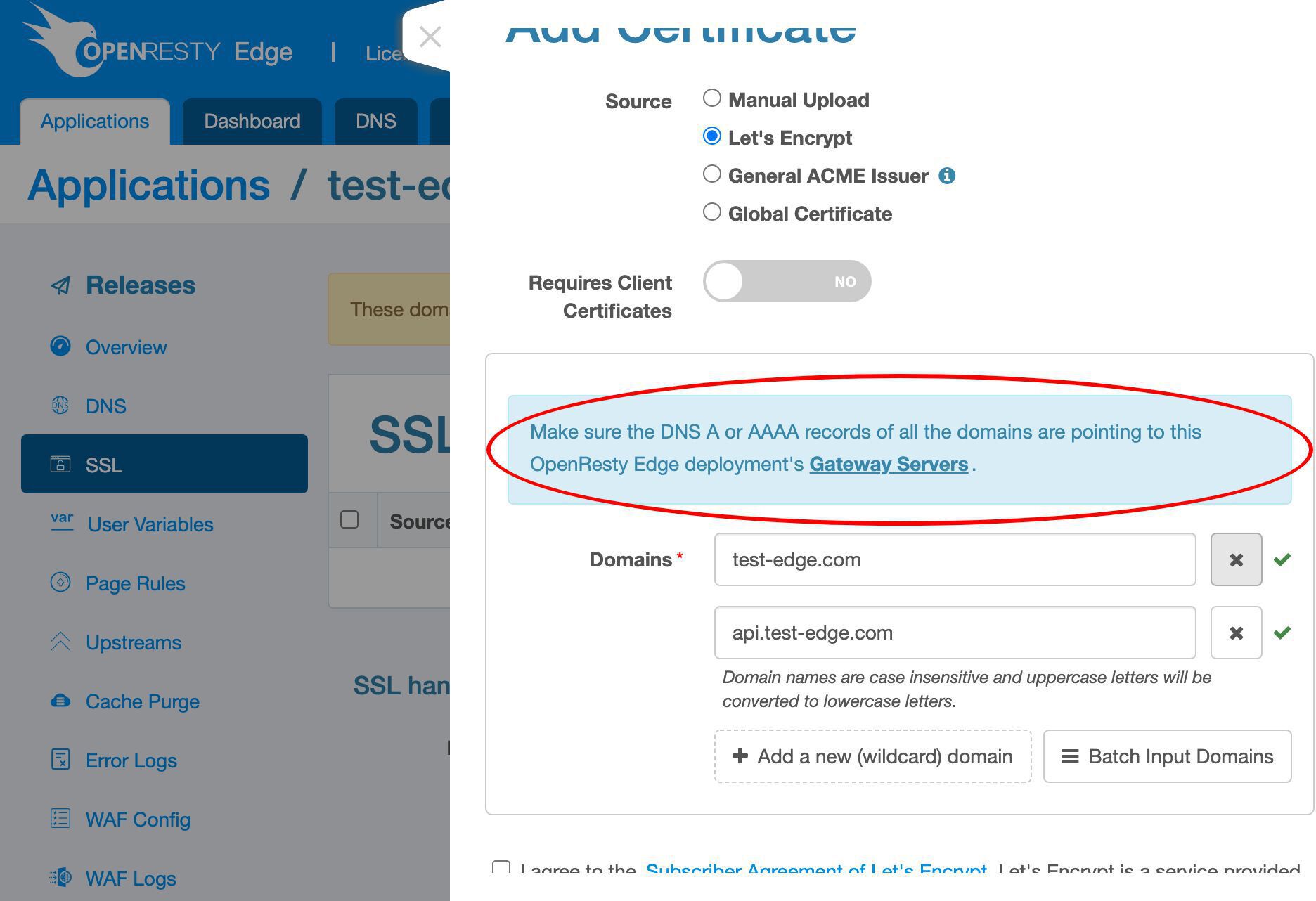
新しい SSL 証明書を発行するためのさまざまな方法をサポートしています。
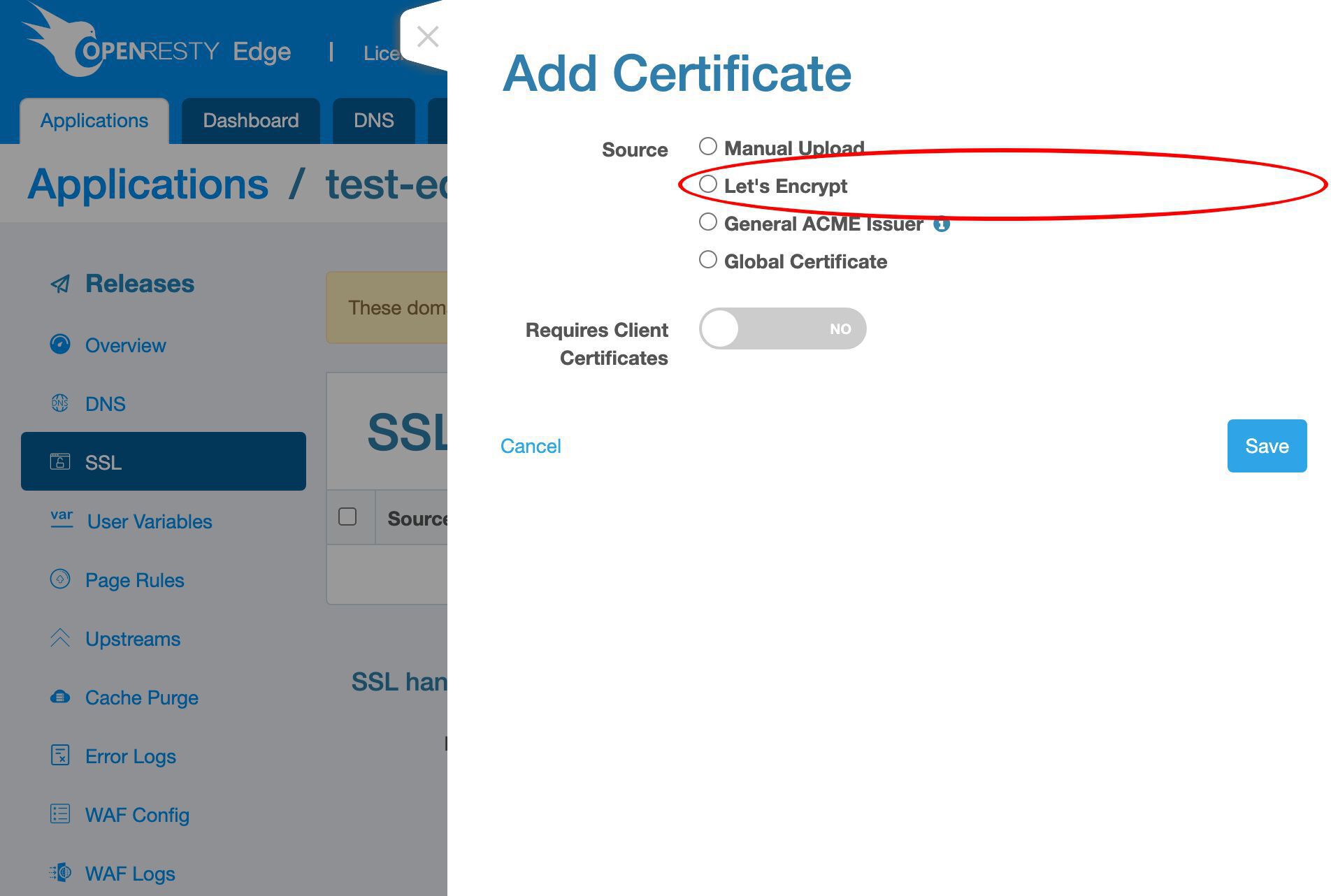
ここでは Let’s Encrypt の方法のみをデモンストレーションします。
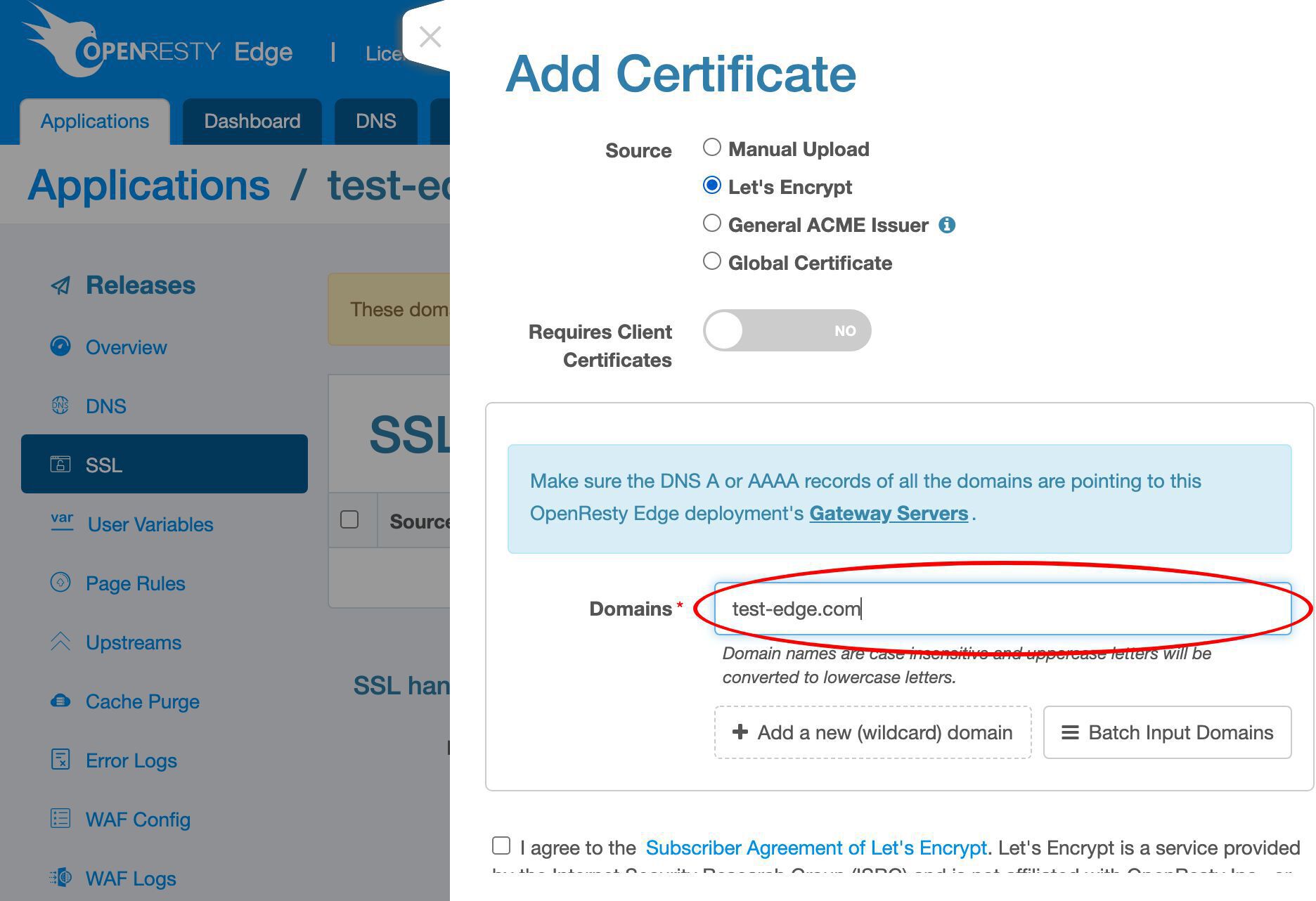
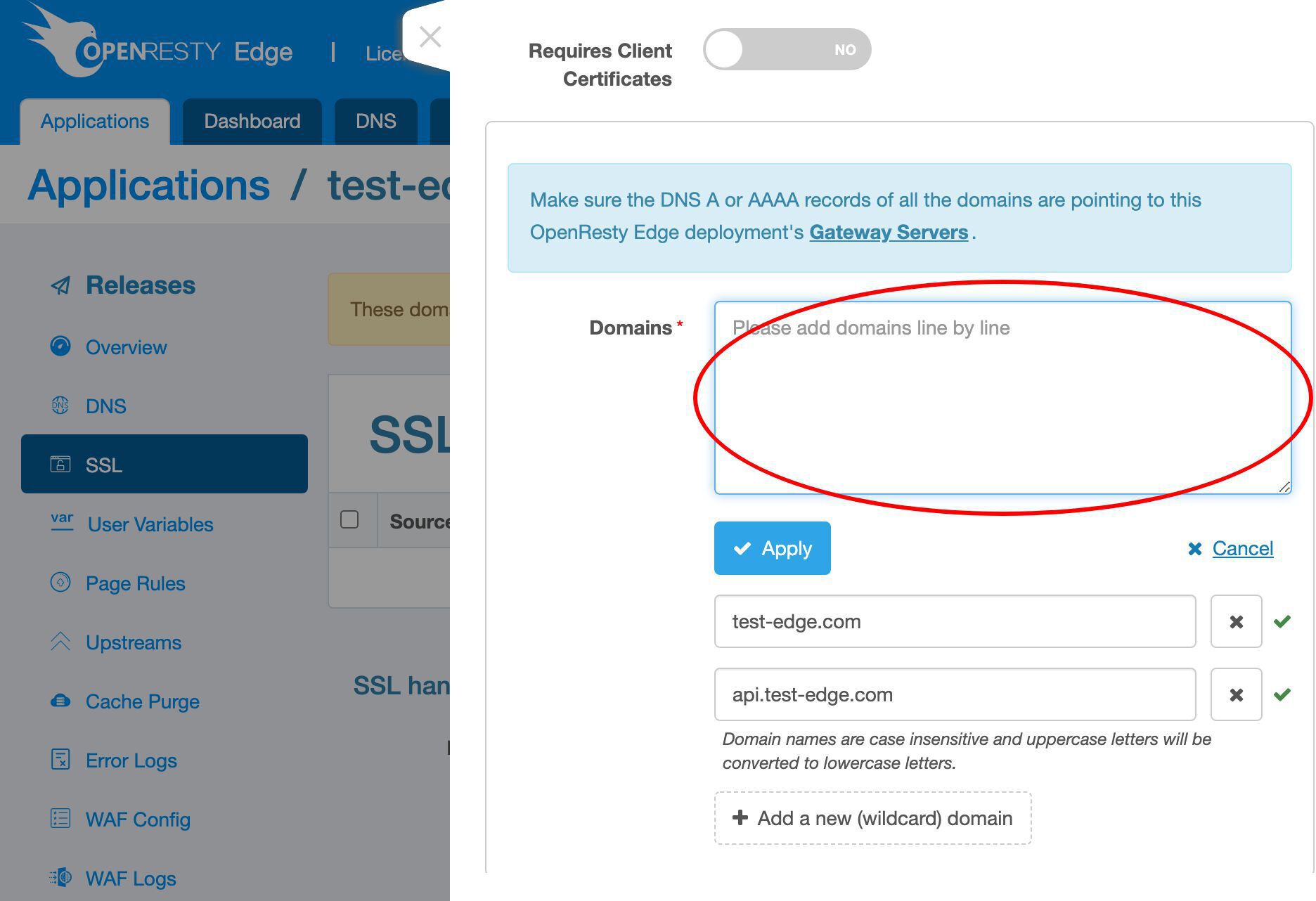
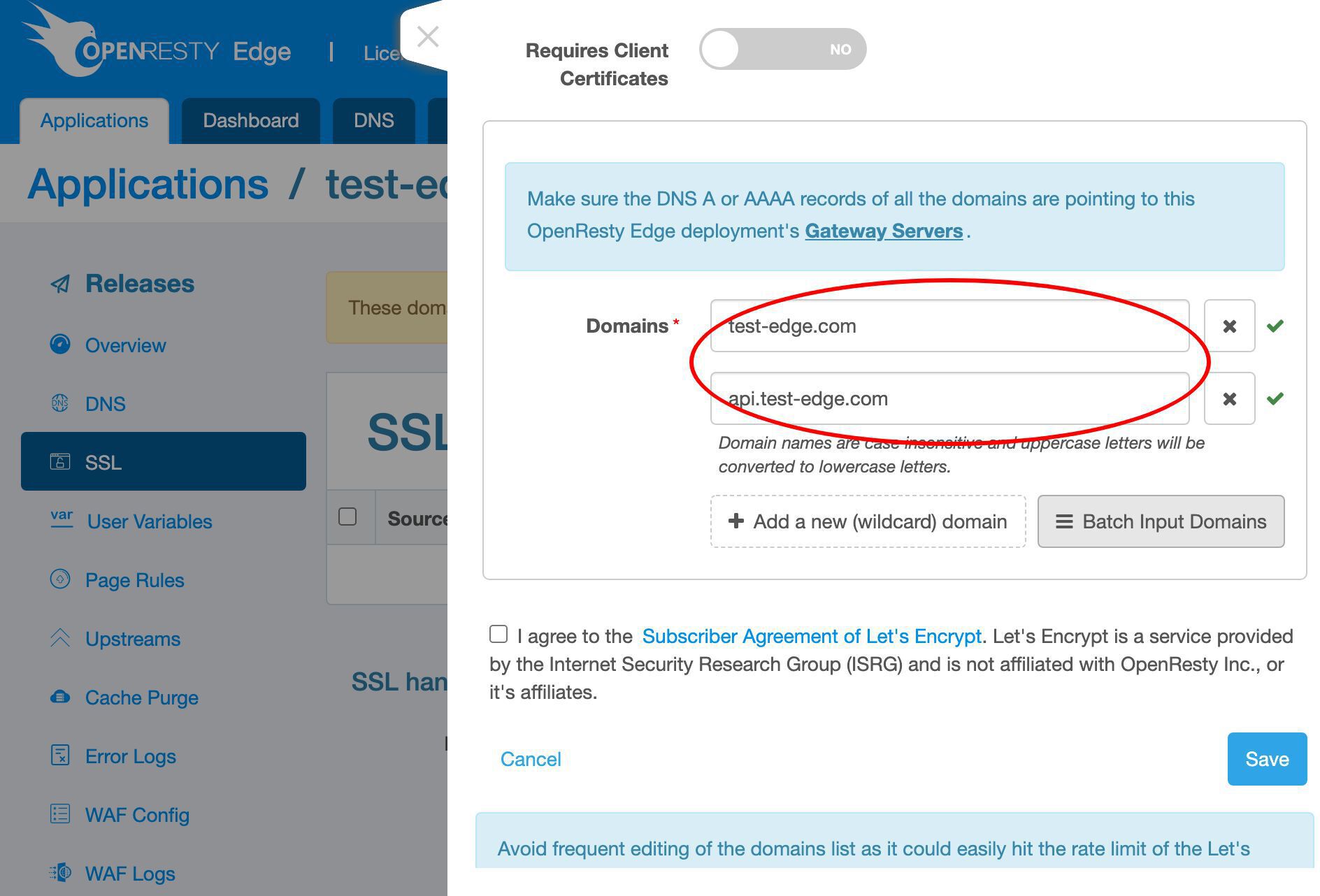
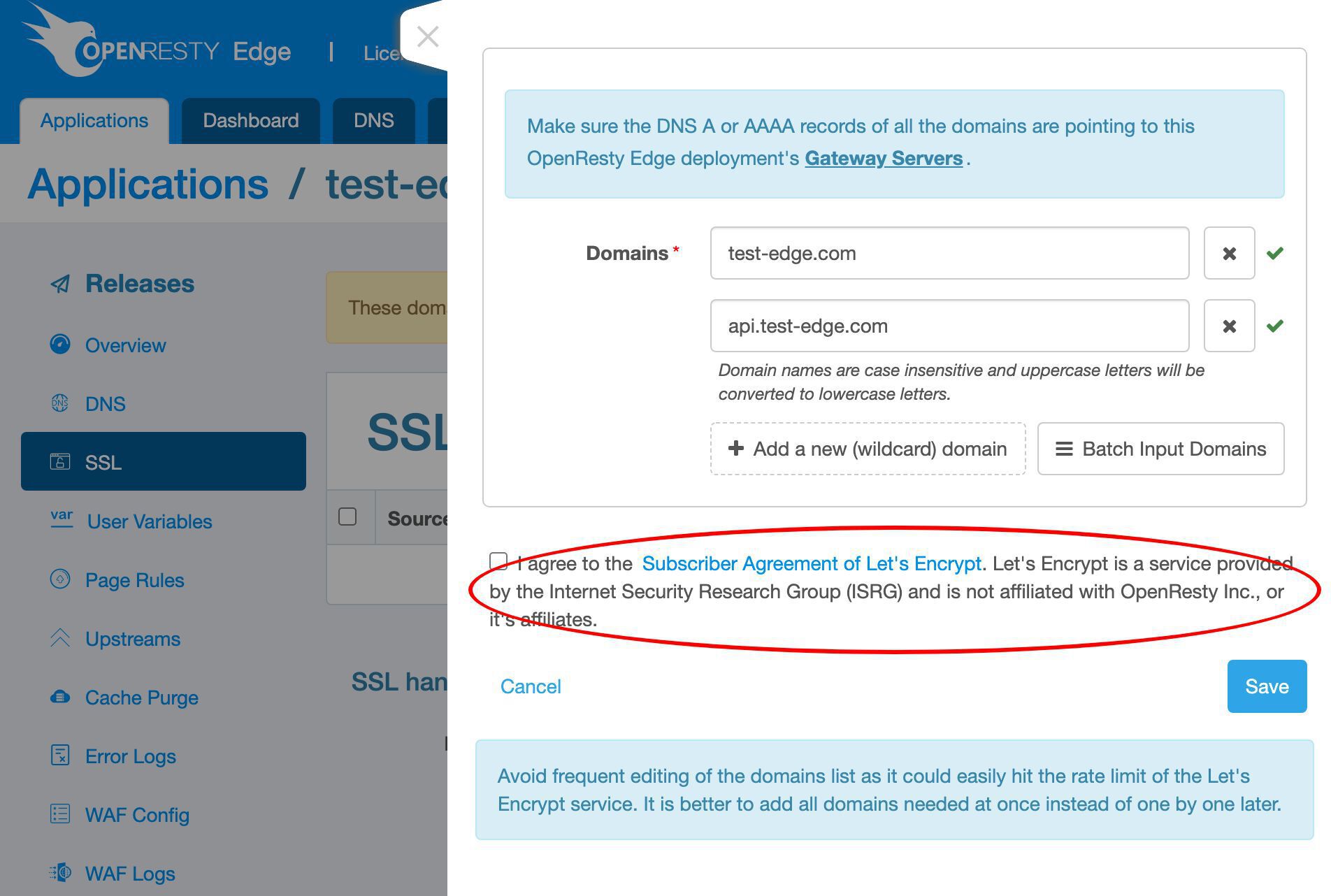
