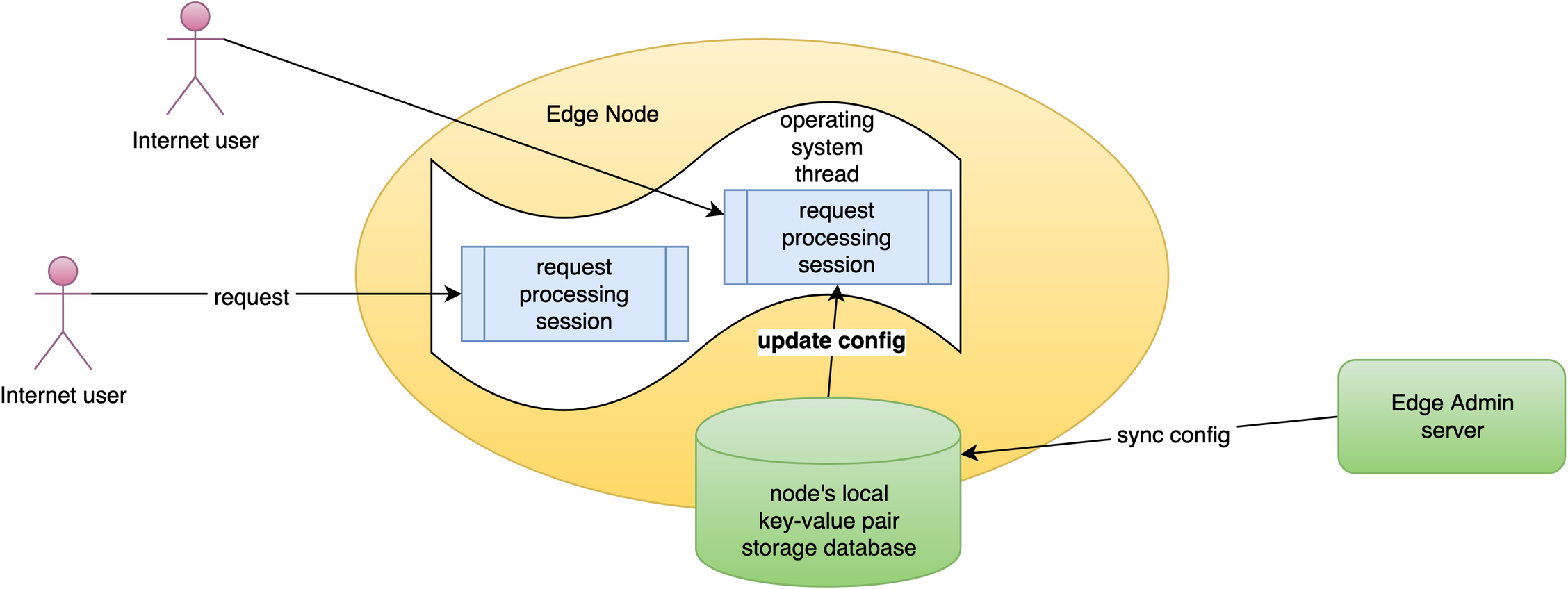
OpenResty Edge における HTTP 基本認証の設定
本日は、OpenResty Edge 製品のデモを続けます。ゲートウェイアプリケーションで HTTP 基本認証を設定する方法をご紹介します。
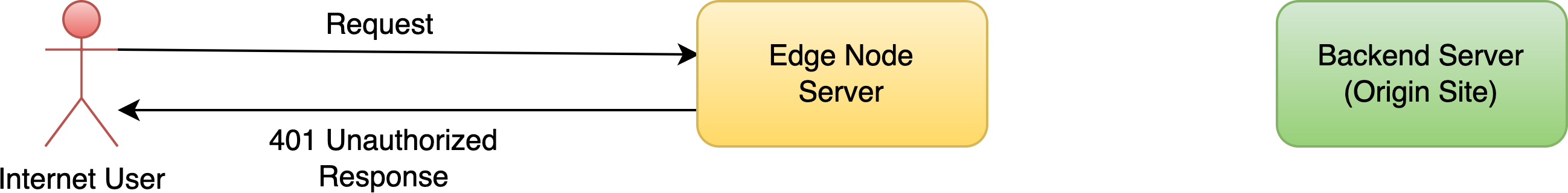
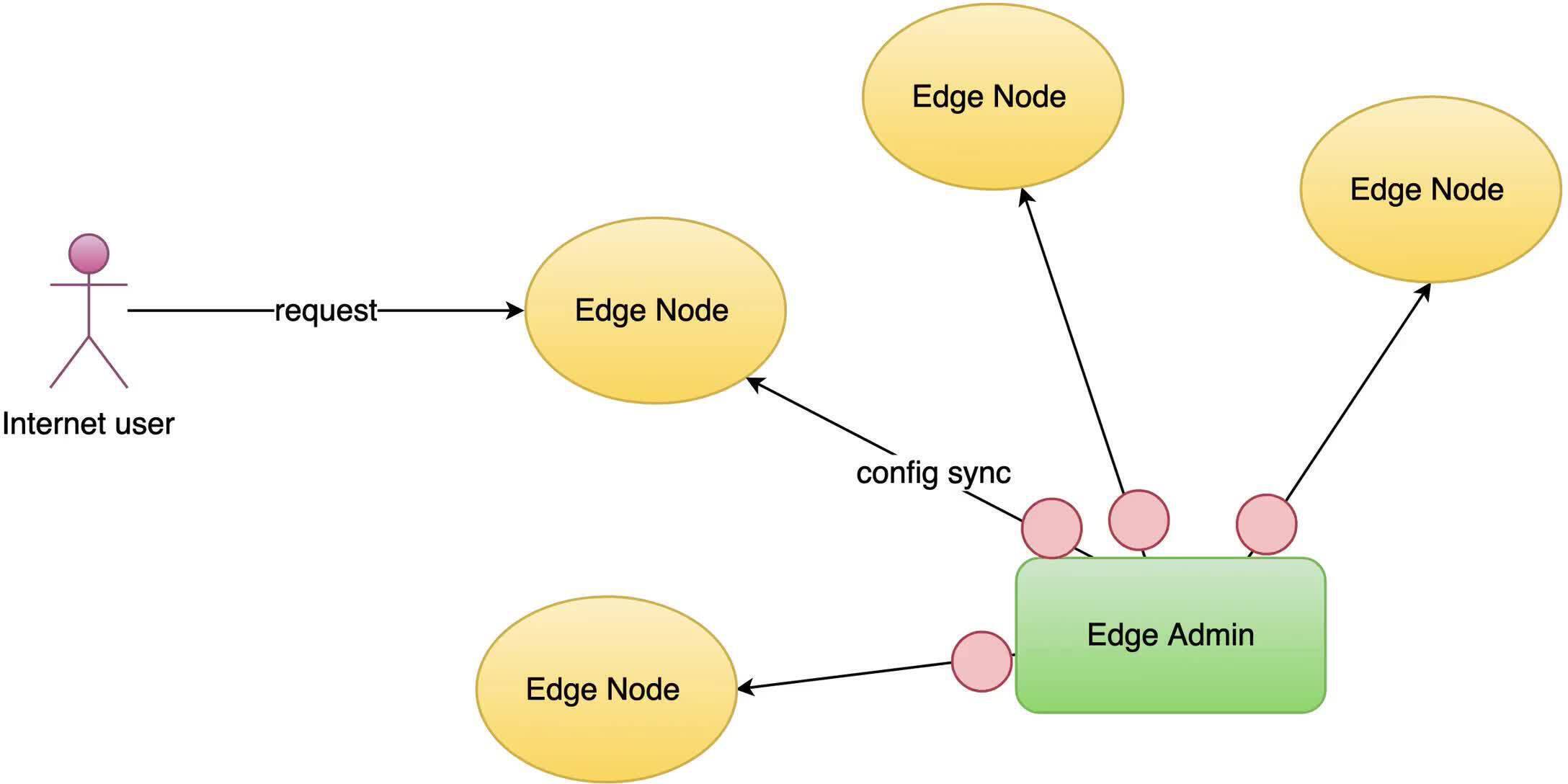
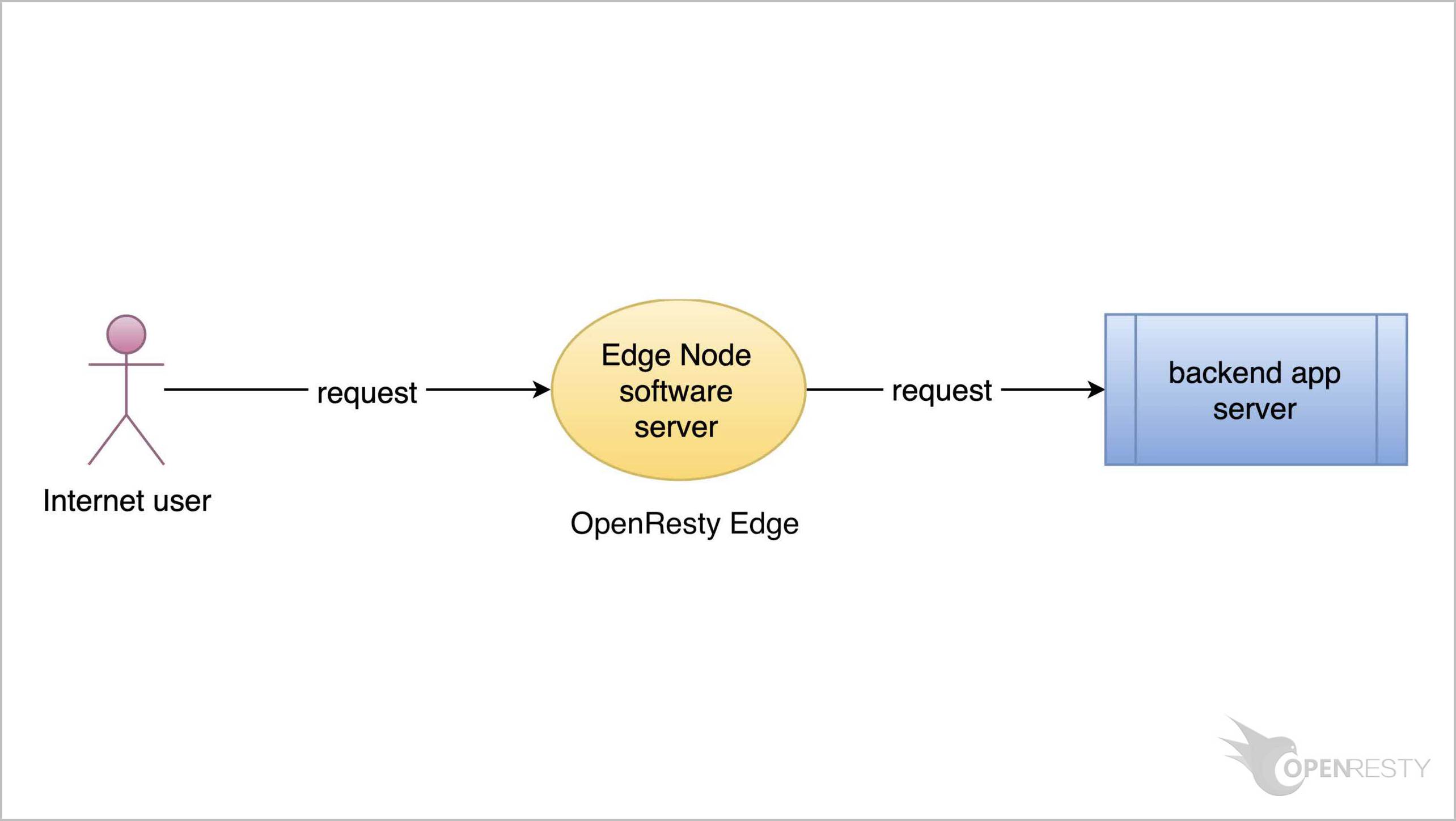
HTTP 基本認証はゲートウェイサーバーによって直接処理されます。
アプリケーションの HTTP 基本認証の設定
