OpenResty Edge の高性能 Web アプリケーションファイアウォール(WAF)
本日は、OpenResty Edge で Web アプリケーションファイアウォール(WAF)を有効にする方法をご紹介いたします。
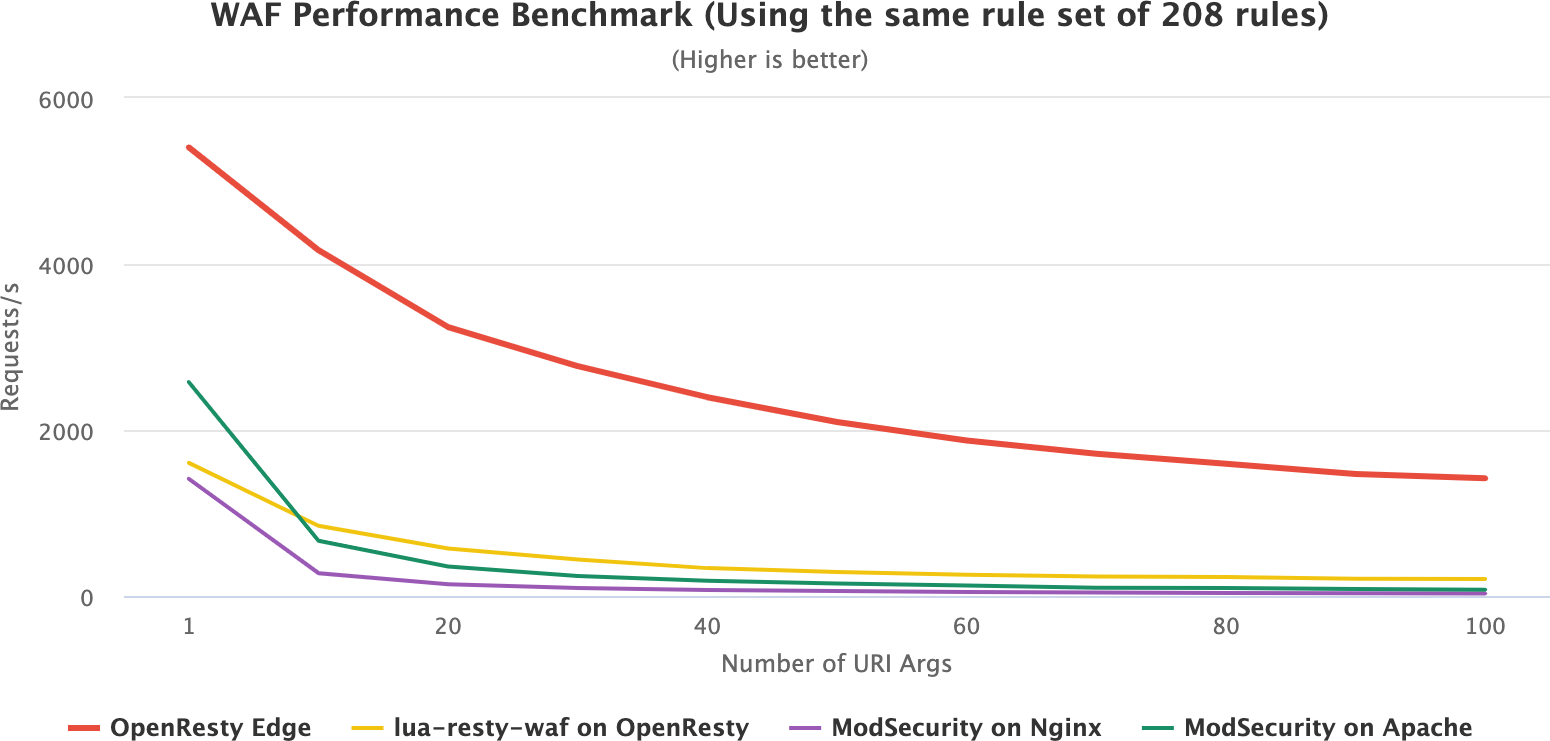
OpenResty Edge の WAF プラットフォームは、ModSecurity や lua-resty-waf などのほぼすべてのオープンソース WAF ソリューションよりも数倍高速です。
アプリケーションの WAF を有効化する
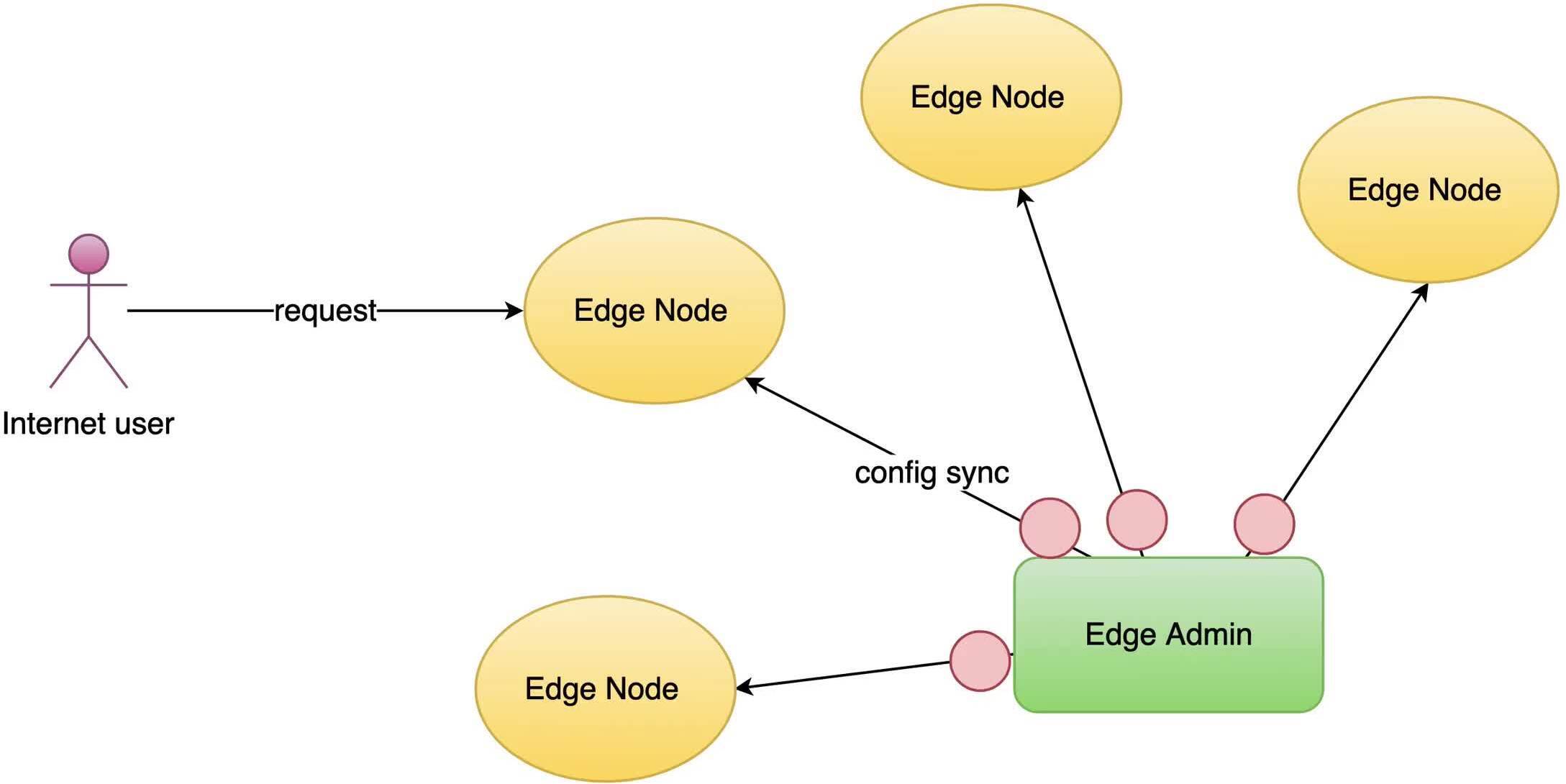
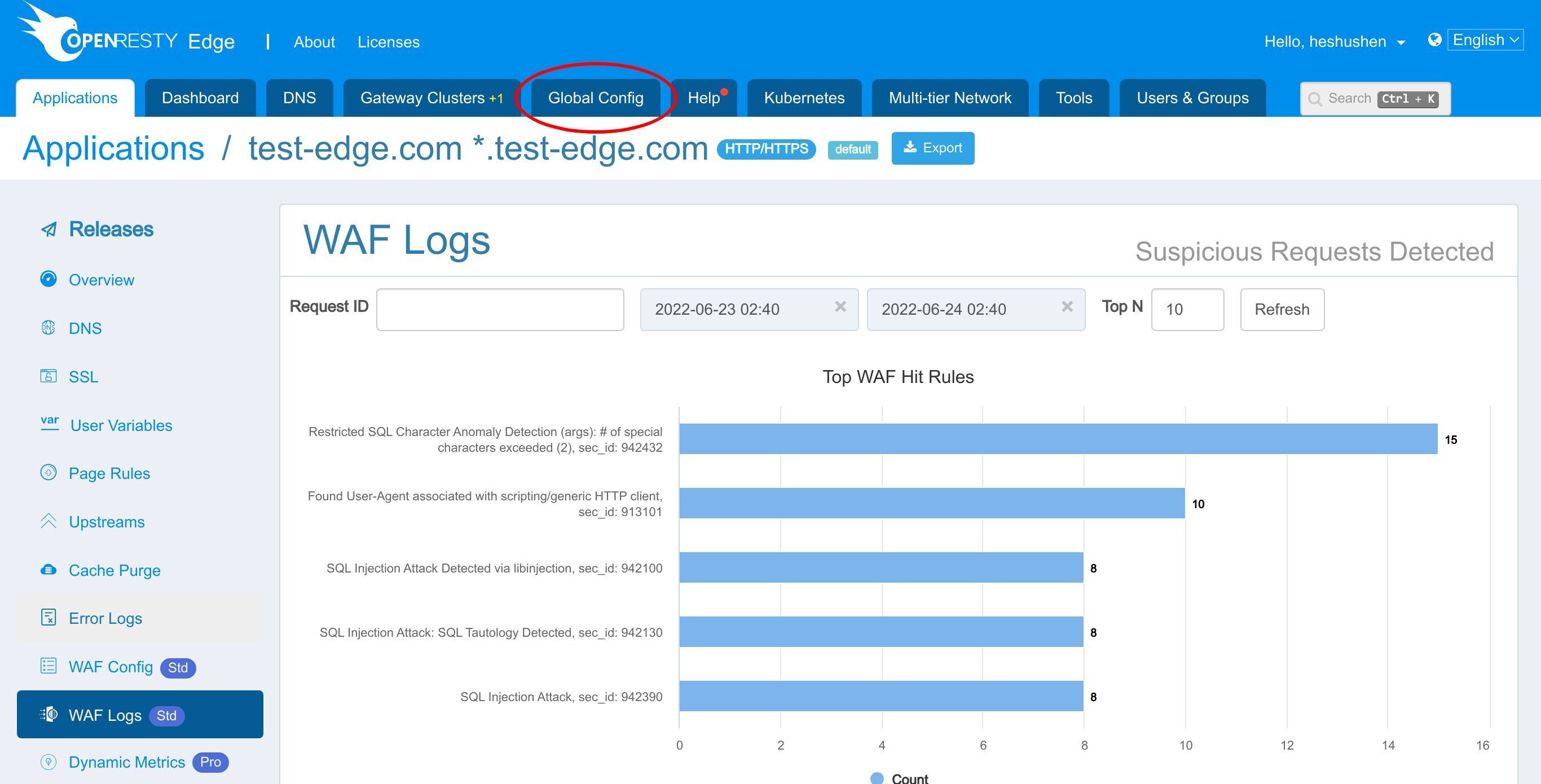
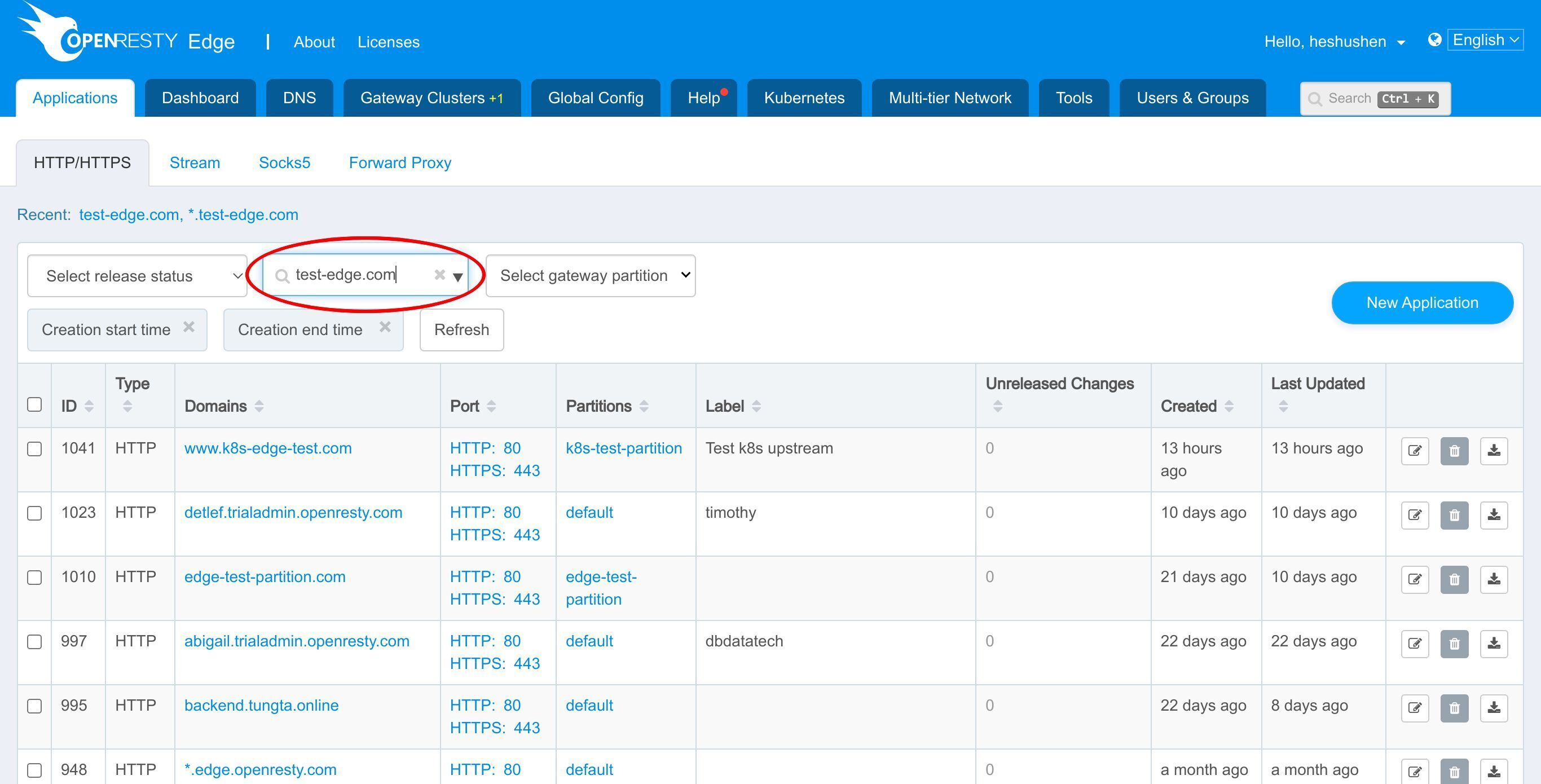
OpenResty Edge の管理者用 Web コンソールにアクセスしましょう。これはコンソールのサンプルデプロイメントです。各ユーザーは独自のローカルデプロイメントを持っています。