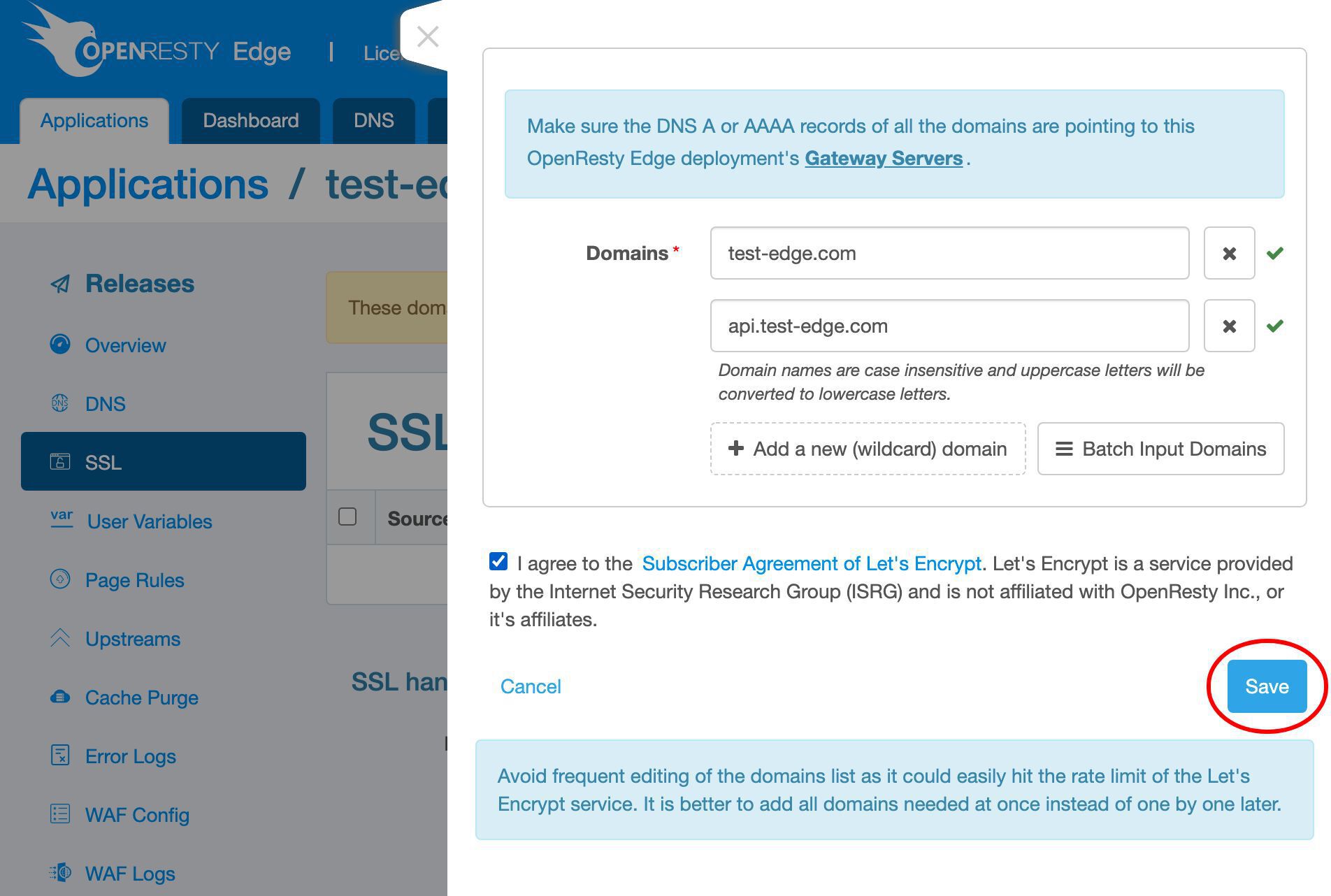
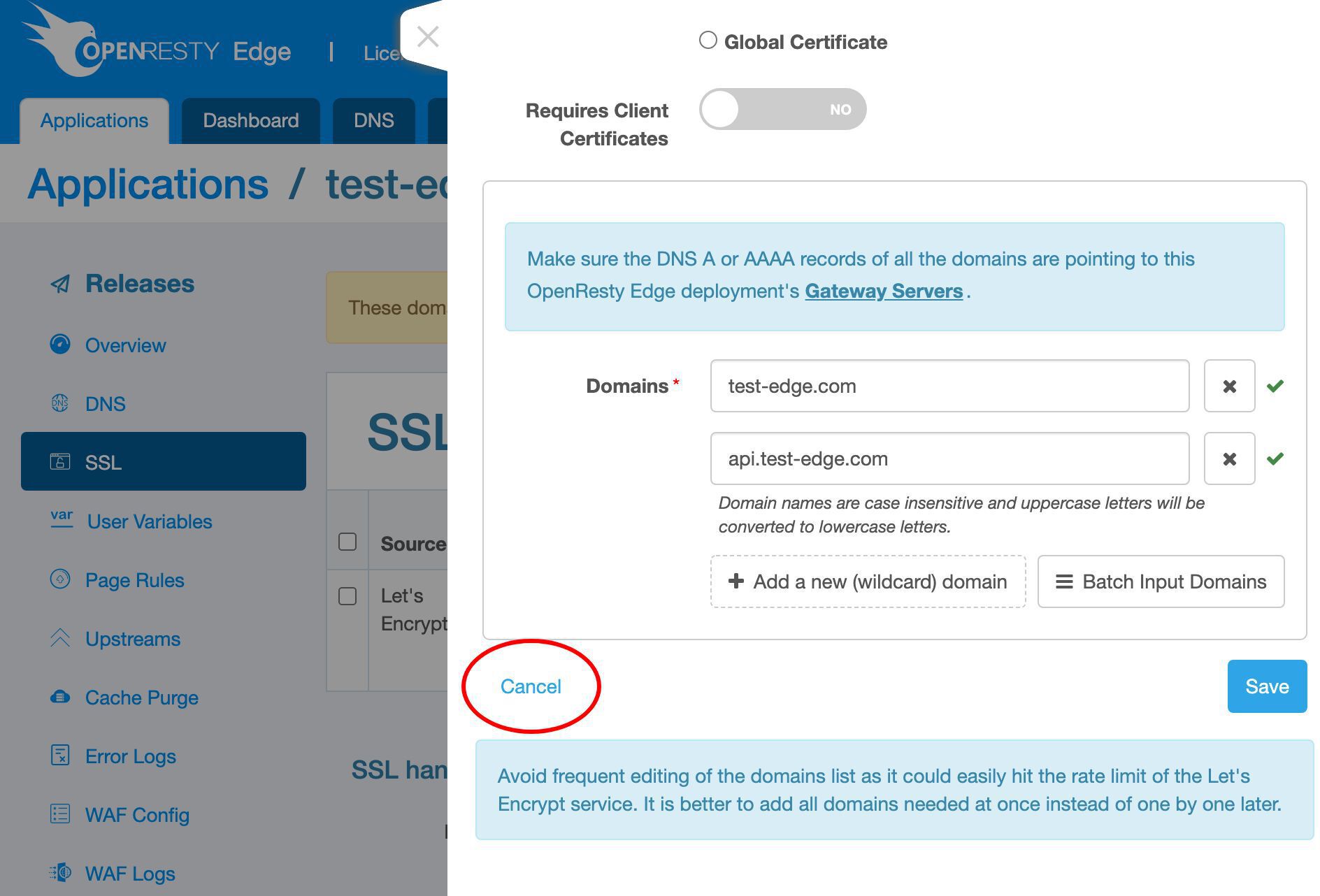
トップレベルドメイン test-edge.com をこの証明書に追加します。
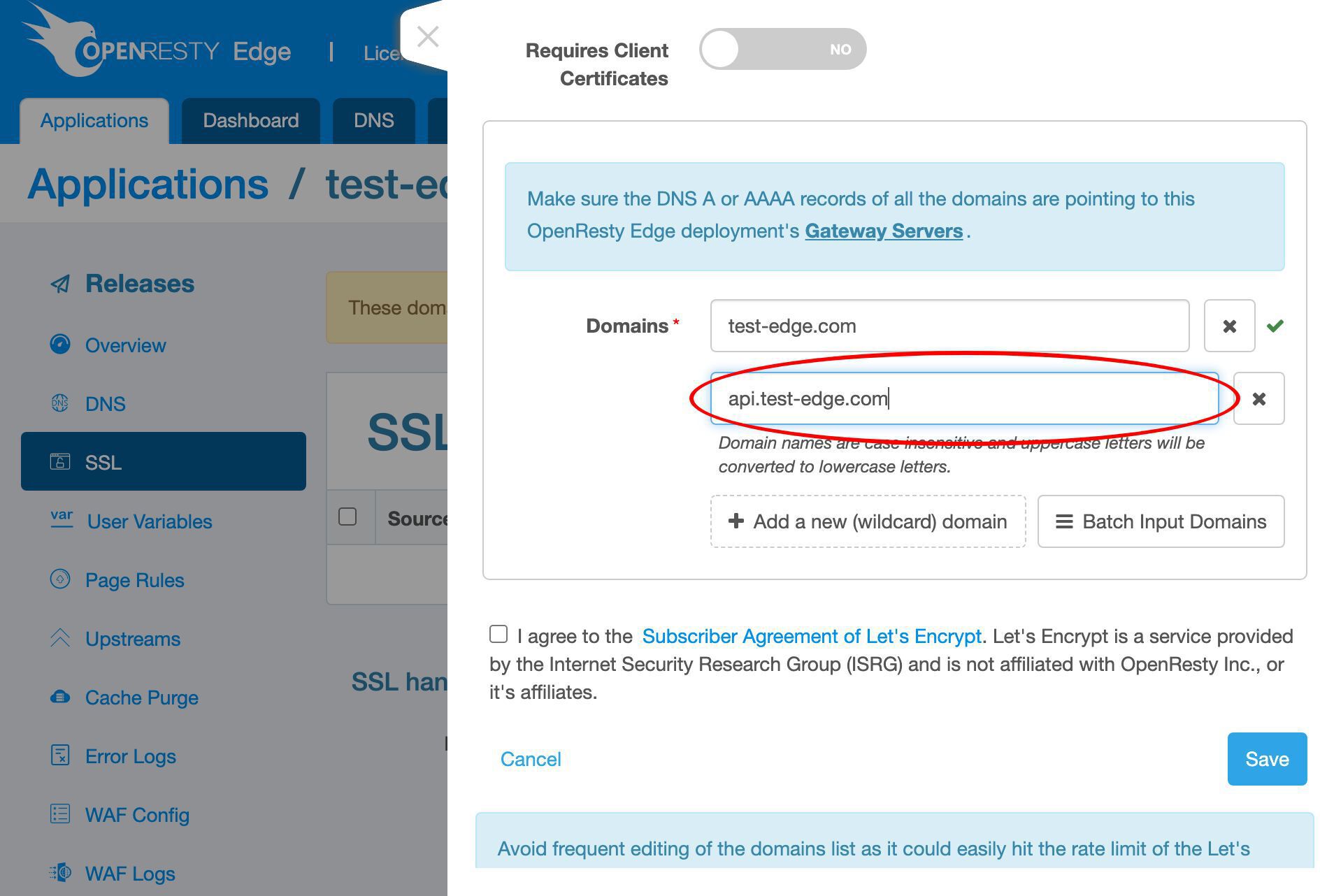
さらにサブドメイン名を追加します。
api サブドメインを入力します。これは何でも構いません。
さらにサブドメインを追加することもできます。
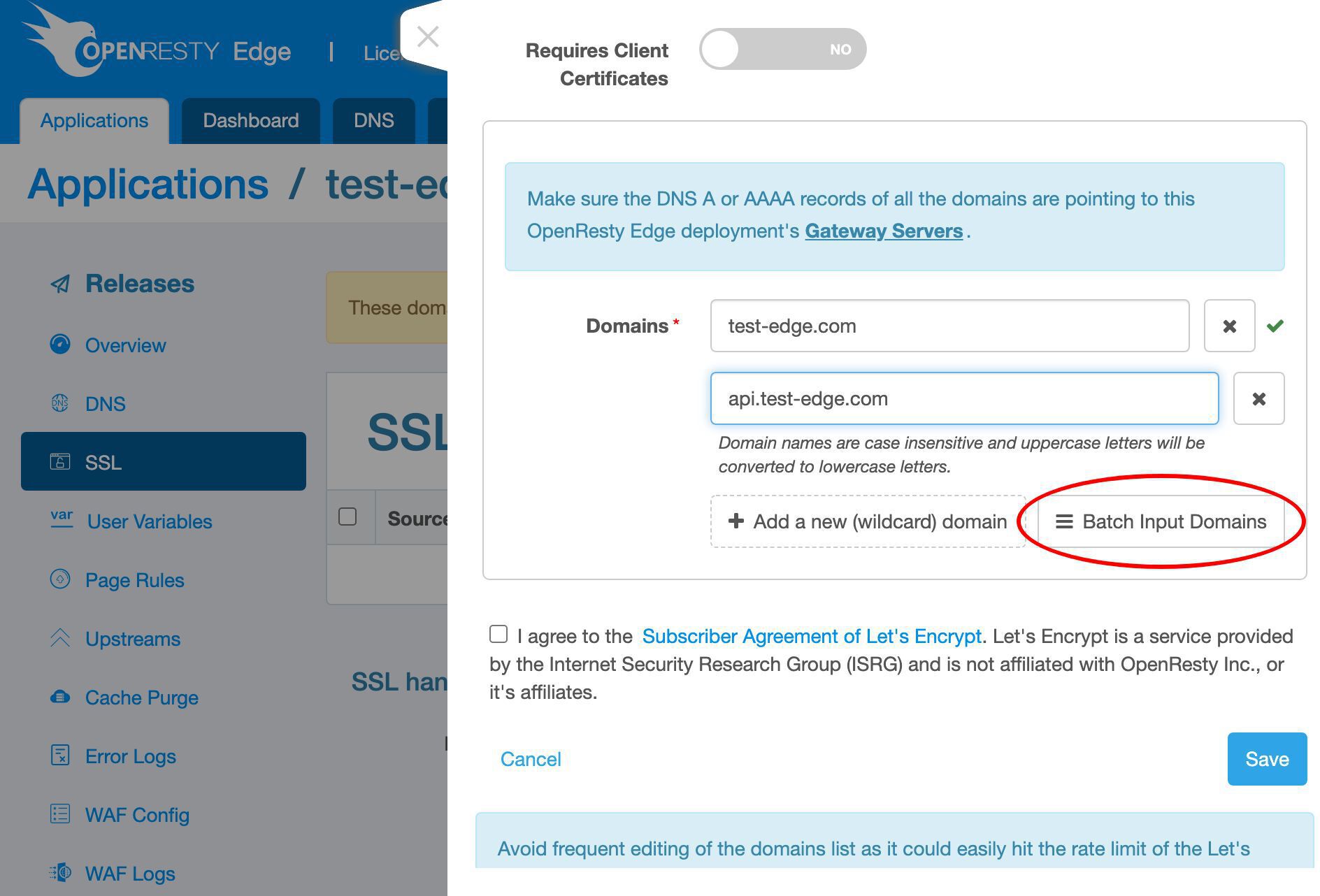
多数のドメインがある場合は、一括入力モードを使用することもできます。
ここで必要なドメイン名を 1 行ずつ入力できます。