いつものように、OpenResty Edge の Admin Web コンソールにアクセスしましょう。これはコンソールのサンプルデプロイメントです。各ユーザーは独自のローカルデプロイメントを持っています。
ゲートウェイアプリケーションの HTTP 基本認証の認証情報を設定しましょう。
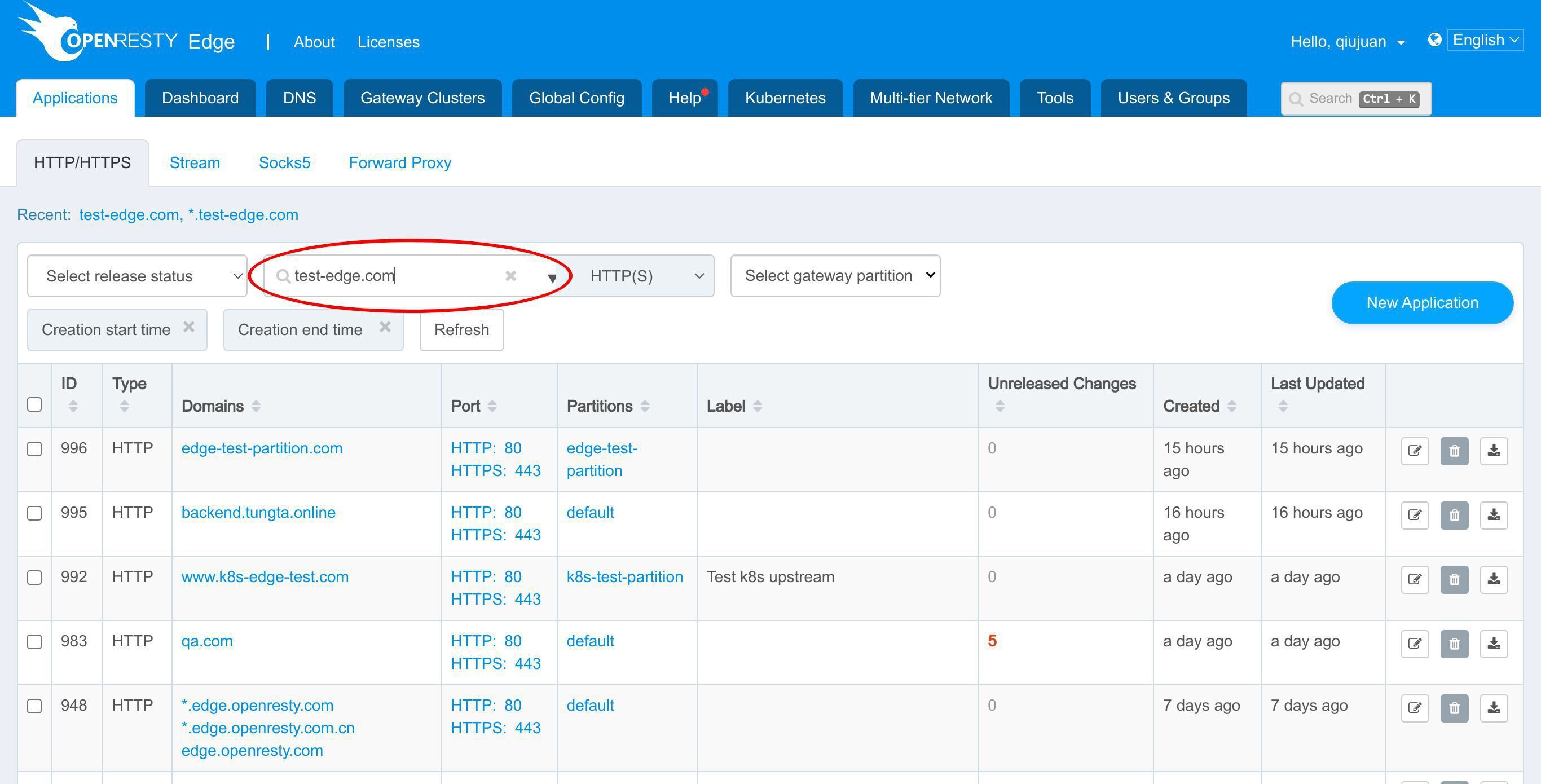
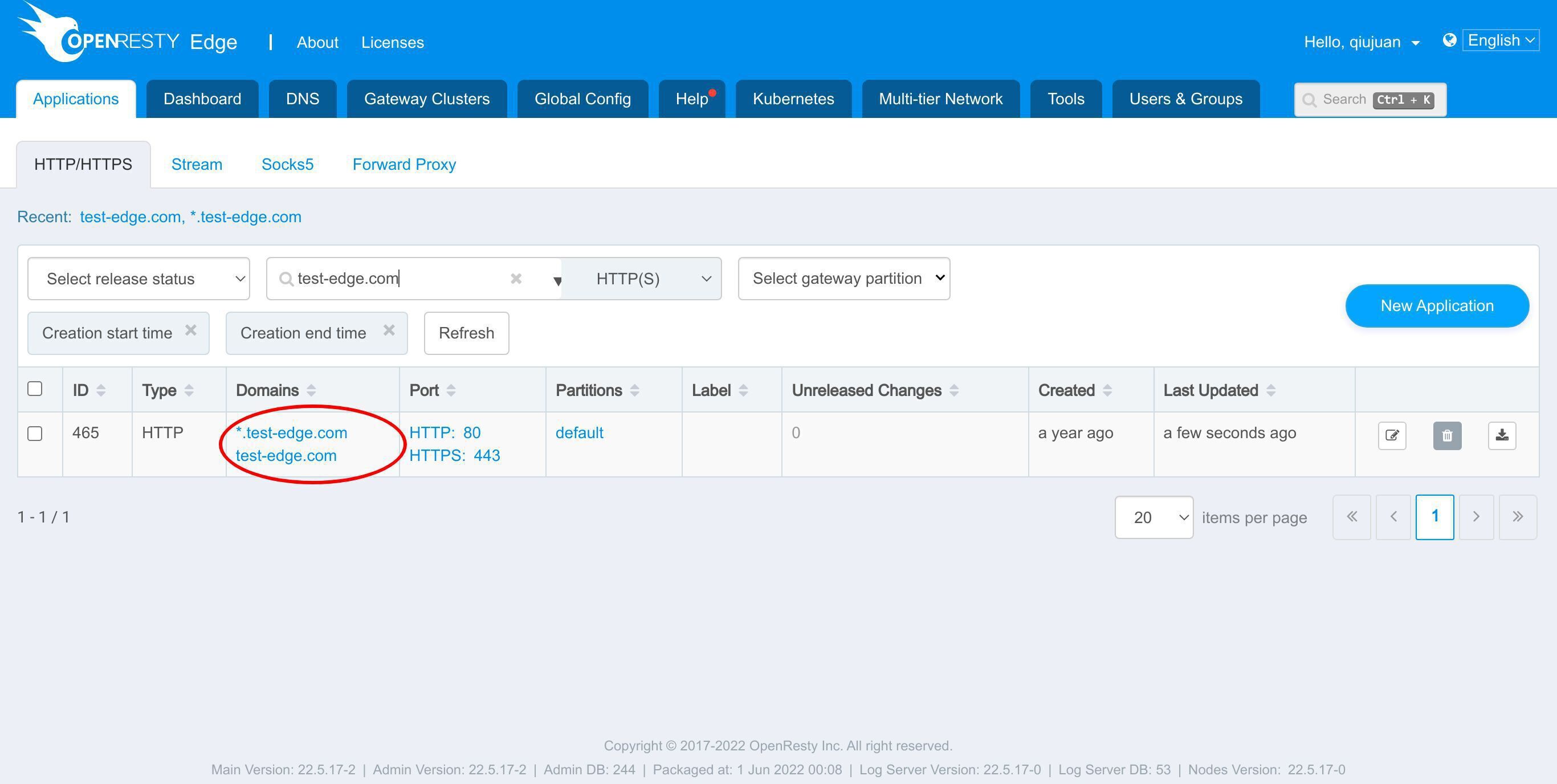
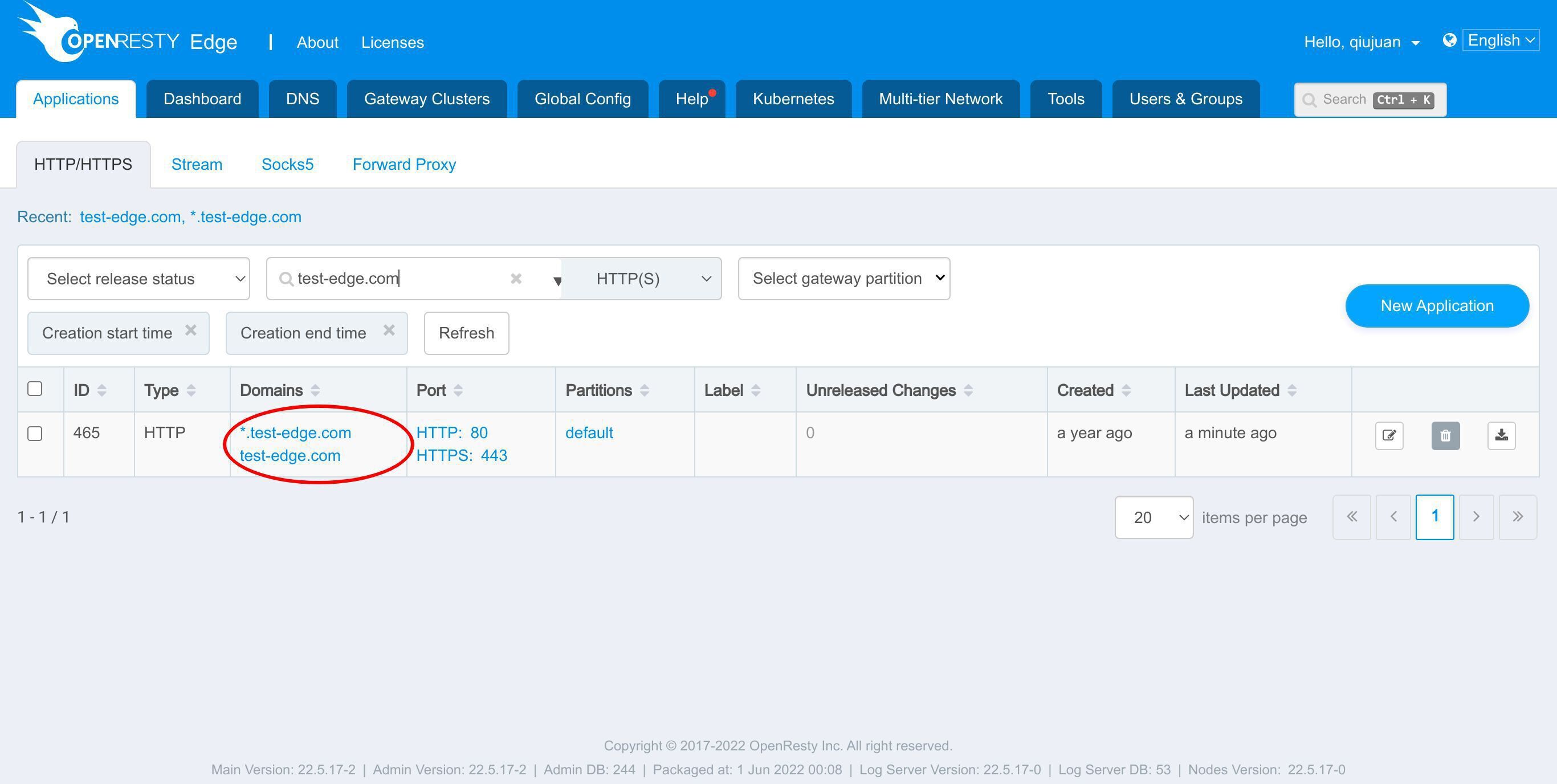
以前の例で使用した test-edge.com アプリケーションを引き続き使用できます。
このアプリケーションに入ります。
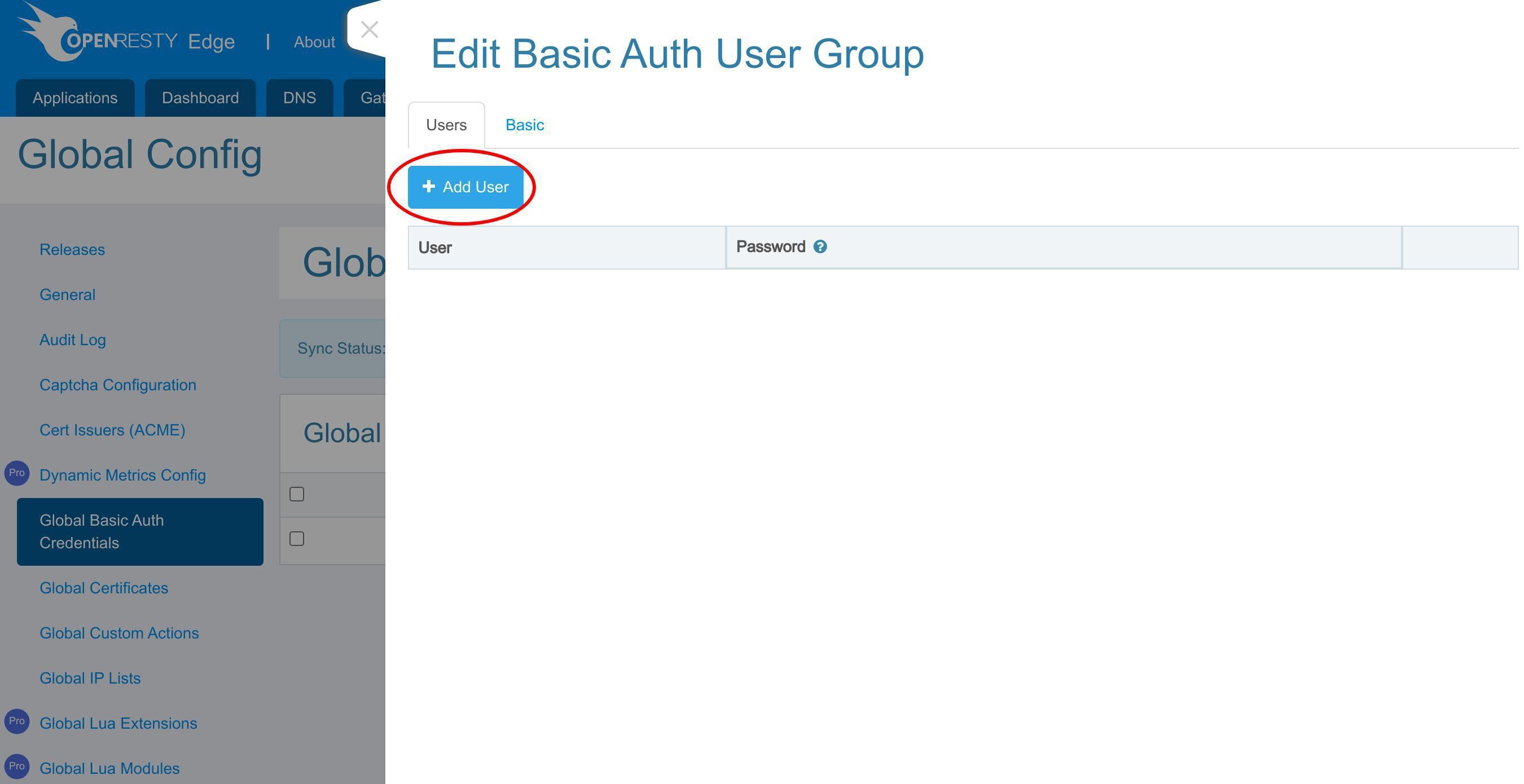