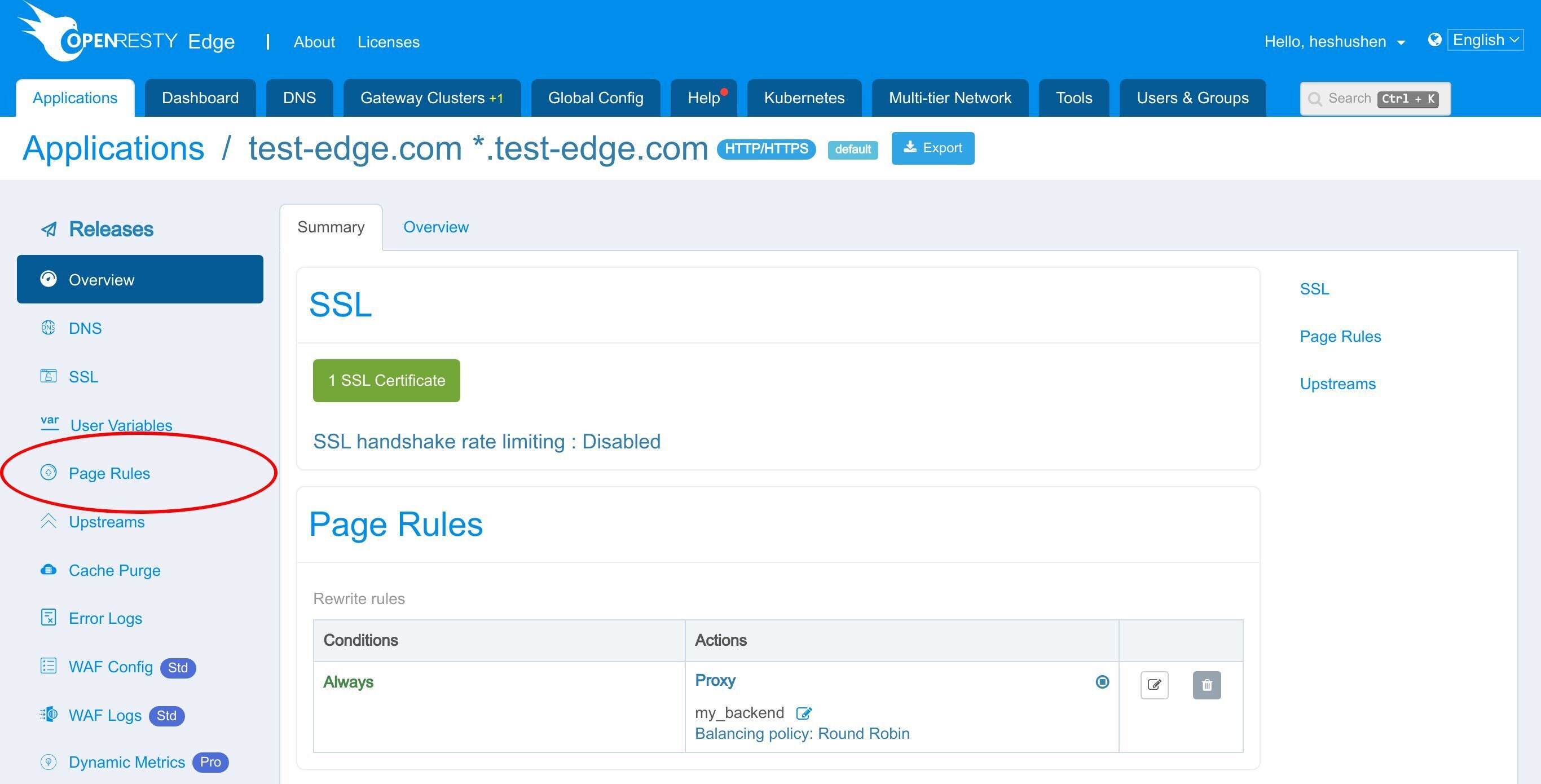
今回も test-edge.com ドメインのサンプルアプリケーションを使用します。
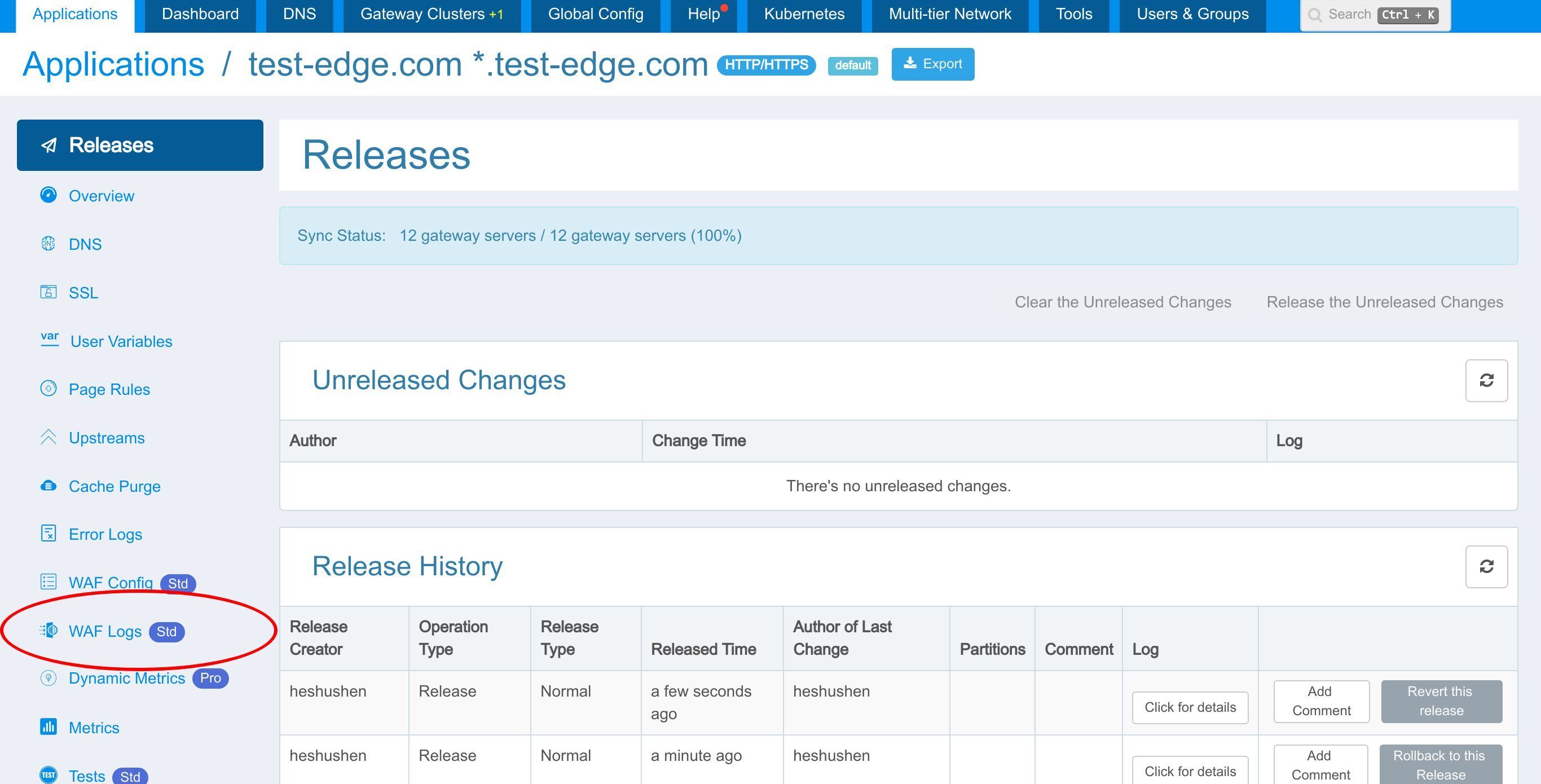
このアプリケーションに進みます。
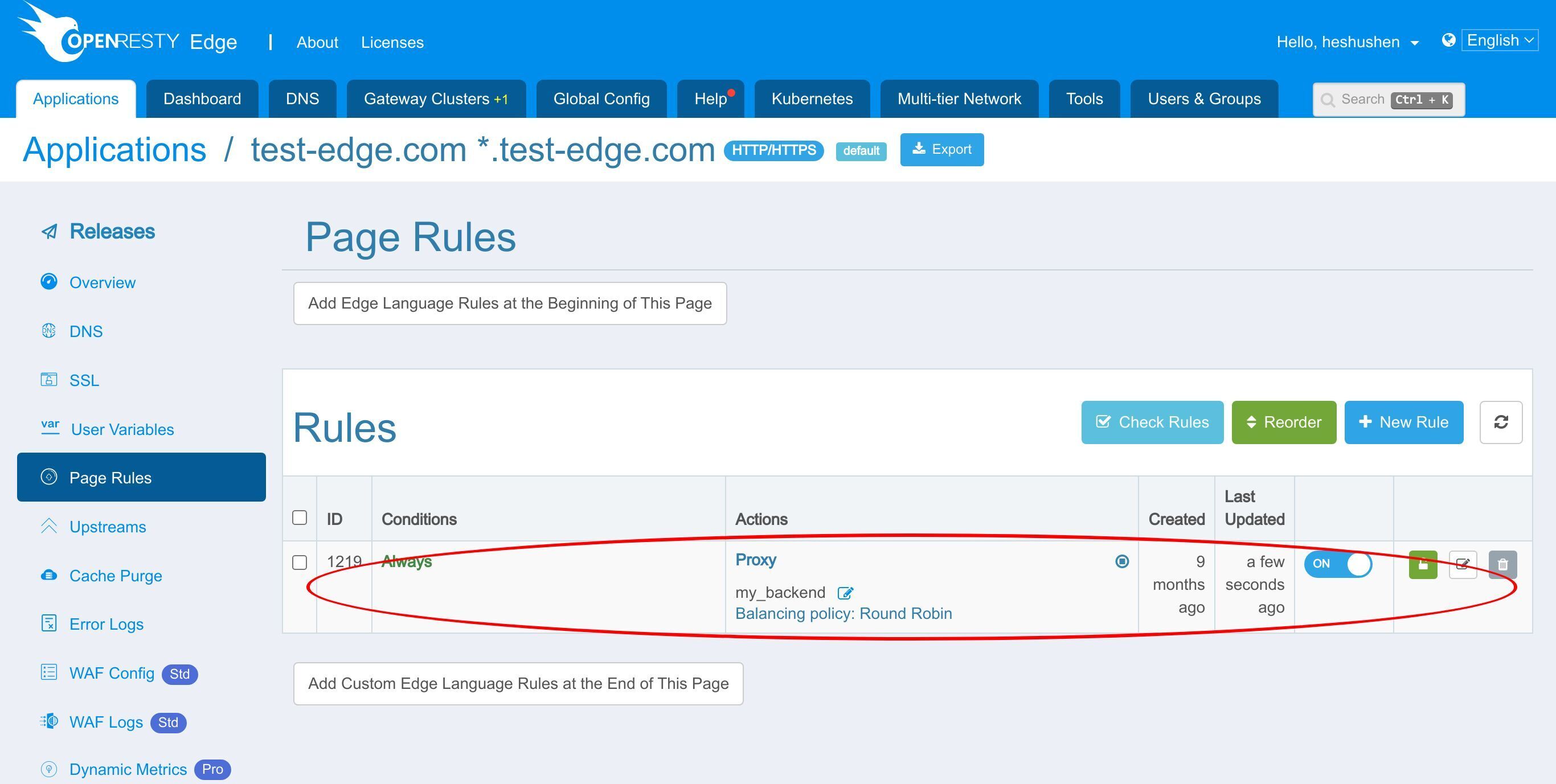
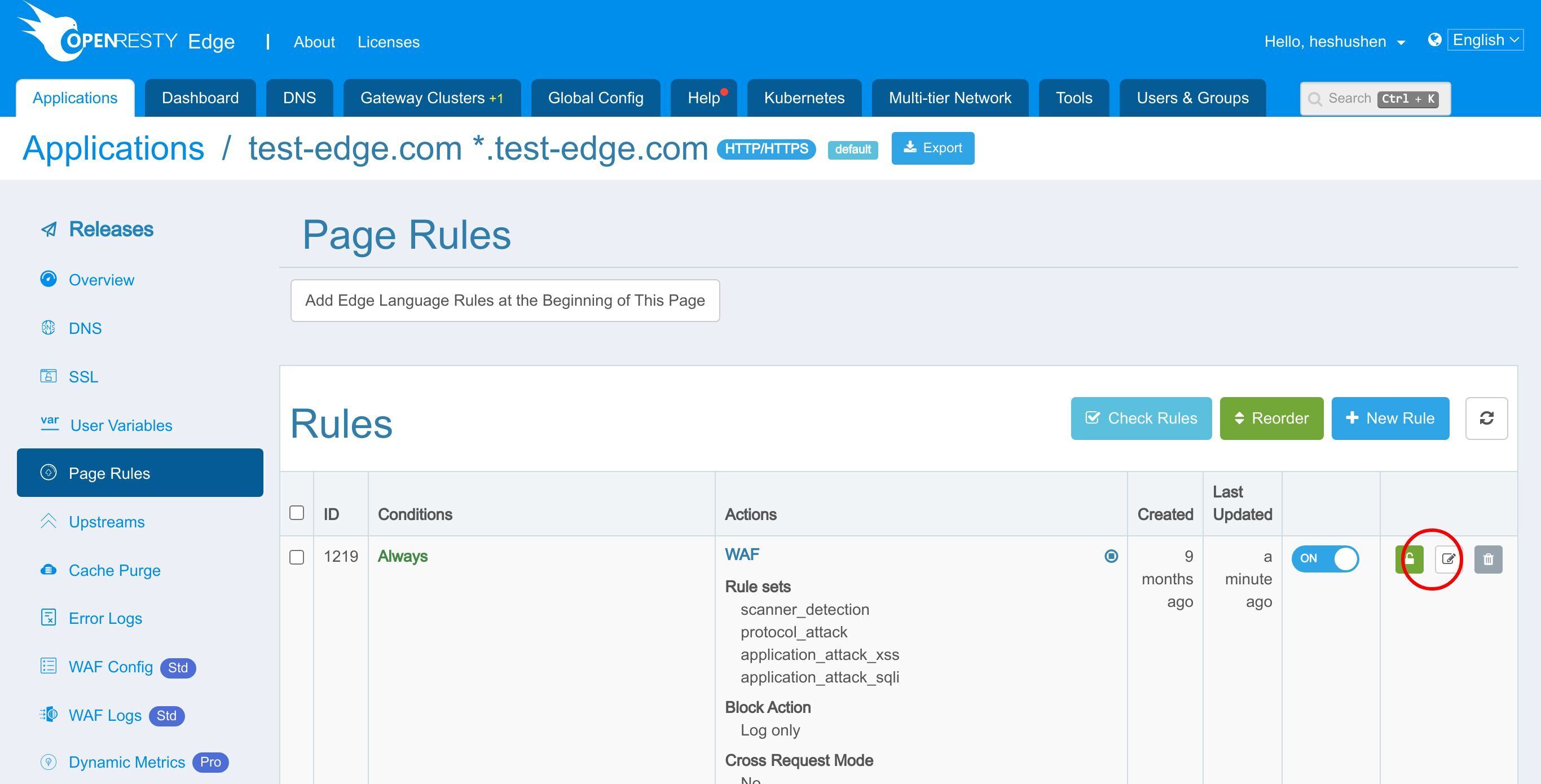
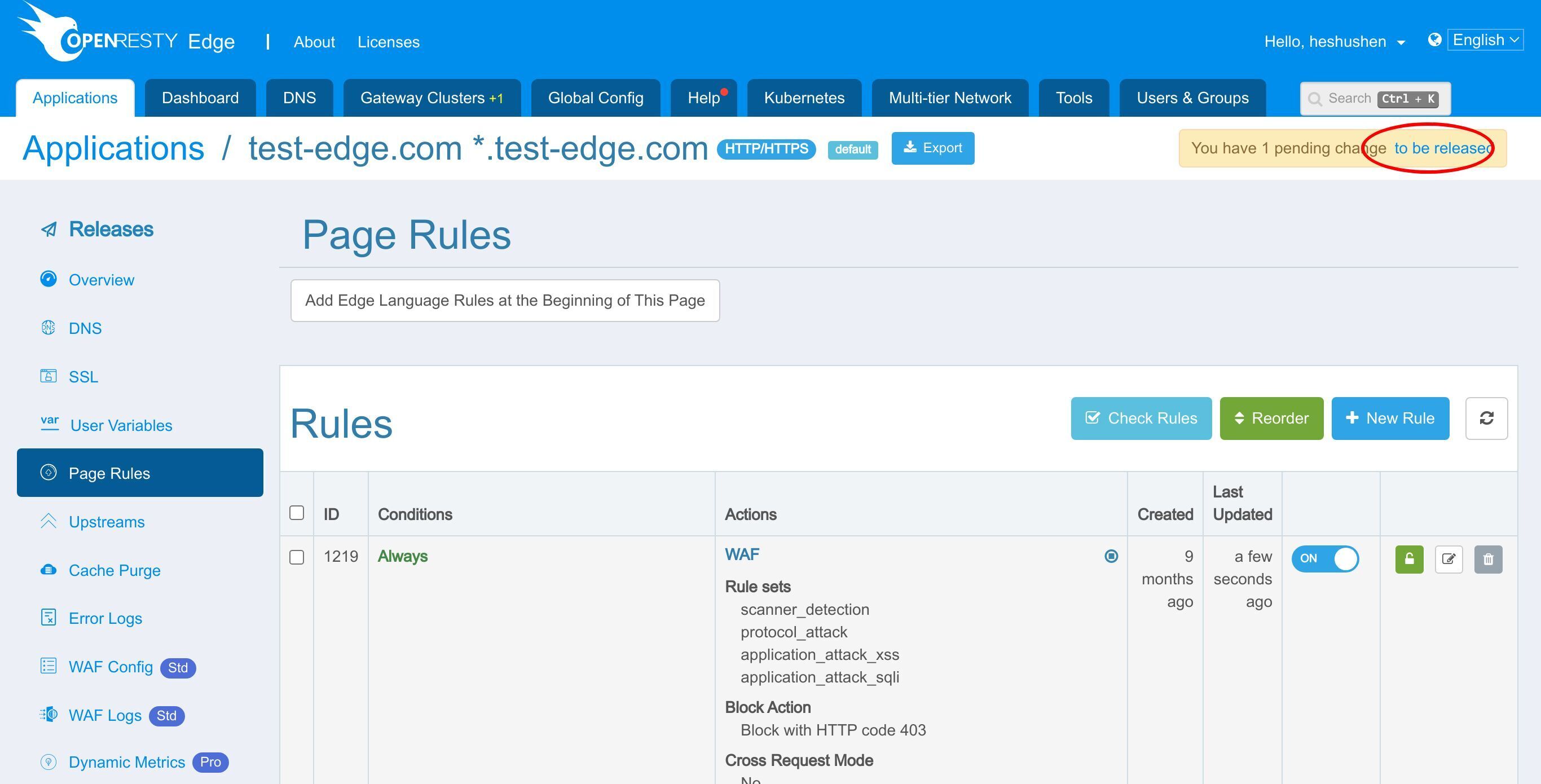
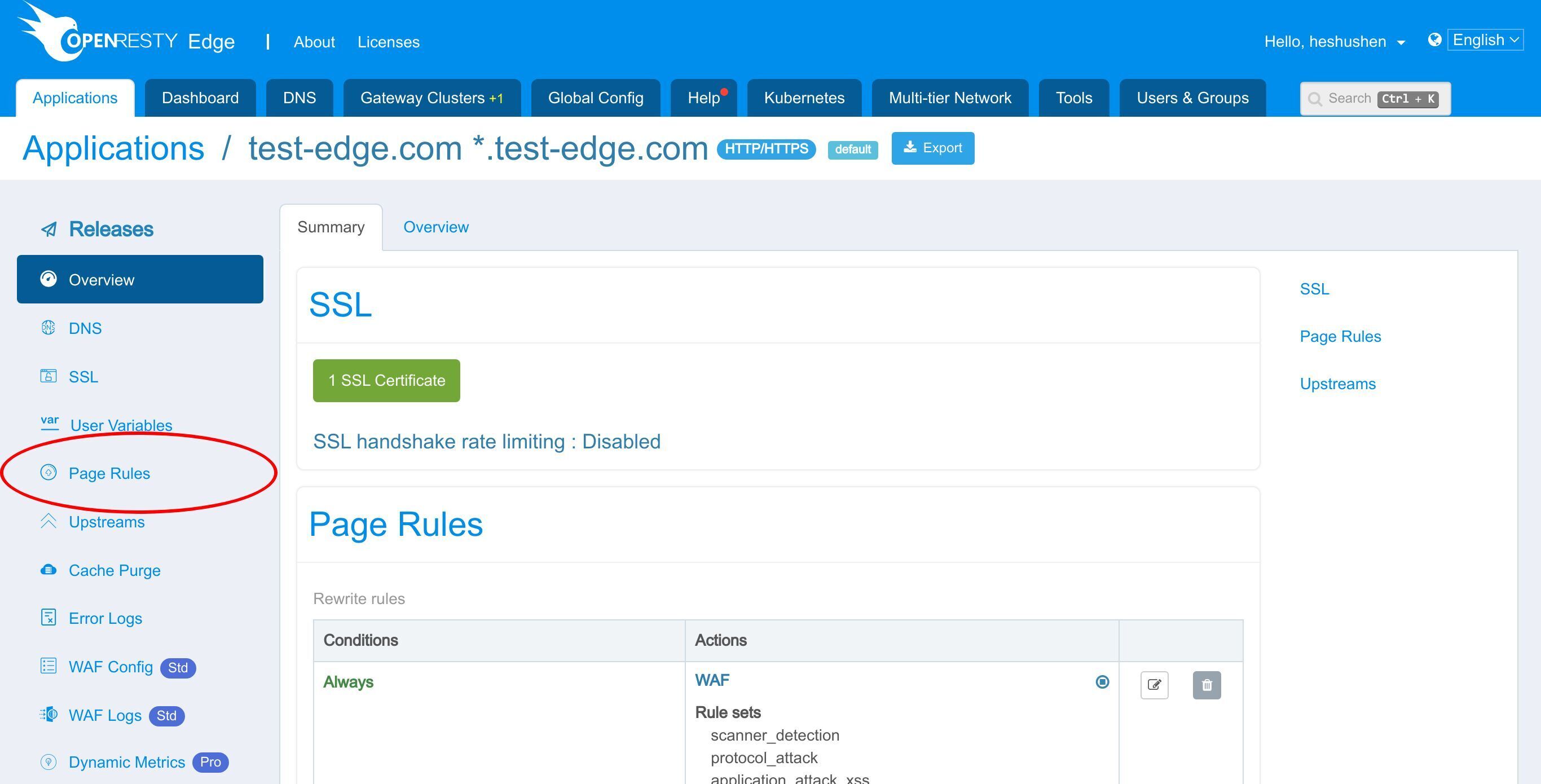
Page Rule ページに進みます。
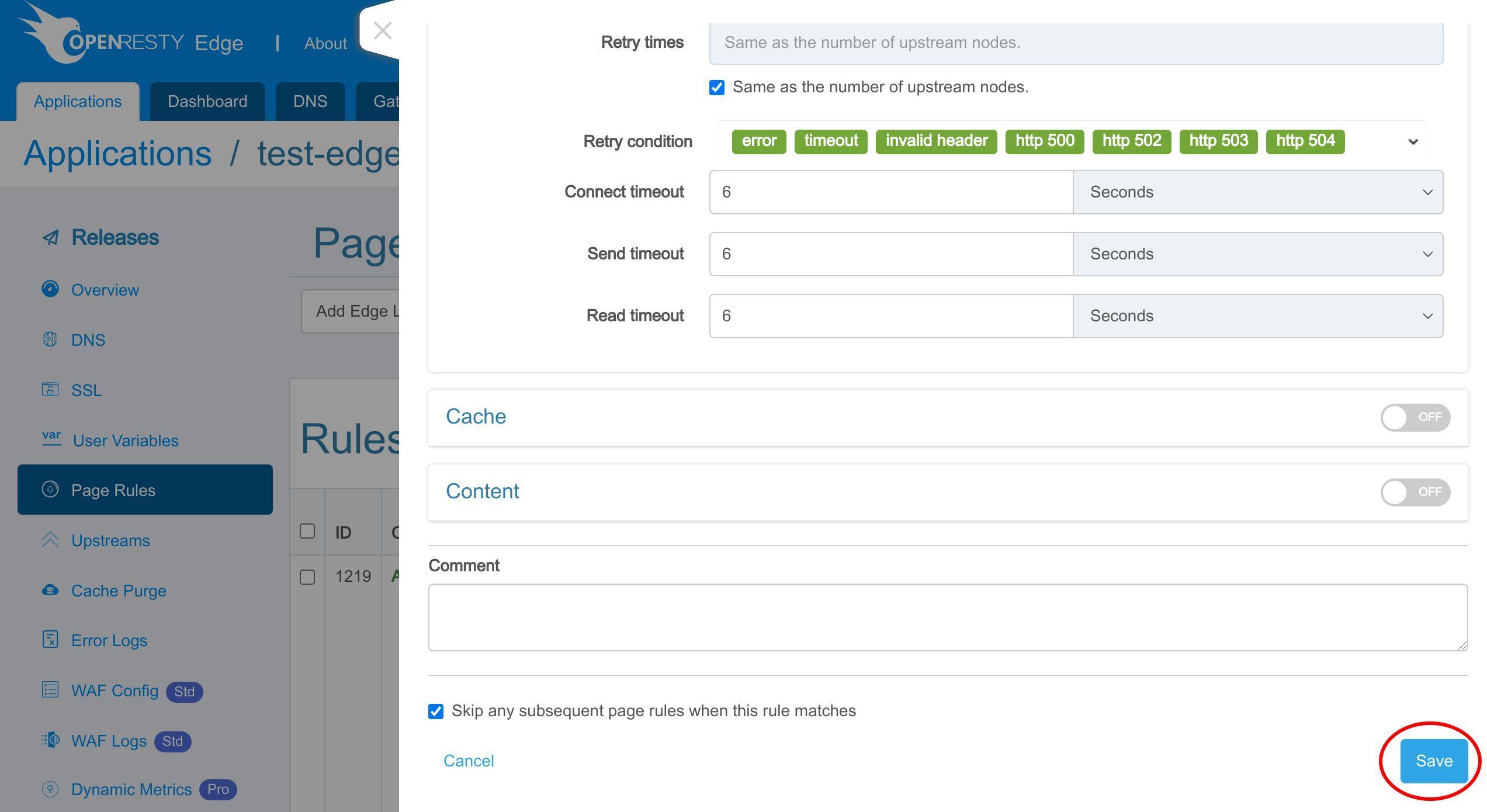
前回のチュートリアルでリバースプロキシのページルールを設定しました。
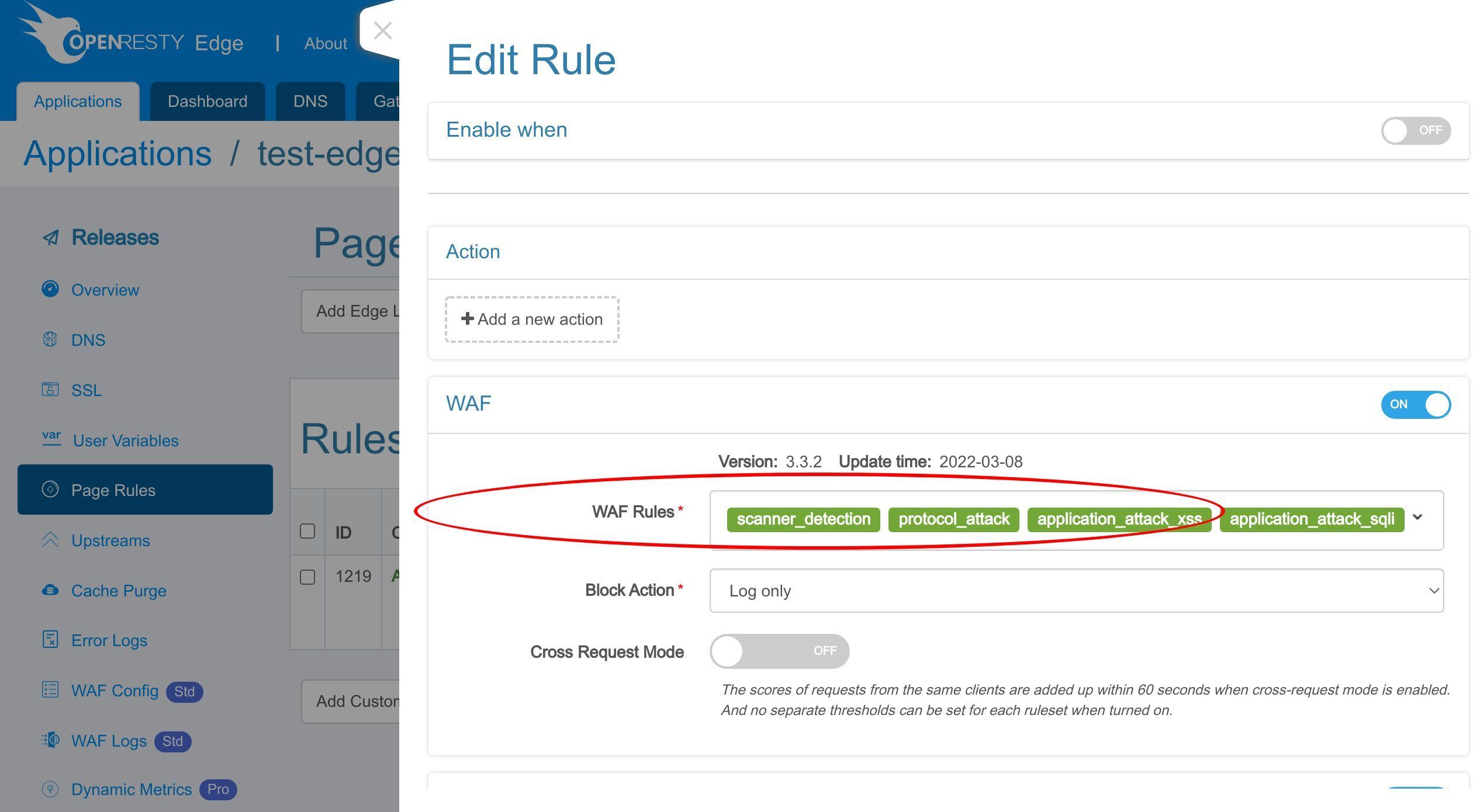
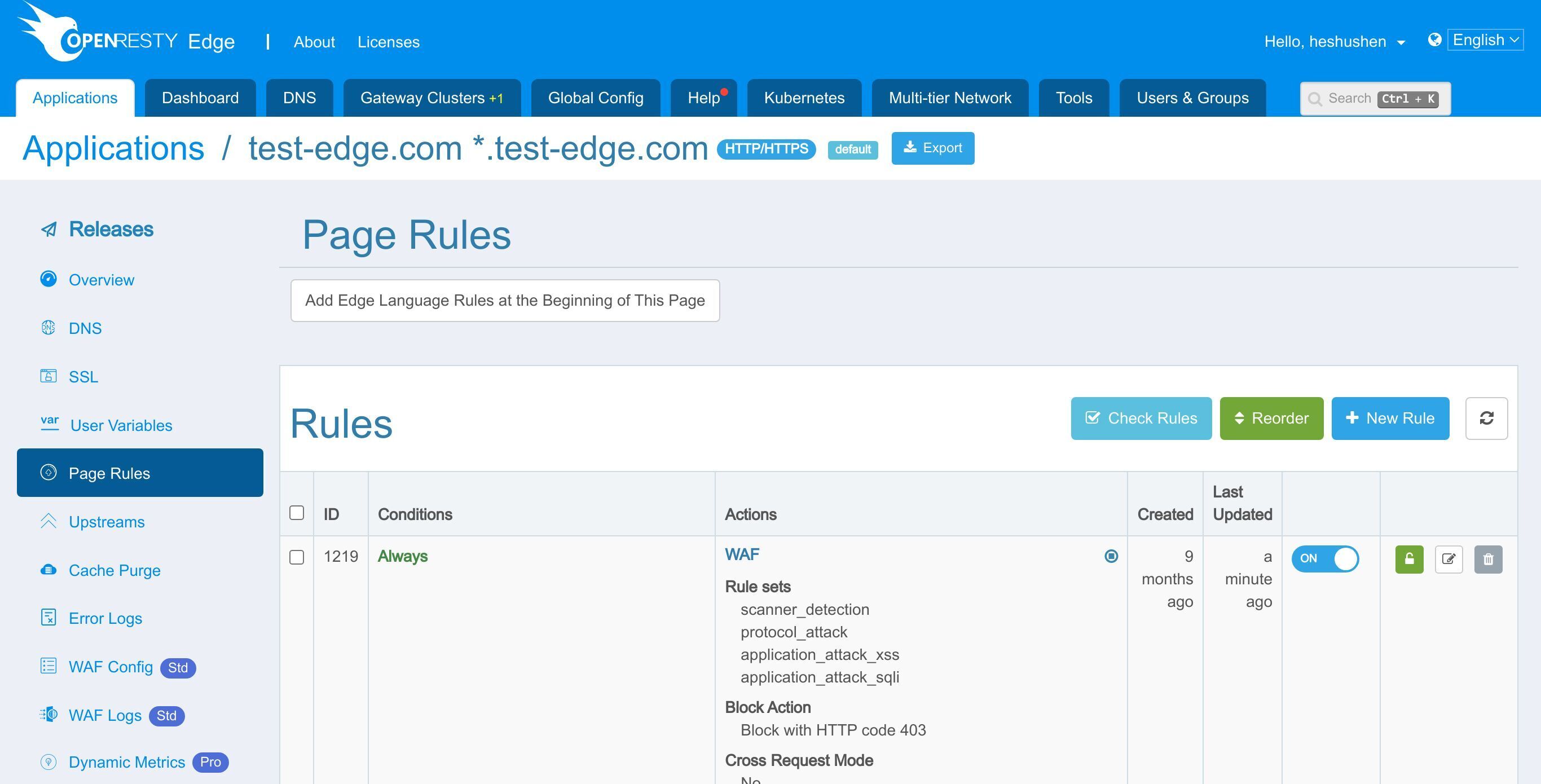