一括入力モードを終了します。
ここにあるすべてのドメインは、この OpenResty Edge デプロイメントのゲートウェイサーバーに解決される必要があります。
この要件についてもここで言及されています。
ターミナルでは、dig コマンドを使用してドメインがゲートウェイサーバーに解決されているかどうかをテストできます。
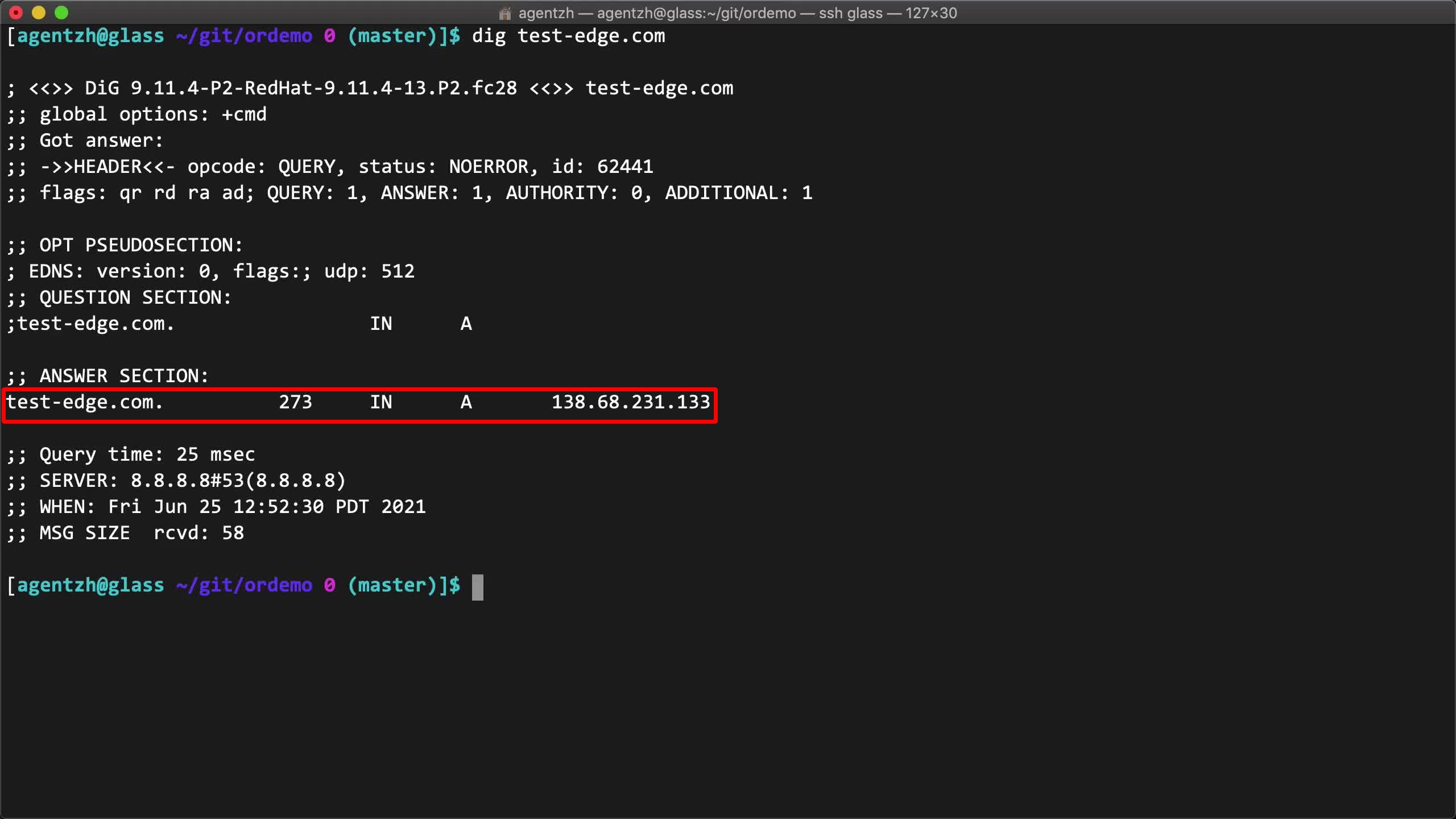
dig test-edge.com
有効な DNS 応答が表示されます。
api サブドメインもテストできます。
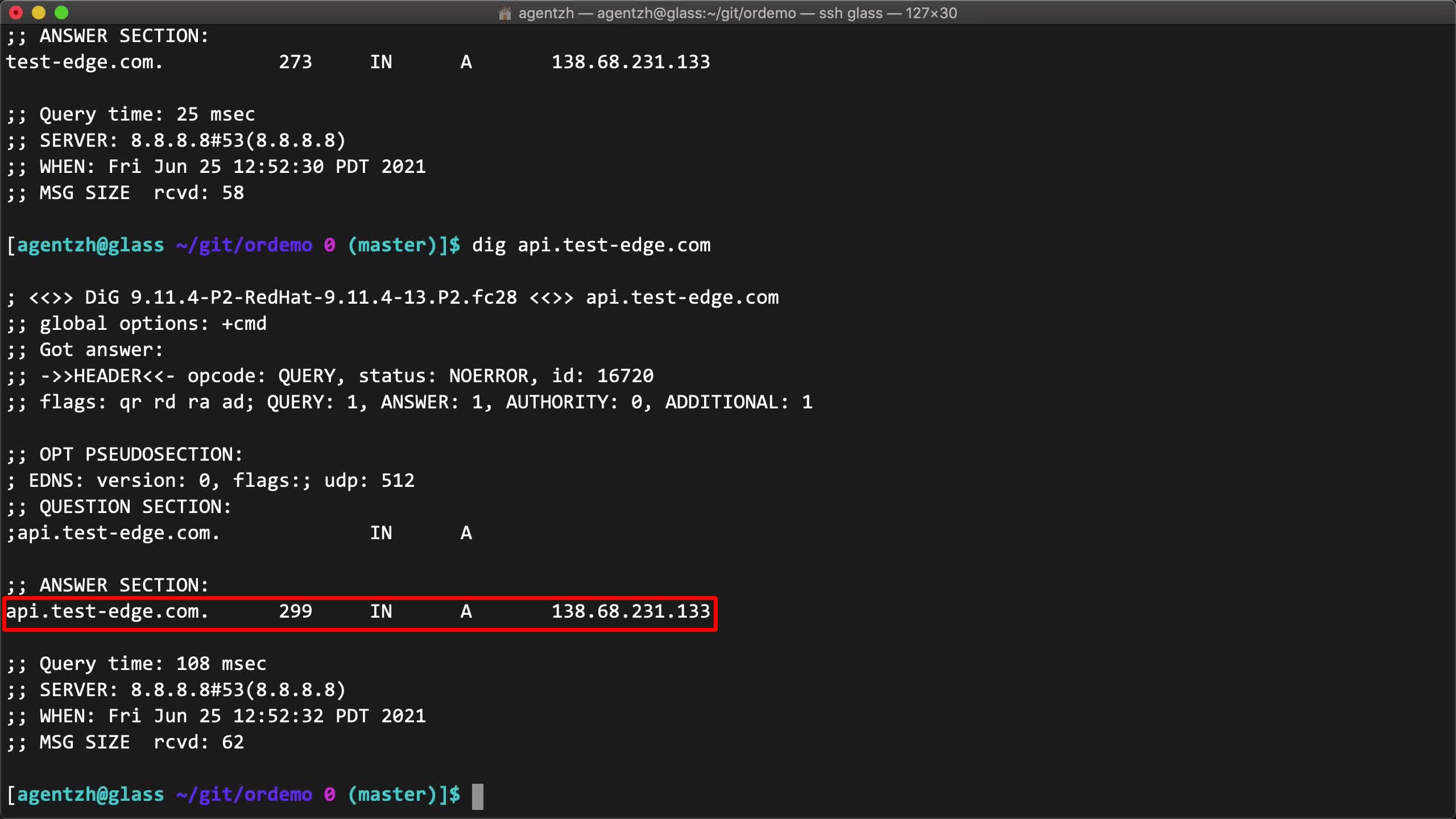
dig api.test-edge.com