基本認証ユーザーグループの追加
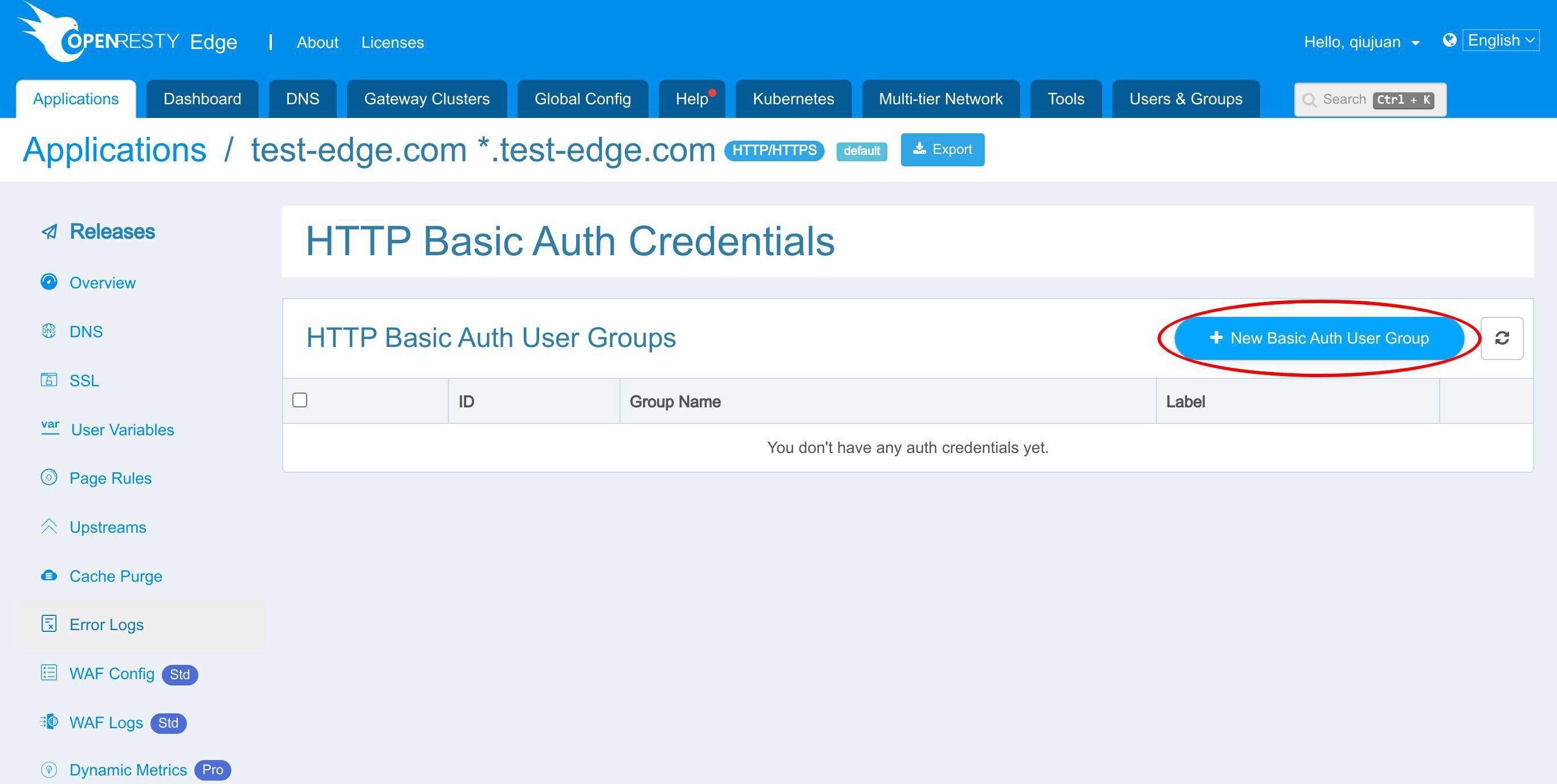
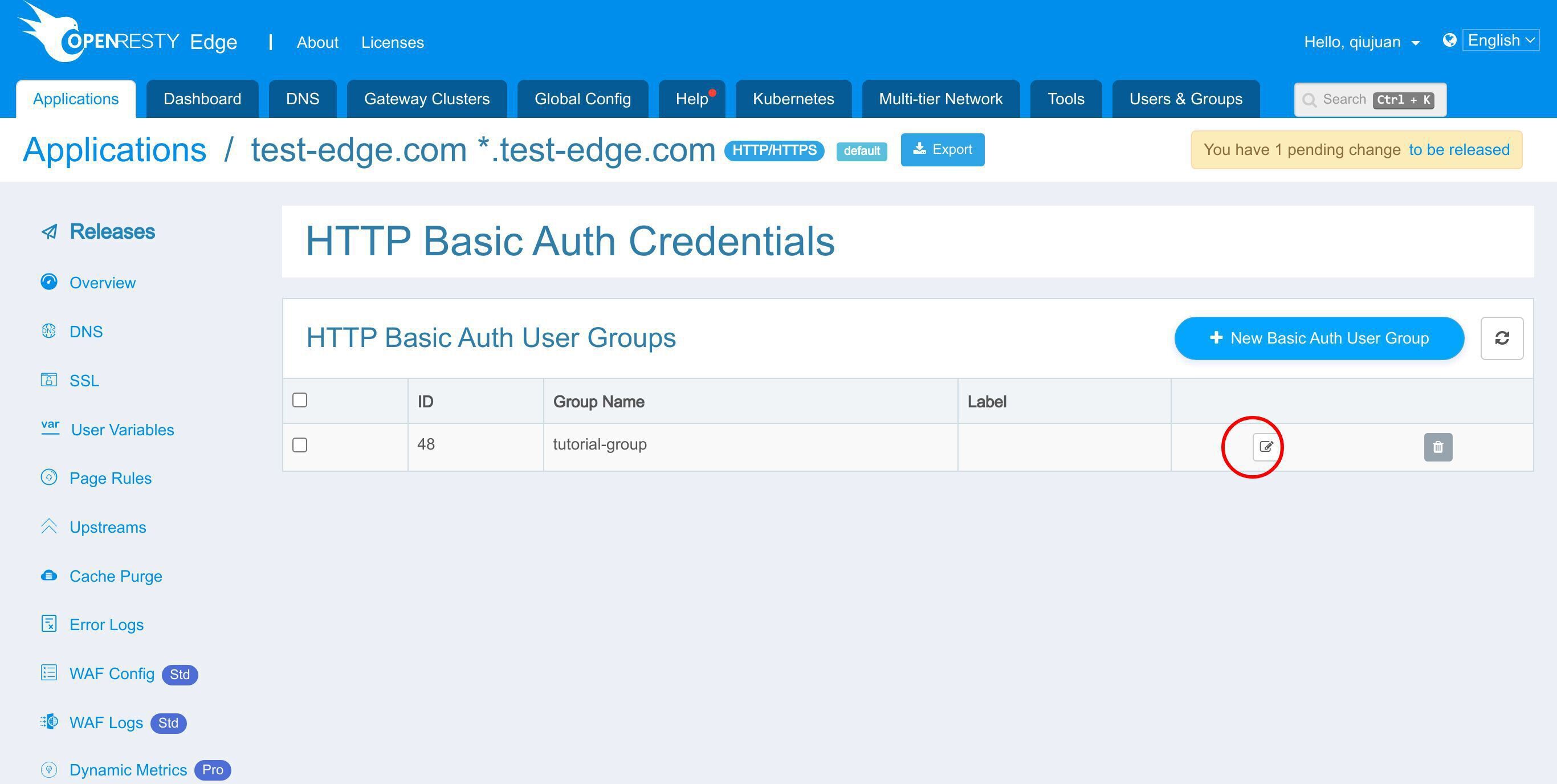
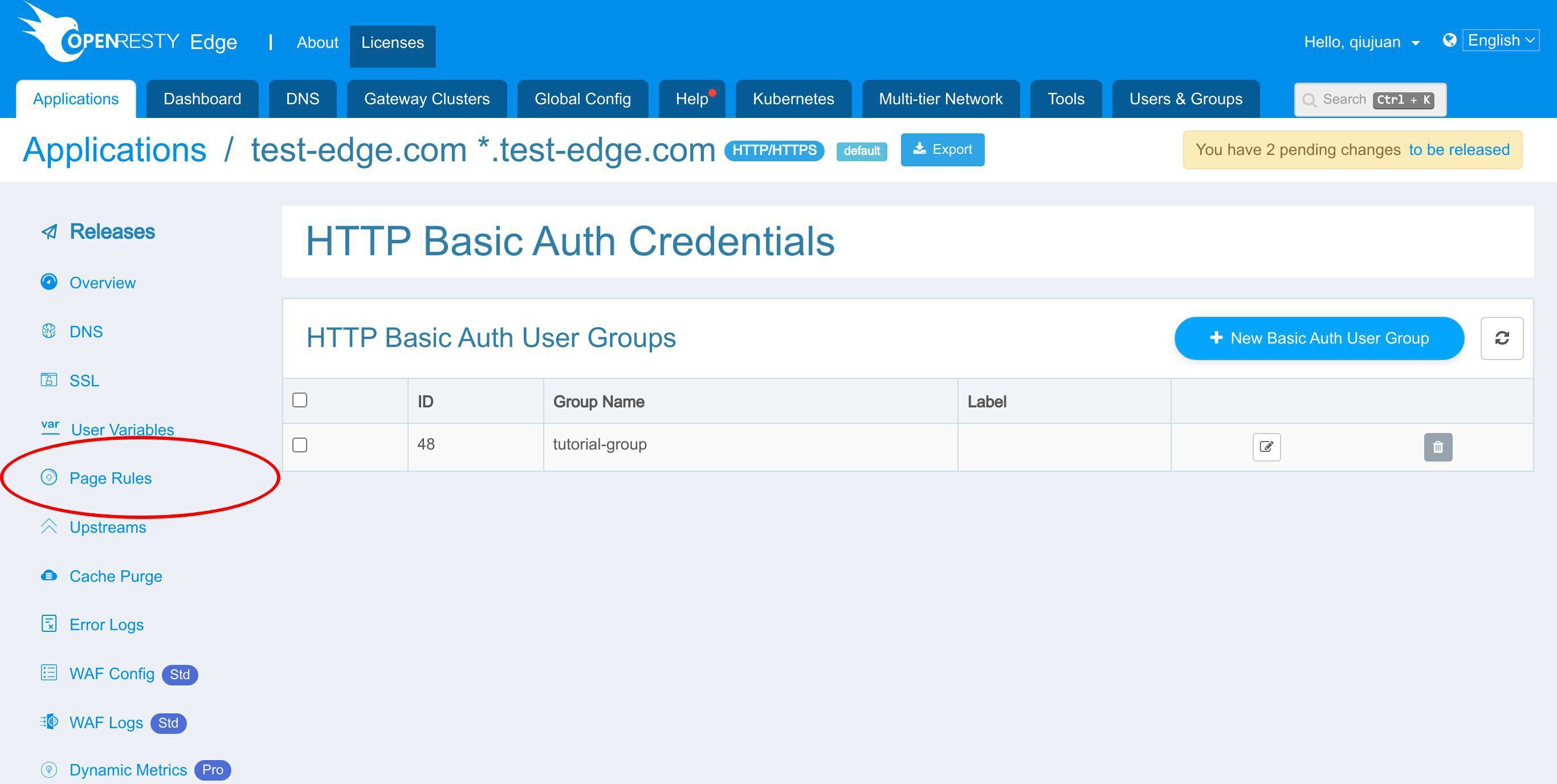
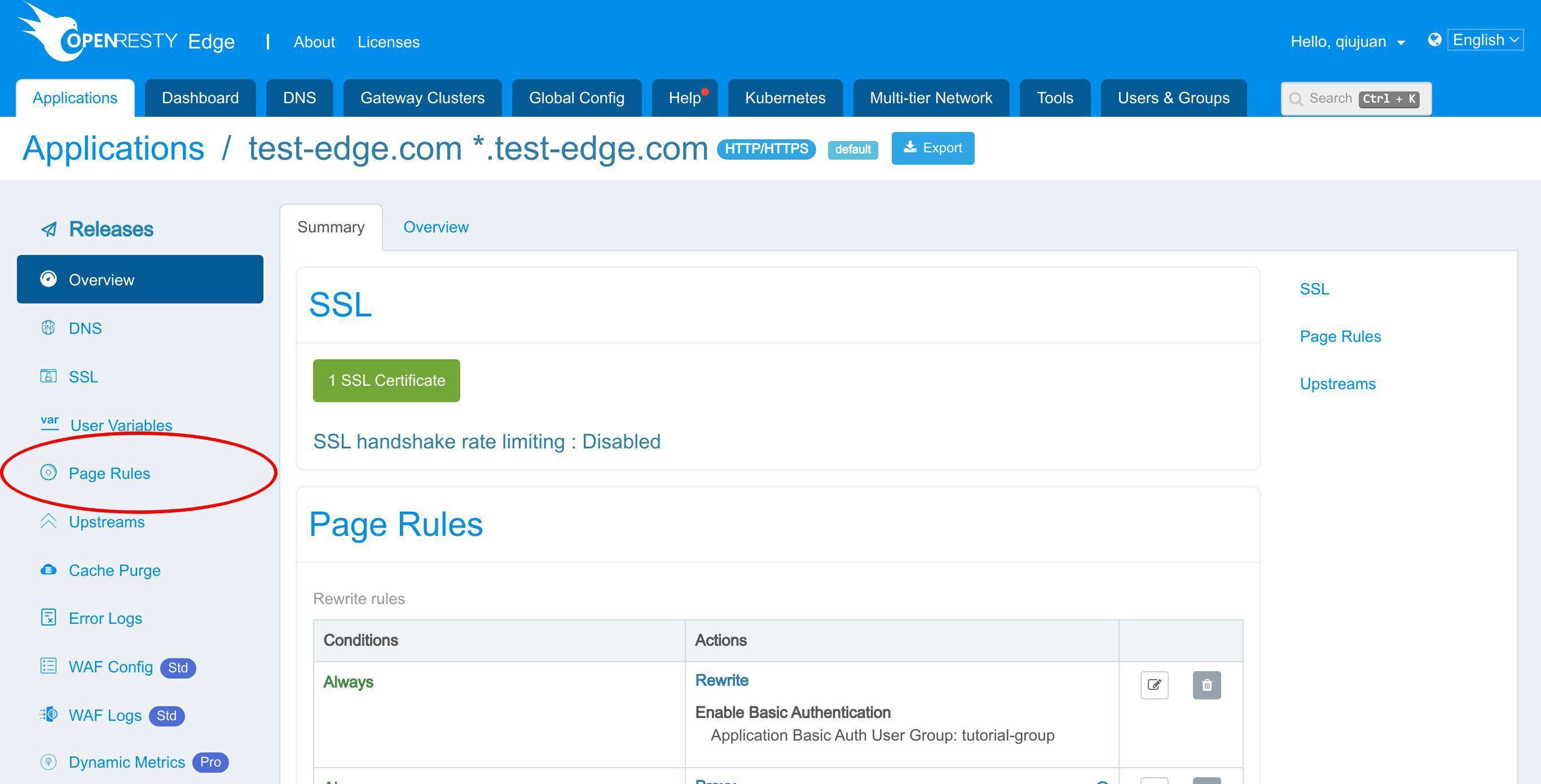
HTTP 基本認証アカウントのページに移動します。
1 つまたは複数の基本認証ユーザーグループを追加することができます。各ユーザーグループには 1 人または複数のユーザーを設定できます。
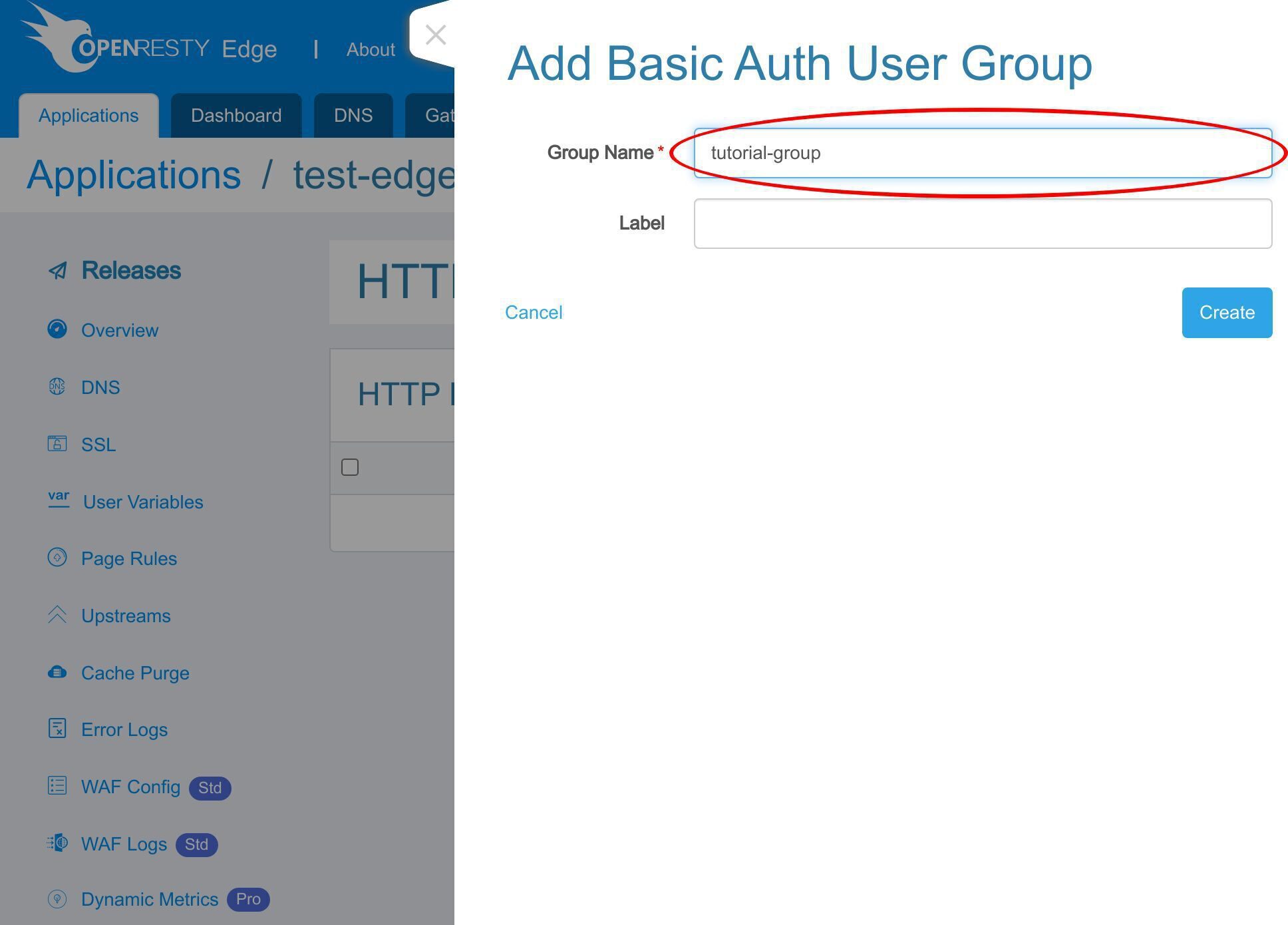
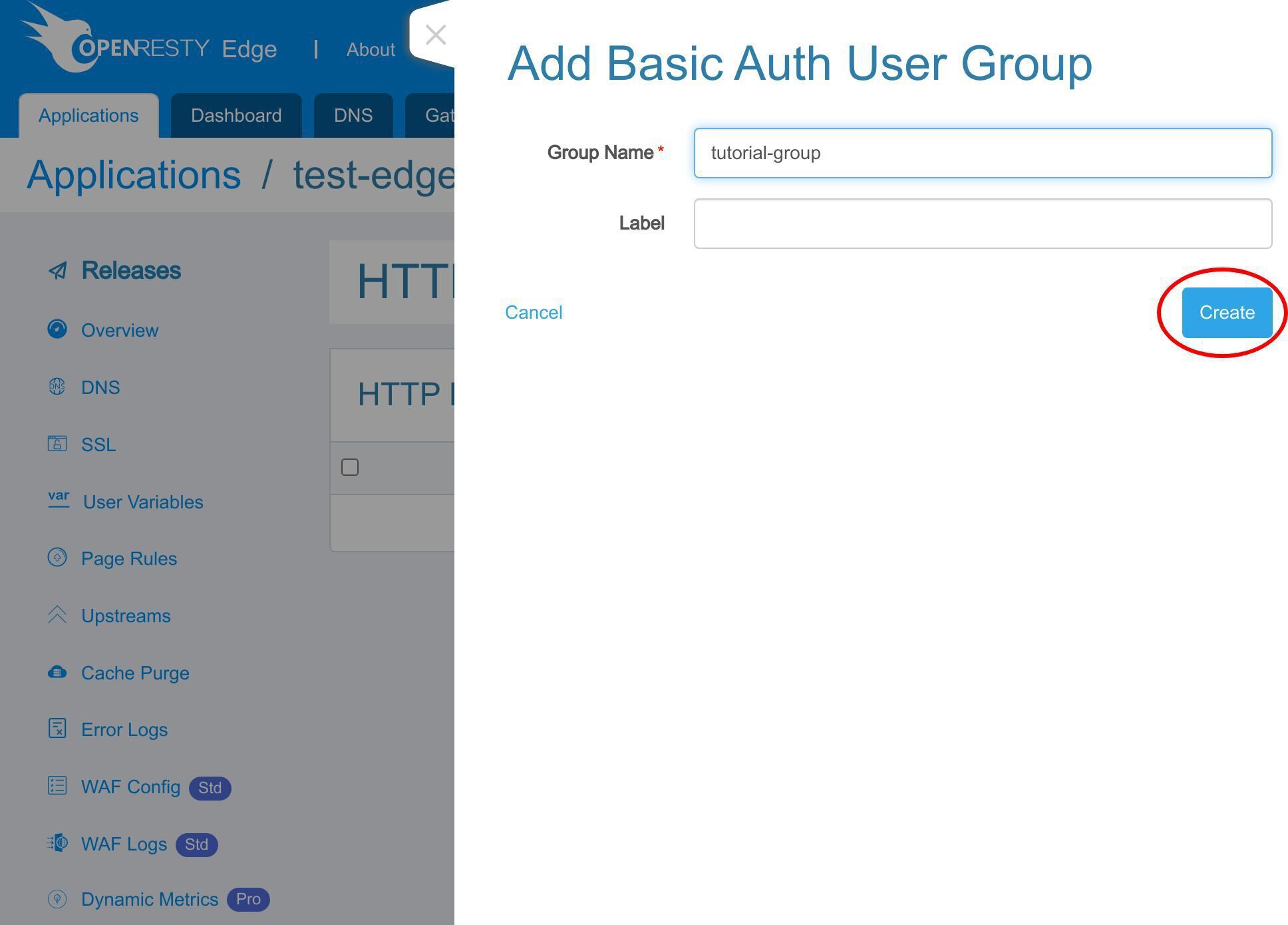