ここで、いくつかの WAF ルールセットを有効にしましょう。
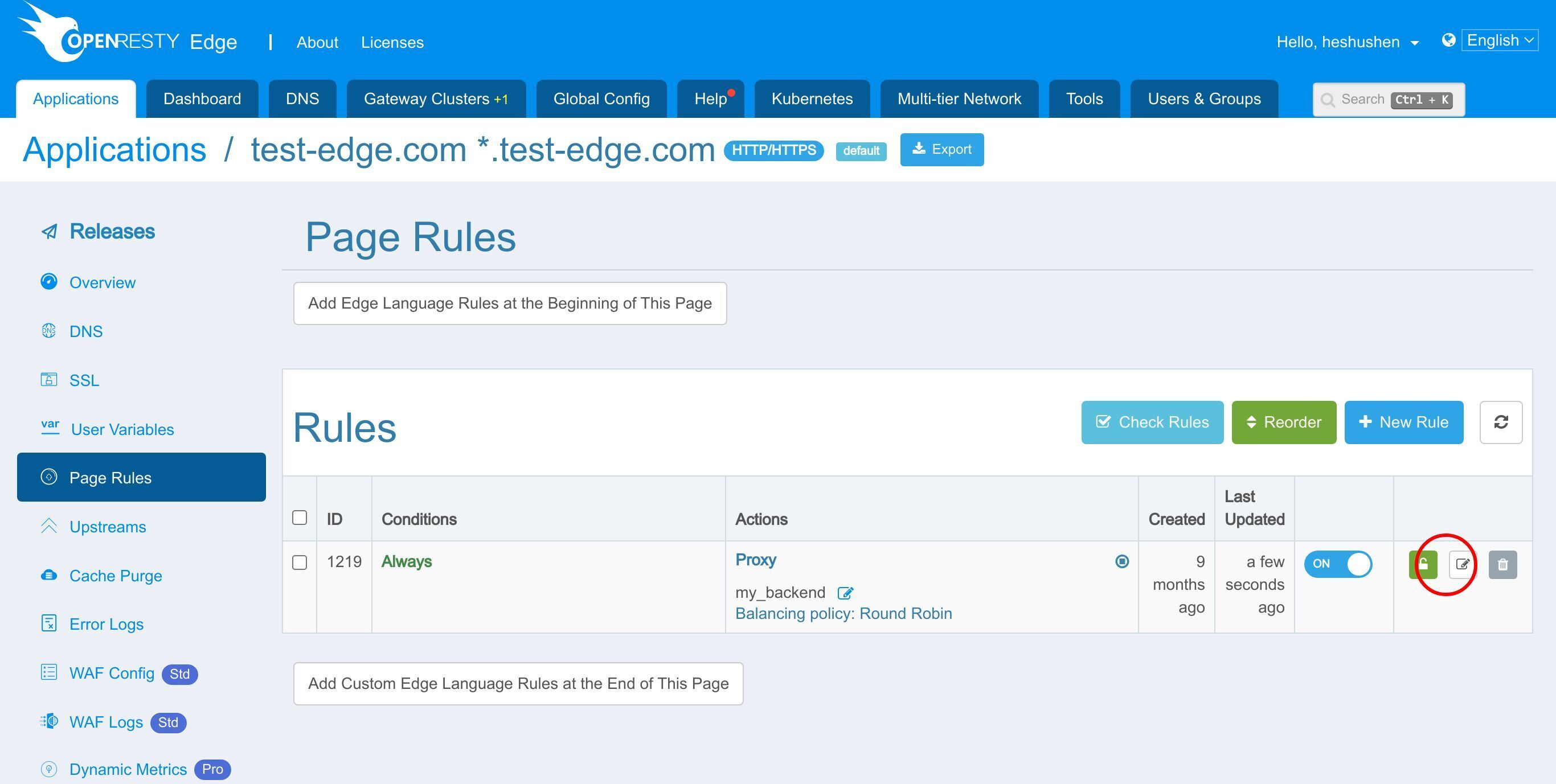
このページルールを編集するためにクリックします。
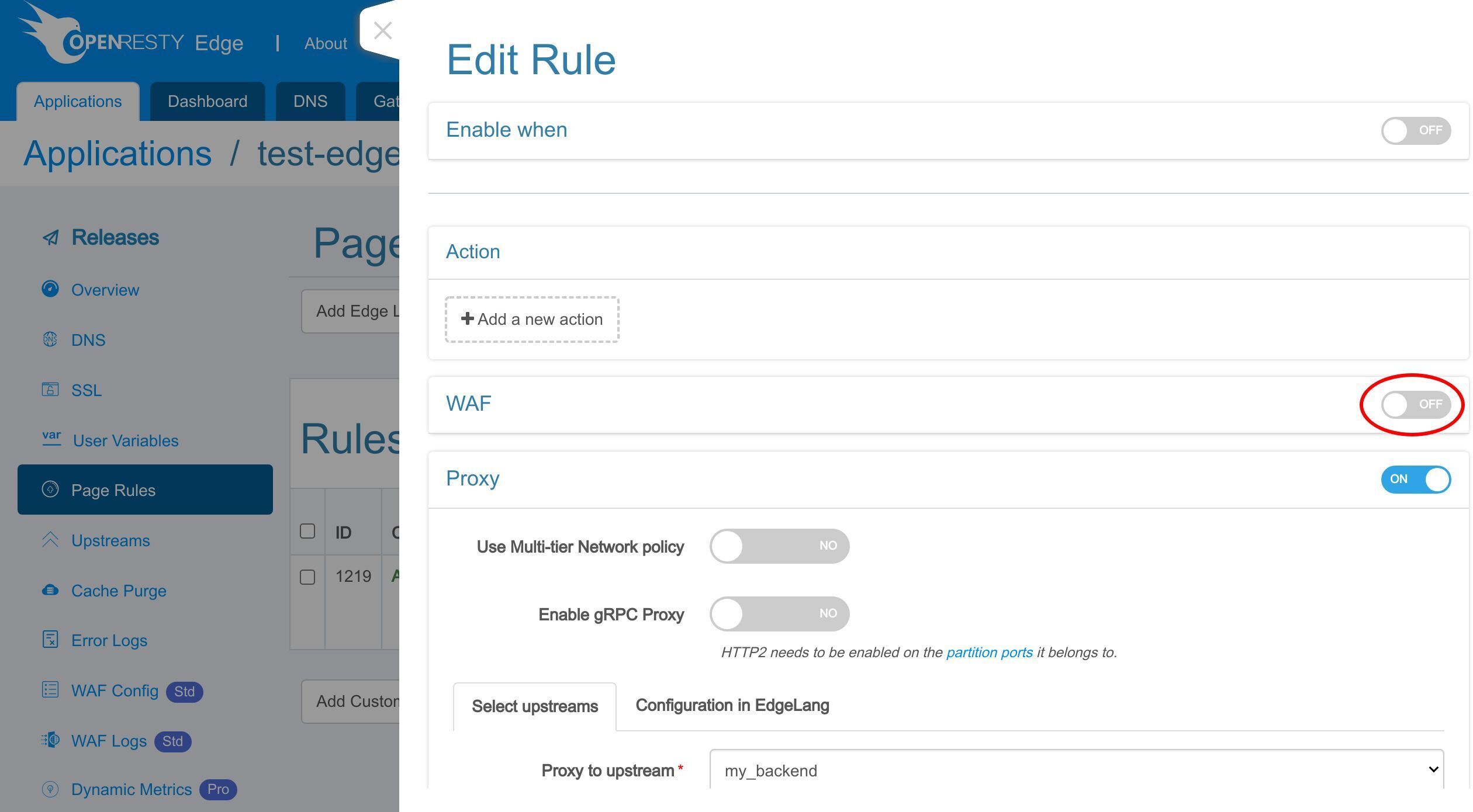
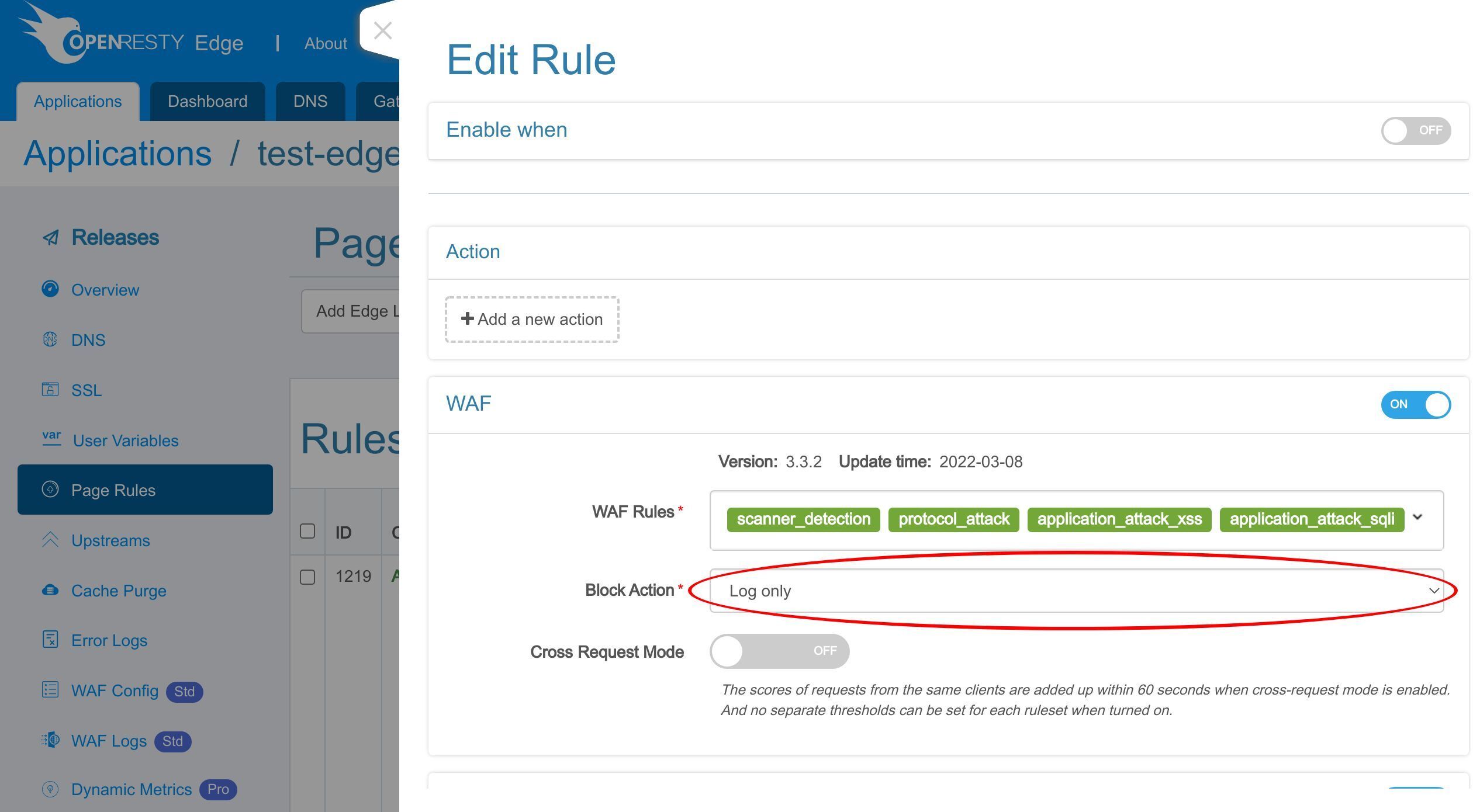
WAF を有効にするには、このスイッチをクリックする必要があります。
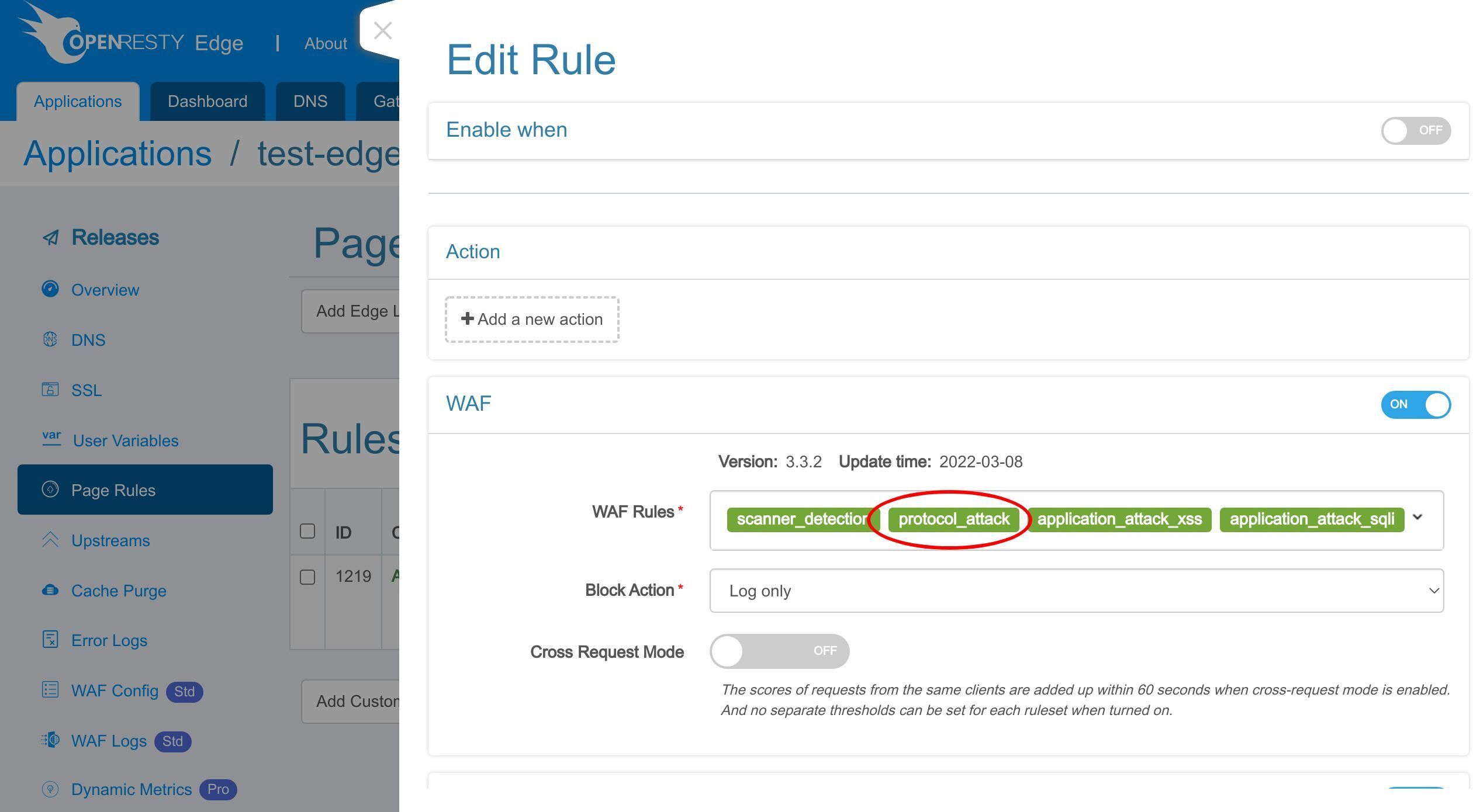
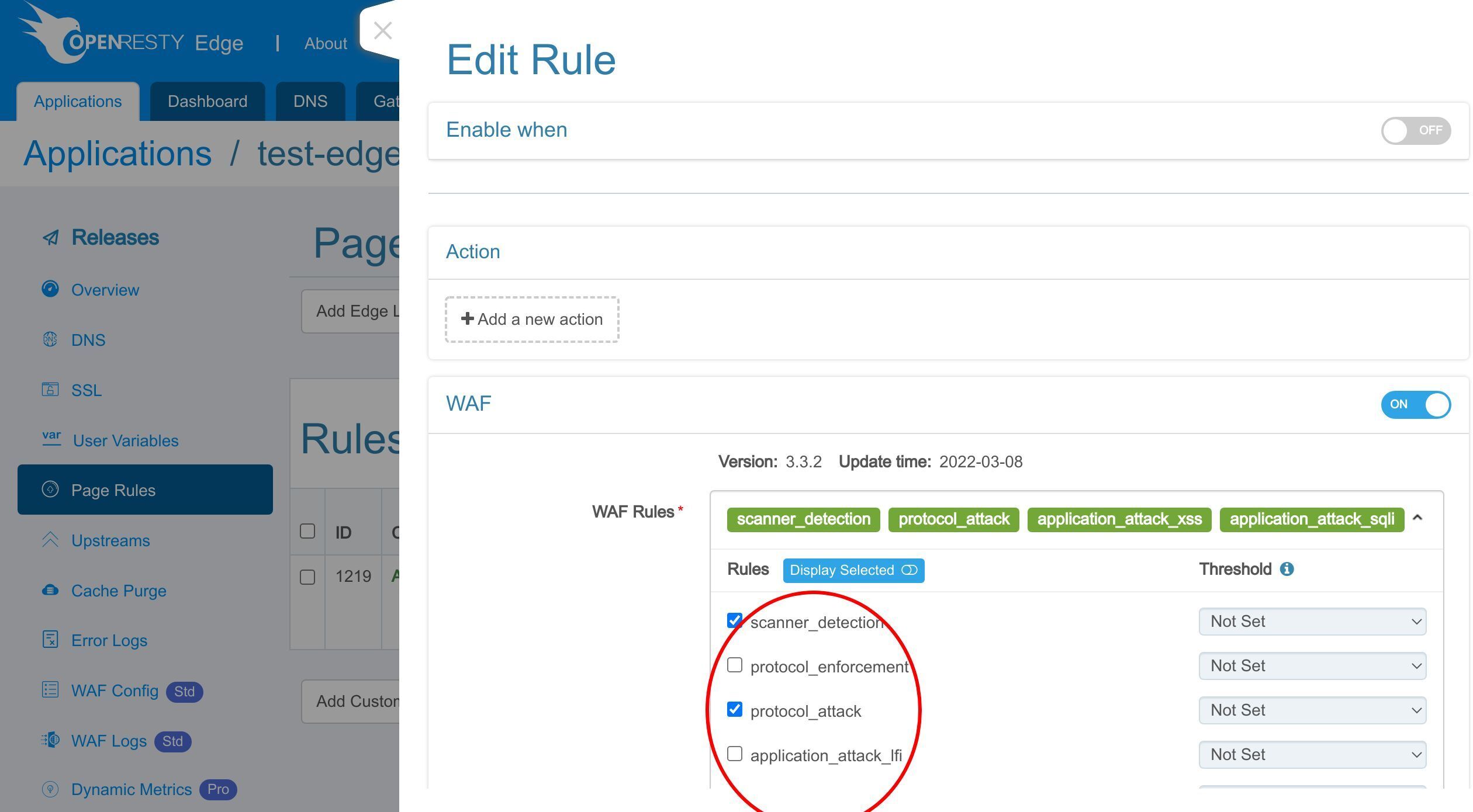
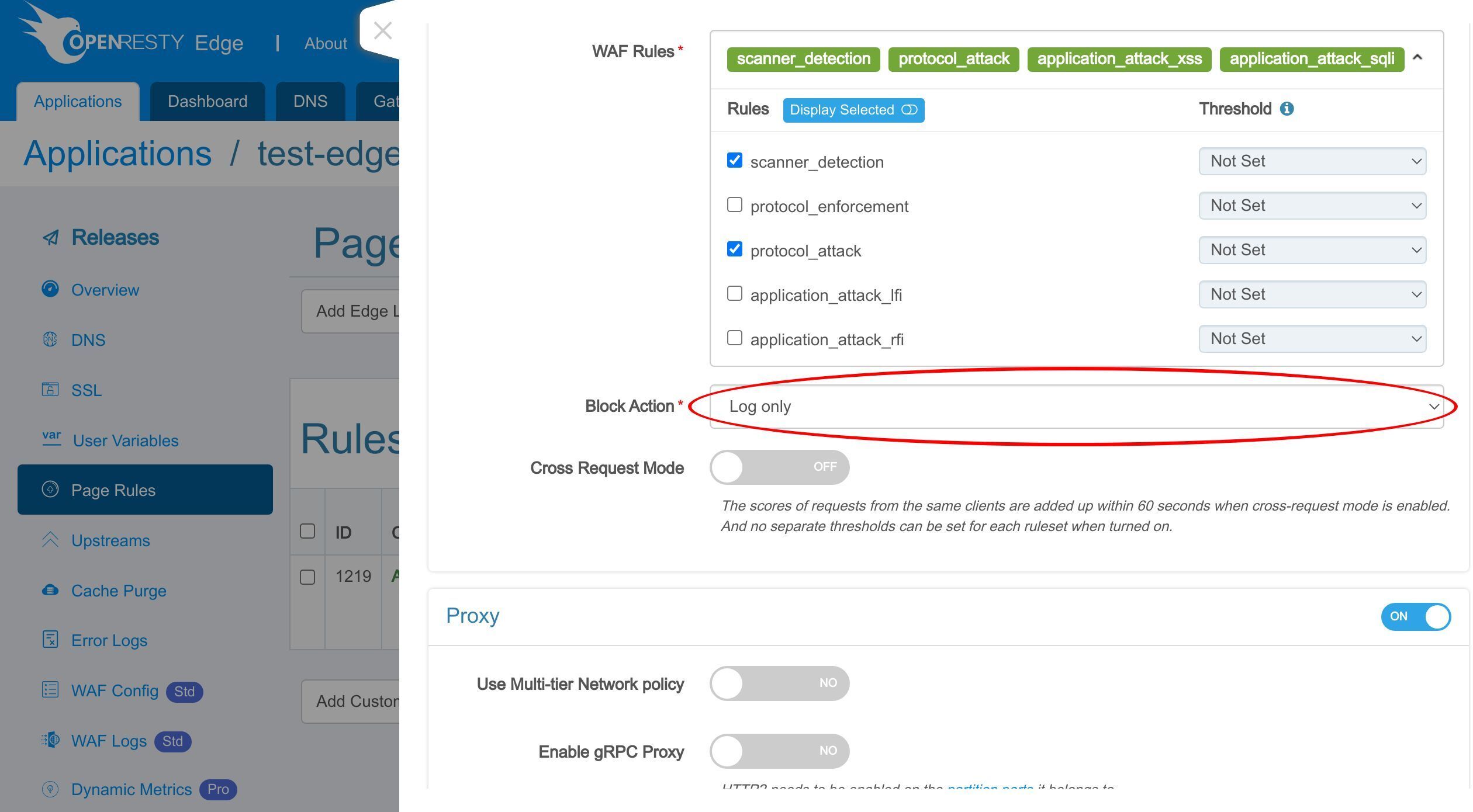
有効にする WAF ルールセットを選択できます。
ここでは、デフォルトのルールセットのみを保持します。
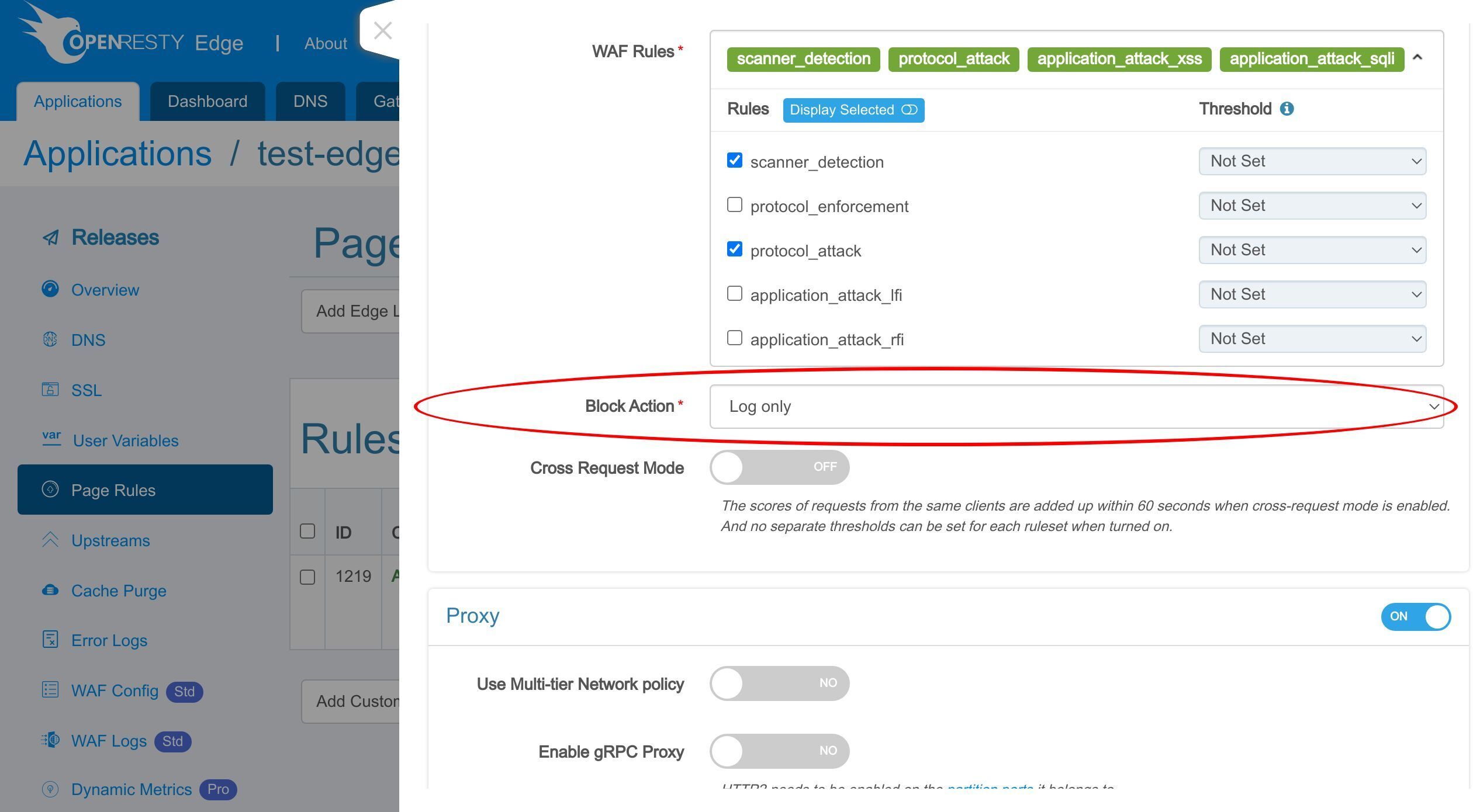
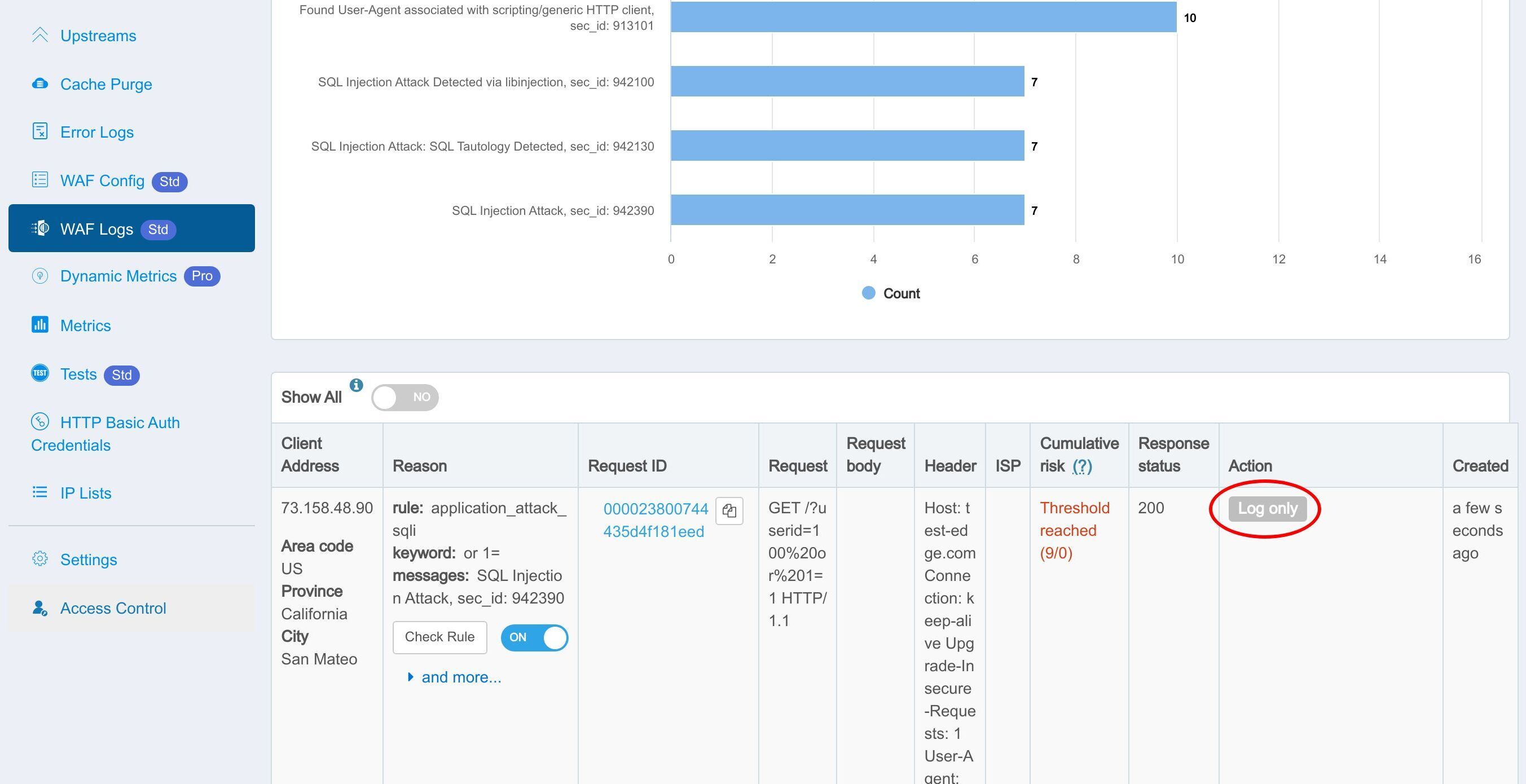