同様に有効な DNS 応答が得られます。
Let’s Encrypt サーバーは、これらのドメインを通じてゲートウェイサーバーにアクセスする必要があります。これは、私たちが実際にこれらのドメインを所有していることを確認する必要があるためです。
ワイルドカードドメインの場合、OpenResty Edge をドメインの権威 DNS ネームサーバーとして使用する必要もあります。
Let’s Encrypt 利用規約に同意します。
保存します。
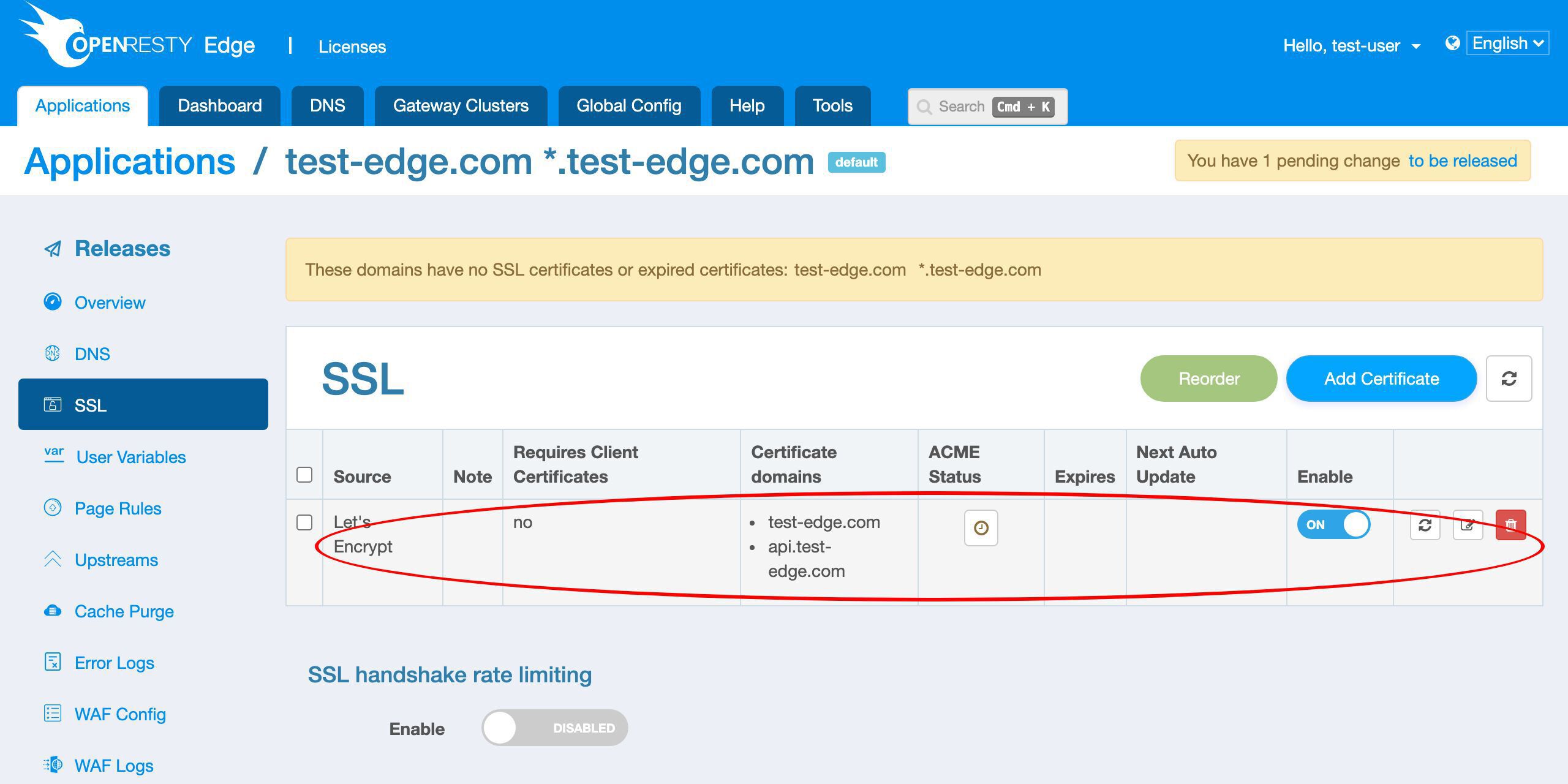
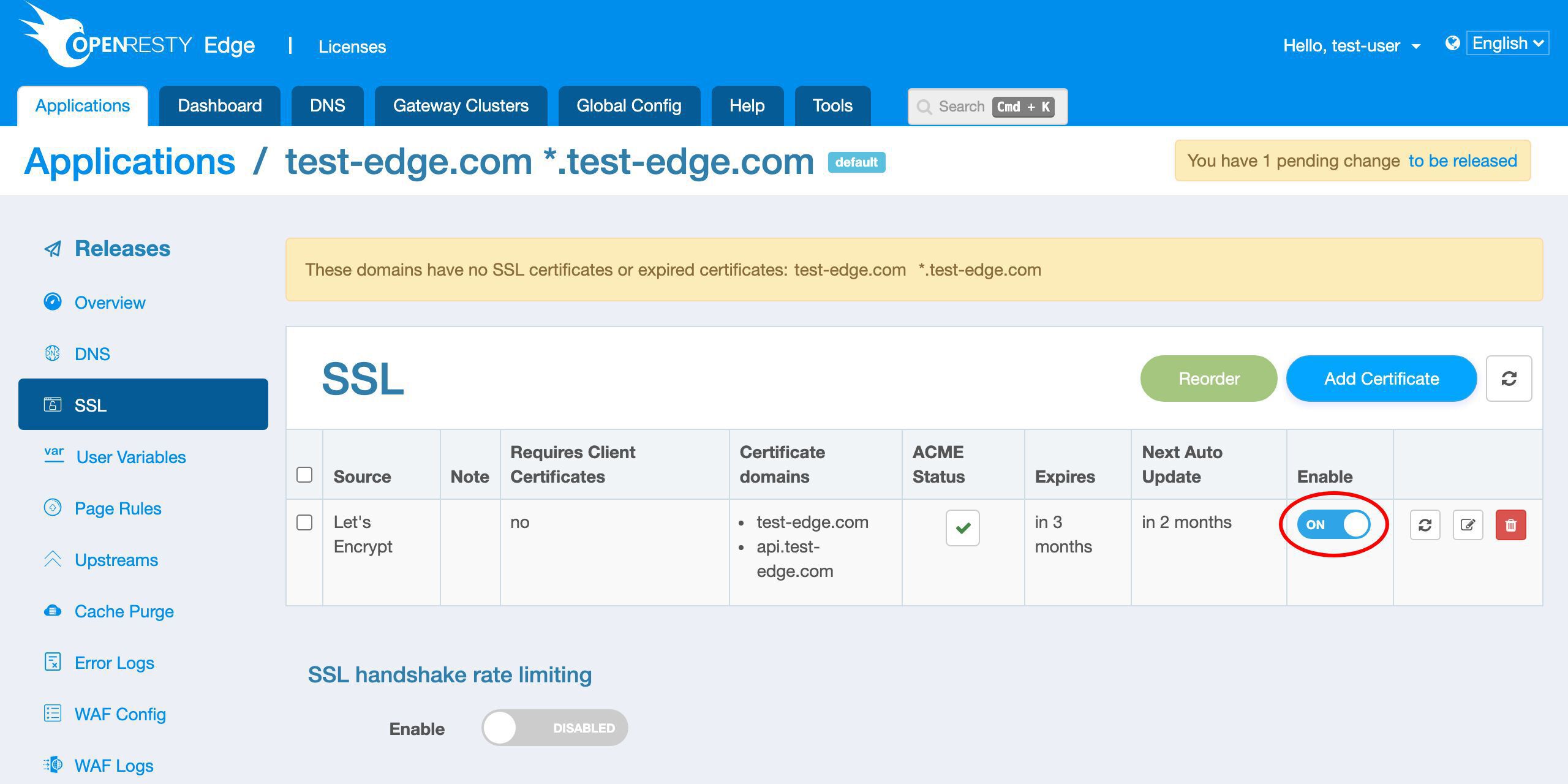
新しい Let’s Encrypt 証明書が表示されます。