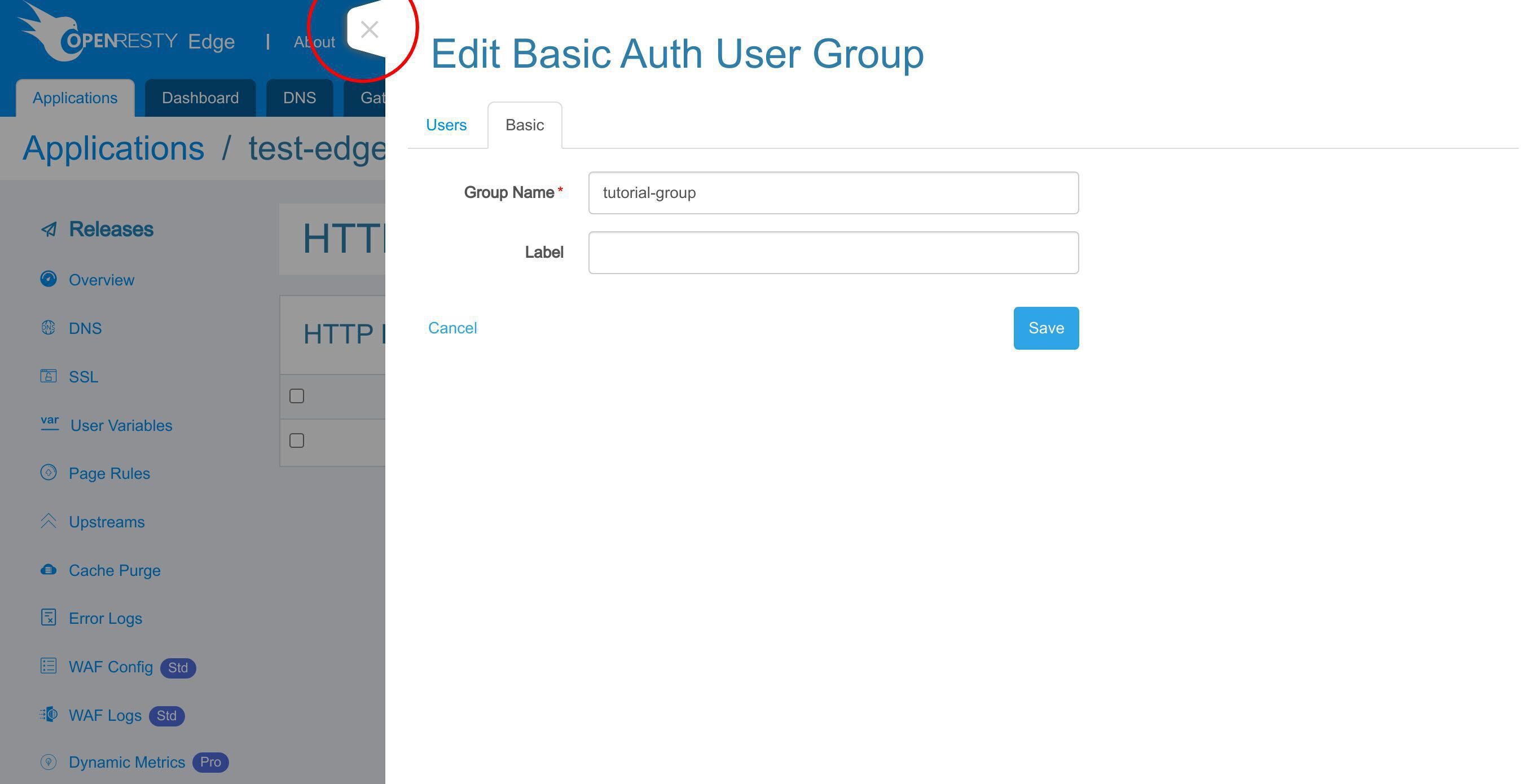
新しい基本認証ユーザーグループを追加します。
グループ名として「tutorial-group」を入力します。このユーザーグループはこのチュートリアルのデモンストレーション用です。
保存します。
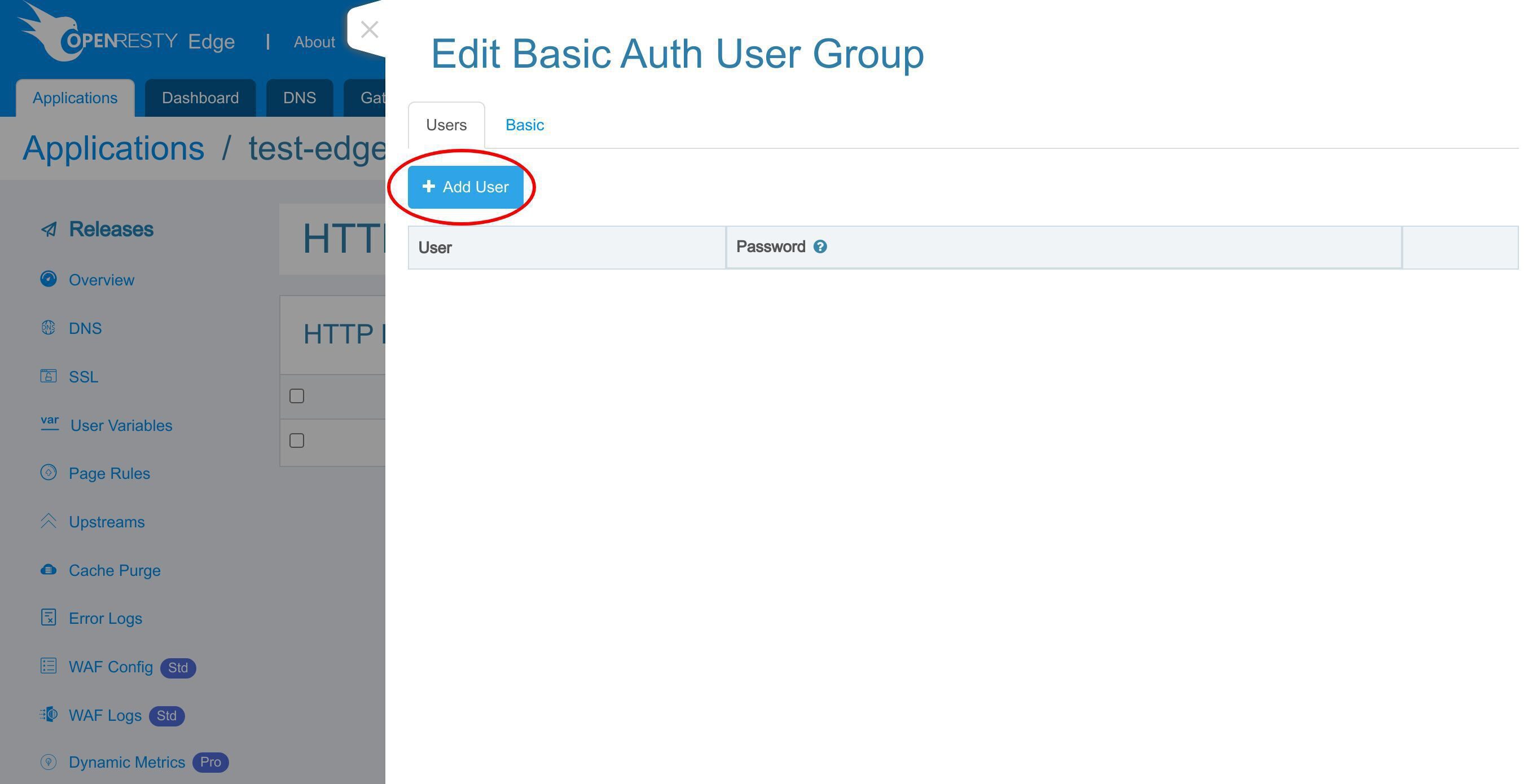
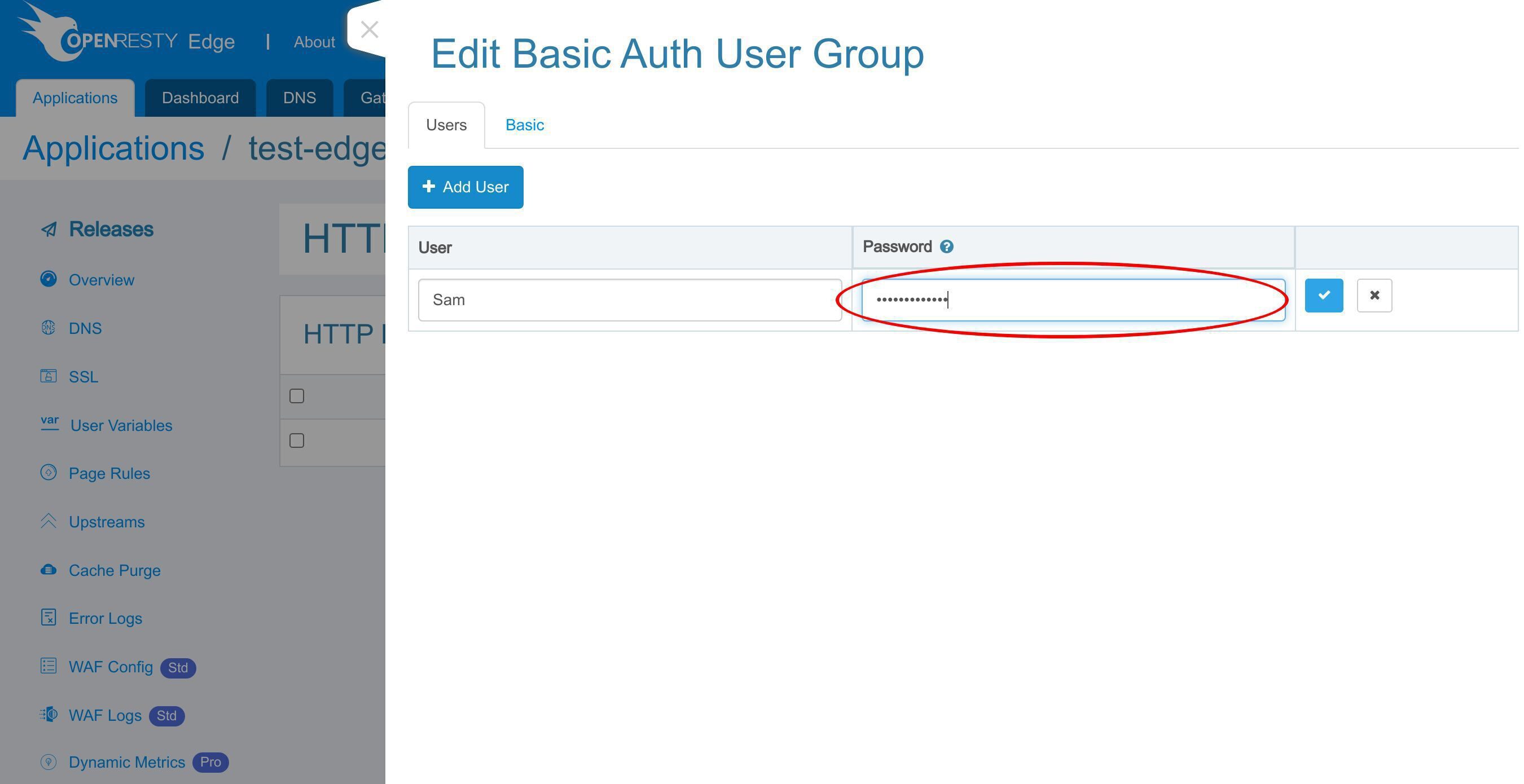
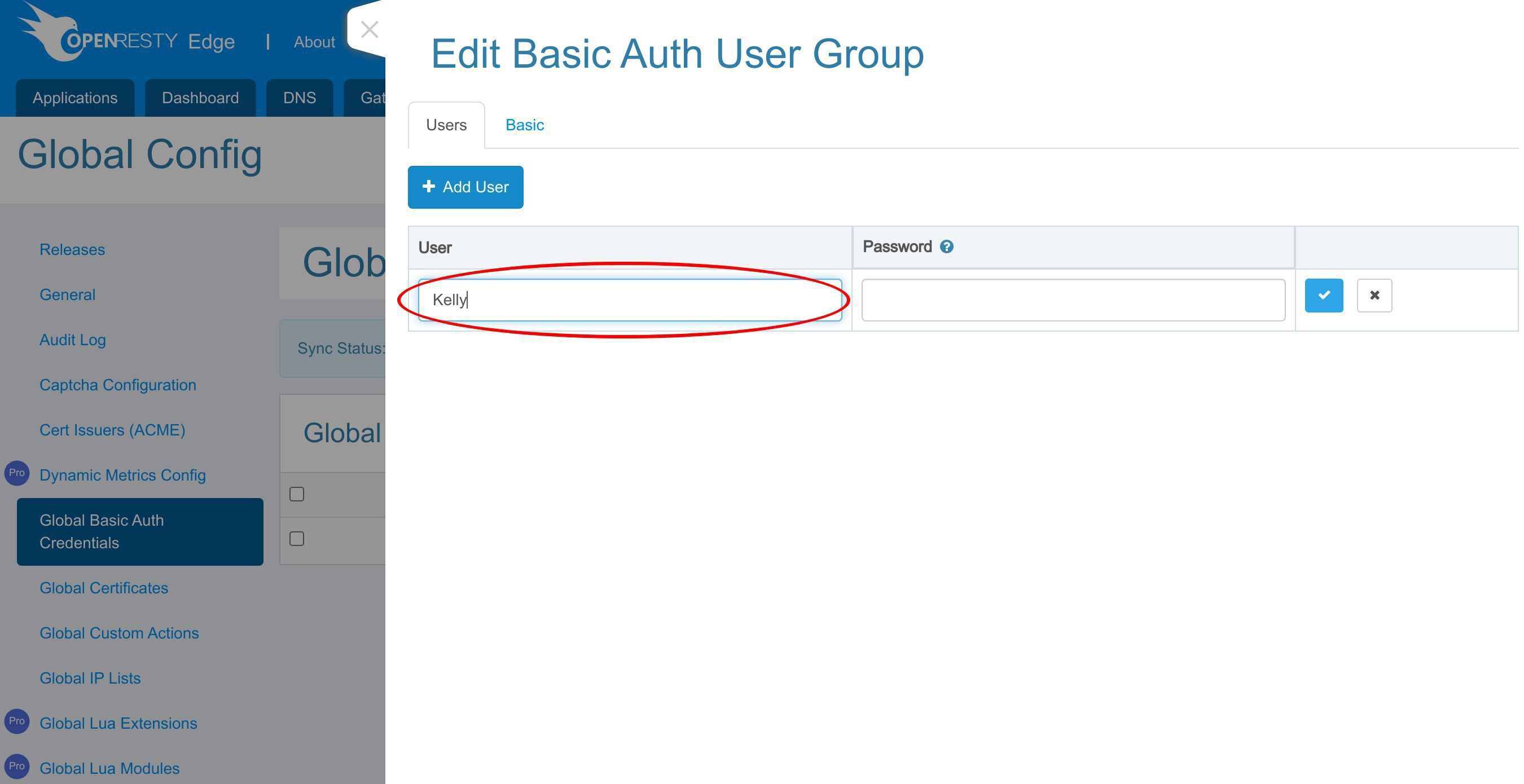
このグループに新しいユーザーを追加します。
このボタンをクリックして追加します。
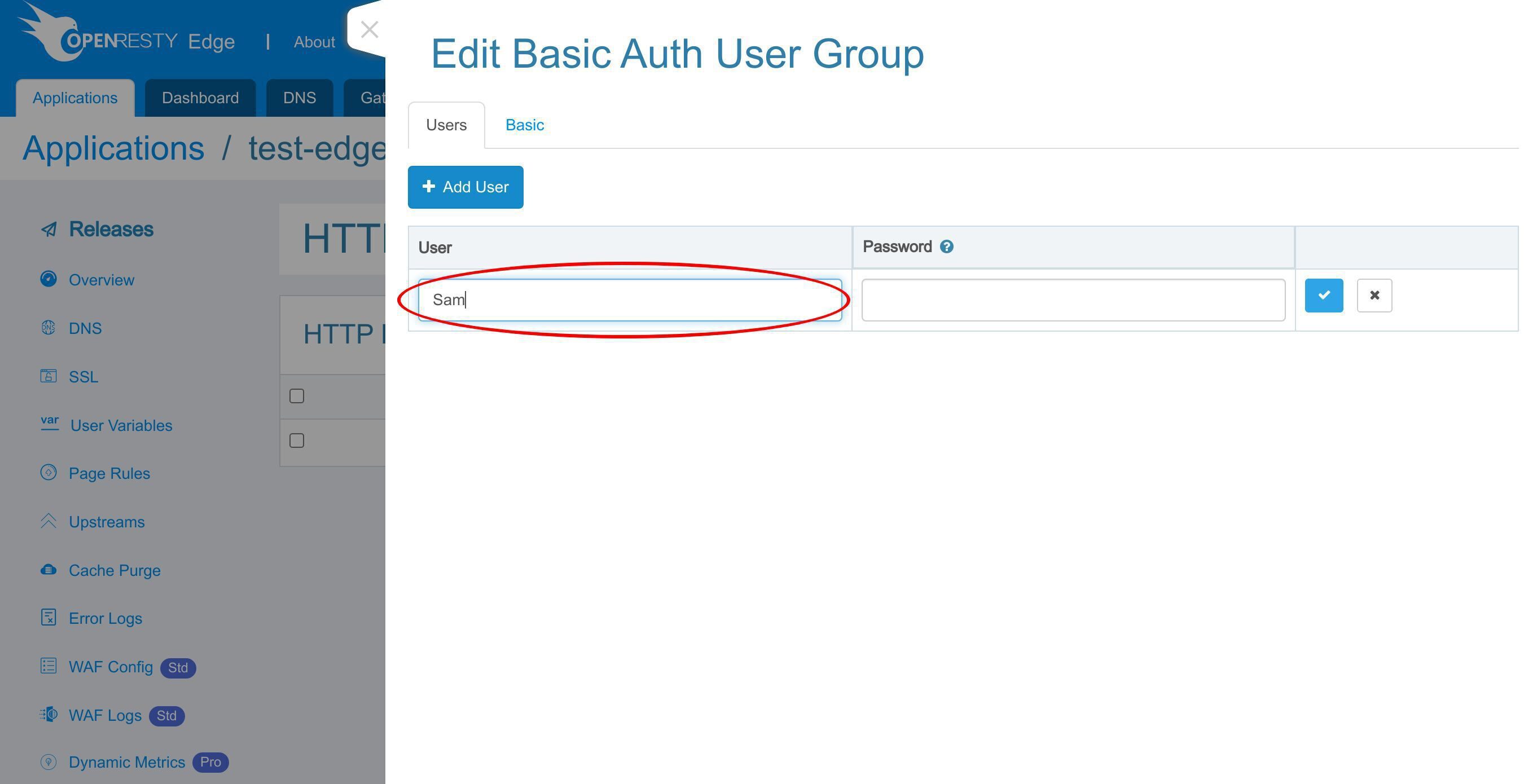