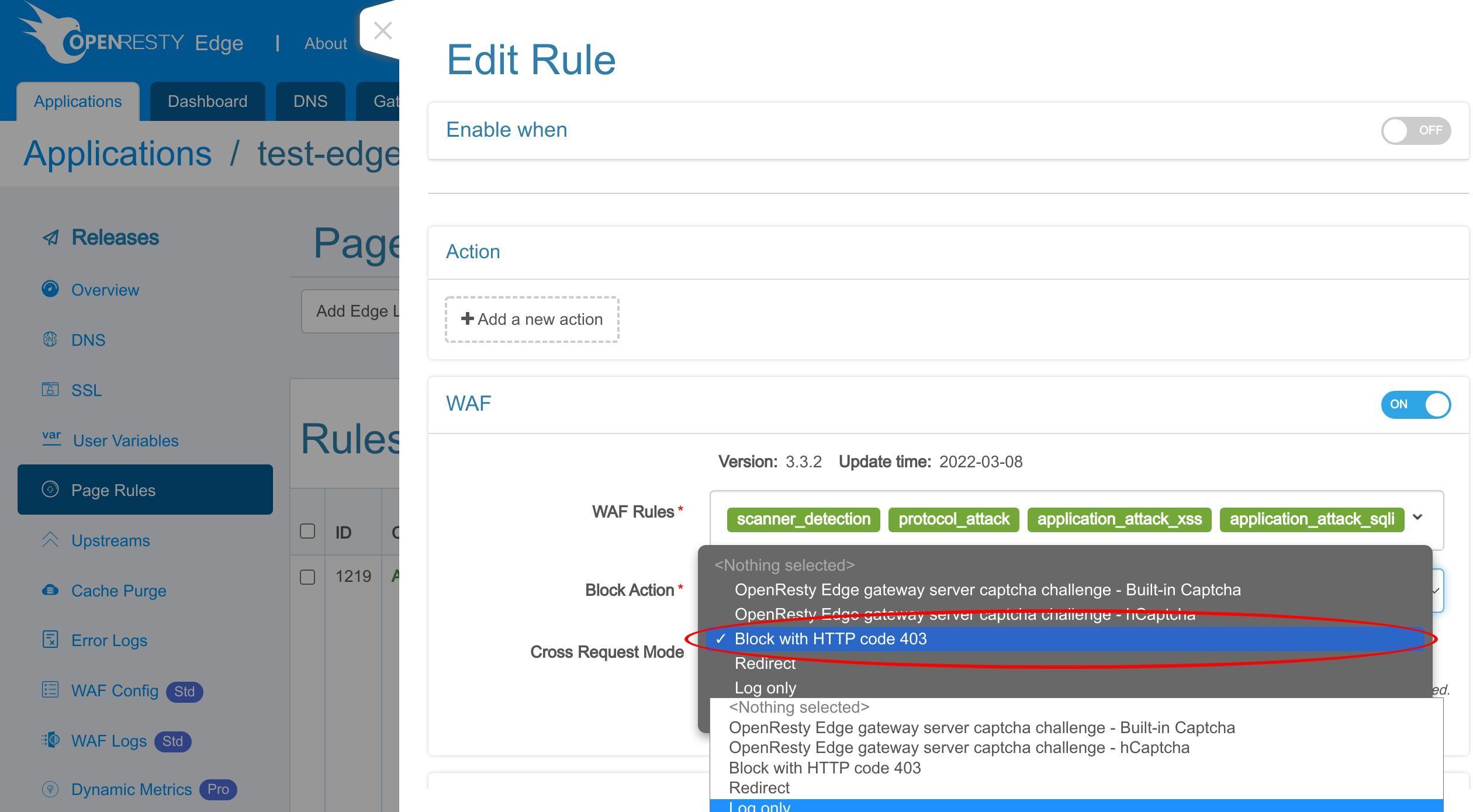
WAF ルールにヒットしたリクエストに対して実行するアクションを選択します。
「Log only」アクションは、リクエスト自体に影響を与えずに WAF ルールをテストするのに役立ちます。
このルールを保存します。
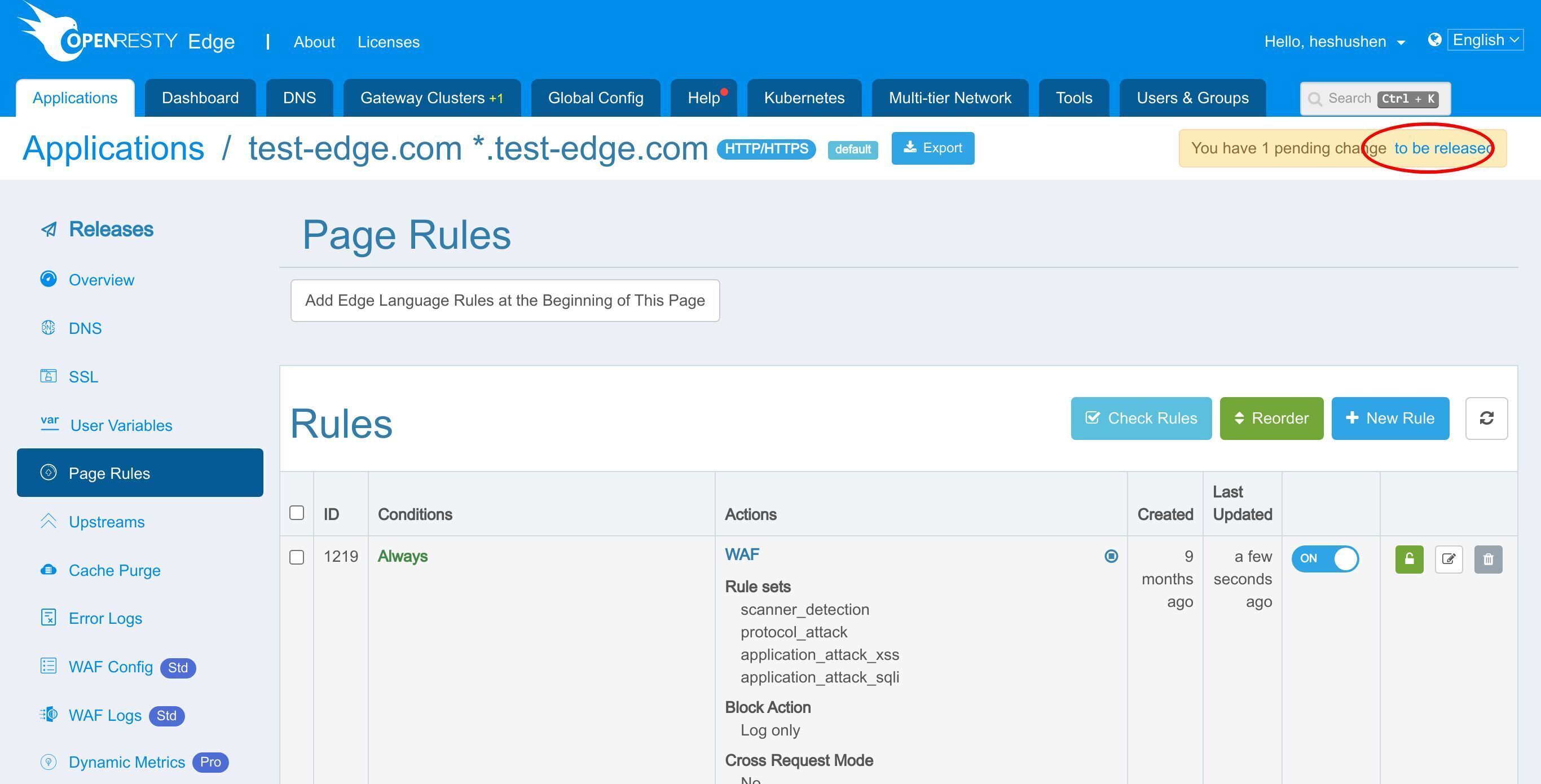
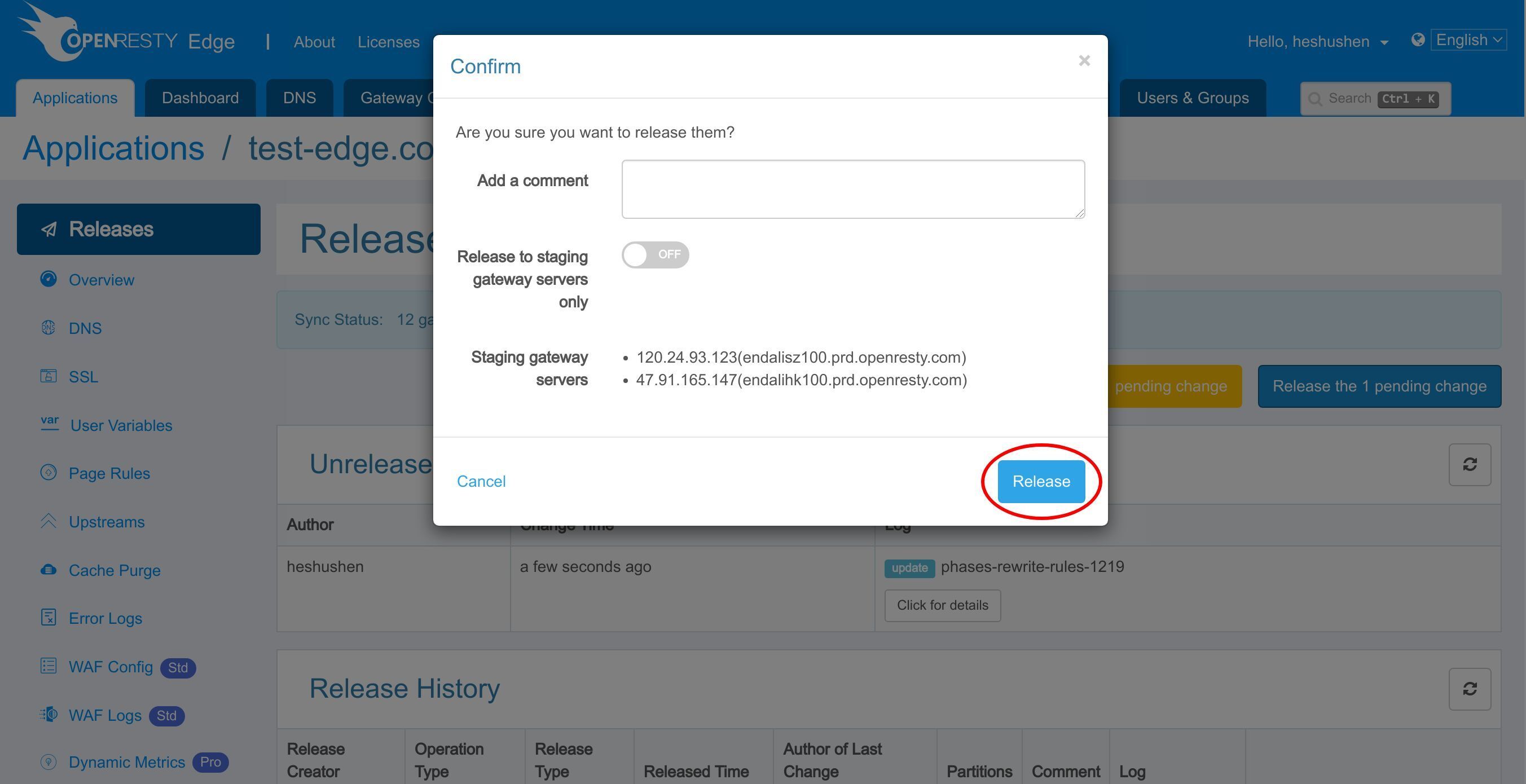
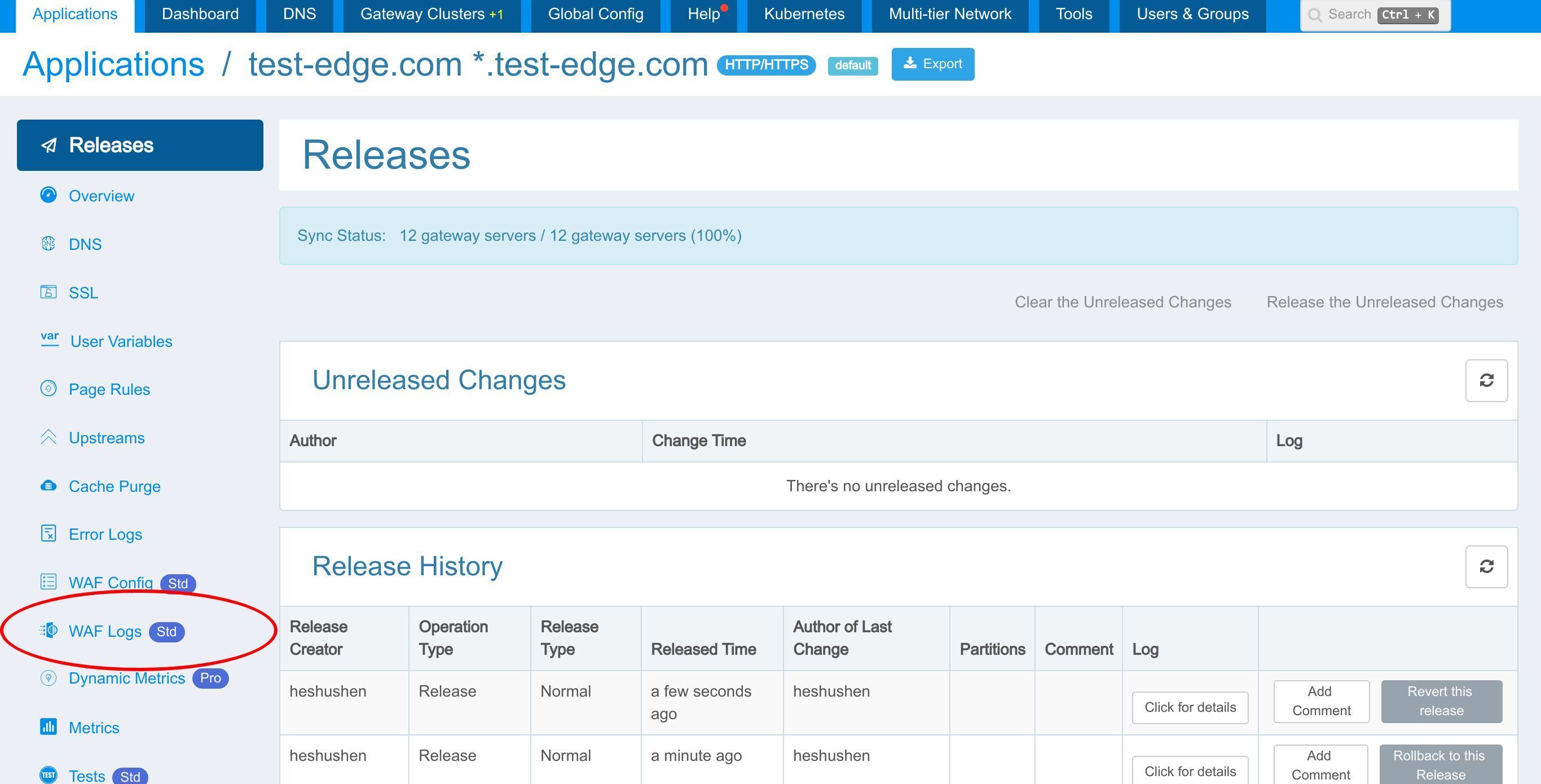
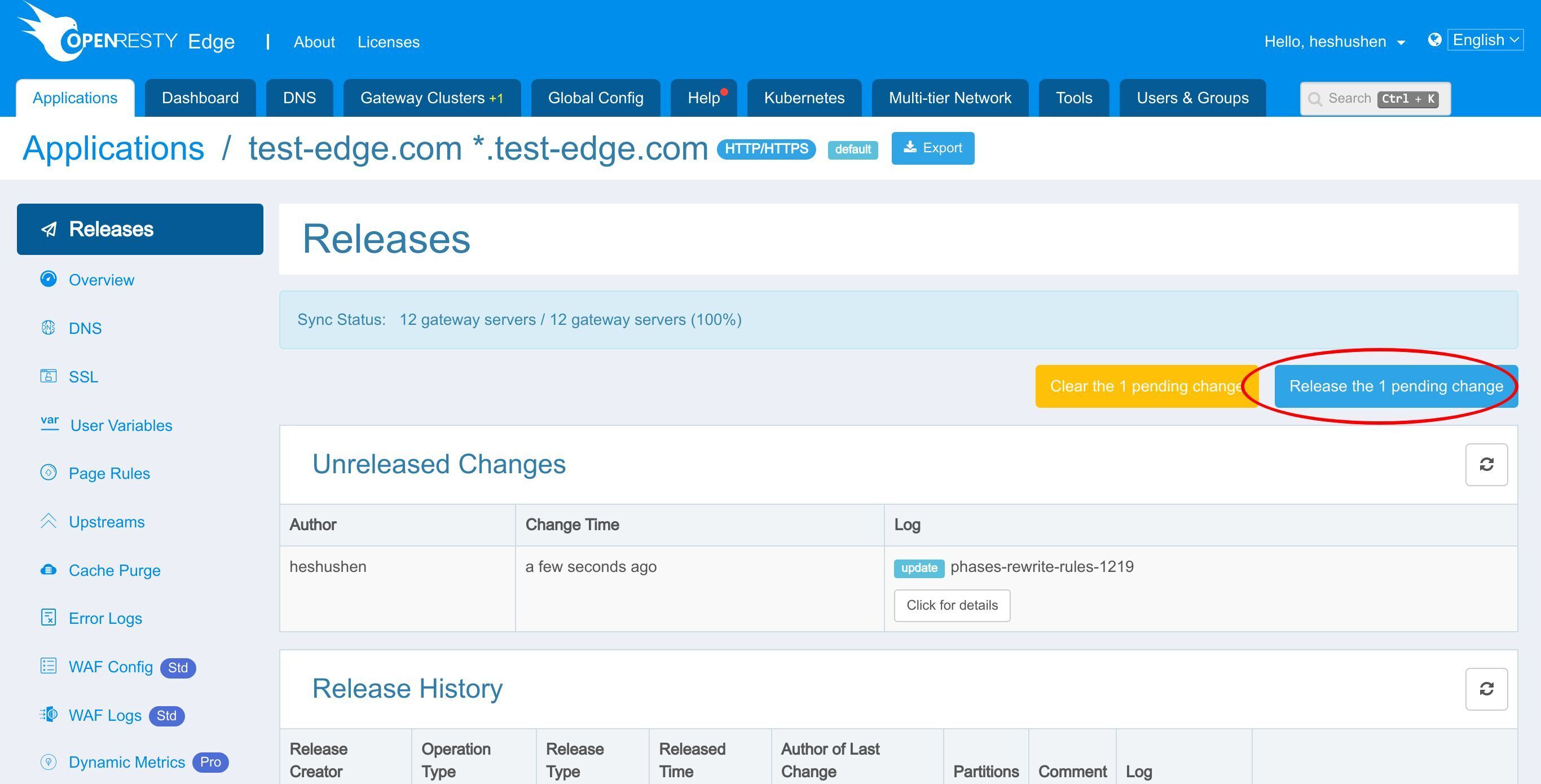
いつもと同様に、先ほどの変更をプッシュするために新しいバージョンをリリースする必要があります。
このボタンをクリックします。
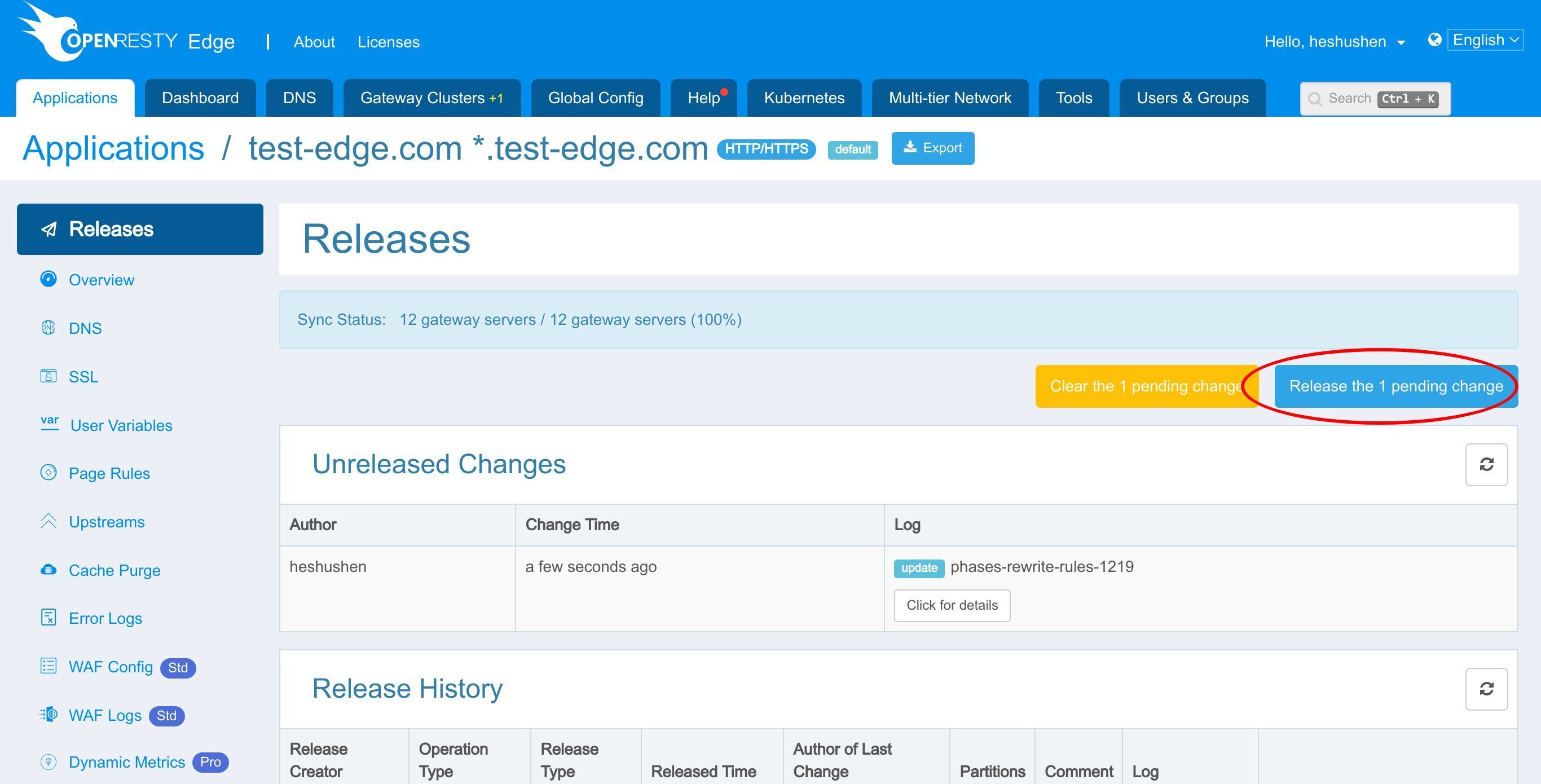
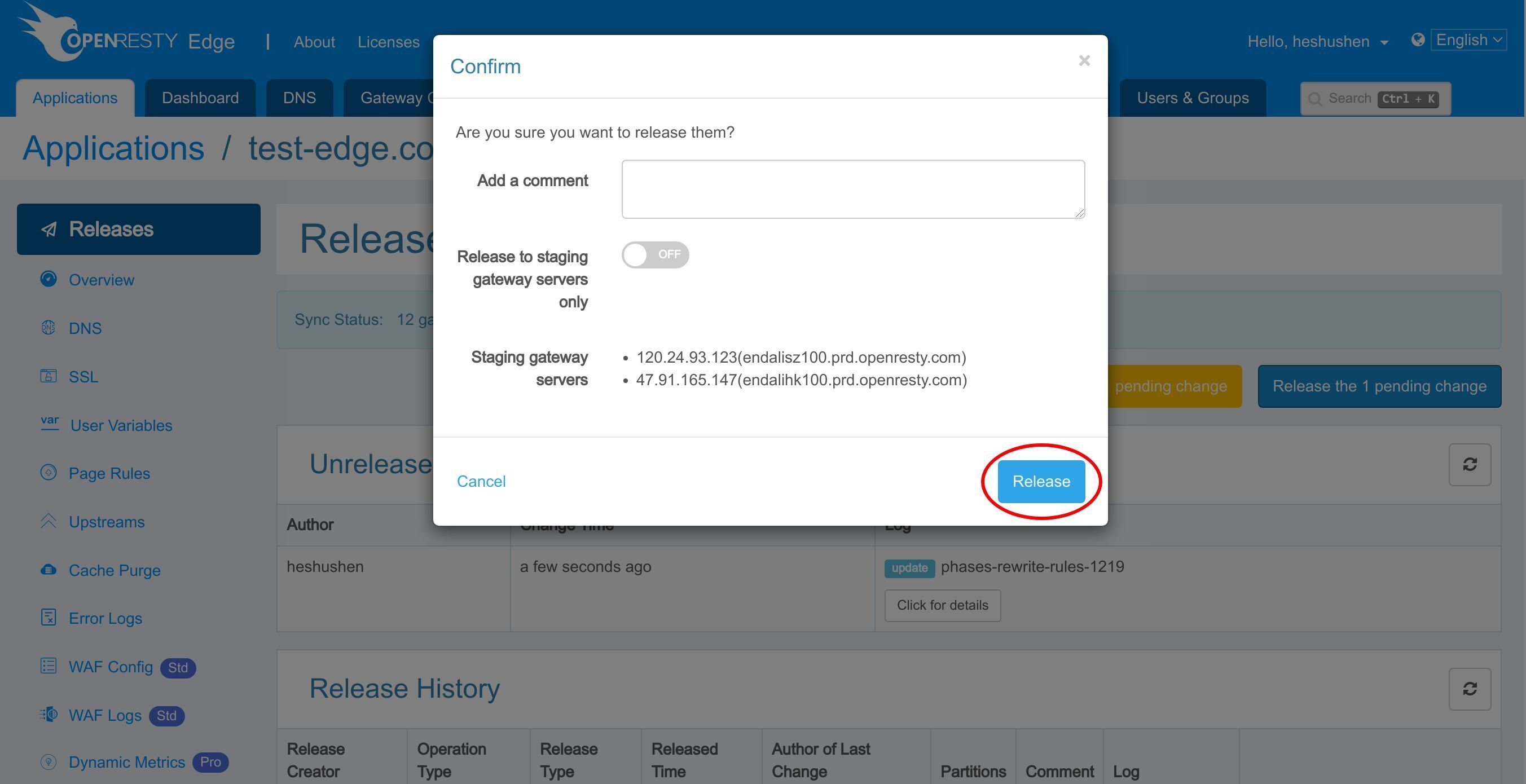
リリースします!