証明書の発行元は Let’s Encrypt です。
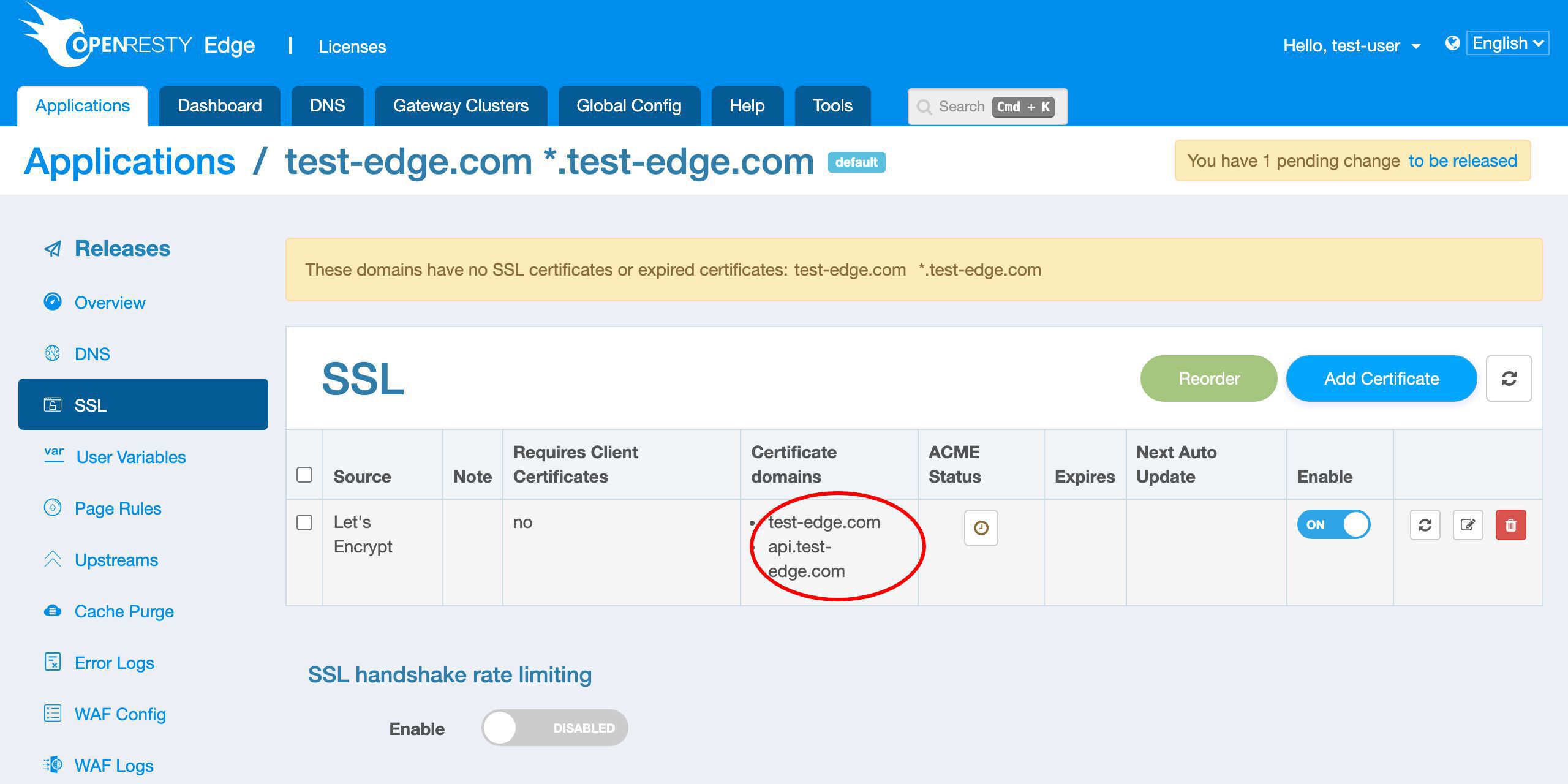
予想通り、2 つのドメインがあります。
ここでリアルタイムのステータスを確認できます。
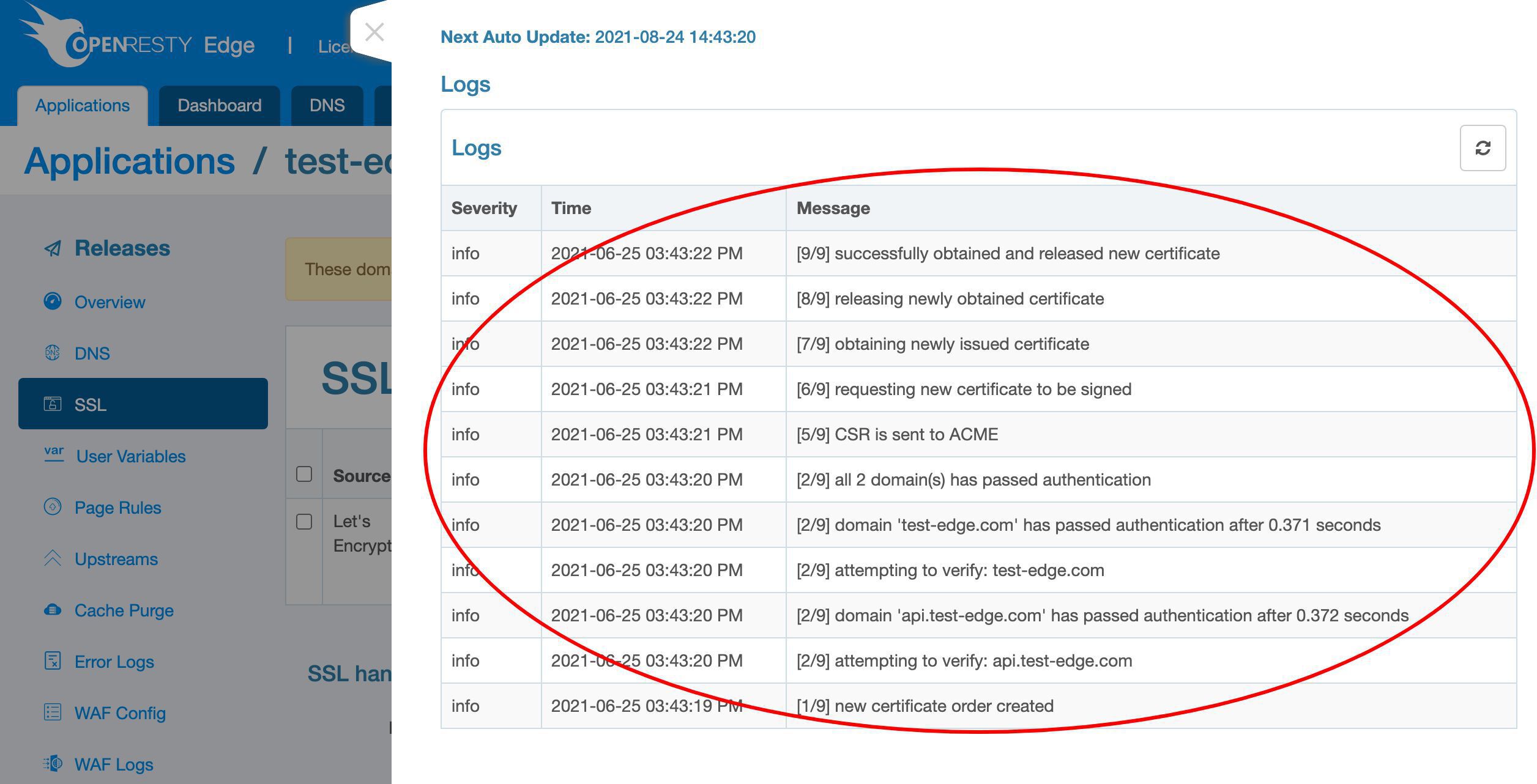
このステータスアイコンをクリックして詳細な進捗状況を確認します。
Let’s Encrypt 証明書の発行プロセスに関する詳細なログもここで確認できます。
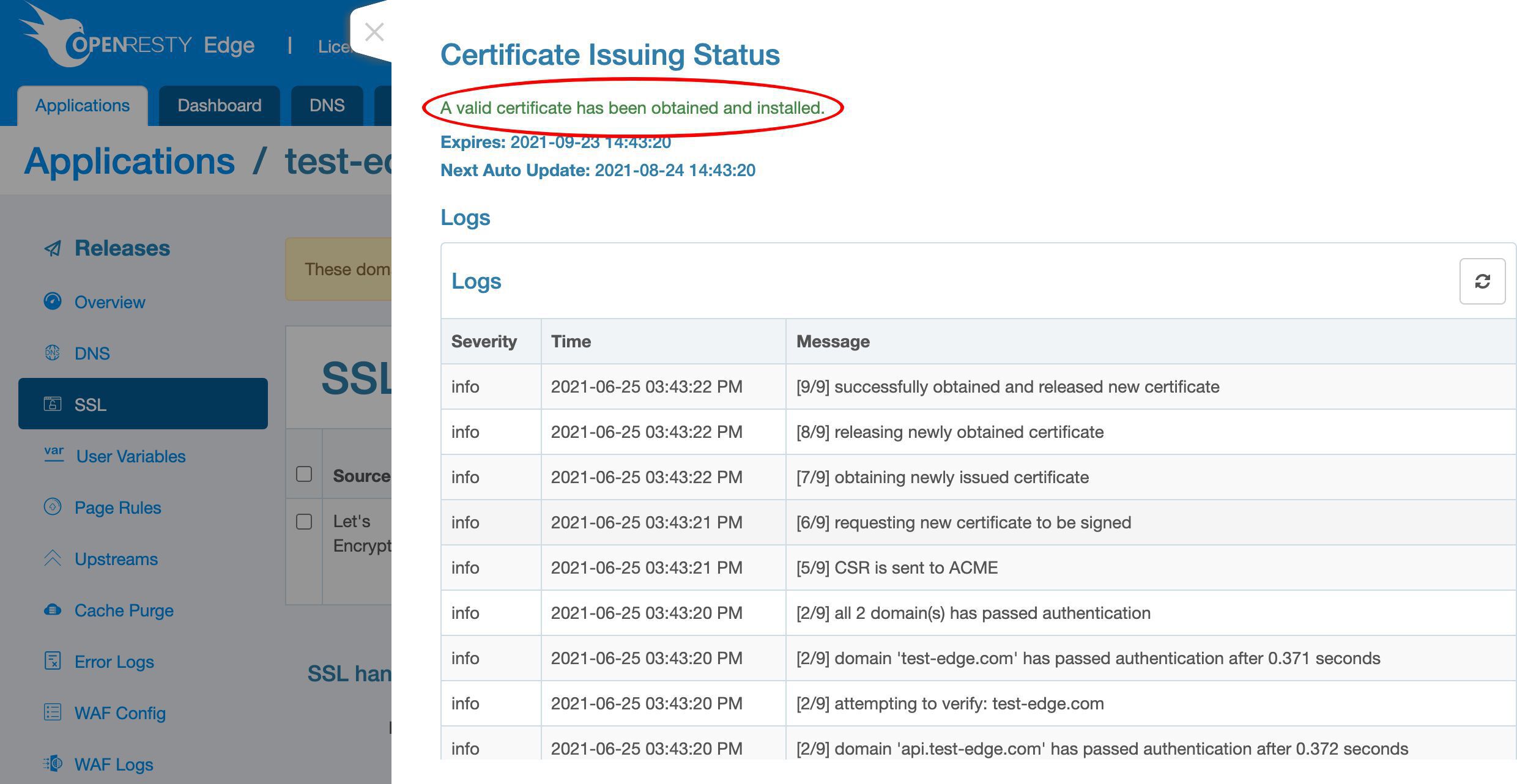
証明書が発行されたことが確認できます。
このステータスページを終了しましょう。