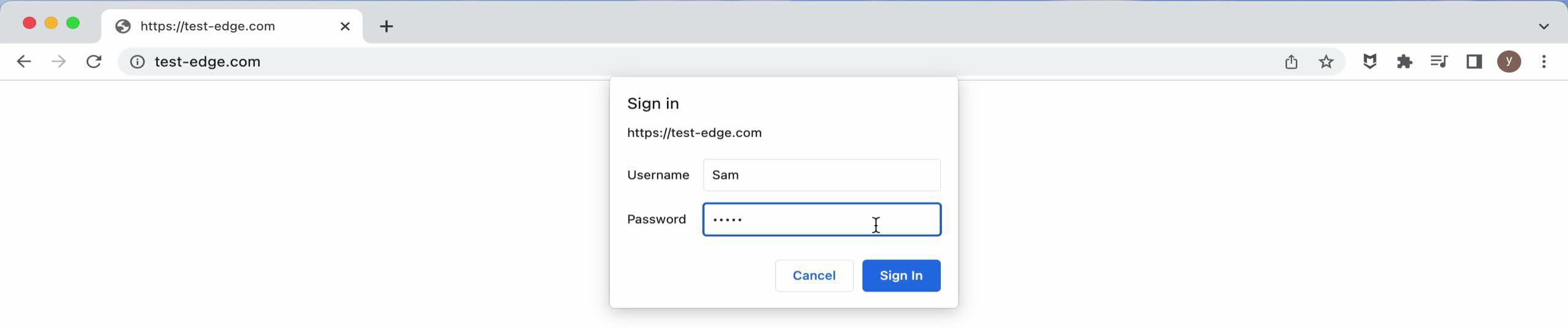
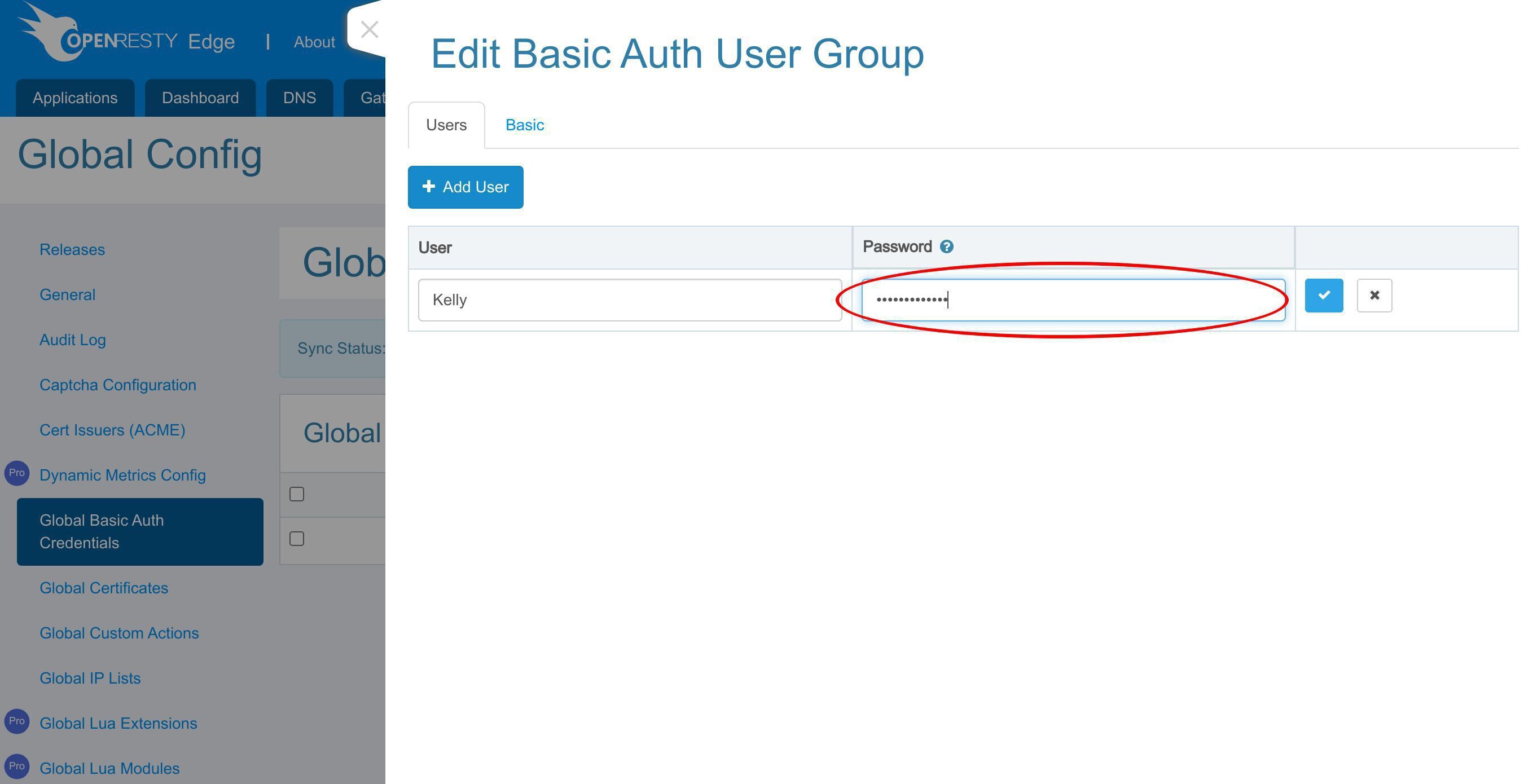
ユーザー名「Sam」を入力してください。
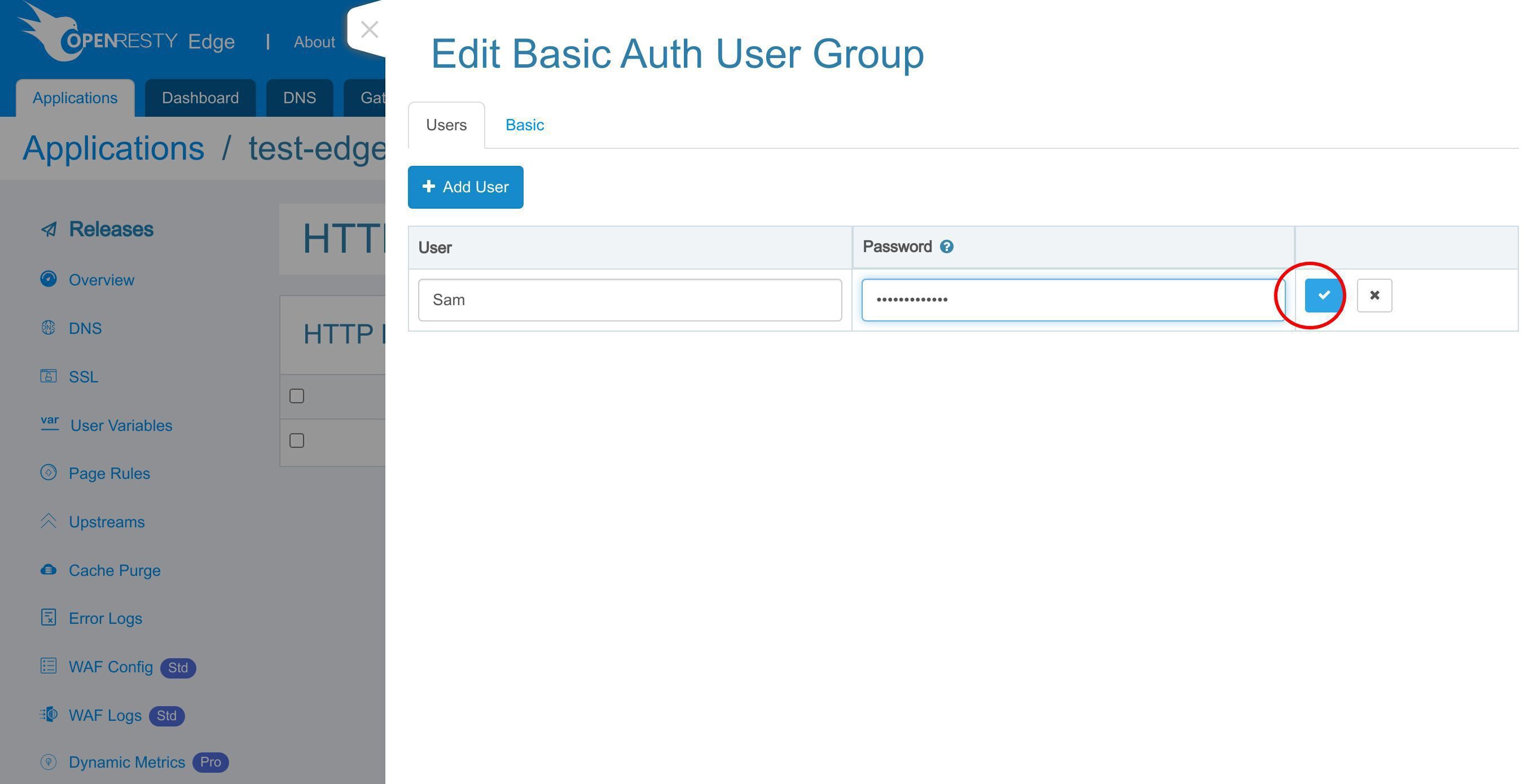
パスワードを入力してください。
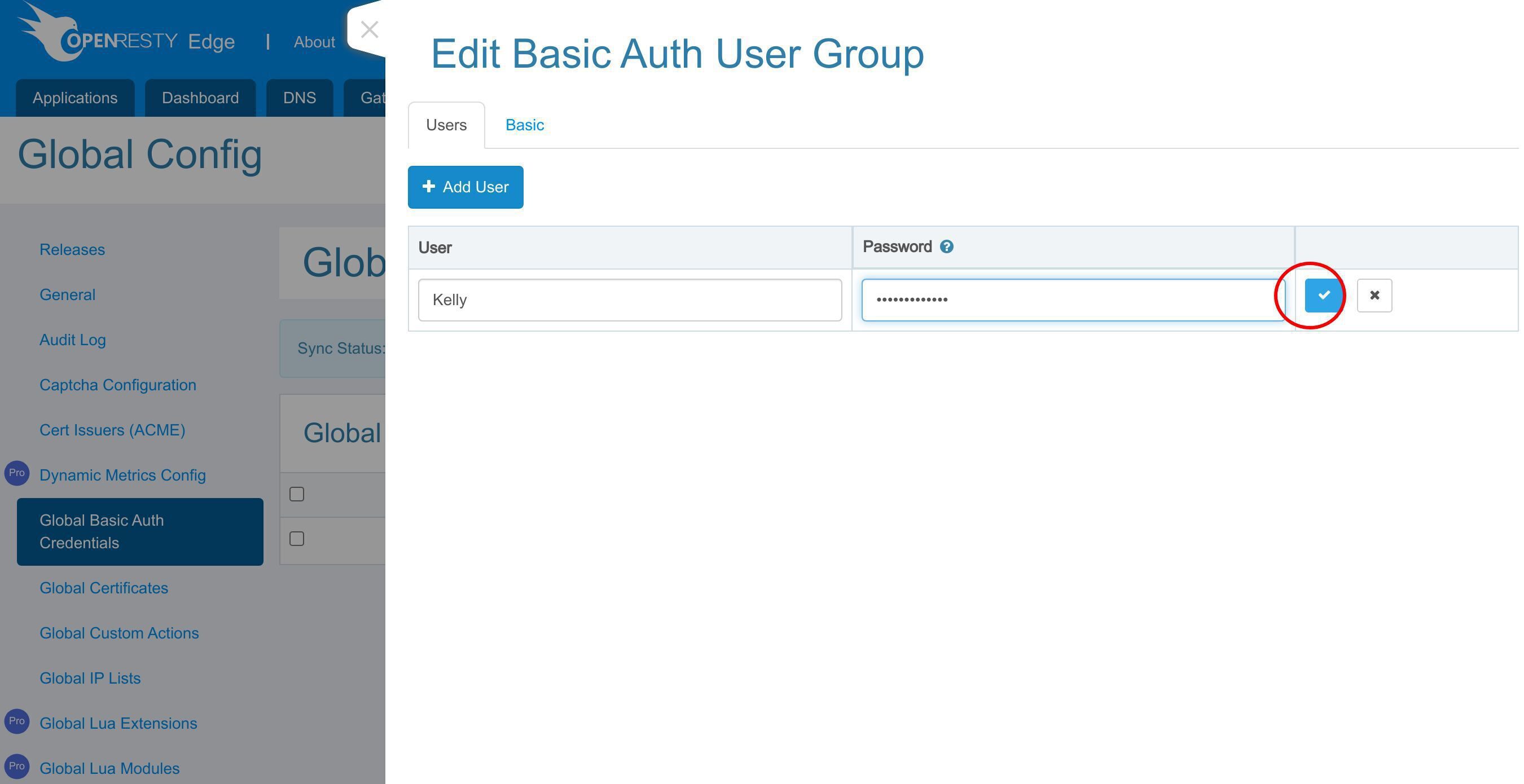
保存してください。
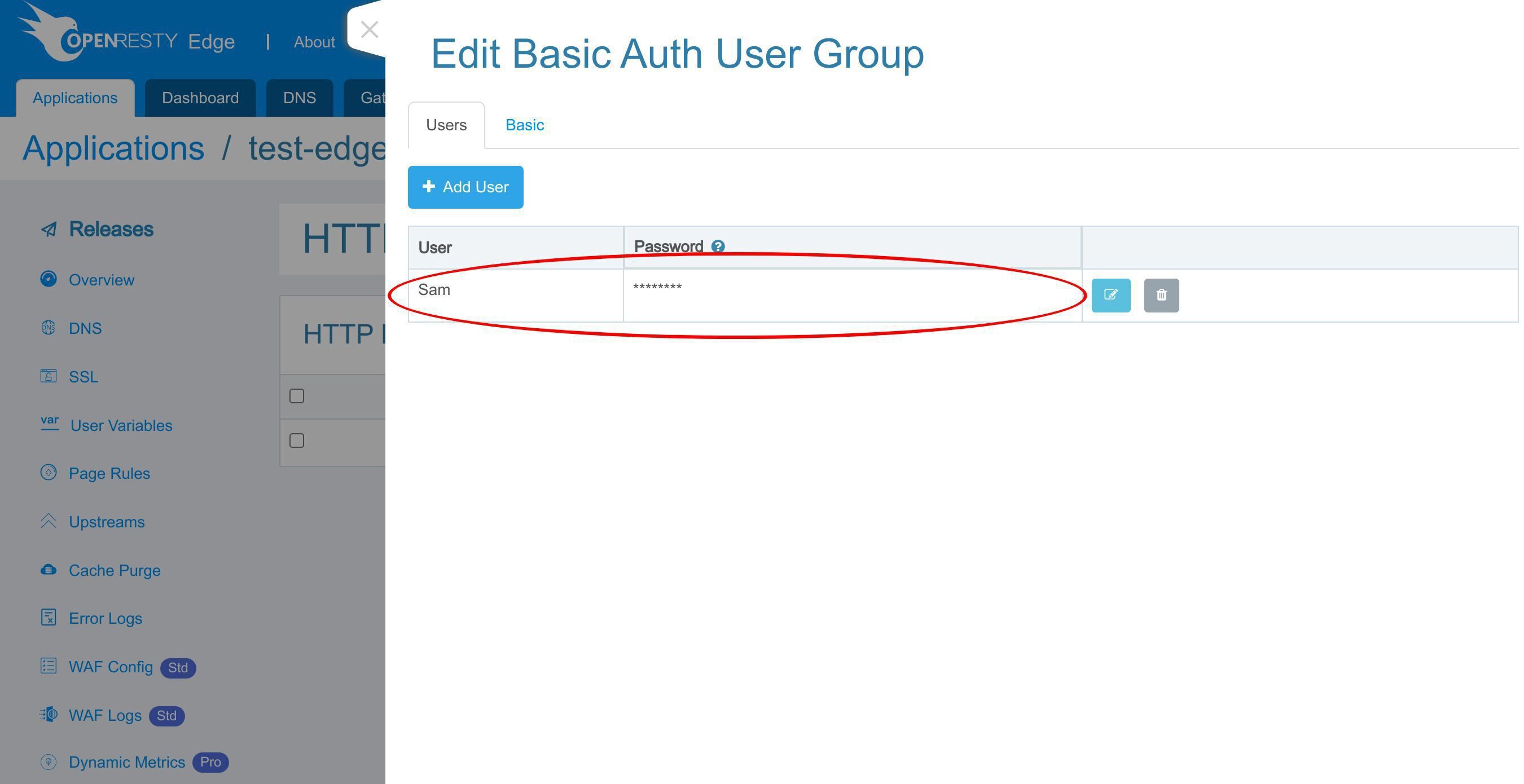
これで「tutorial-group」というユーザーグループに新しいユーザーが追加されました。
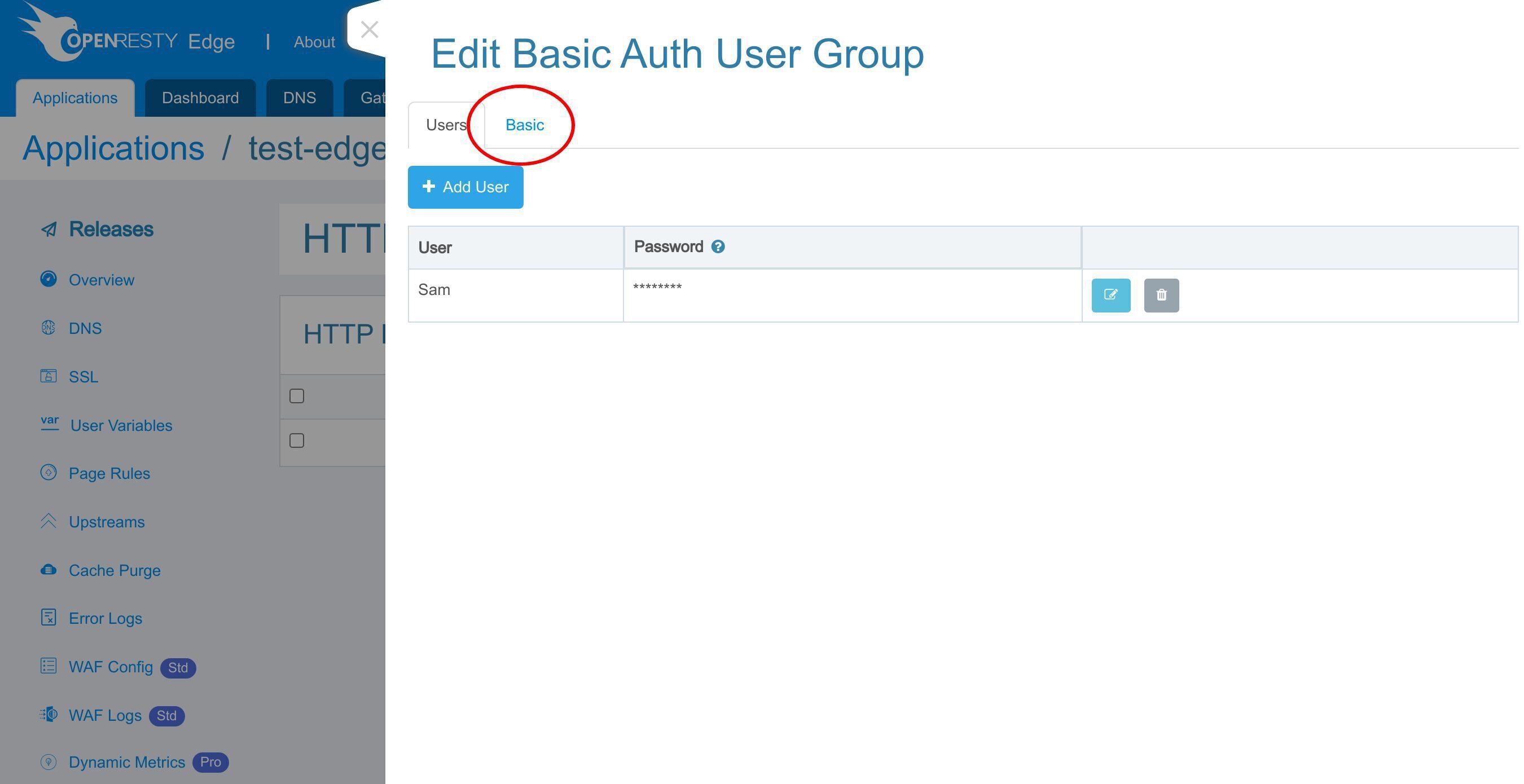