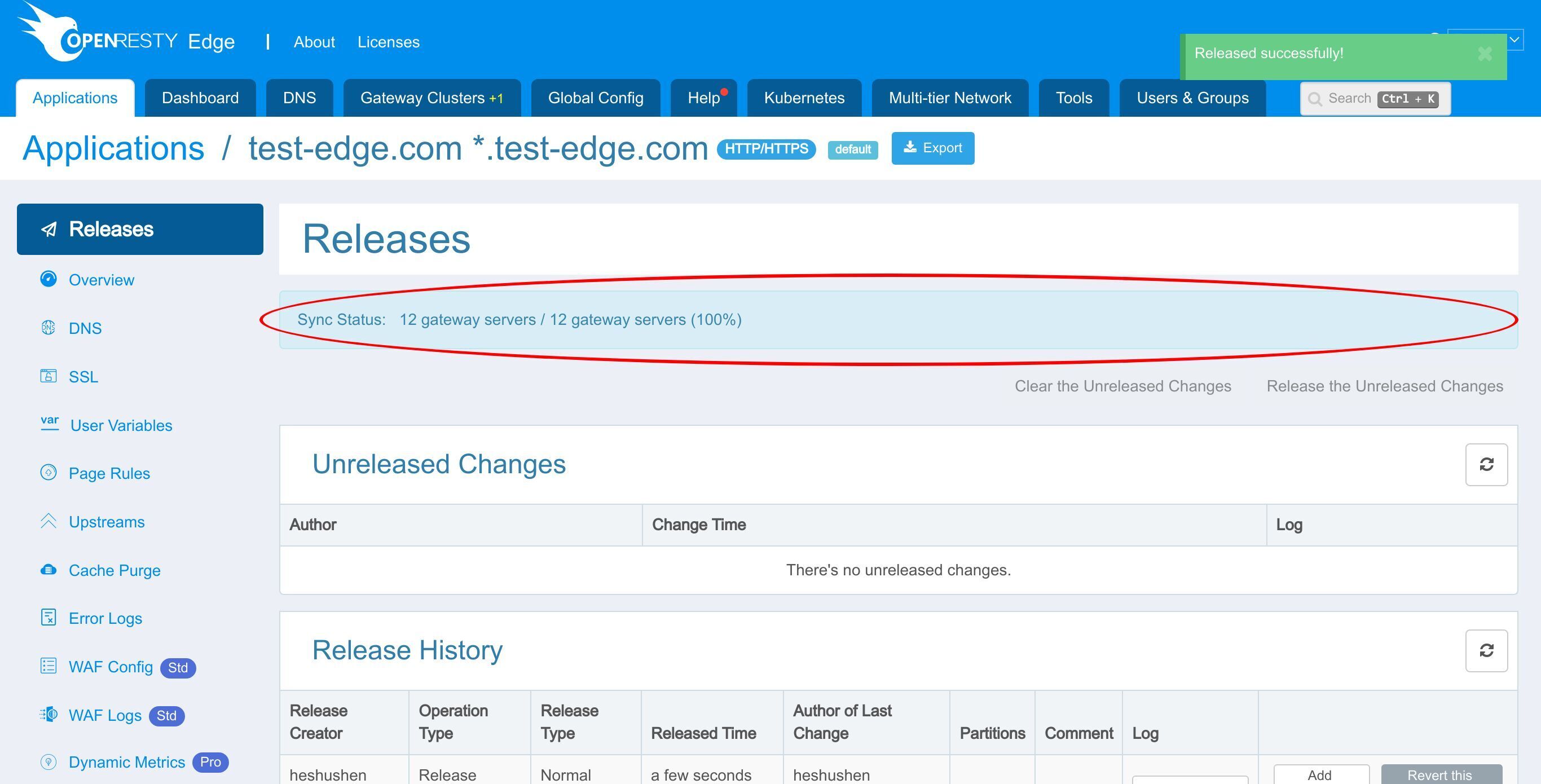
新しいバージョンがすべてのゲートウェイサーバーに同期されました。
これで、新しいページルールがすべてのゲートウェイクラスターとサーバーにプッシュされました。
これらの設定変更には、サーバーのリロード、再起動、またはバイナリアップグレードは必要ありません。そのため、非常に効率的でスケーラブルです。
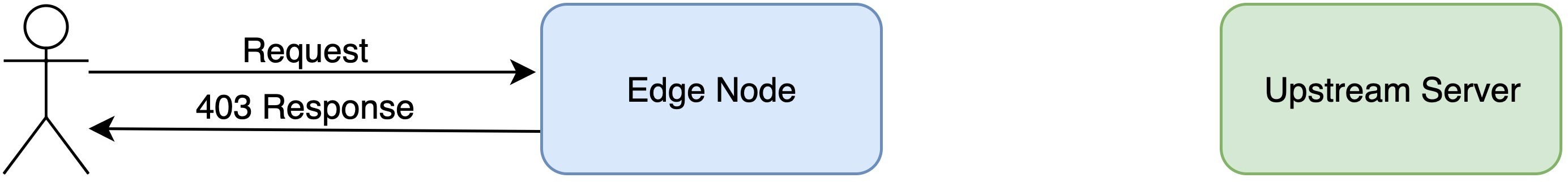
アプリケーションの WAF 設定をテストする
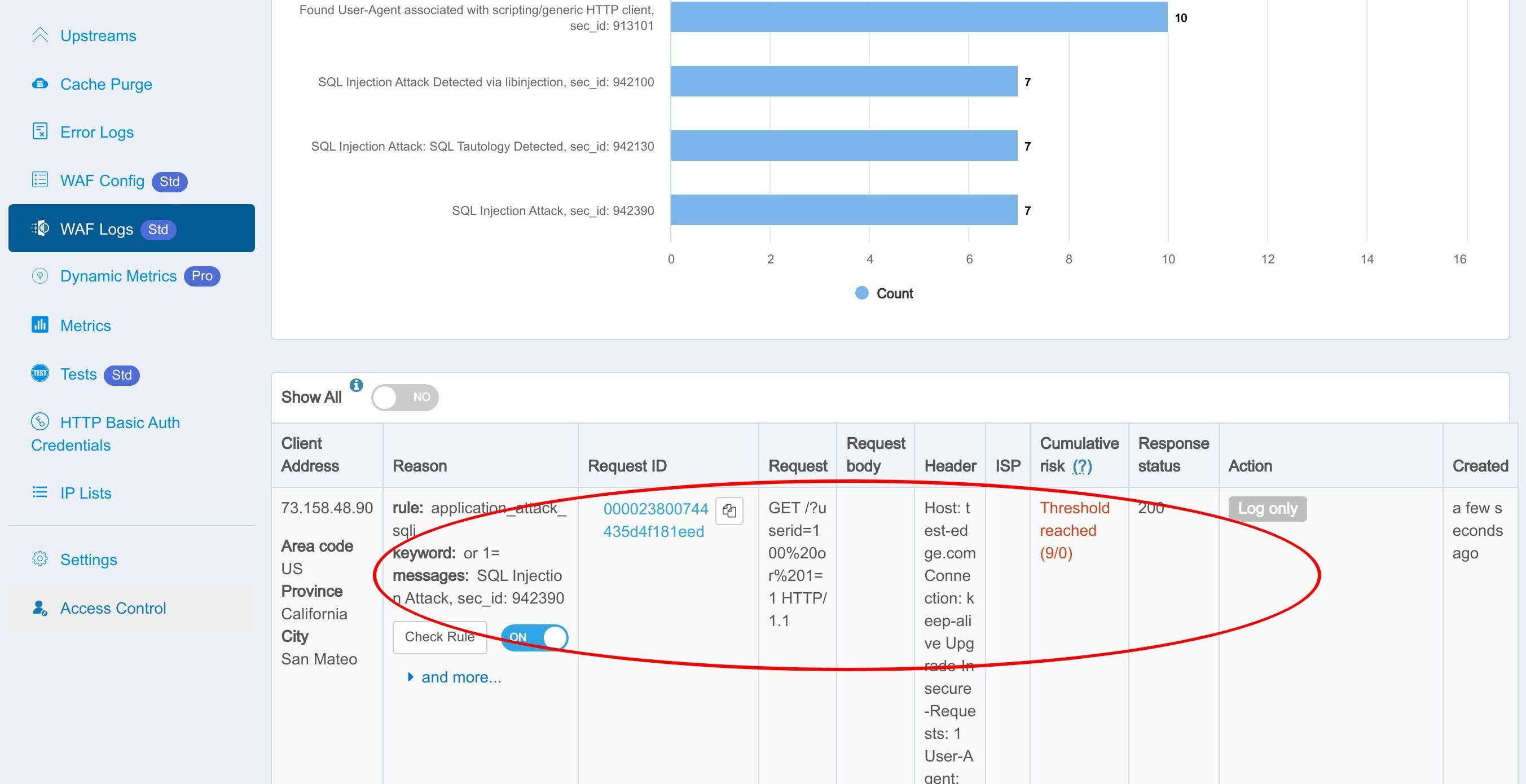
ここで、SQL インジェクションを試みる悪意のあるリクエストを送信してみましょう。
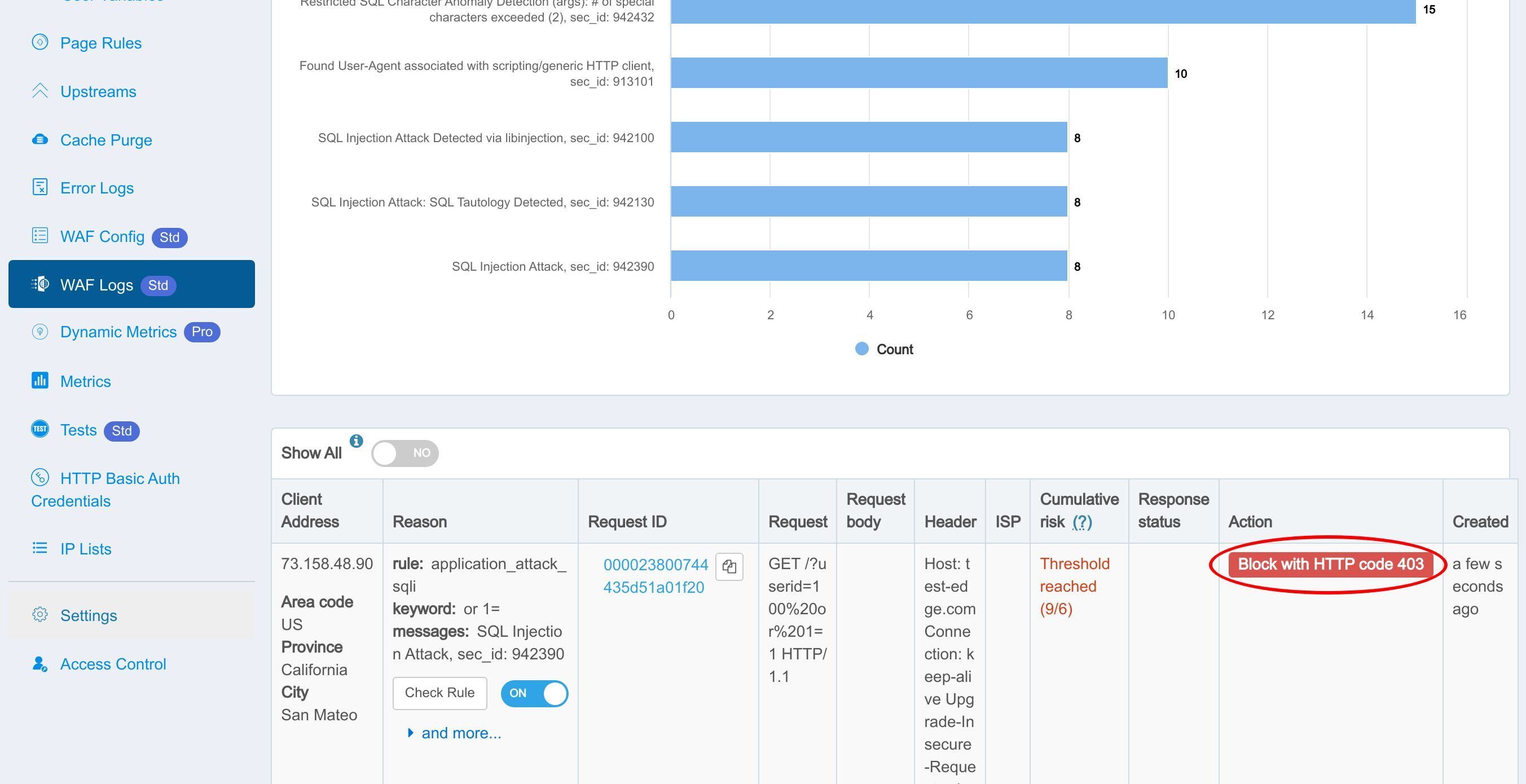
リクエストはオリジンサーバーのデフォルトインデックスページを返します。これは「Log only」アクションを選択したため、予想通りの動作です。Web コンソールで WAF ヒットログを確認しましょう。
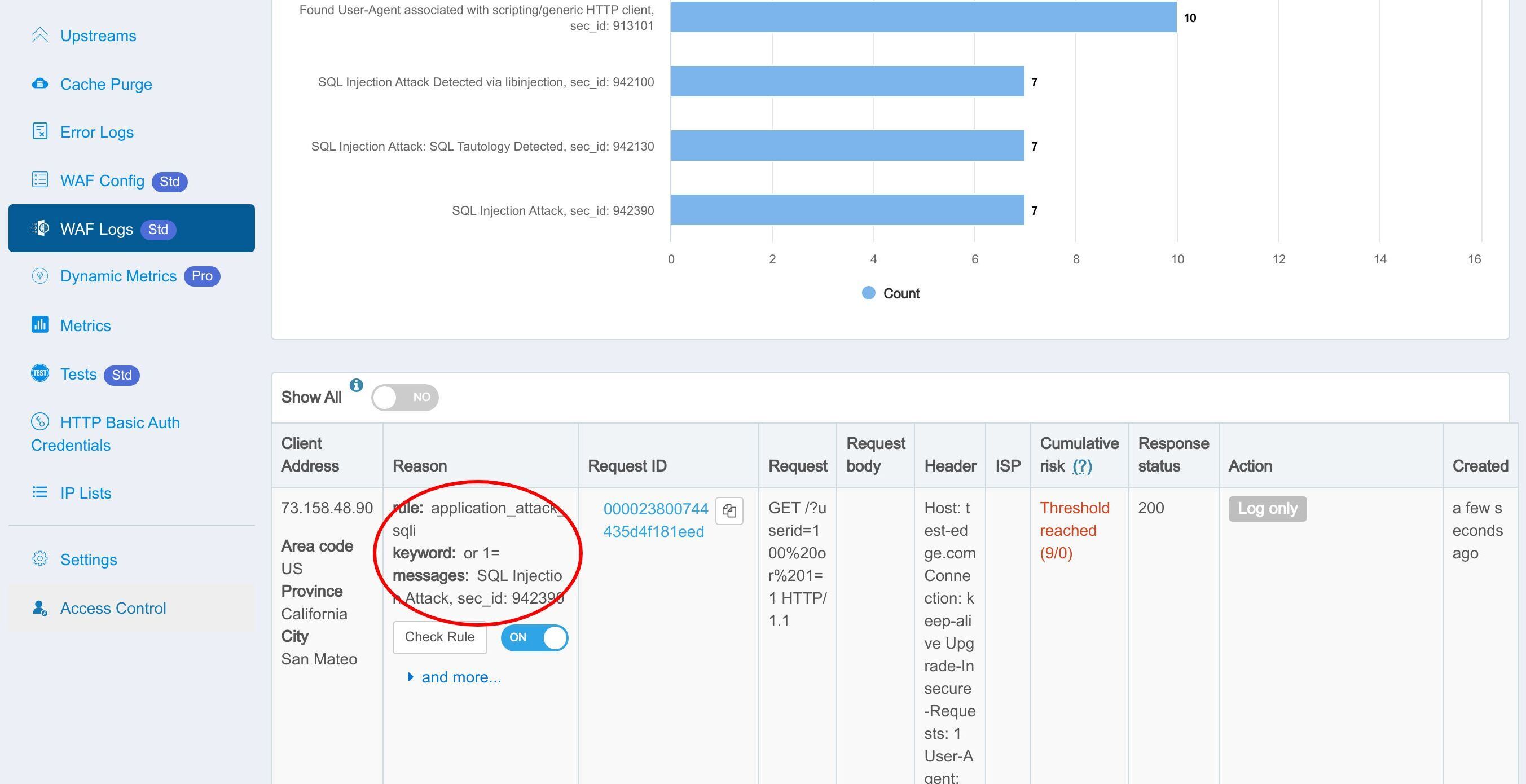
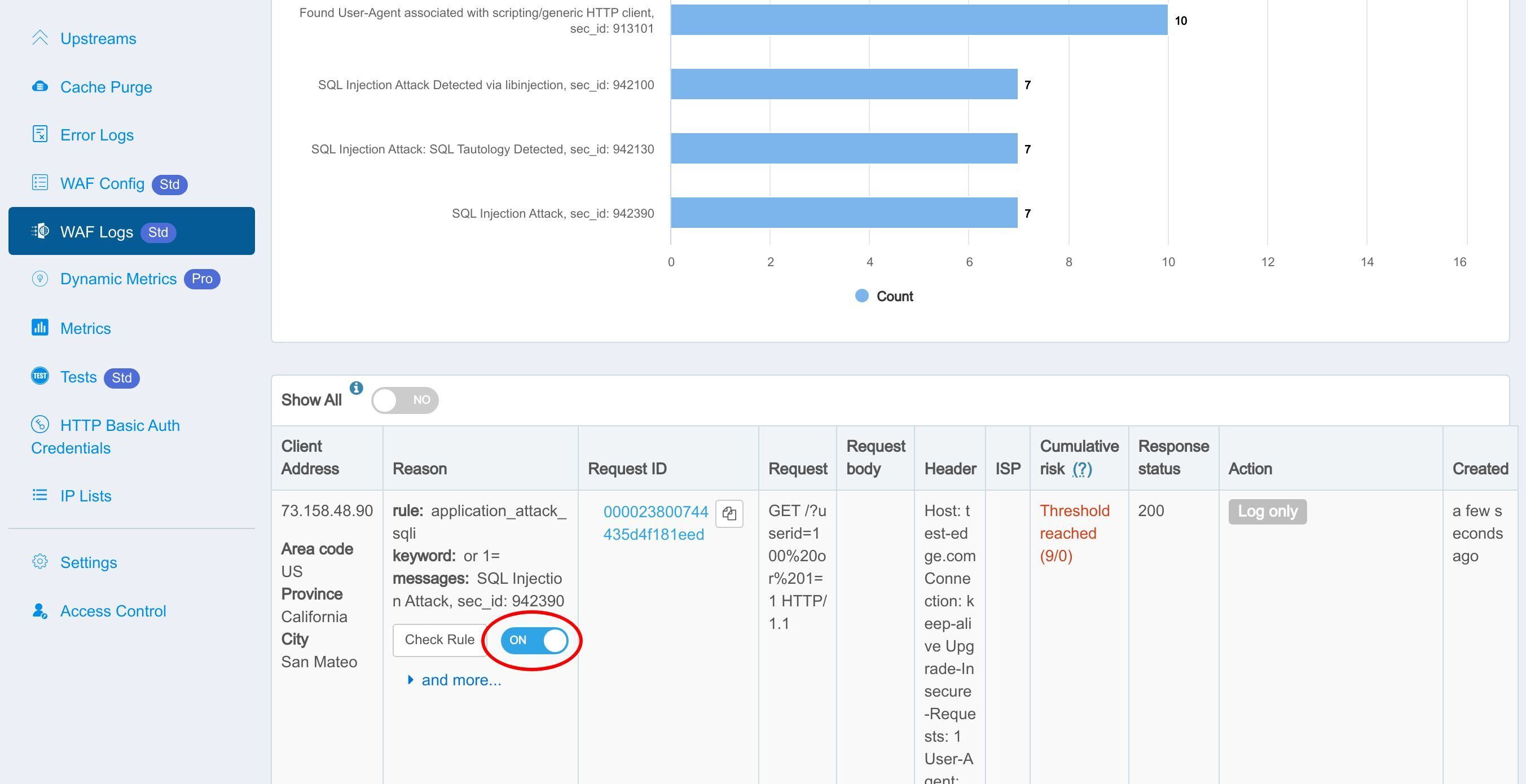
このルールが確かにヒットし、ログに記録されたことがわかります。
この部分は、WAF によってキャプチャされたリクエストの詳細を示しています。
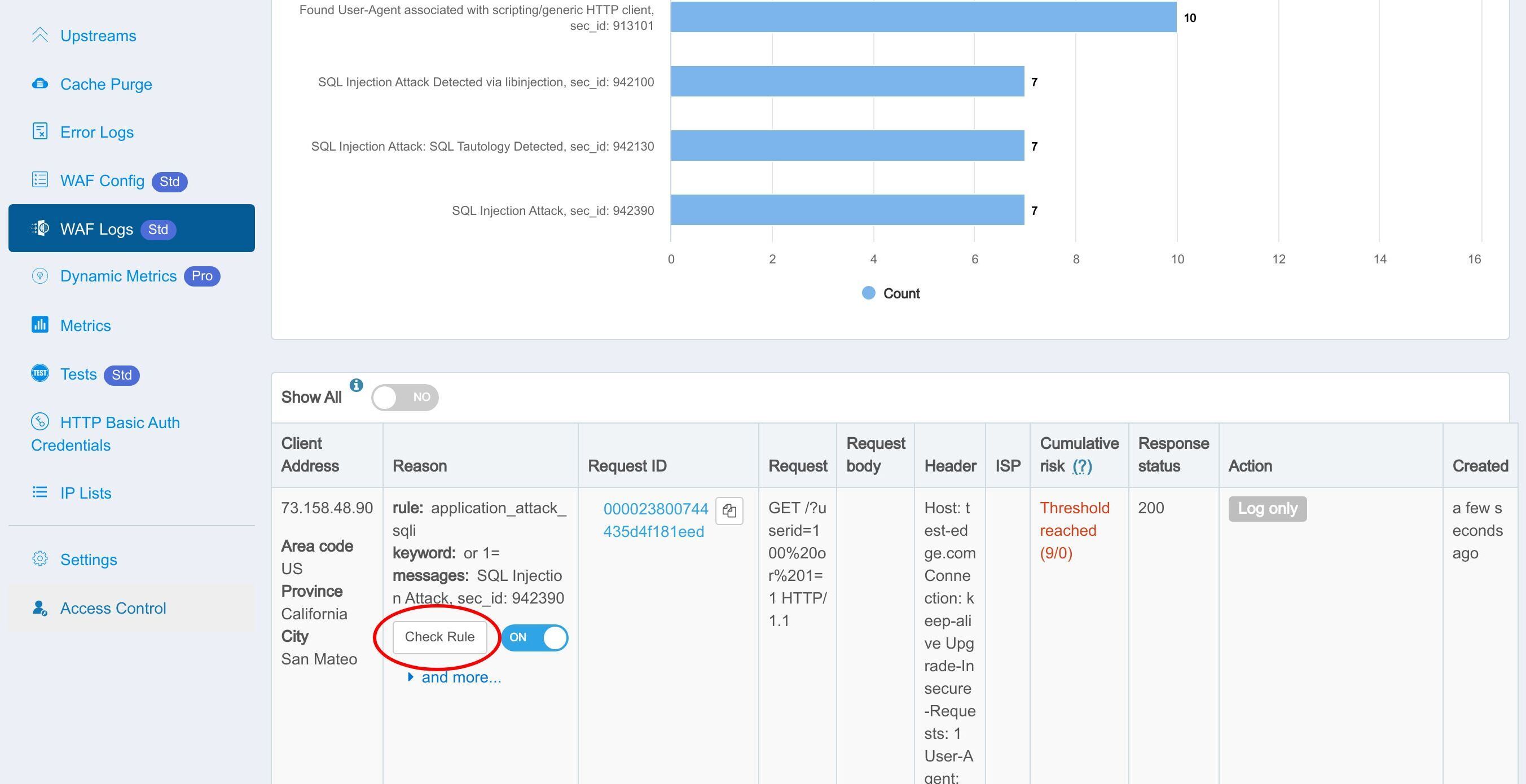
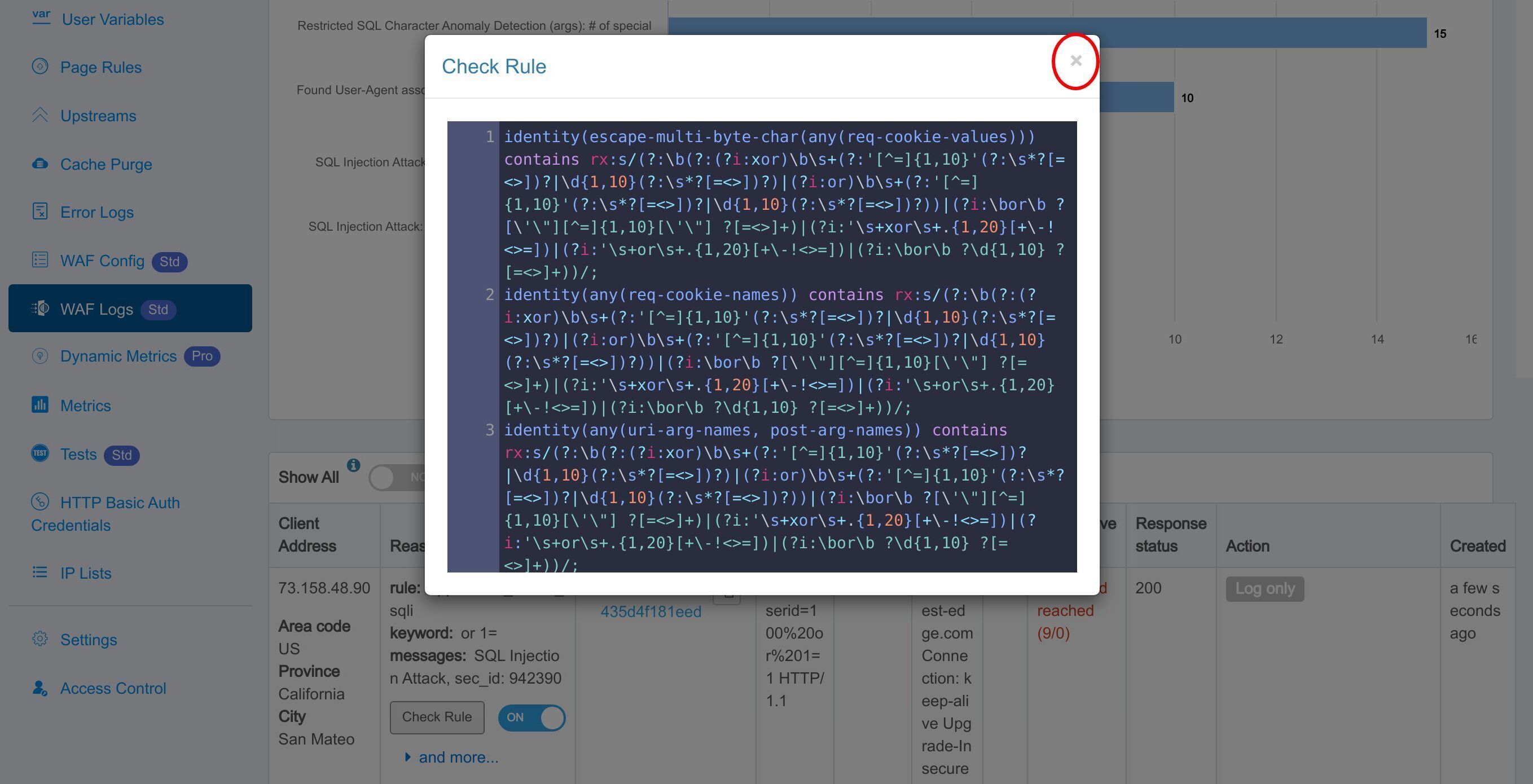
ルールを確認ボタンをクリックして、ヒットした WAF ルールの詳細を確認します。
ここにそのルールの Edgelang 定義が表示されています。
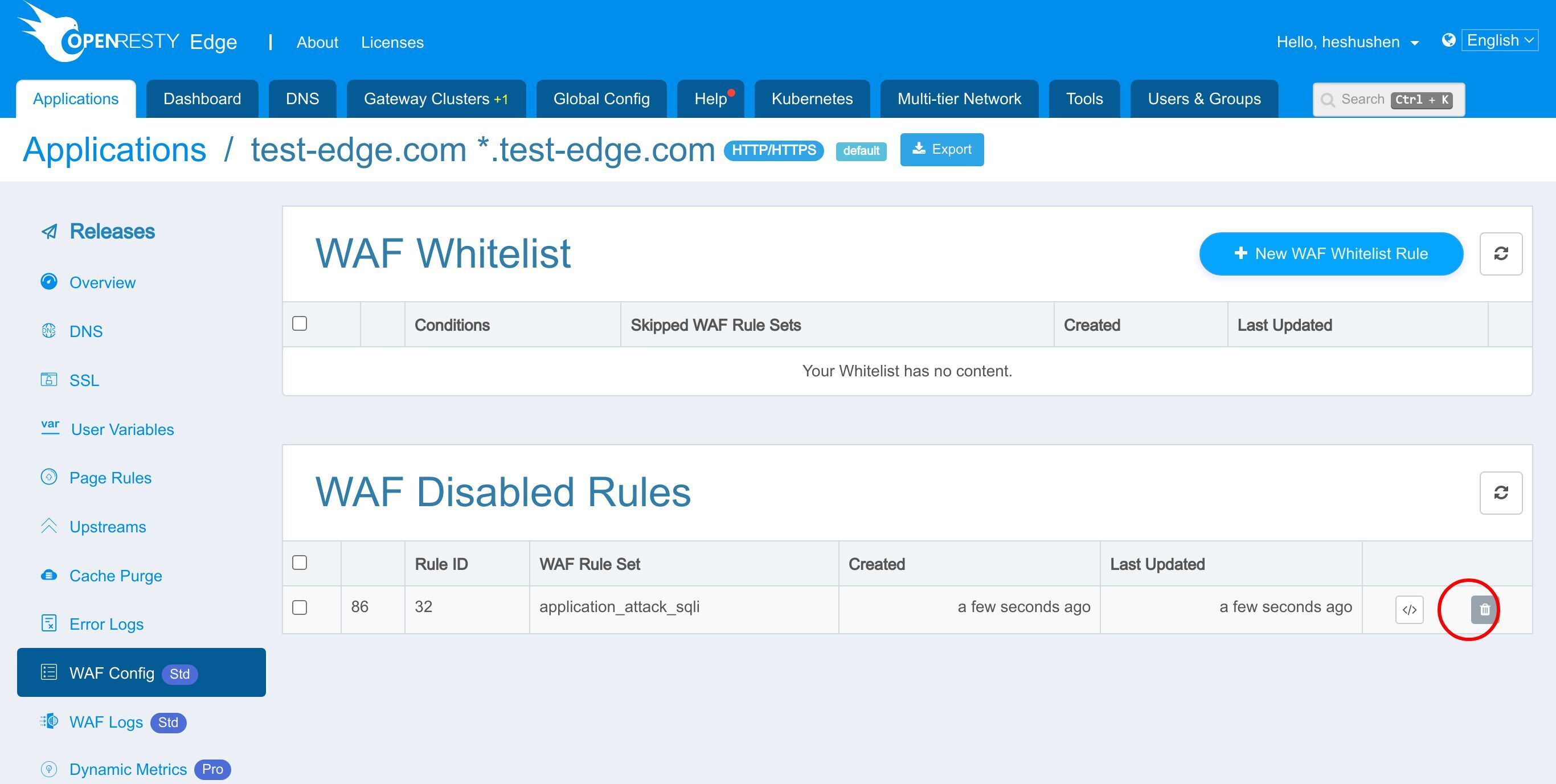
WAF の無効化と再有効化
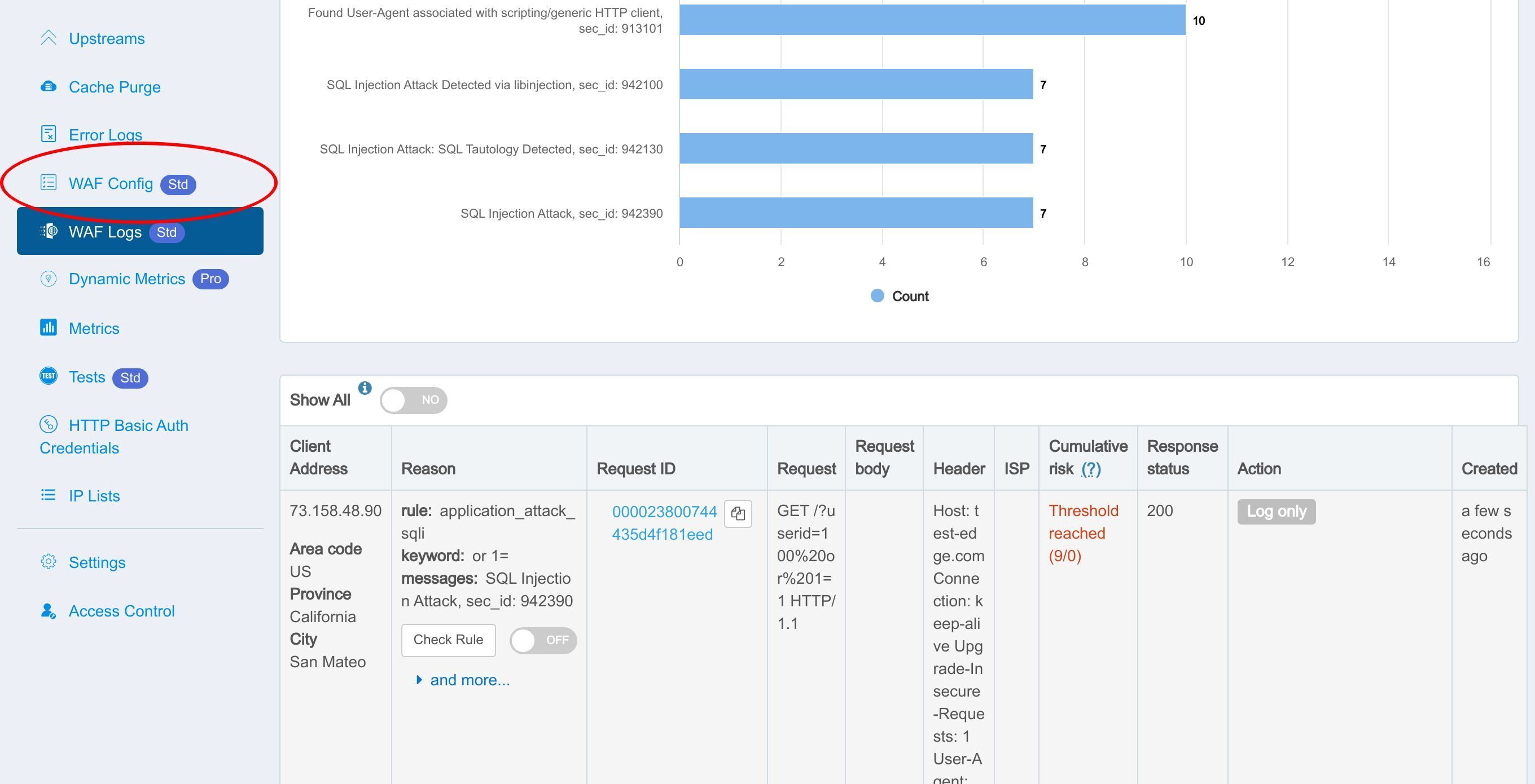
誤検知が発生した場合、このスイッチをオフにして、個別の WAF ルールを無効にすることができます。
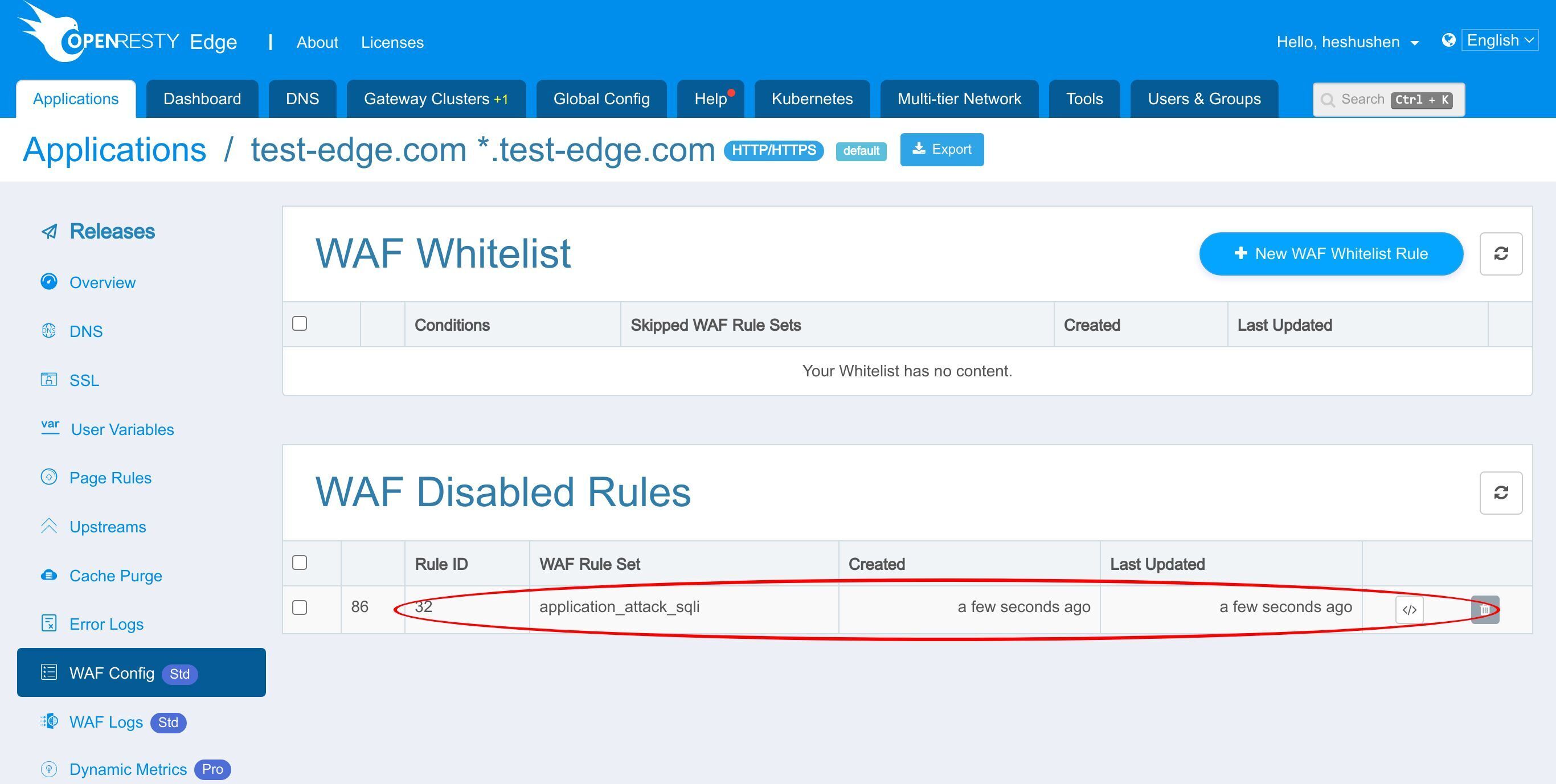