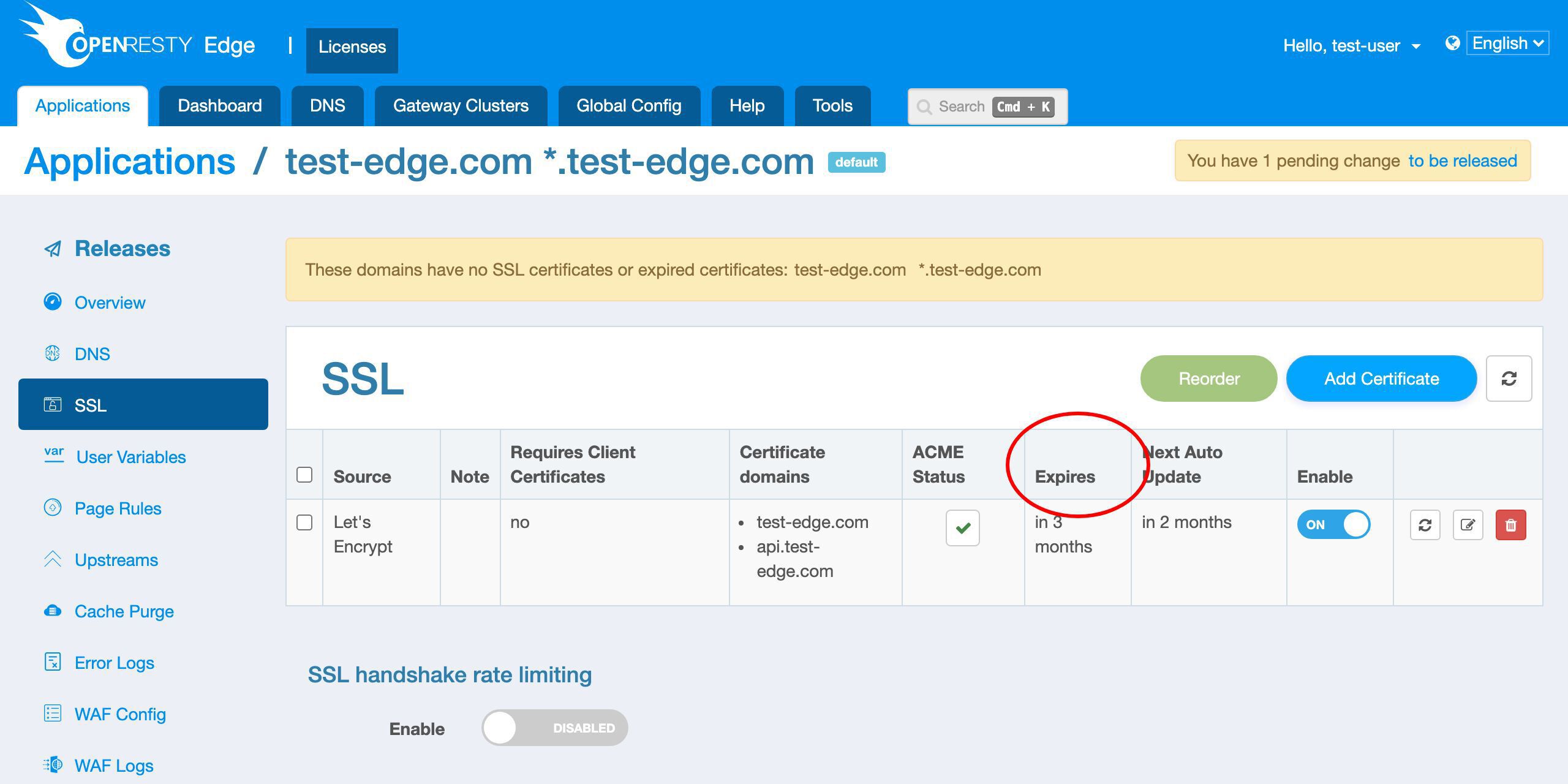
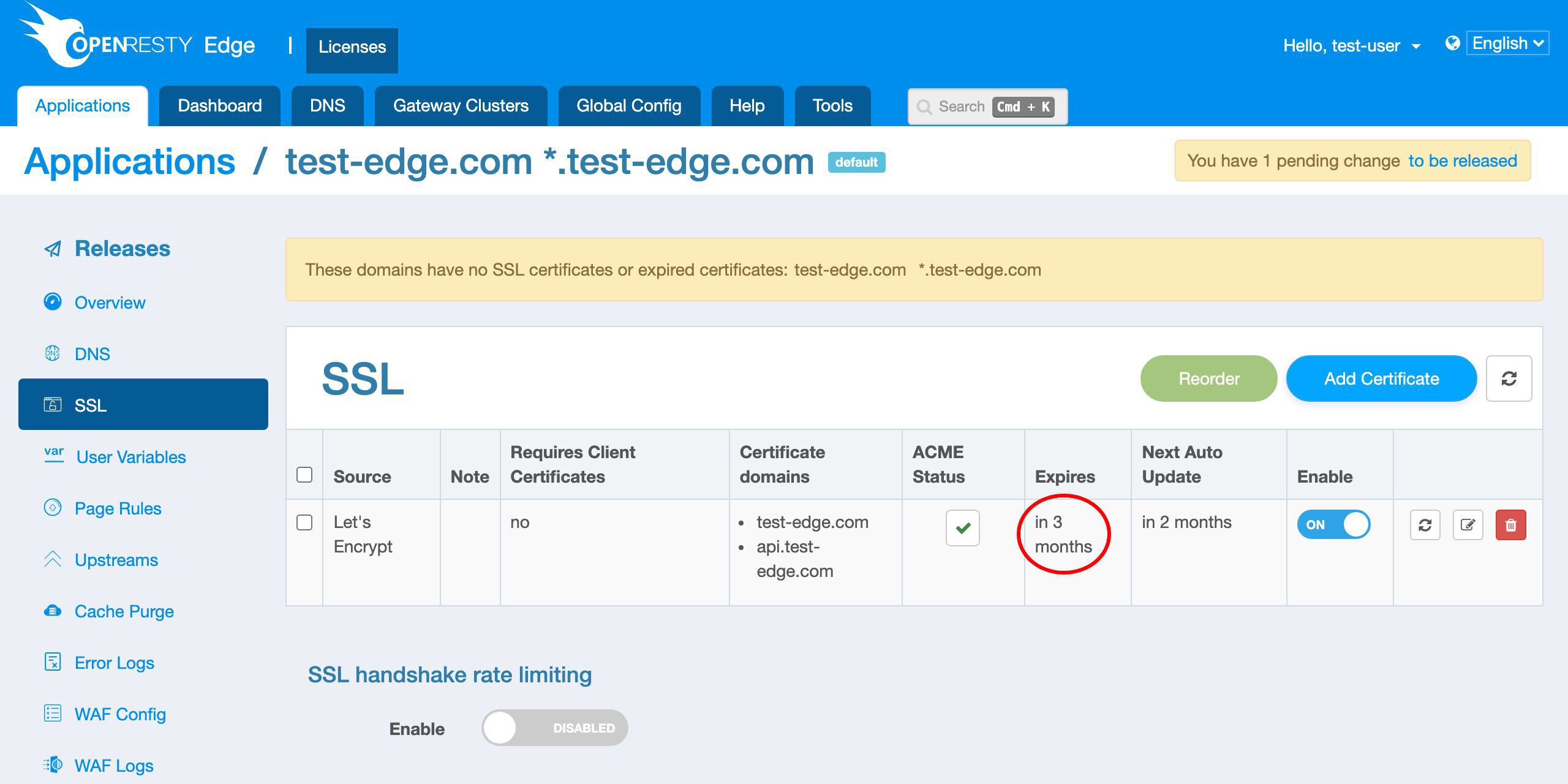
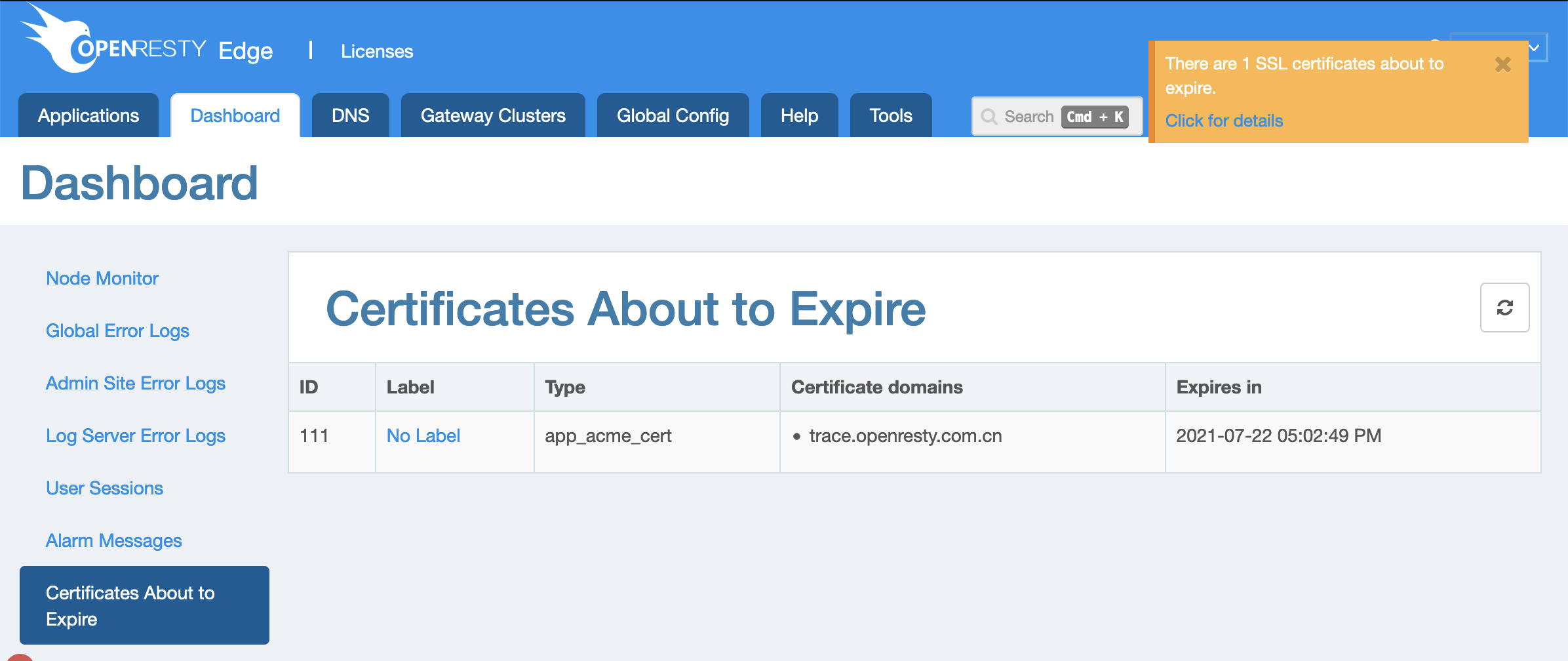
この列で新しい証明書の有効期限を確認できます。
この証明書は 3 ヶ月後に期限切れになります。
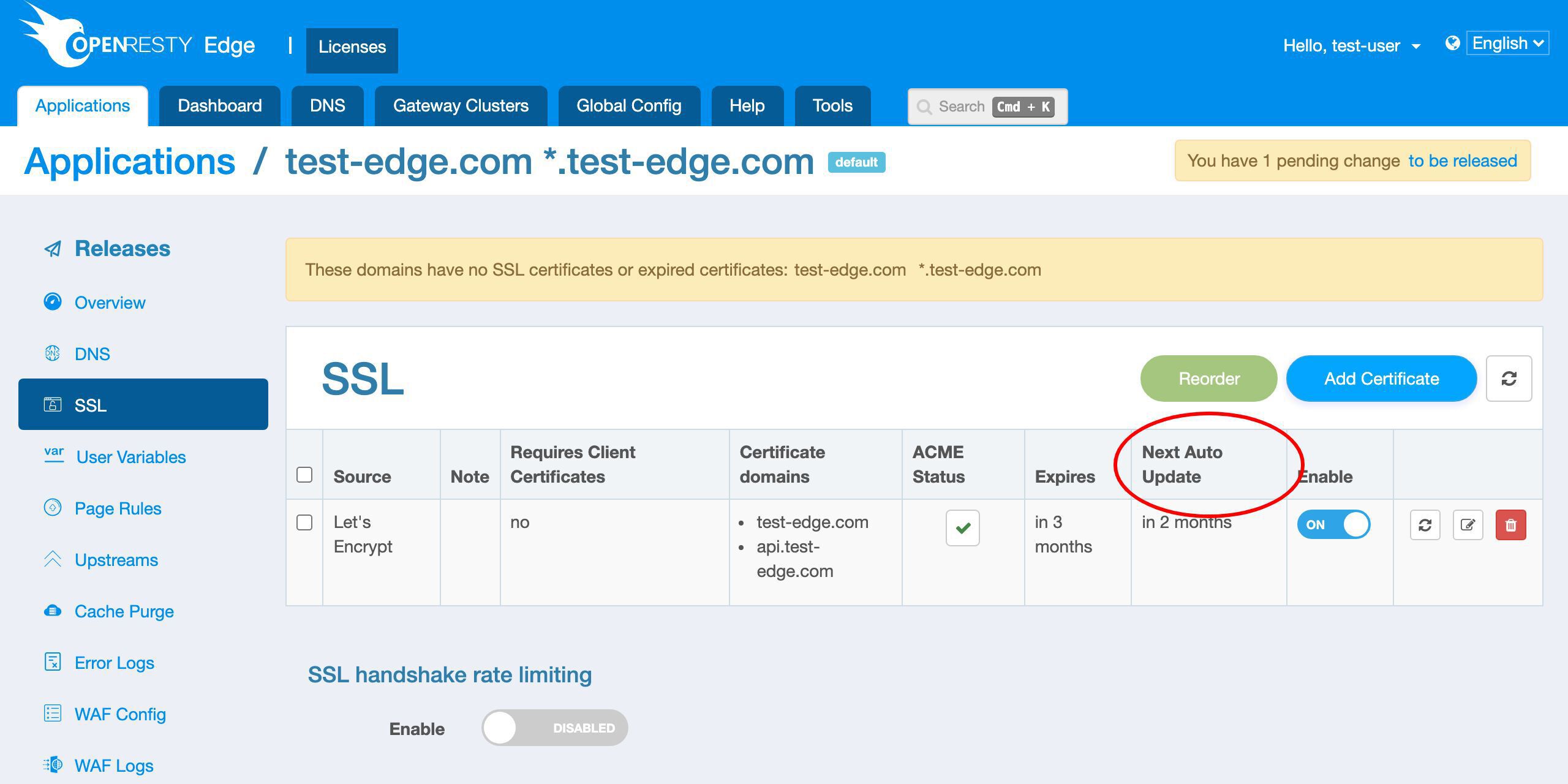
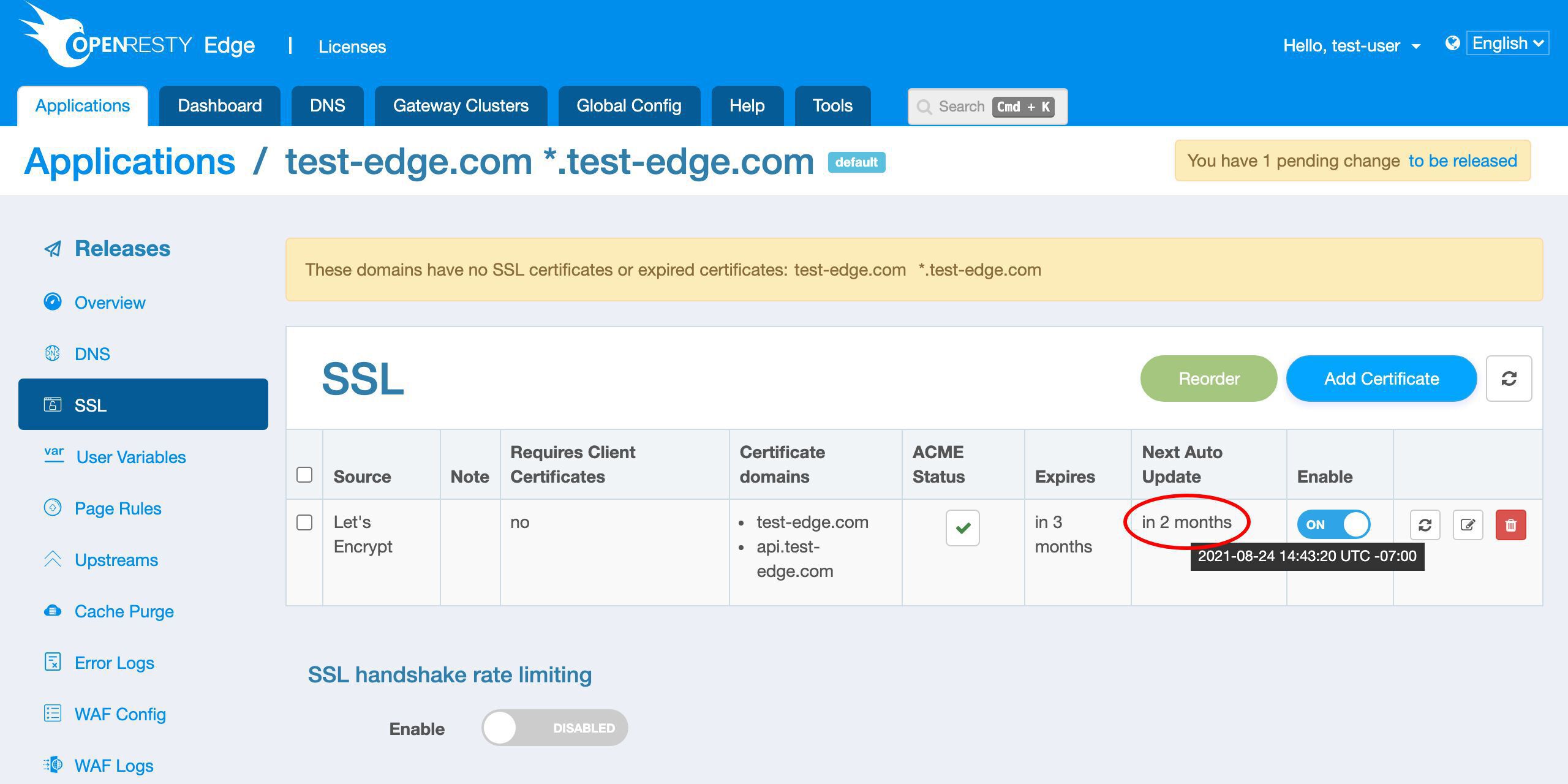
OpenResty Edge は、将来証明書の期限が近づいたときに自動的に更新します。
次回の更新が 2 ヶ月後に予定されていることがわかります。つまり、期限切れの 1 ヶ月前です。