なお、基本タブでユーザーグループの設定を編集することができます。ここでは変更を加えません。
このページを閉じてください。
基本認証の有効化
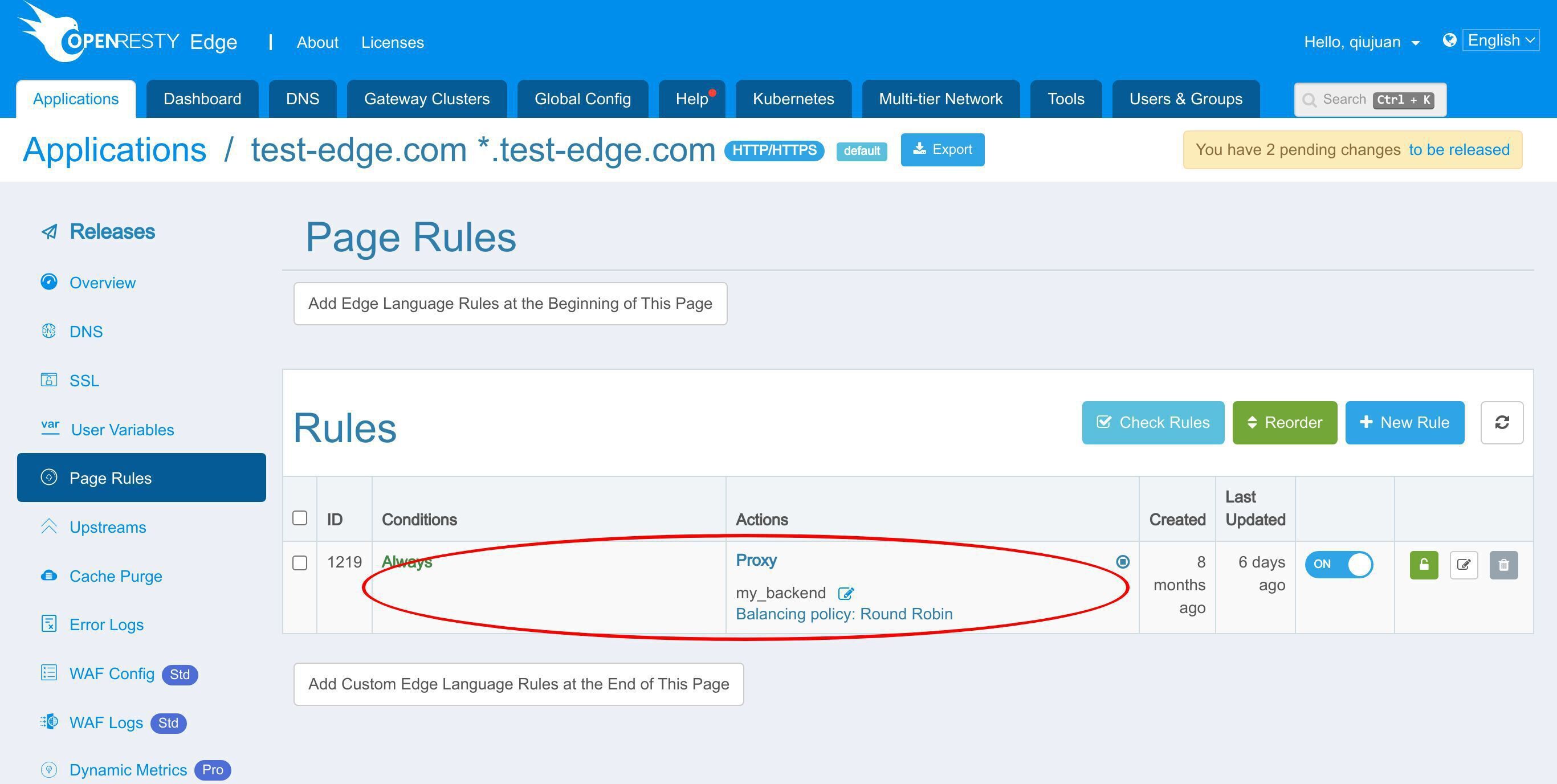
ページルールのページに移動し、基本認証を有効にしてください。
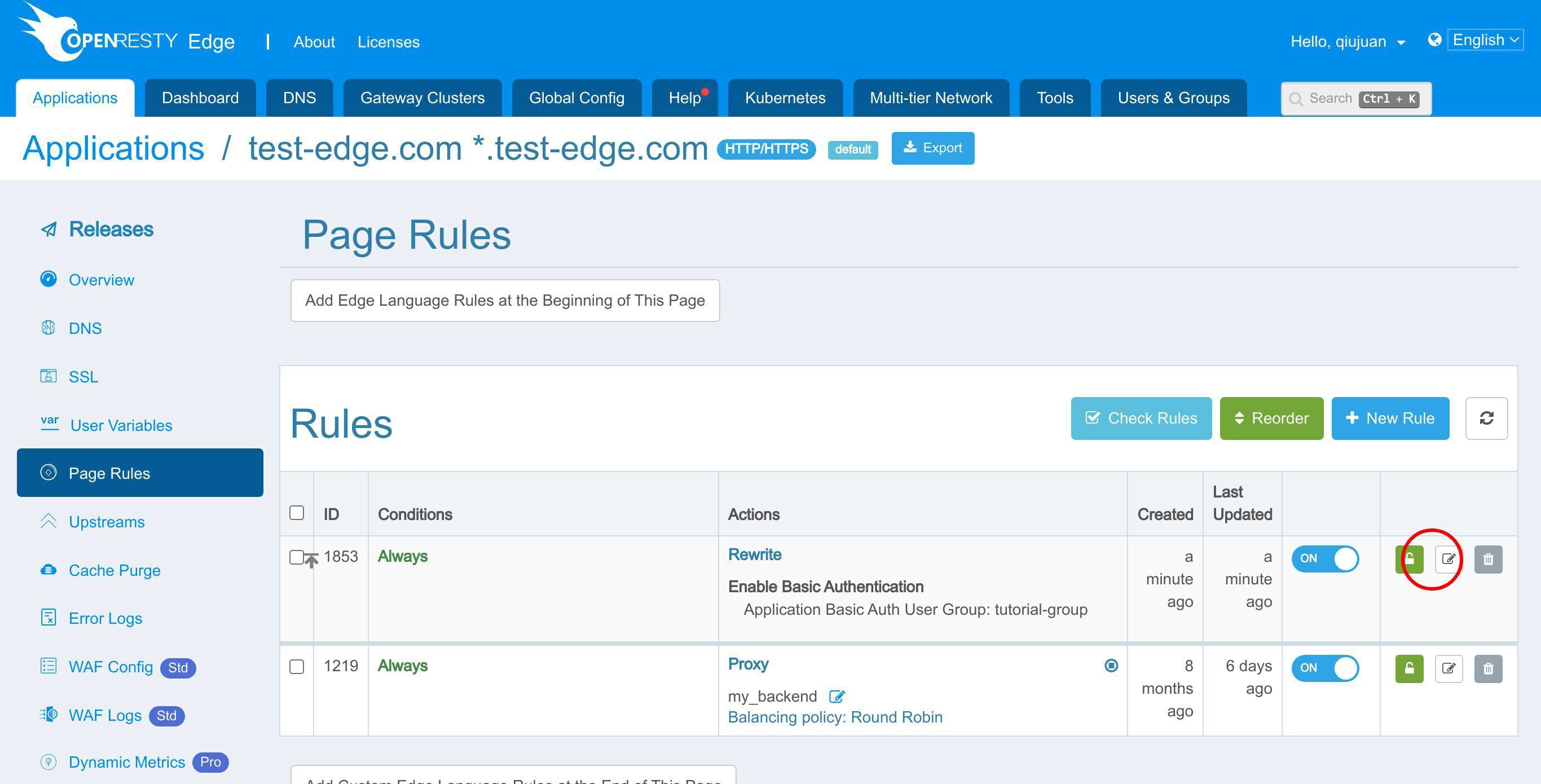
この既存のページルールには、事前に定義されたアップストリームへのリバースプロキシが設定されています。この部分については、以前のチュートリアルで説明しました。
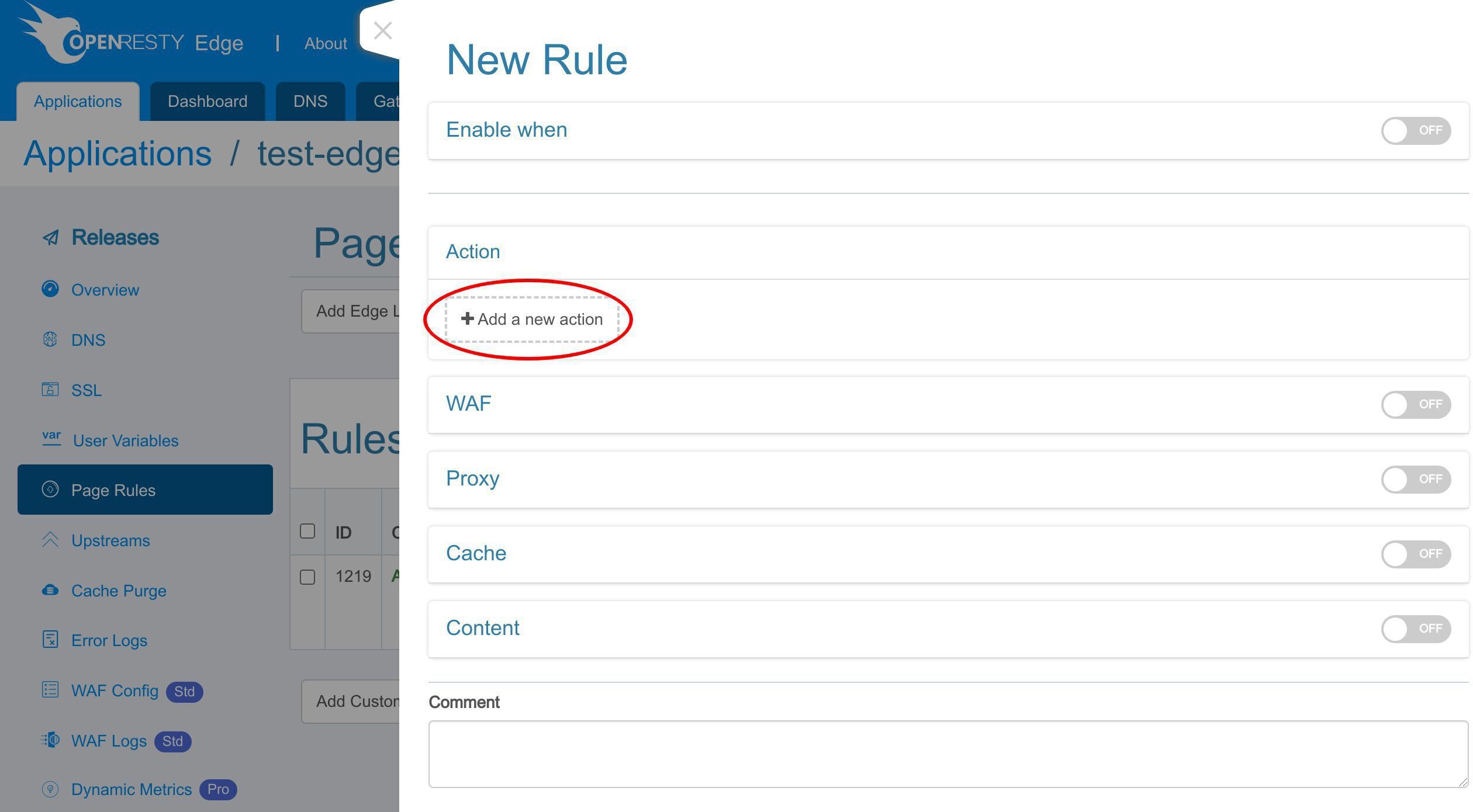
新しいページルールを追加しましょう。
新しいアクションを追加します。
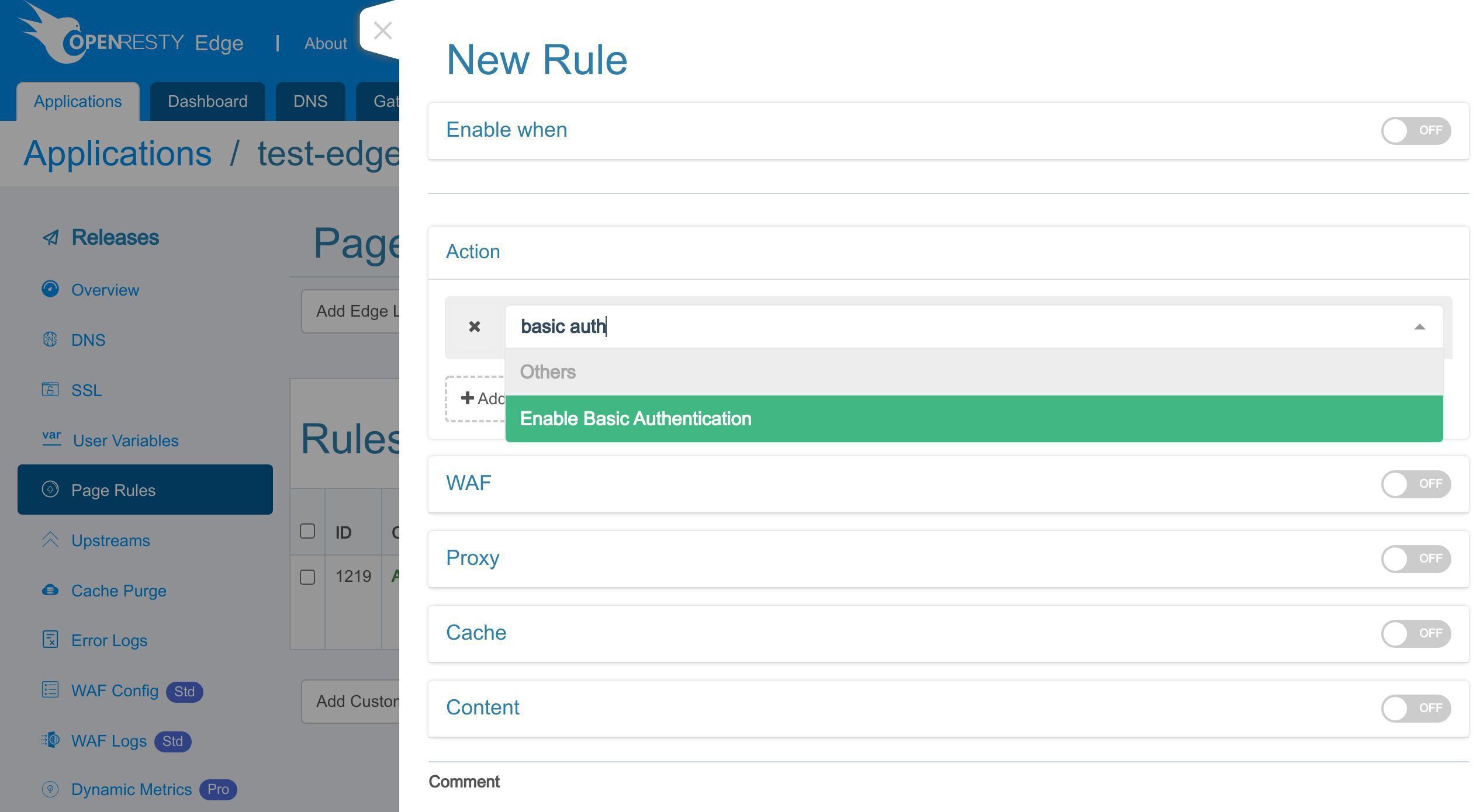