無効化されたルールは WAF 設定ページに表示されます。
ここに無効化されたすべての WAF ルールのリストがあります。
これが先ほど無効にした WAF ルールです。
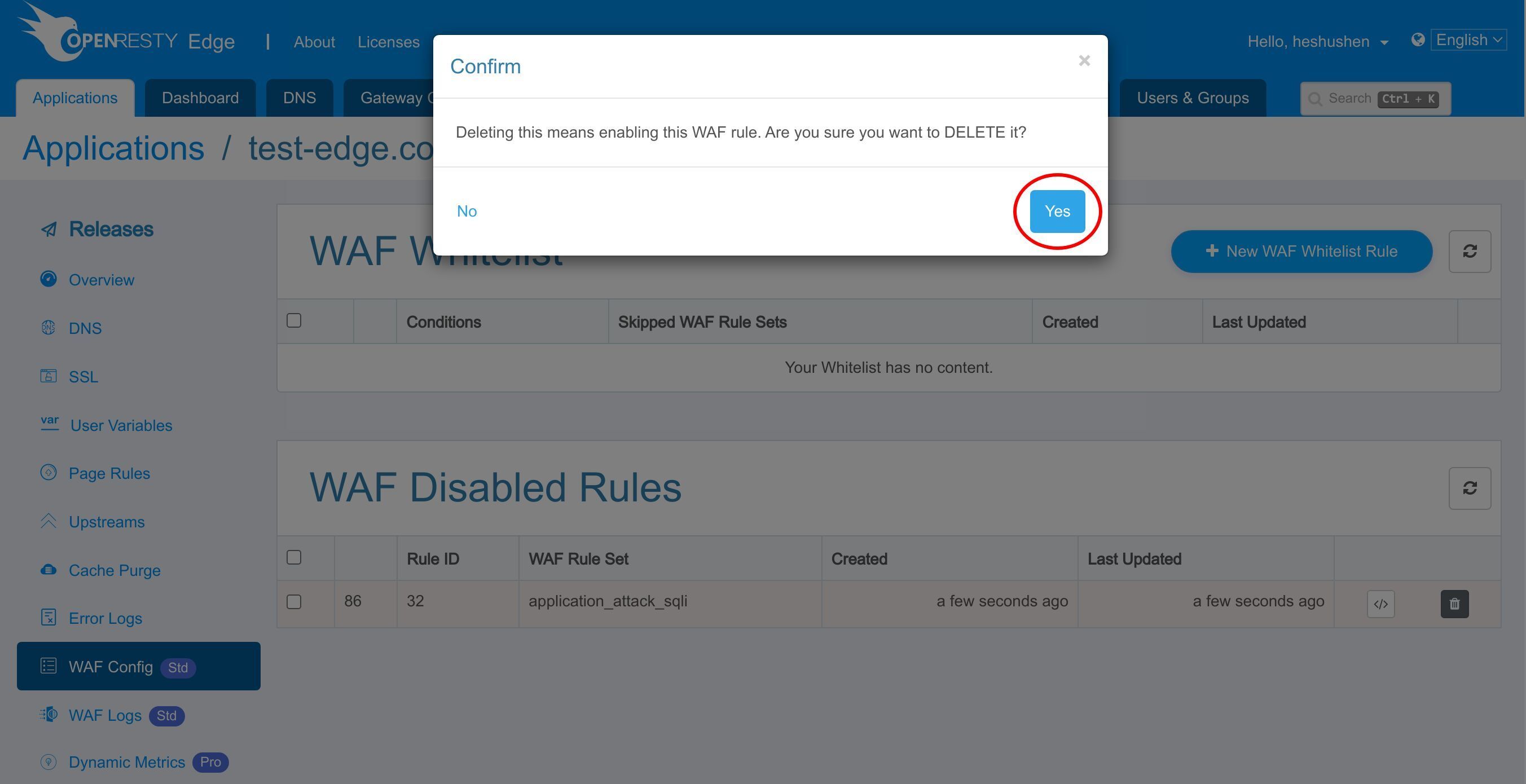
削除ボタンをクリックすると、このルールを再度有効にすることができます。
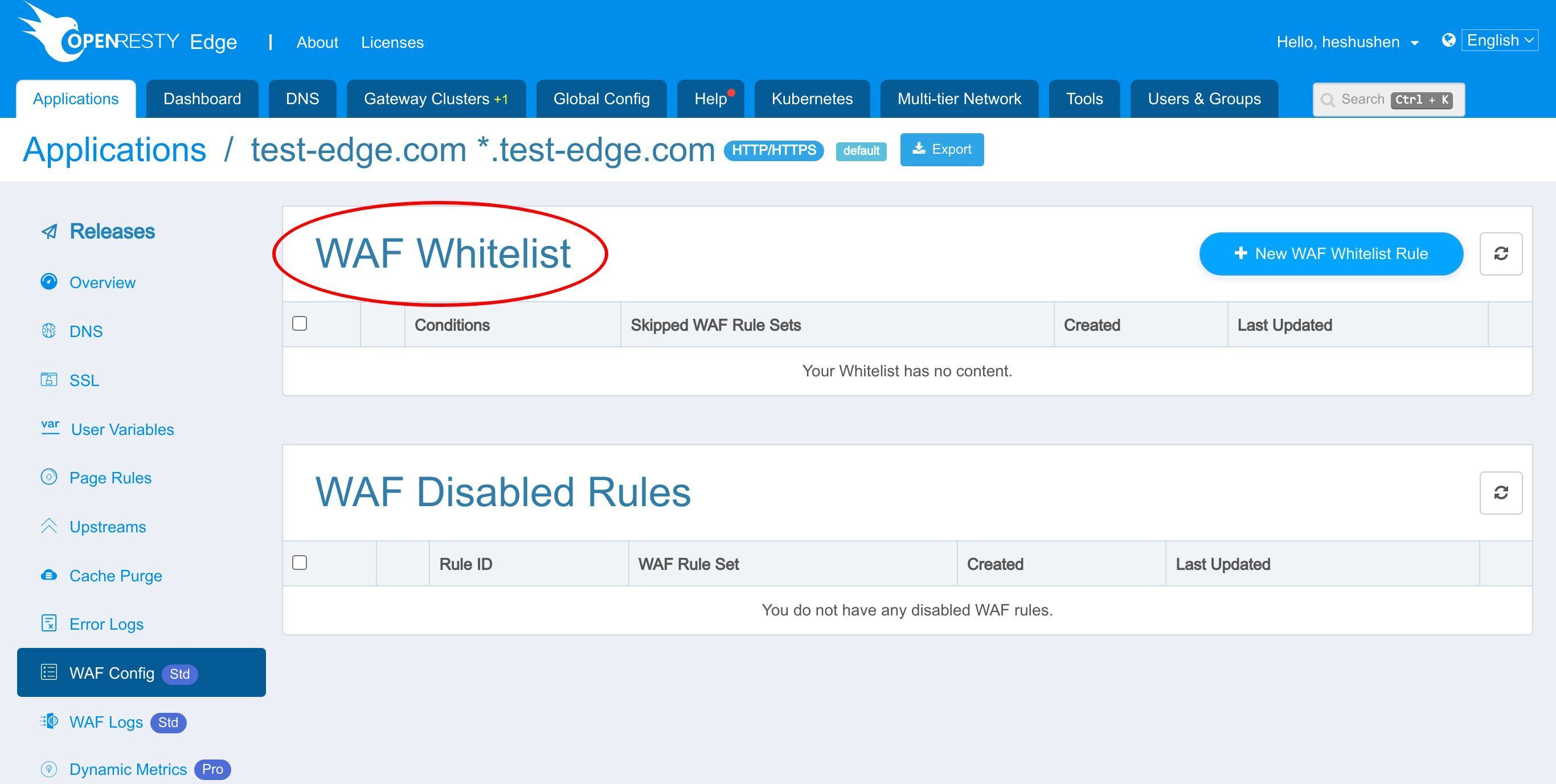
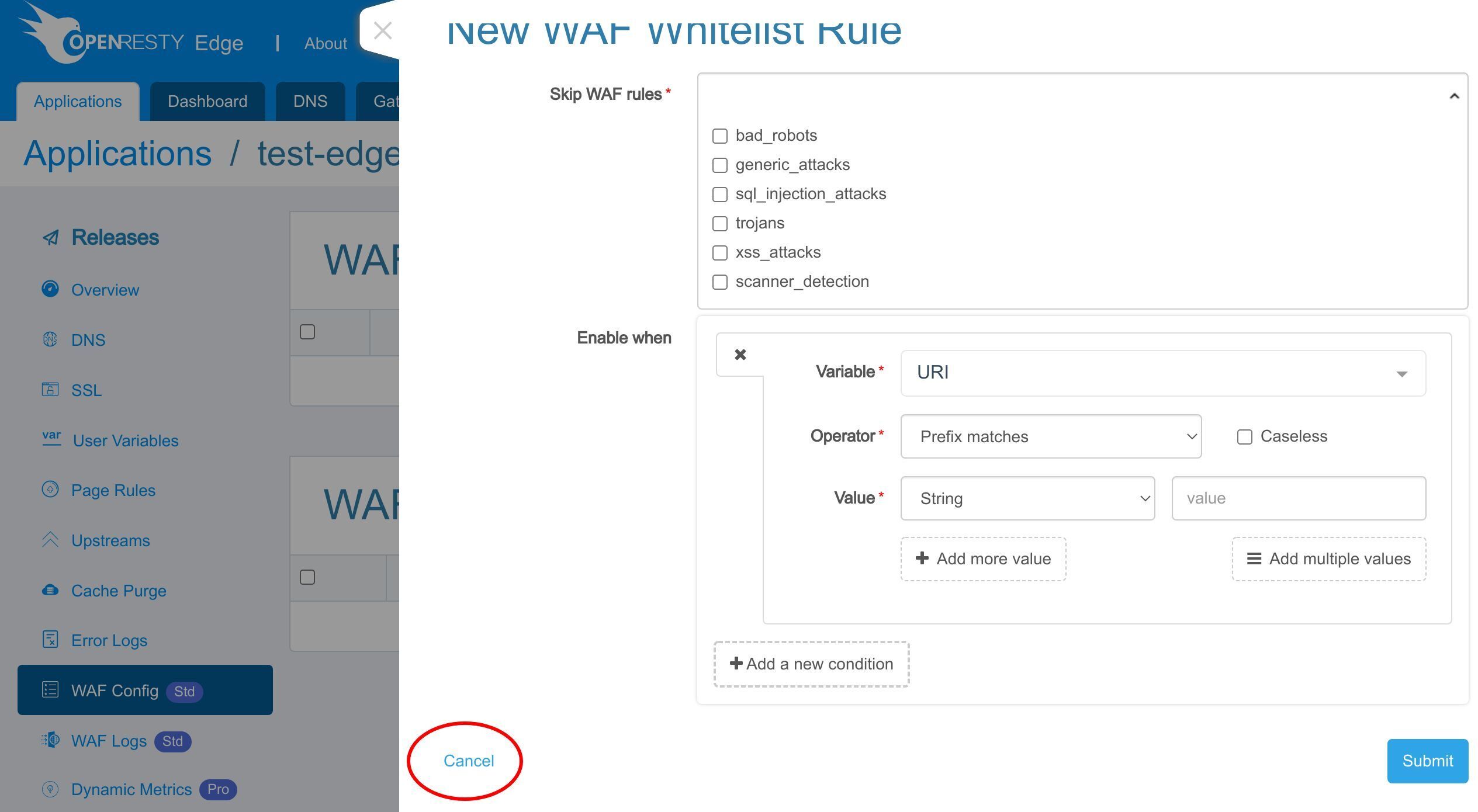
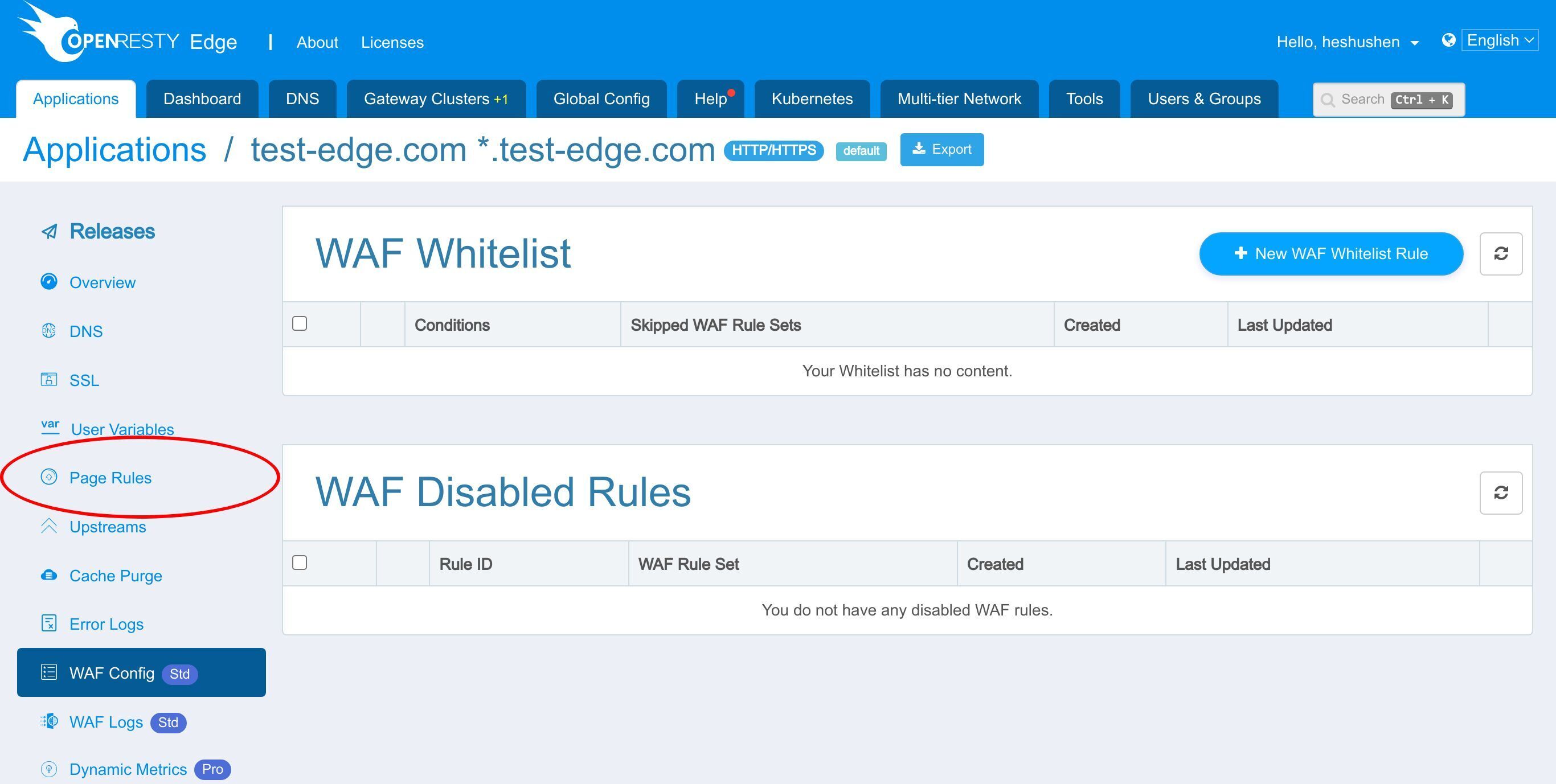
WAF ホワイトリスト
さらに、CPU リソースを節約するために、WAF をバイパスすべきすべてのリクエストを列挙する WAF ホワイトリストを追加することができます。
例えば、通常、静的リソースに WAF フィルタリングを使用する必要はありません。これらのリソースをスキップすることで、サーバーのオーバーヘッドを減らすことができます。
WAF ヒット後のブロックアクションの変更
今回は、「Log only」アクションを別のものに変更しましょう。例えば、403 エラーレスポンスを返すようにします。
Page Rule ページに戻ります。
再度ページルールを編集します。
アクションを変更します。
今回は悪意のあるリクエストをブロックします。
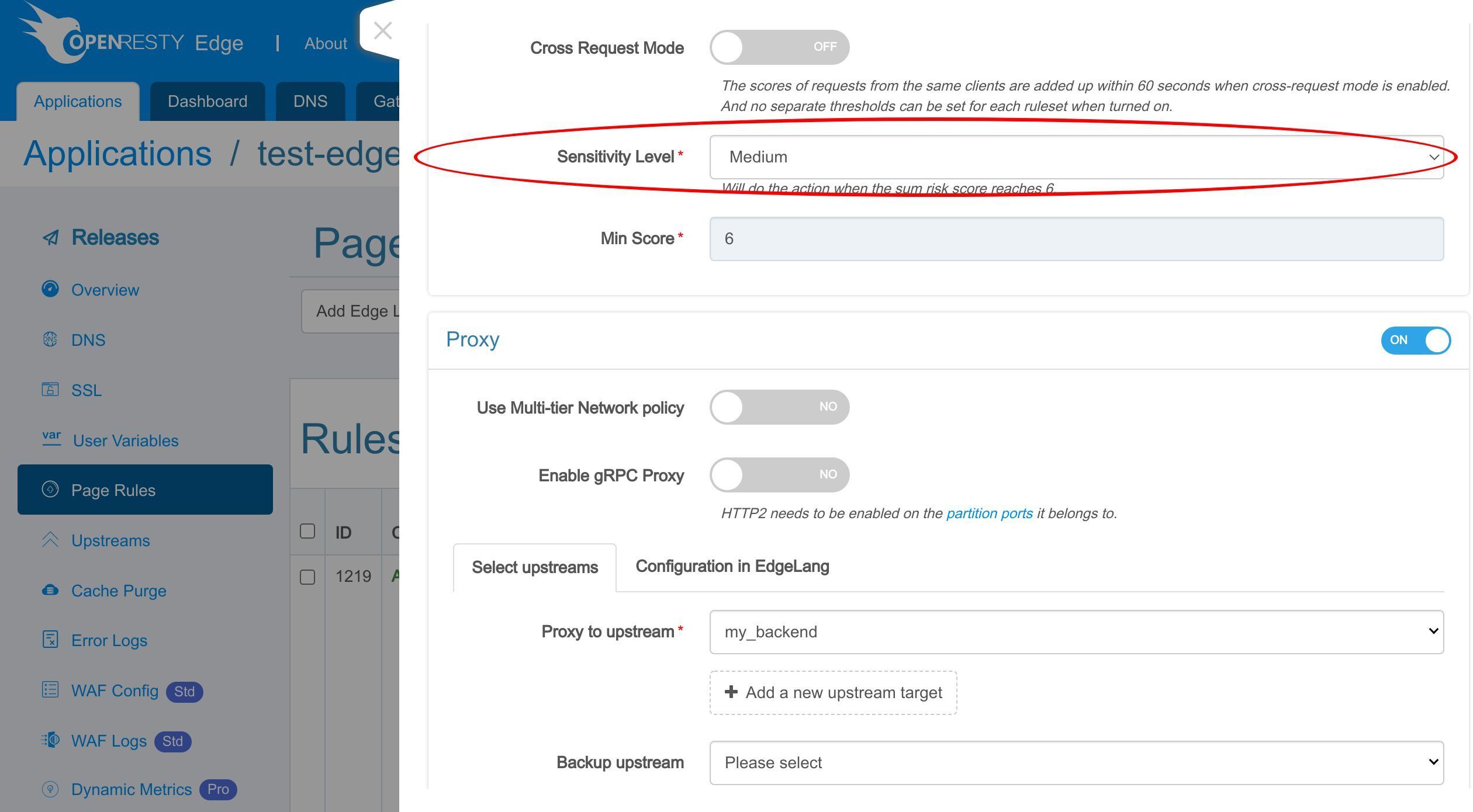
ここで感度レベルを設定できます。
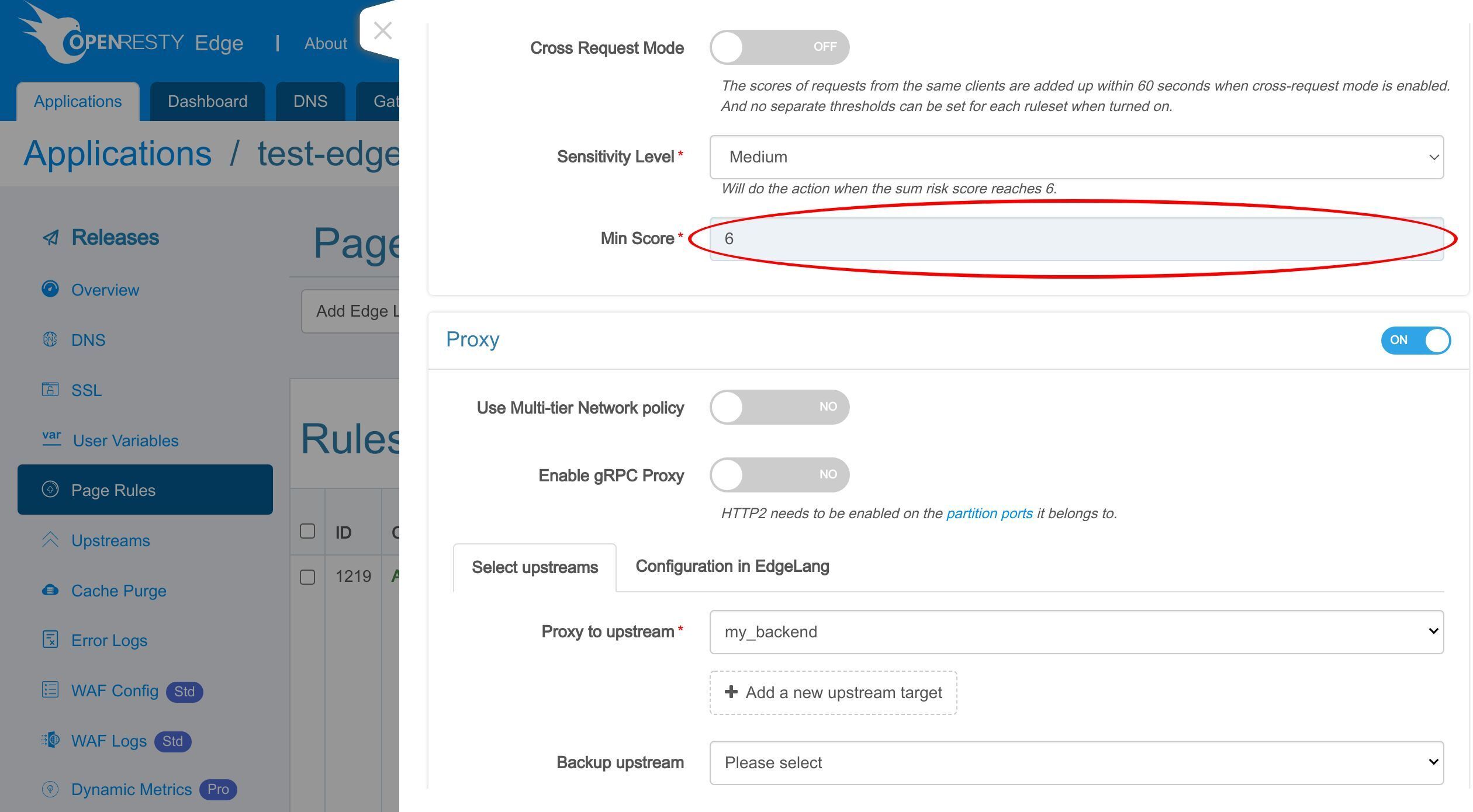
また、スコアしきい値を設定することもできます。
これは、ヒットしたすべての WAF ルールのリスクスコアの合計です。先ほど設定したアクションは、合計スコアがしきい値に達した場合にのみ実行されます。このルールを保存します。
再度、設定の変更をリリースします。
新しいブロックアクションのテスト
再度、悪意のあるリクエストを送信します。
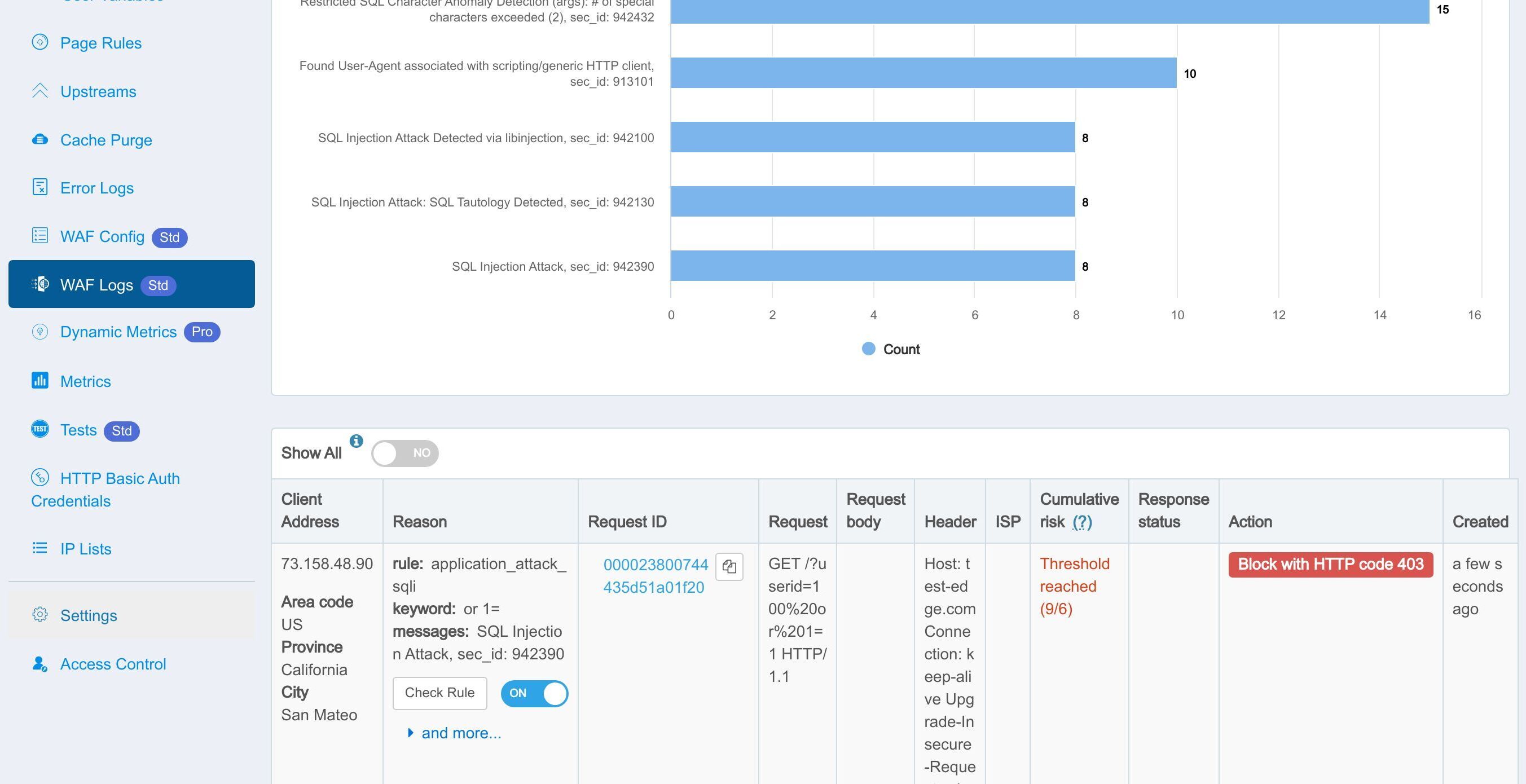
今回、サーバーは「403 Forbidden」レスポンスを返しました。
WAF のログページをもう一度確認しましょう。