既存の Let’s Encrypt 証明書も編集可能です。
ここでは変更を加えません。
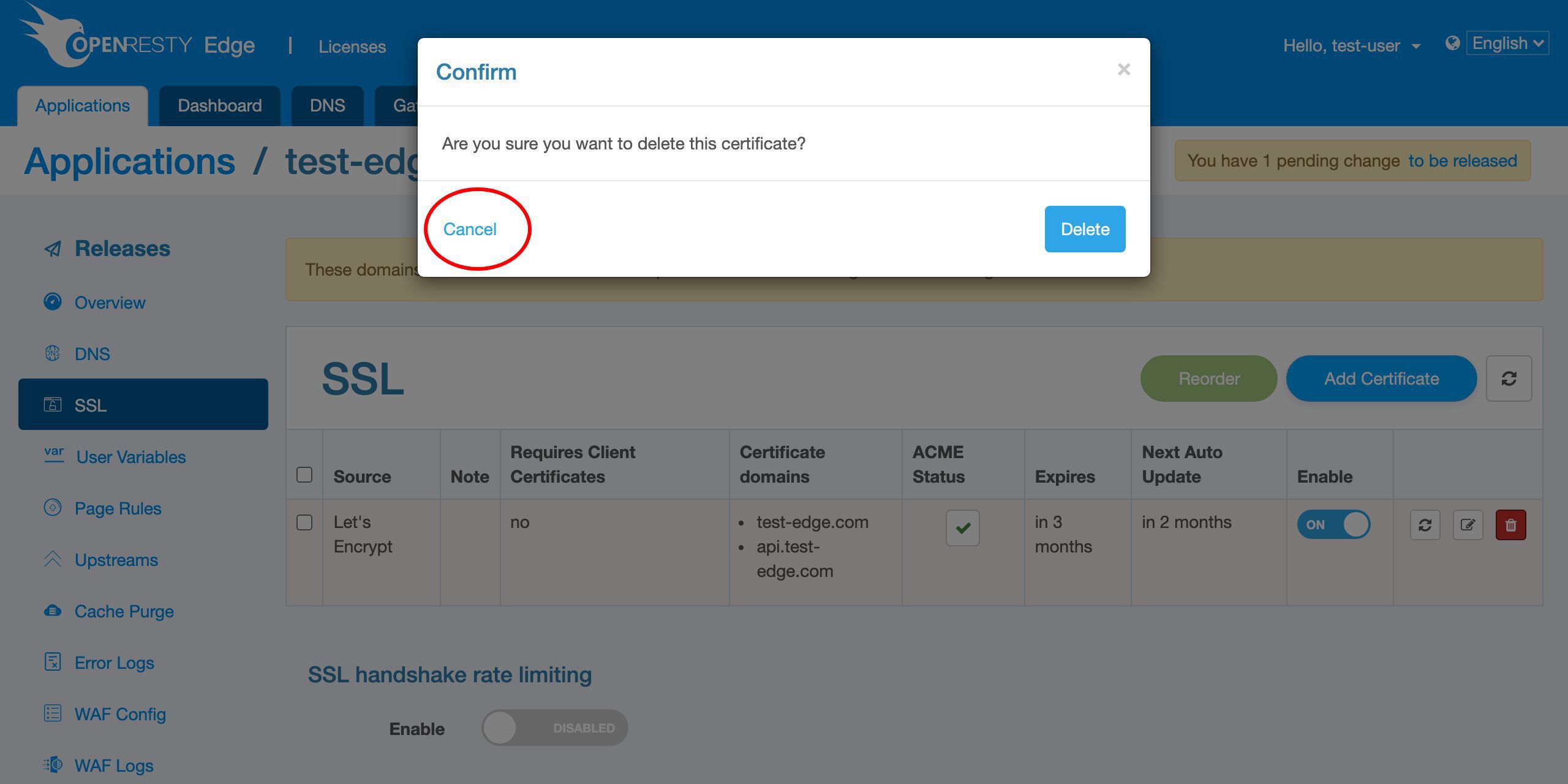
または、この証明書を削除することもできます。
今は削除したくありません。
ただし、削除せずに無効にすることはできます。
その後、再び有効にすることもできます。
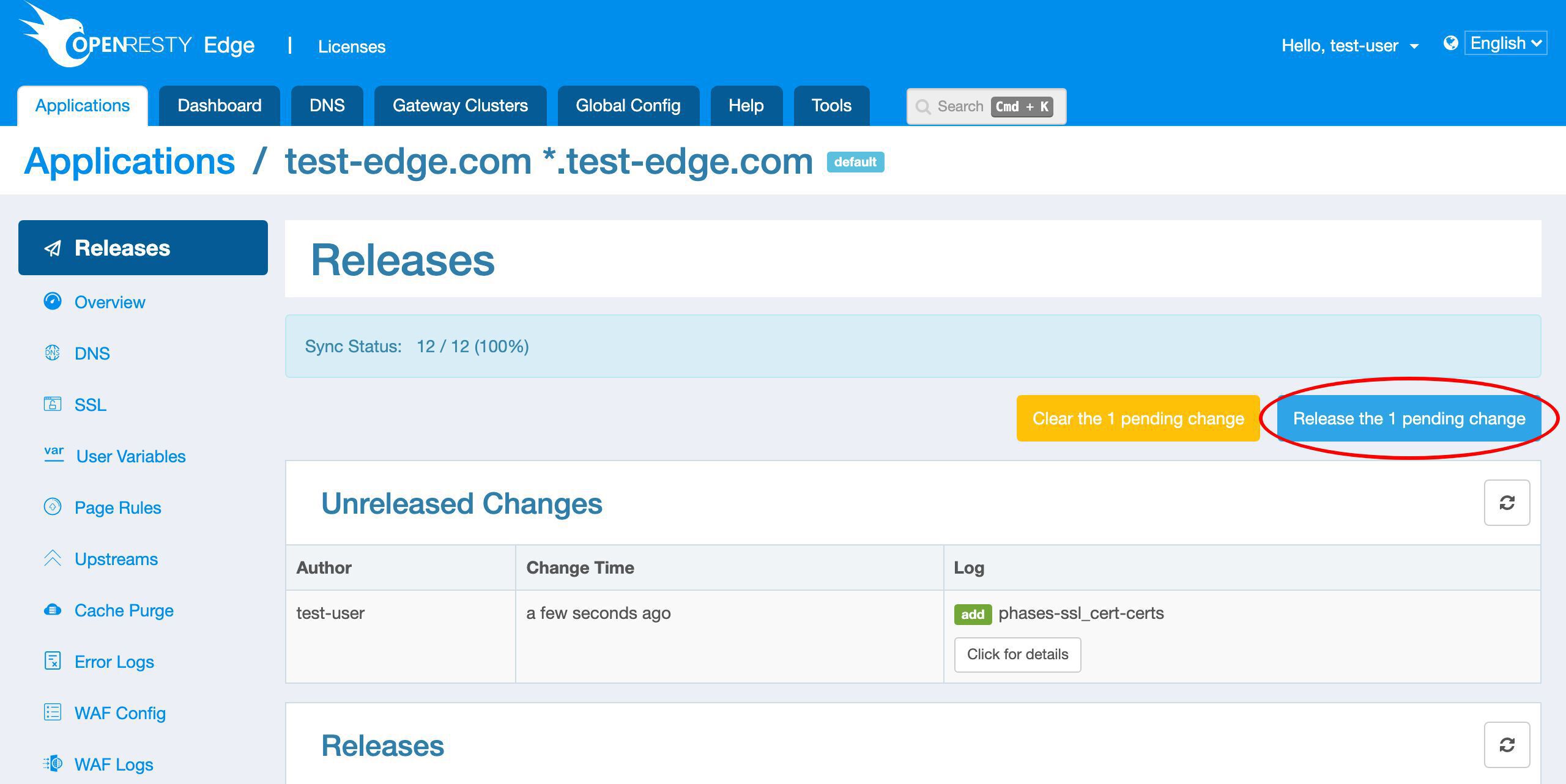
新しい証明書をプッシュするために、いつものように新しいバージョンをリリースする必要があります。
このボタンをクリックします。
リリースします!
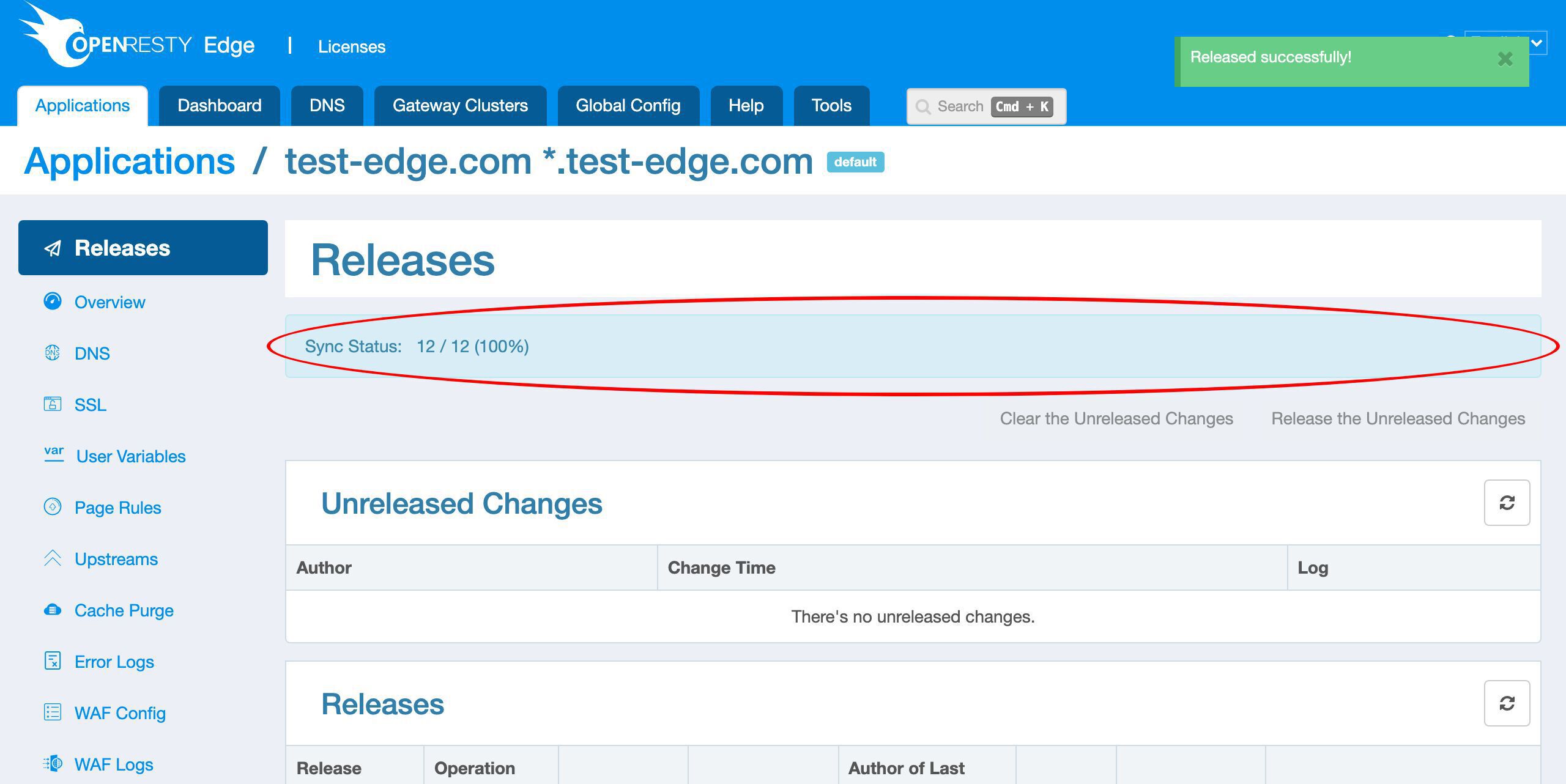
これで完了です!