「basic auth」と入力して検索します。
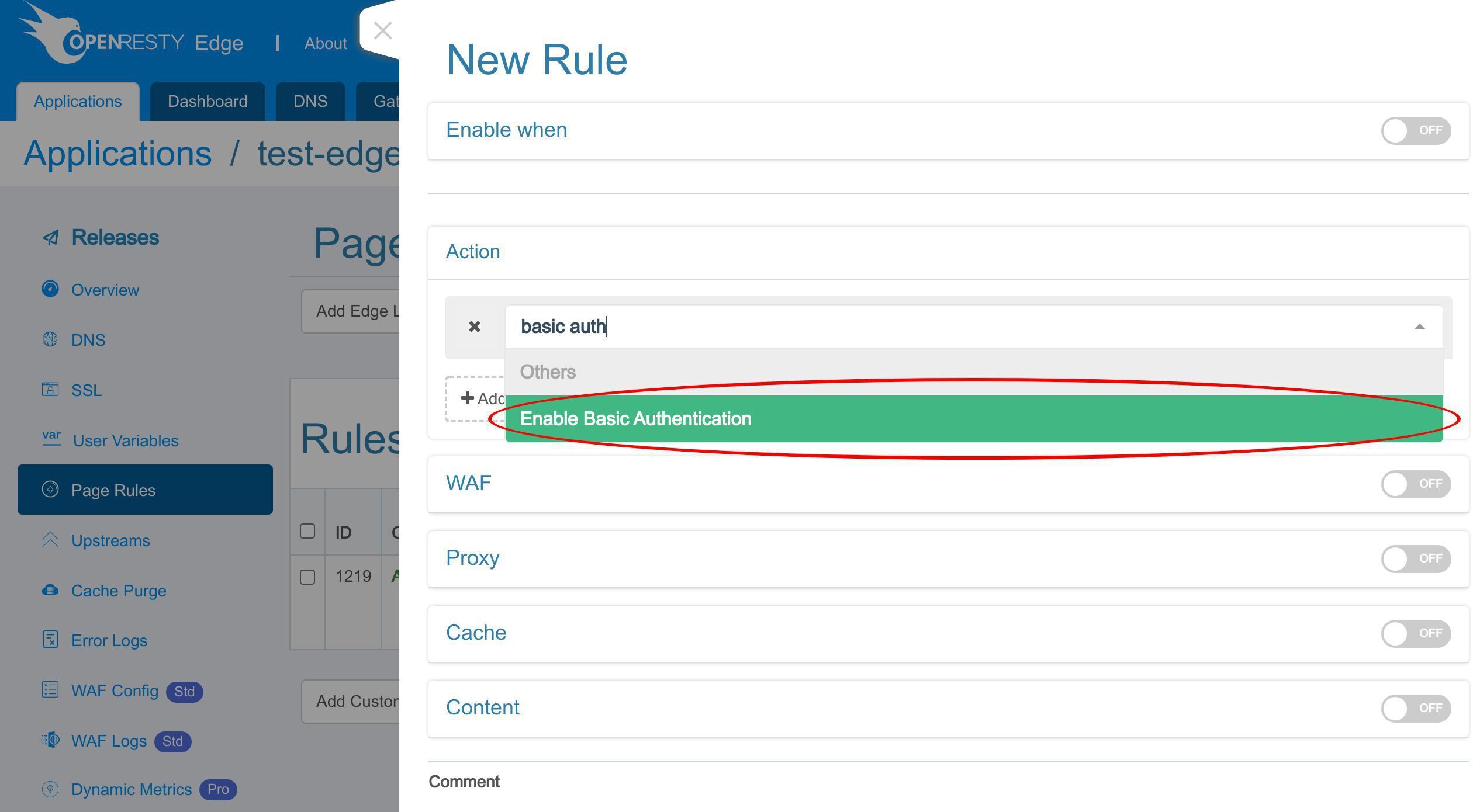
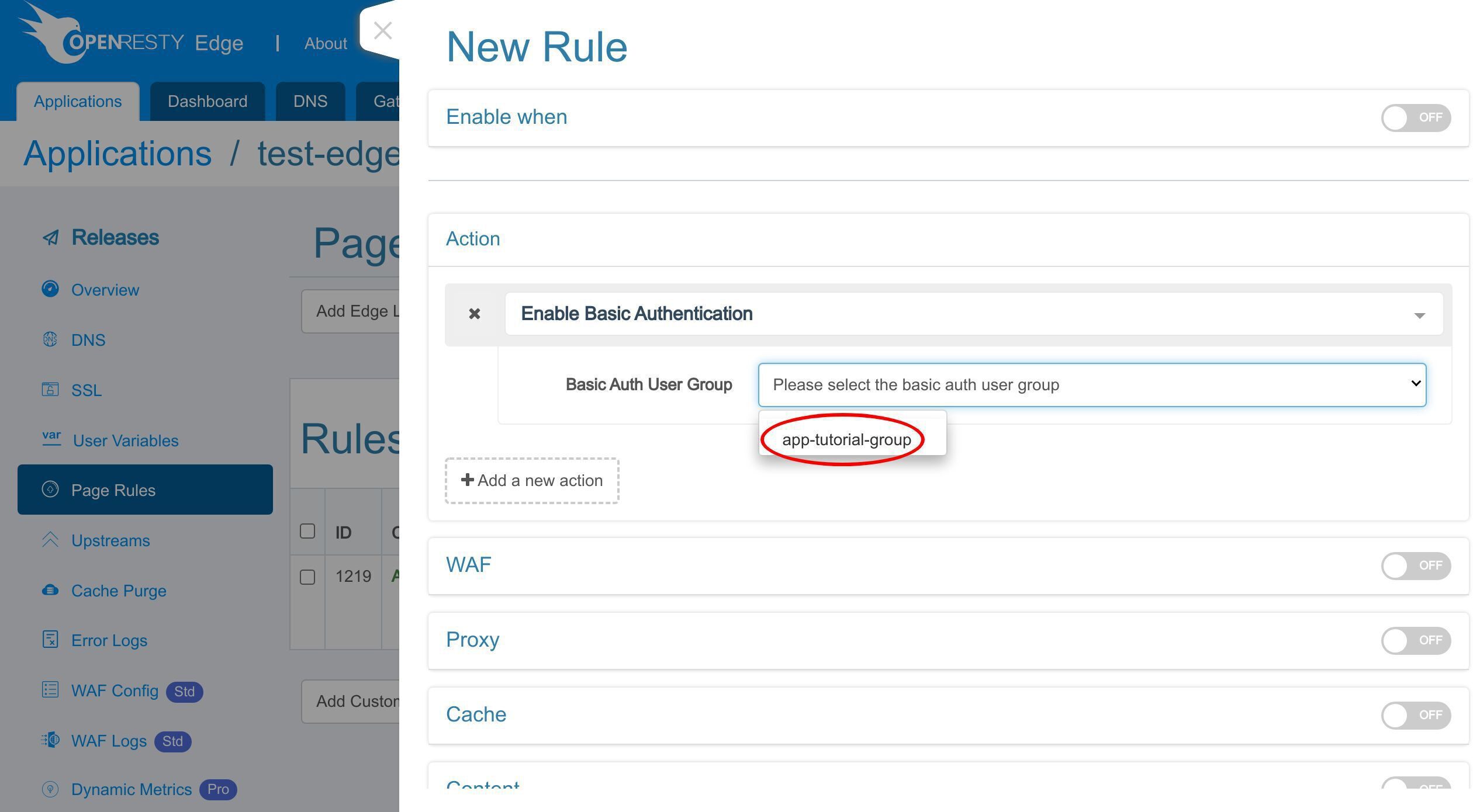
「基本認証を有効にする」オプションを選択します。
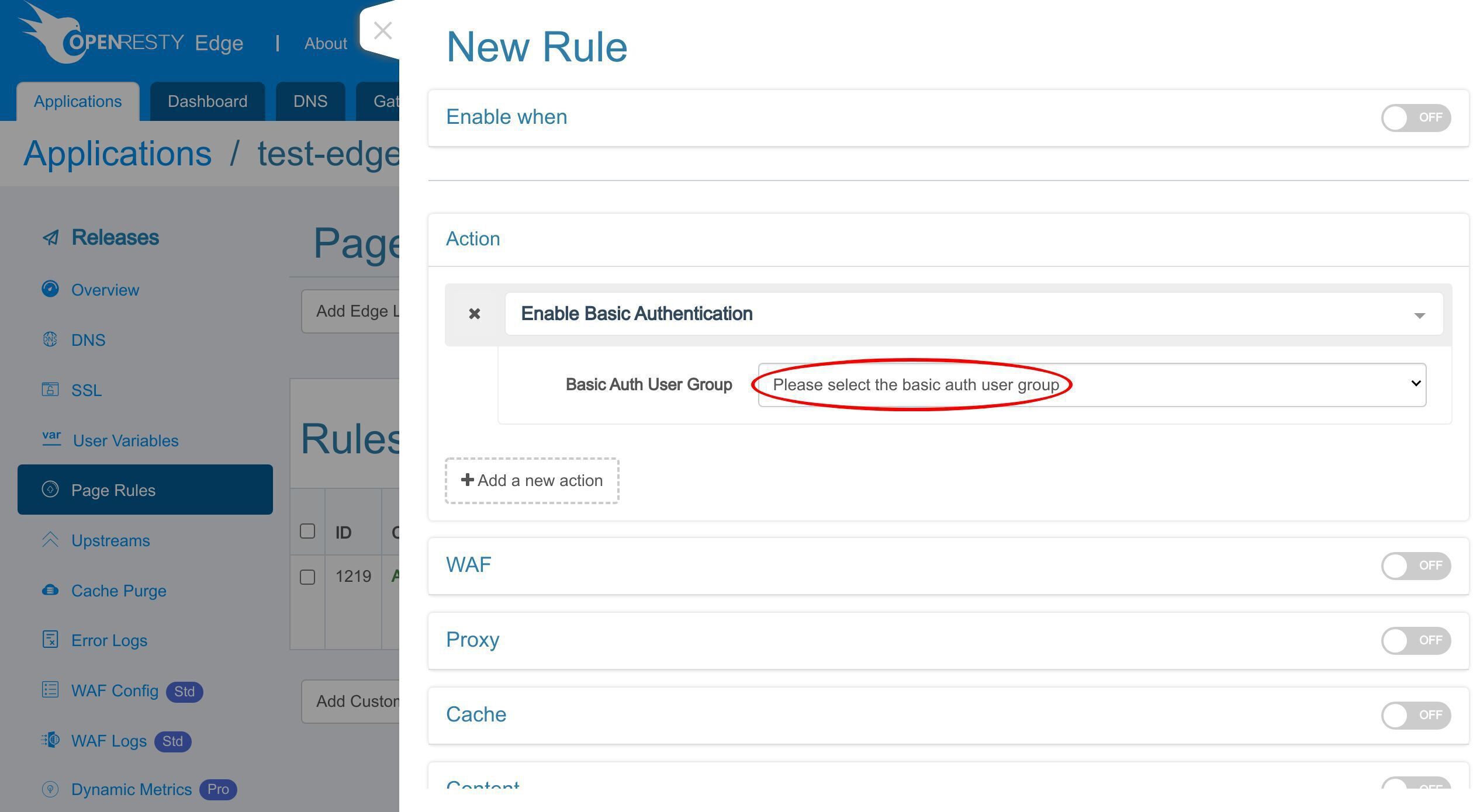
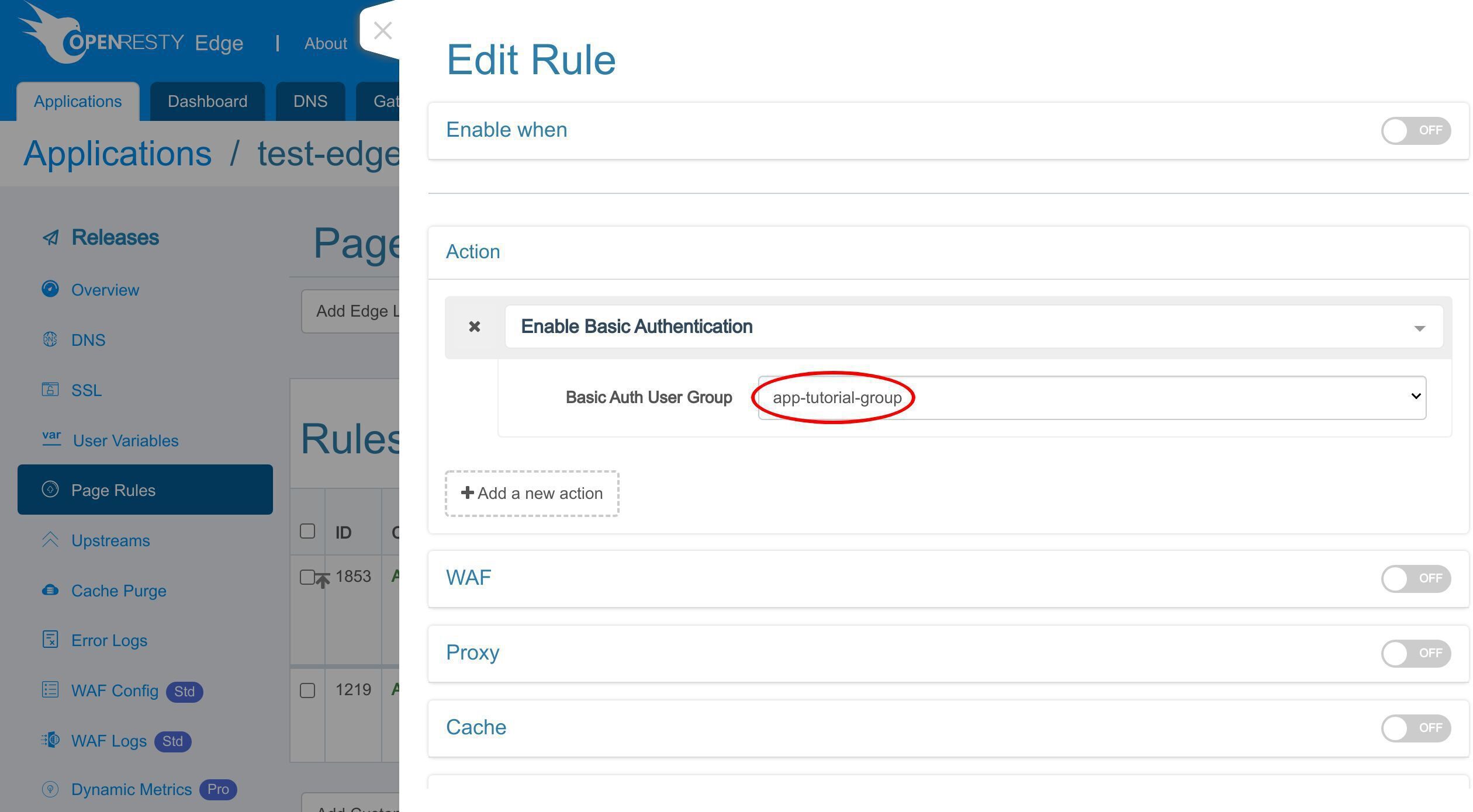
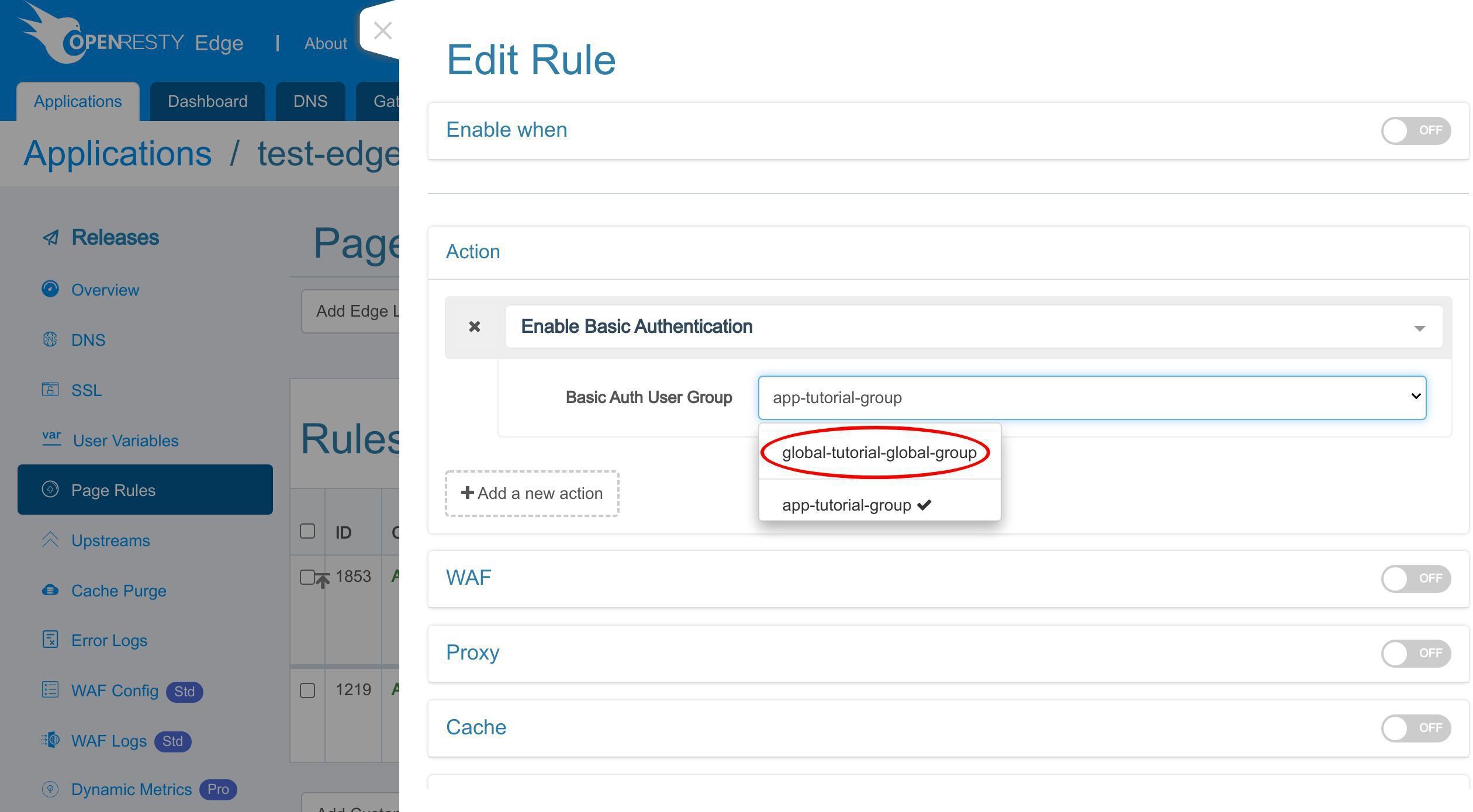
先ほど作成した基本認証ユーザーグループを選択します。
「app-tutorial-group」を選択します。