ここに記録されたアクションは確かに「HTTP コード 403 でブロック」となっています。
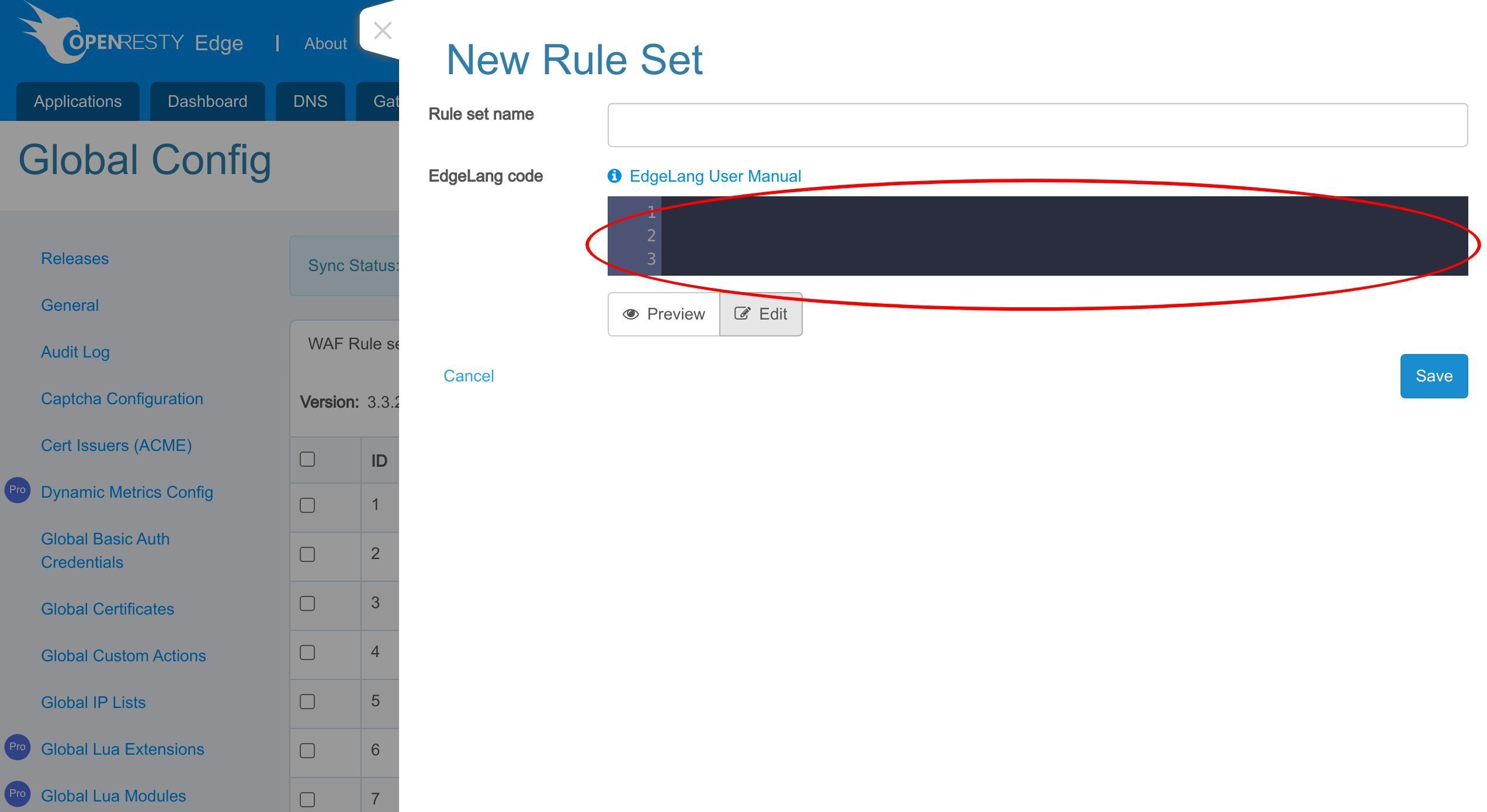
WAF ルールセットの作成
WAF プラットフォームは非常に柔軟で拡張可能です。独自の WAF ルールセットを作成することもできます。
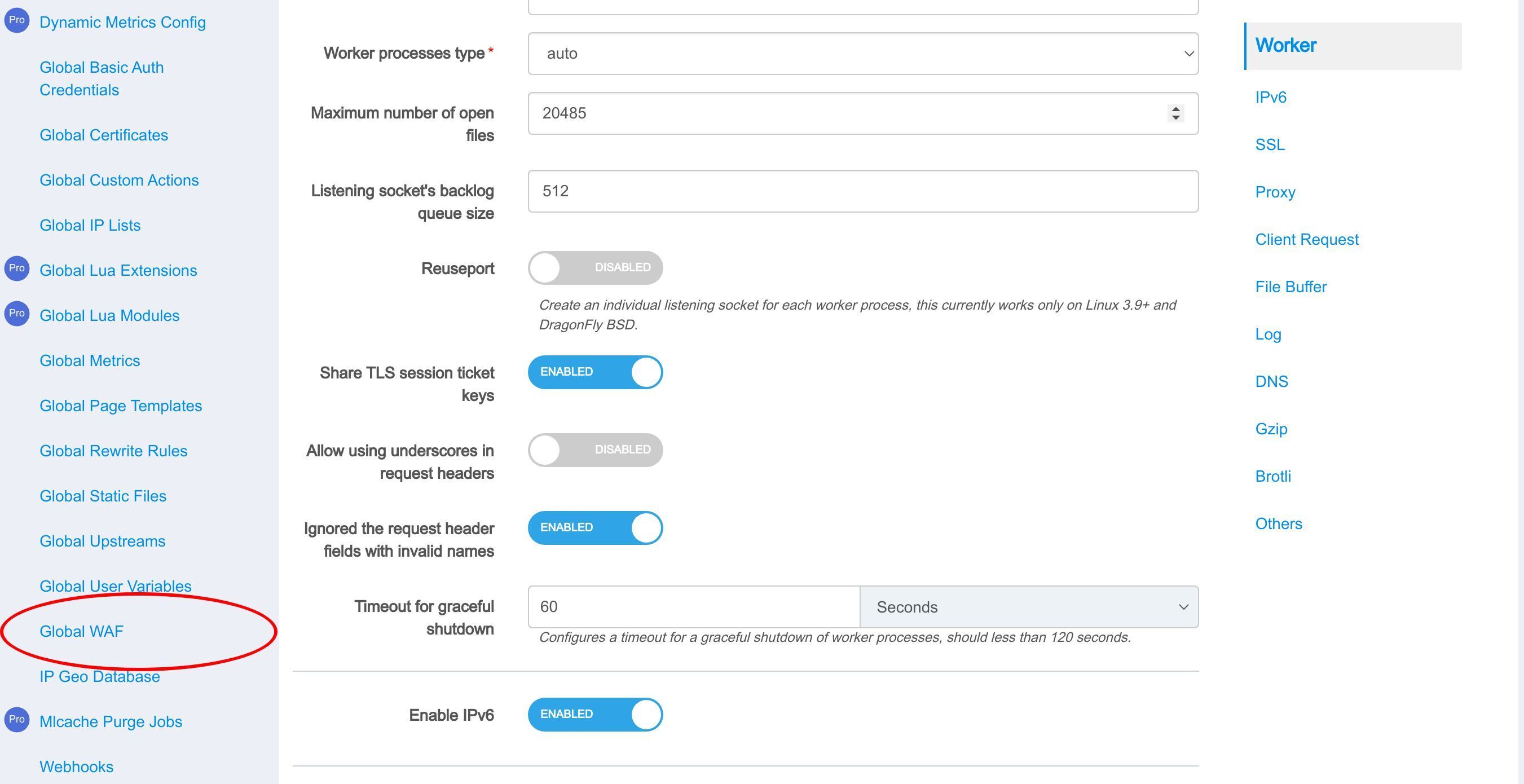
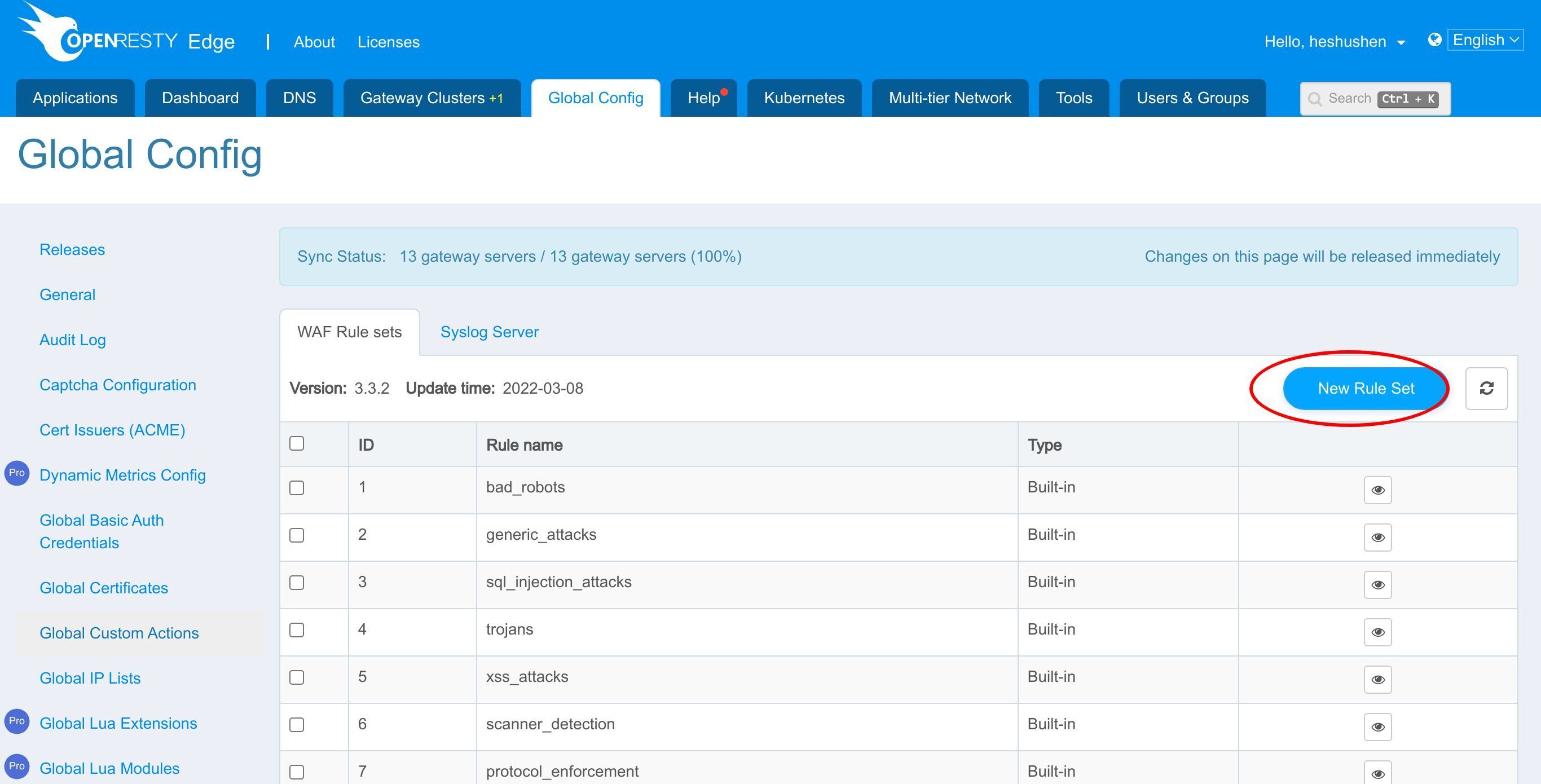
グローバル設定ページに移動します。
「グローバル WAF」メニュー項目をクリックします。
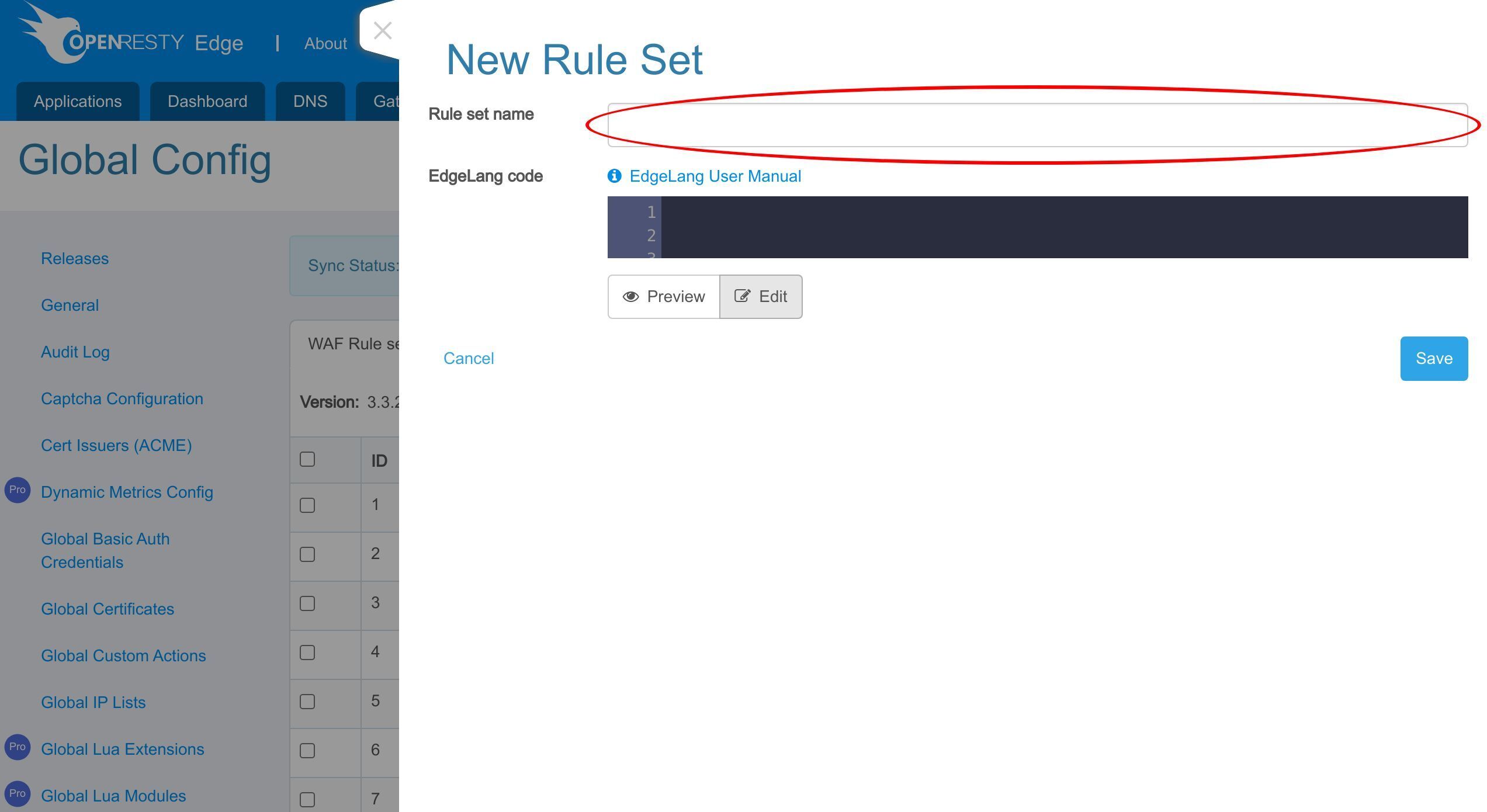
「新規ルールセット」ボタンをクリックします。
ここでルールセットの名前と定義を入力します。
Edge 言語で WAF ルールを定義できます。Edge 言語は Edgelang と略されます。
このルールセットを保存します。
このページを終了します。
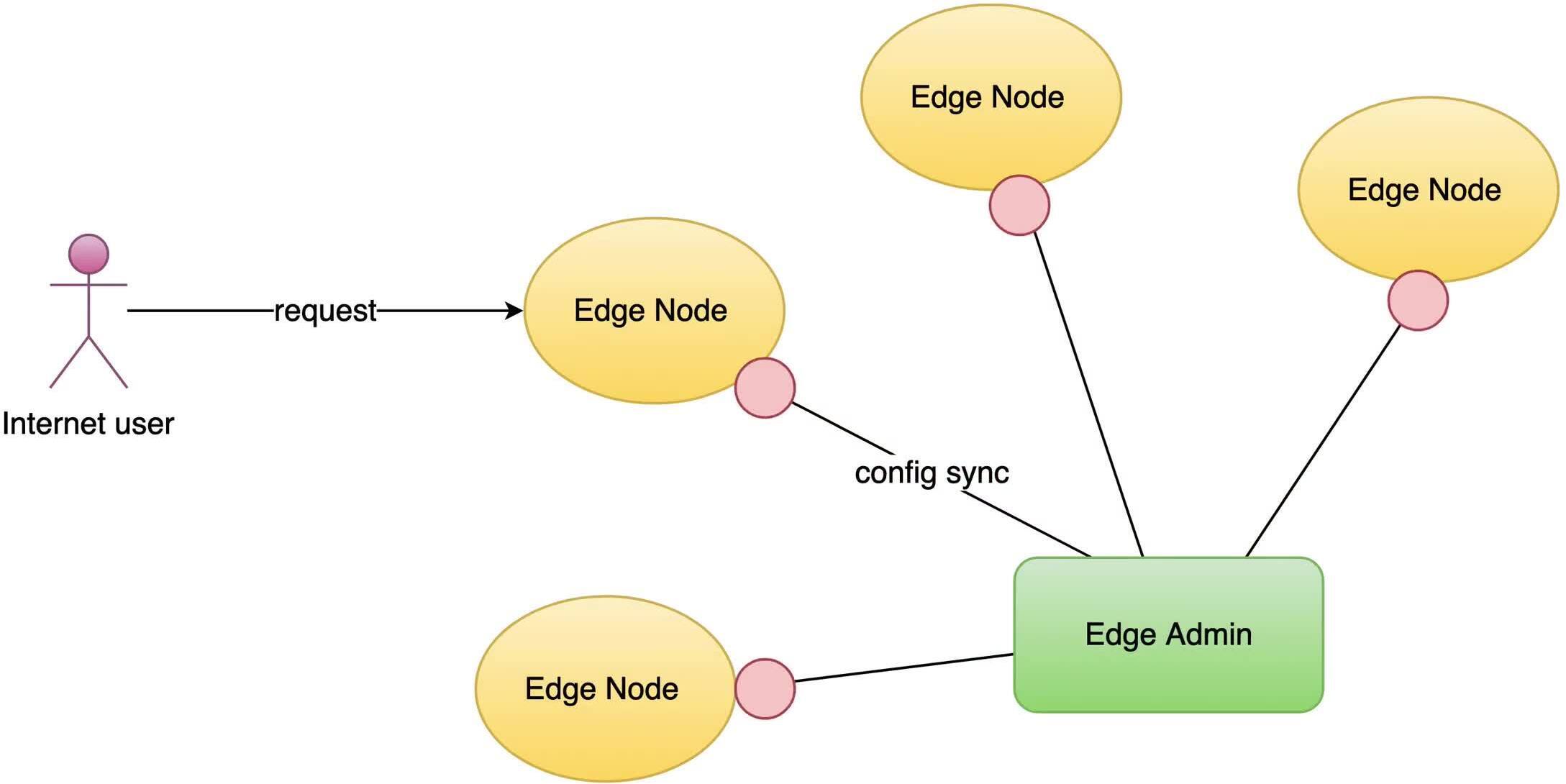
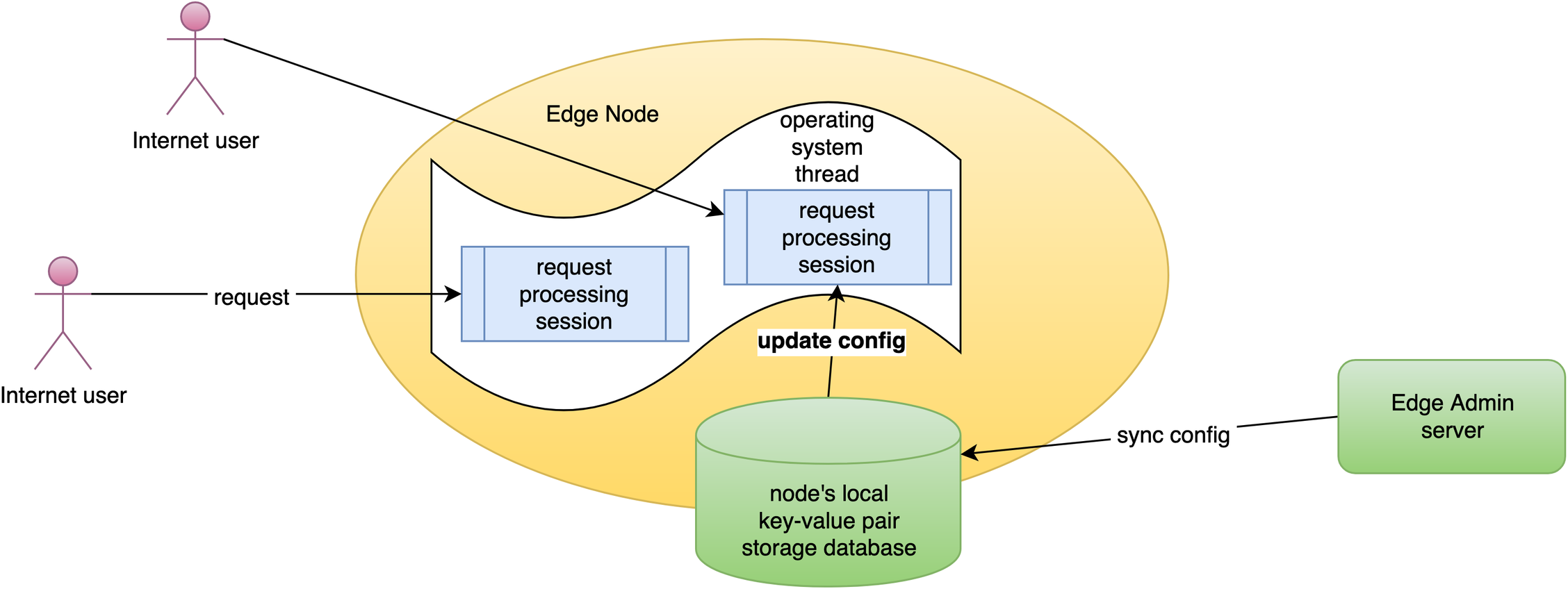
OpenResty Edge における WAF の実装
OpenResty Edge の WAF は非常に効率的です。これは多くの先進的な最適化技術を実装しているためです。
すべての WAF ルールが参照する正規表現を 1 つのステートマシンに結合することをサポートしています。これにより、リクエストデータを 1 回スキャンするだけで、どのルールがマッチし、それらのルールのどの部分がマッチするかを即座に知ることができます。
また、すべての Edgelang ルールの定数文字列プレフィックスとサフィックスパターンを単一のツリー状データ構造に結合することもサポートしています。
これらの最適化は WAF プラットフォームだけのものではありません。
すべてのページルールと Edge 言語ルールも、まったく同じ最適化を持っています。
以上が本日お伝えする内容です。
OpenResty Edge について
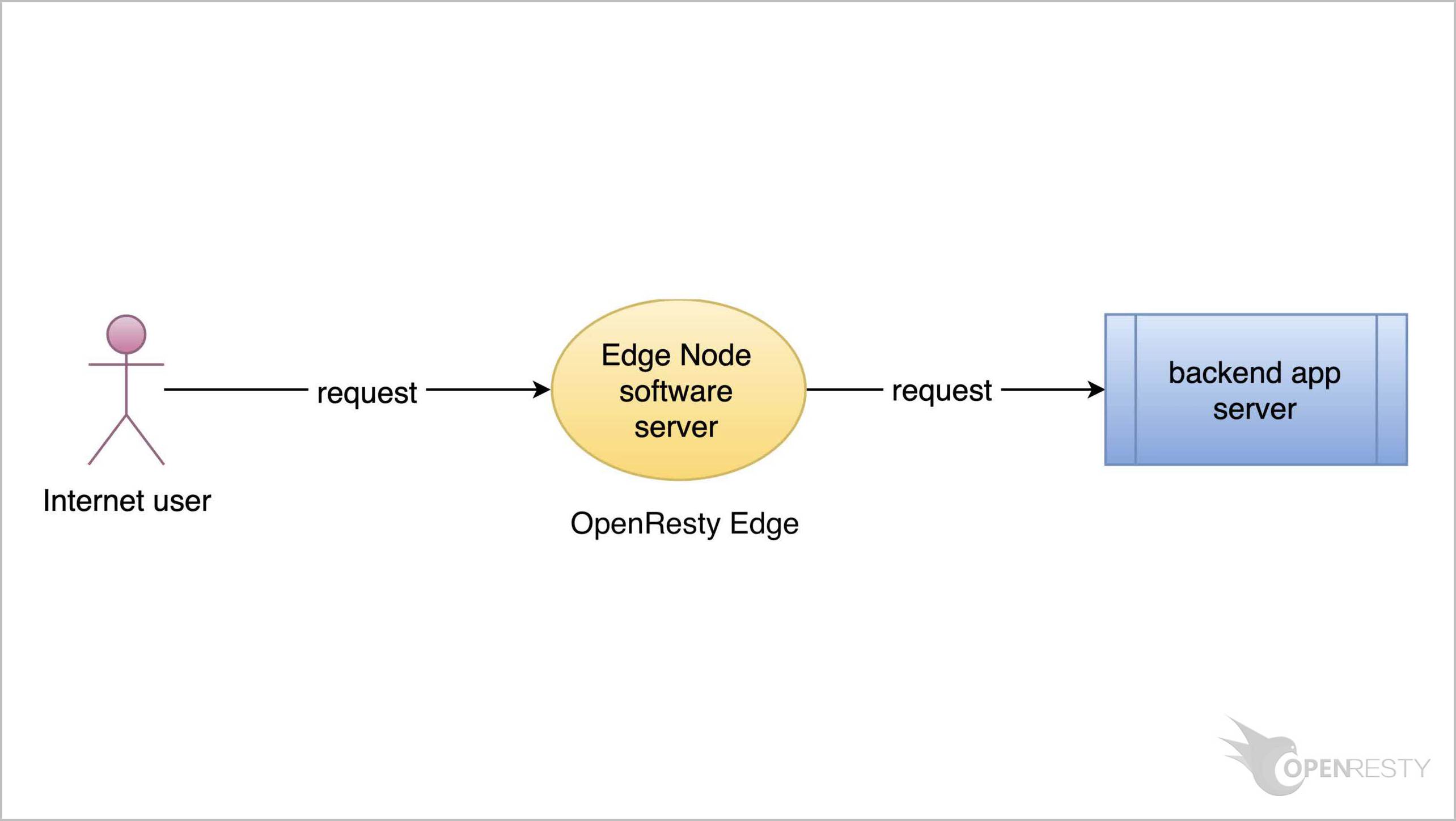