新しい証明書がすべてのゲートウェイクラスターとサーバーにプッシュされました。
設定の変更にはサーバーのリロード、再起動、またはサーバープロセスのバイナリアップグレードは必要ありません。そのため、非常に効率的でスケーラブルです。
その後、OpenResty Edge は、これらの証明書が期限切れになる前に Let’s Encrypt からの証明書を自動的に再度更新します。
何らかの理由で一部の証明書が更新されなかった場合、ユーザーはこのようなグローバル通知を受け取ります。
テスト
新しいブラウザタブを開き、https を使用して test-edge.com ウェブサイトにアクセスしてみましょう。
成功しました!
api サブドメインもテストしてみます。
これも機能しています!
ターミナルで、ゲートウェイクラスターサーバーを使用して新しい証明書をテストすることもできます。
サンフランシスコ近くのゲートウェイサーバーを選択します。
133 で終わるパブリック IP アドレスをコピーします。
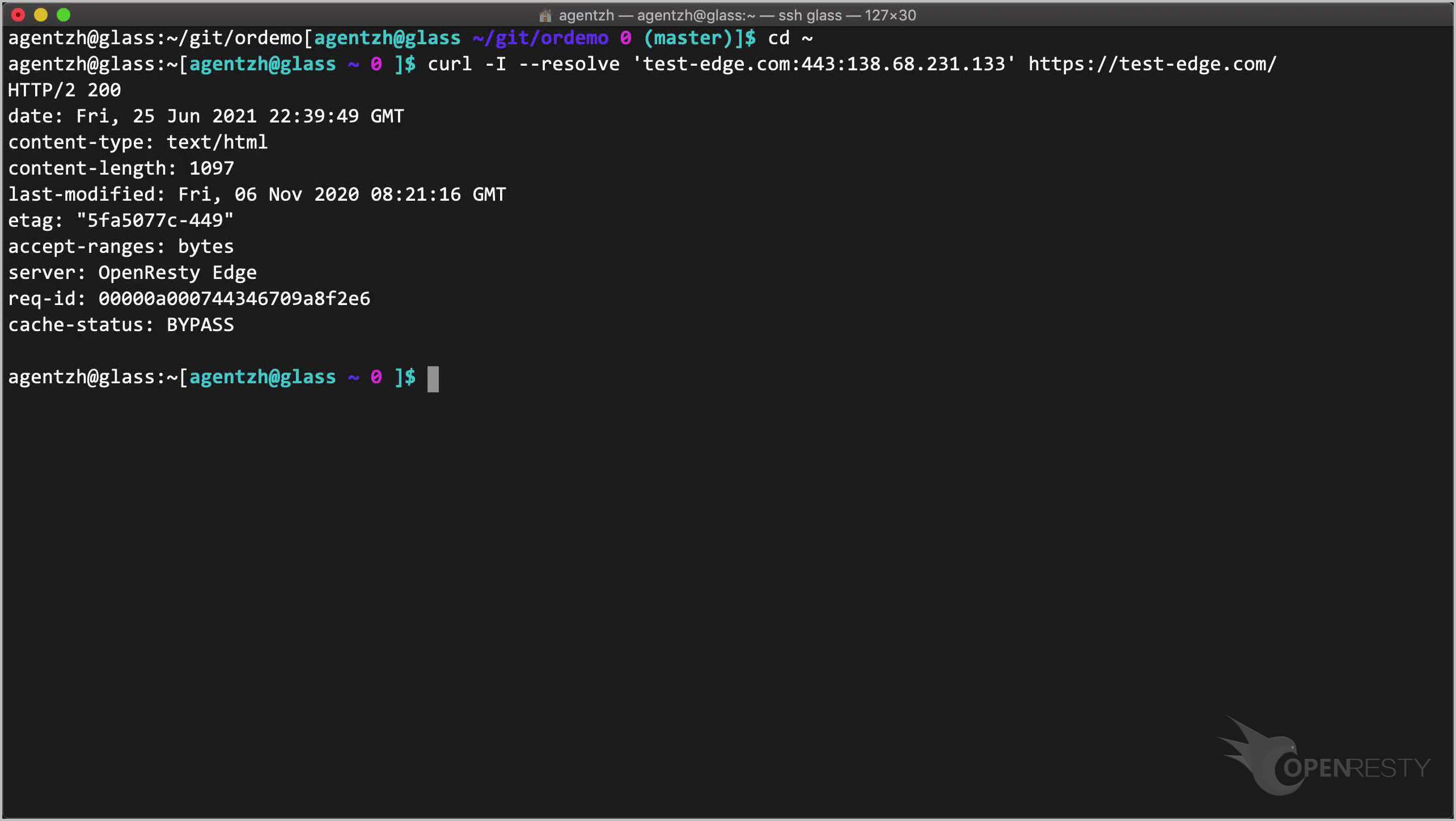
ターミナルで、このゲートウェイサーバーに HTTPS リクエストを送信できます。
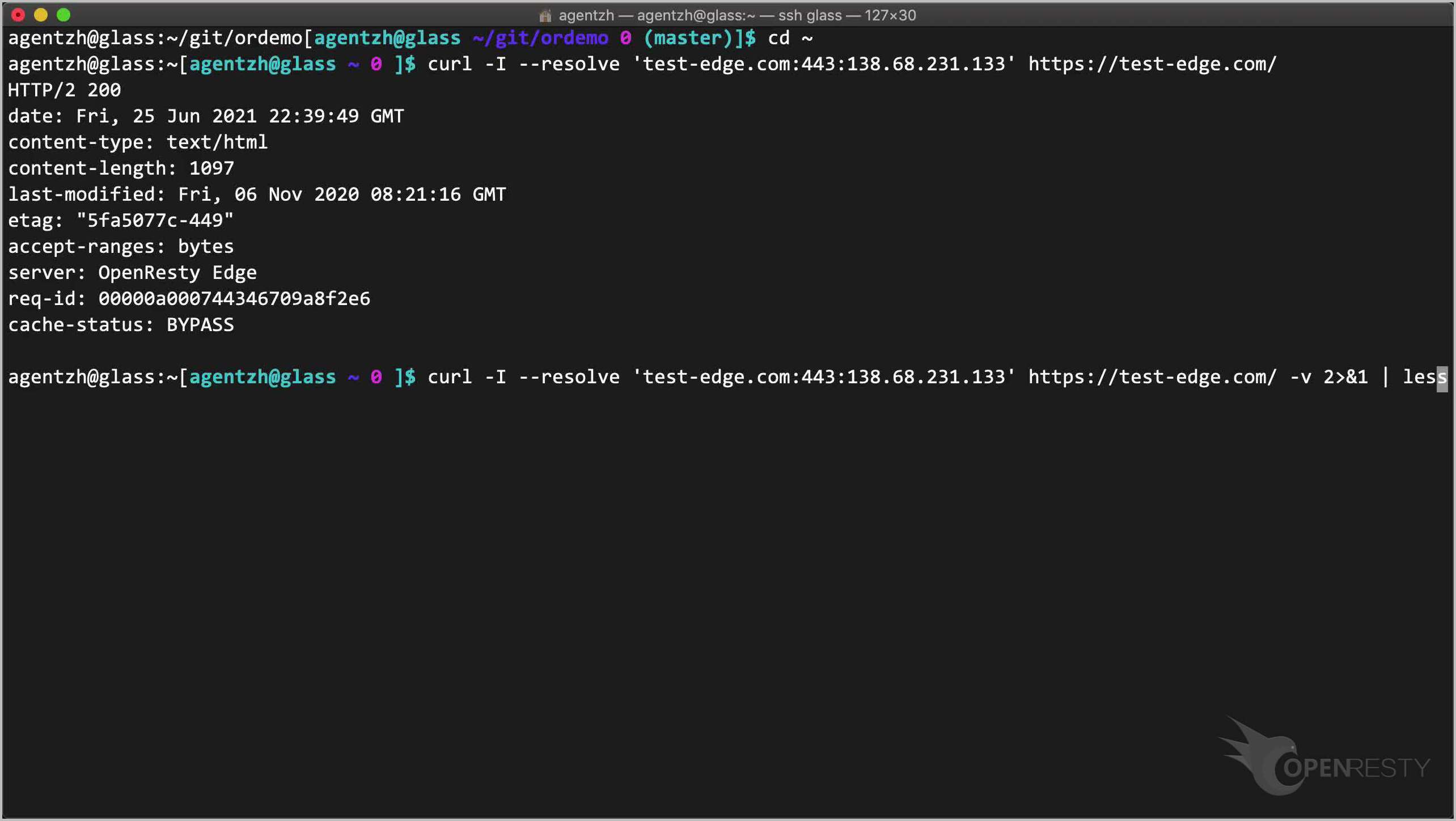
curl -I --resolve 'test-edge.com:443:138.68.231.133' https://test-edge.com/
成功しました!
-v オプションを使用して、より詳細な情報を取得することもできます。
curl -I --resolve 'test-edge.com:443:138.68.231.133' https://test-edge.com/ -v
このコマンドを実行します。
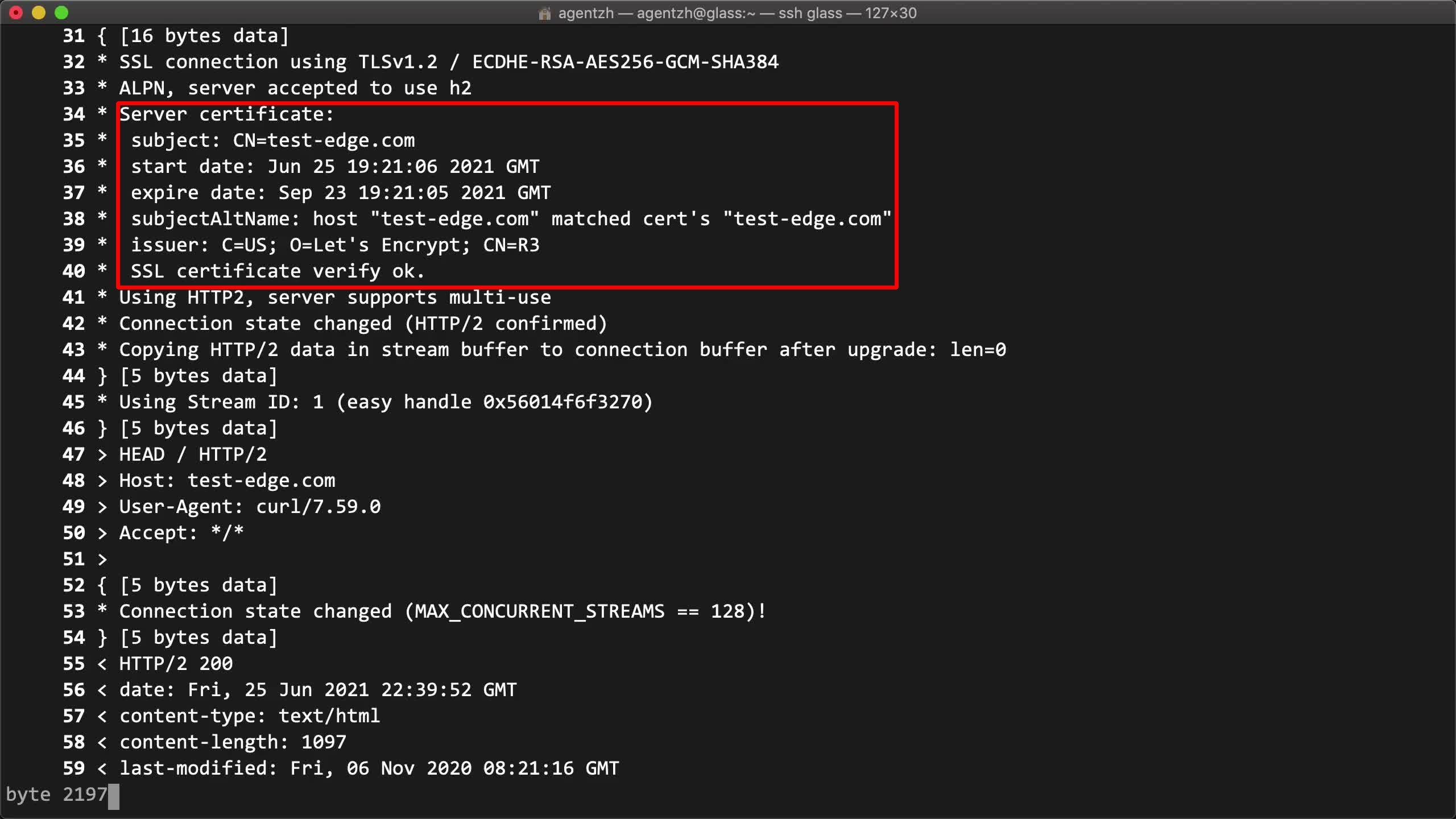
ここで実際にサーバー証明書を確認できます。また、この証明書が確かに Let’s Encrypt によって発行されたものであることも確認できます。
著者について
章亦春(Zhang Yichun)は、オープンソースの OpenResty® プロジェクトの創始者であり、OpenResty Inc. の CEO および創業者です。
章亦春(GitHub ID: agentzh)は中国江蘇省生まれで、現在は米国ベイエリアに在住しております。彼は中国における初期のオープンソース技術と文化の提唱者およびリーダーの一人であり、Cloudflare、Yahoo!、Alibaba など、国際的に有名なハイテク企業に勤務した経験があります。「エッジコンピューティング」、「動的トレーシング」、「機械プログラミング」 の先駆者であり、22 年以上のプログラミング経験と 16 年以上のオープンソース経験を持っております。世界中で 4000 万以上のドメイン名を持つユーザーを抱えるオープンソースプロジェクトのリーダーとして、彼は OpenResty® オープンソースプロジェクトをベースに、米国シリコンバレーの中心部にハイテク企業 OpenResty Inc. を設立いたしました。同社の主力製品である OpenResty XRay動的トレーシング技術を利用した非侵襲的な障害分析および排除ツール)と OpenResty Edge(マイクロサービスおよび分散トラフィックに最適化された多機能
翻訳
英文版の原文と日本語訳版(本文)をご用意しております。読者の皆様による他の言語への翻訳版も歓迎いたします。全文翻訳で省略がなければ、採用を検討させていただきます。心より感謝申し上げます!