OpenResty Edge は、マイクロサービスと分散トラフィックアーキテクチャ向けに設計された多機能ゲートウェイソフトウェアで、当社が独自に開発しました。トラフィック管理、プライベート CDN 構築、API ゲートウェイ、セキュリティ保護などの機能を統合し、現代のアプリケーションの構築、管理、保護を容易にします。OpenResty Edge は業界をリードする性能と拡張性を持ち、高並発・高負荷シナリオの厳しい要求を満たすことができます。K8s などのコンテナアプリケーショントラフィックのスケジューリングをサポートし、大量のドメイン名を管理できるため、大規模ウェブサイトや複雑なアプリケーションのニーズを容易に満たすことができます。
著者について
章亦春(Zhang Yichun)は、オープンソースの OpenResty® プロジェクトの創始者であり、OpenResty Inc. の CEO および創業者です。
章亦春(GitHub ID: agentzh)は中国江蘇省生まれで、現在は米国ベイエリアに在住しております。彼は中国における初期のオープンソース技術と文化の提唱者およびリーダーの一人であり、Cloudflare、Yahoo!、Alibaba など、国際的に有名なハイテク企業に勤務した経験があります。「エッジコンピューティング」、「動的トレーシング」、「機械プログラミング」 の先駆者であり、22 年以上のプログラミング経験と 16 年以上のオープンソース経験を持っております。世界中で 4000 万以上のドメイン名を持つユーザーを抱えるオープンソースプロジェクトのリーダーとして、彼は OpenResty® オープンソースプロジェクトをベースに、米国シリコンバレーの中心部にハイテク企業 OpenResty Inc. を設立いたしました。同社の主力製品である OpenResty XRay動的トレーシング技術を利用した非侵襲的な障害分析および排除ツール)と OpenResty Edge(マイクロサービスおよび分散トラフィックに最適化された多機能
翻訳
英文版の原文と日本語訳版(本文)をご用意しております。読者の皆様による他の言語への翻訳版も歓迎いたします。全文翻訳で省略がなければ、採用を検討させていただきます。心より感謝申し上げます!