追加の「app-」プレフィックスは、このユーザーグループが現在のアプリケーションにのみ使用されることを示しています。グローバルな基本認証のユーザーグループ名には、追加のプレフィックス「global-」が付きます。グローバル HTTP 基本認証の設定については後ほど説明いたします。
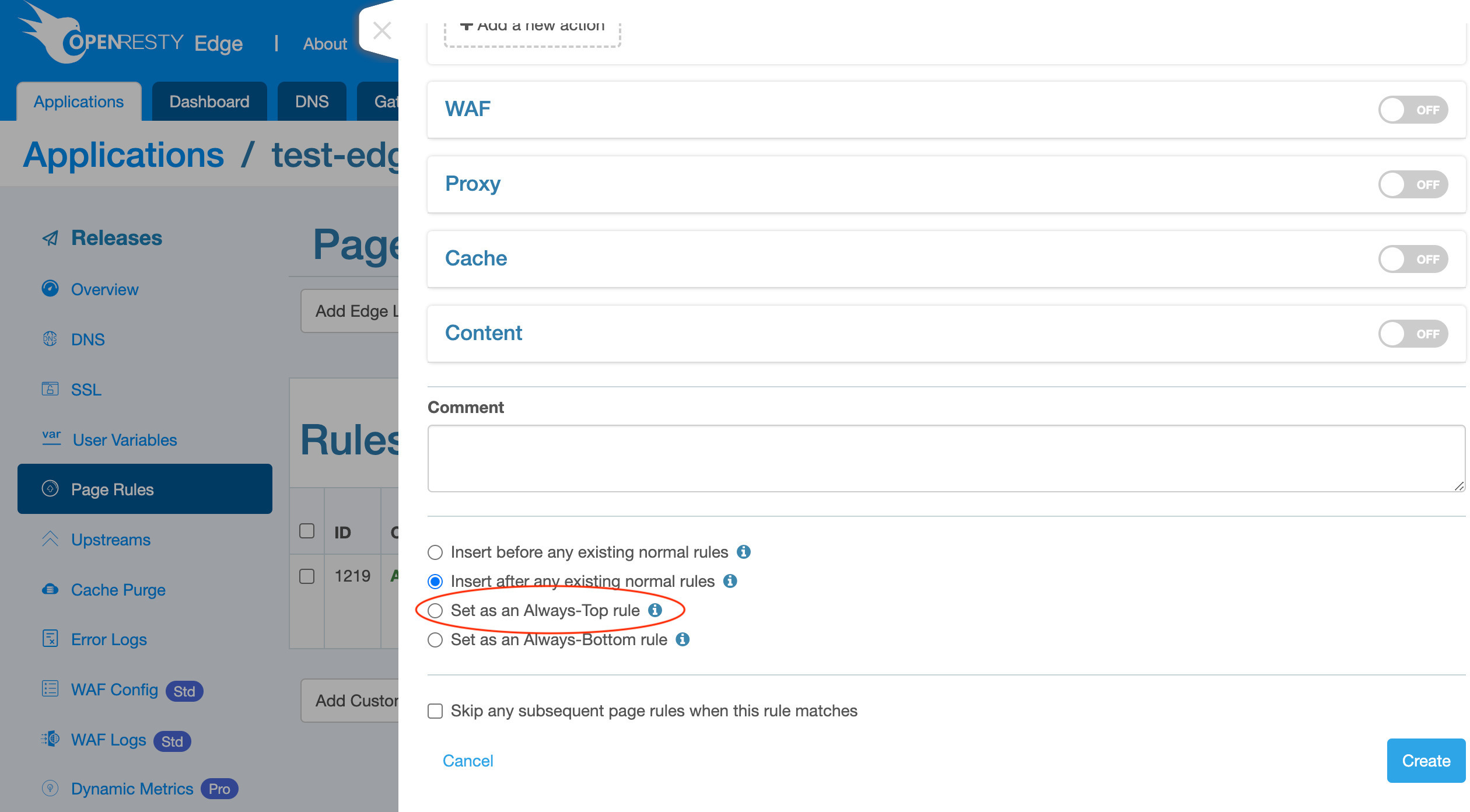
このルールを「トップルール」として設定し、常に最初に実行されるようにします。任意の順序を設定することができます。
このルールを保存します。
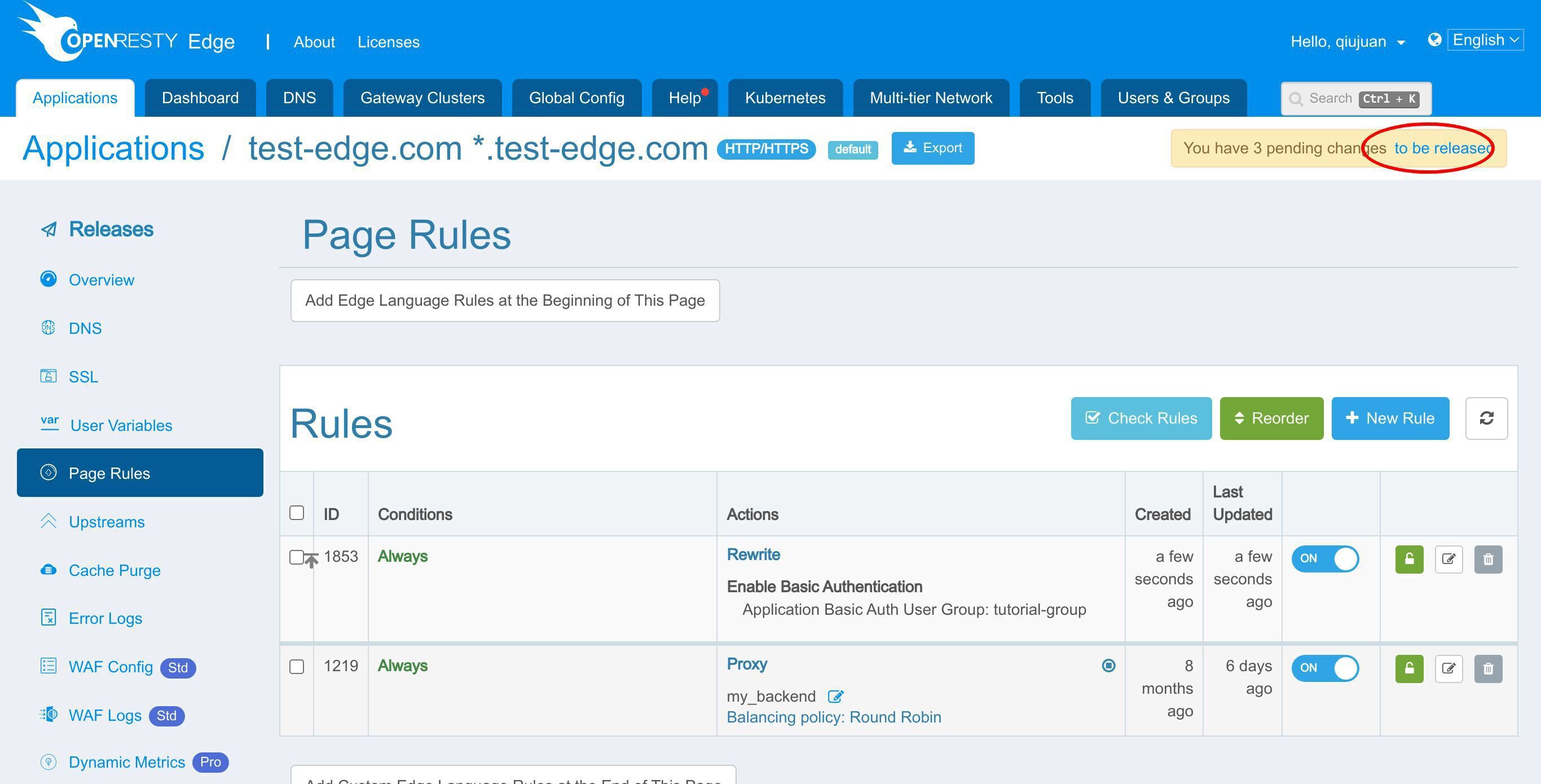
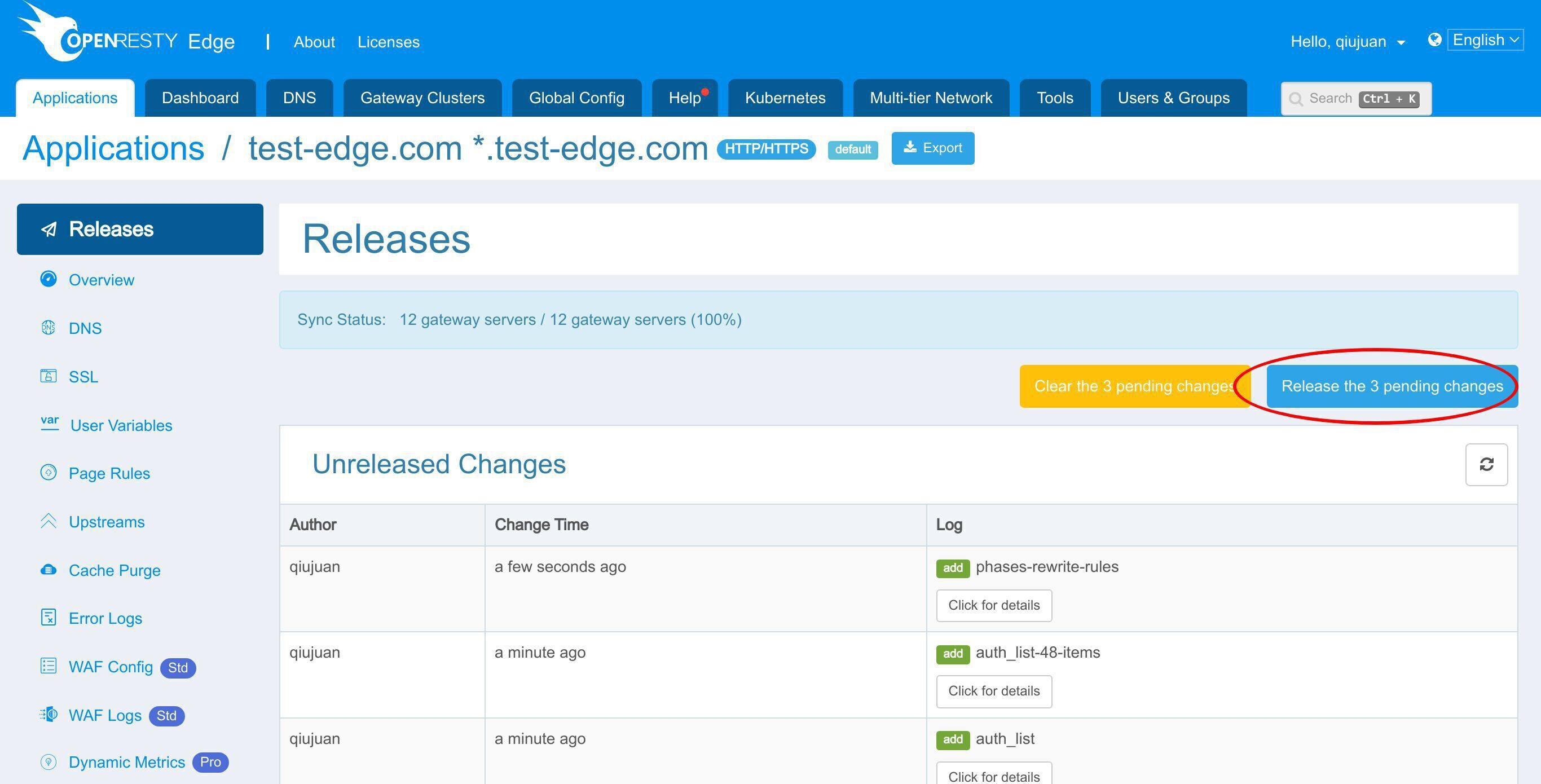
通常通り、この新しい変更をプッシュするためにリリースする必要があります。
このボタンをクリックします。
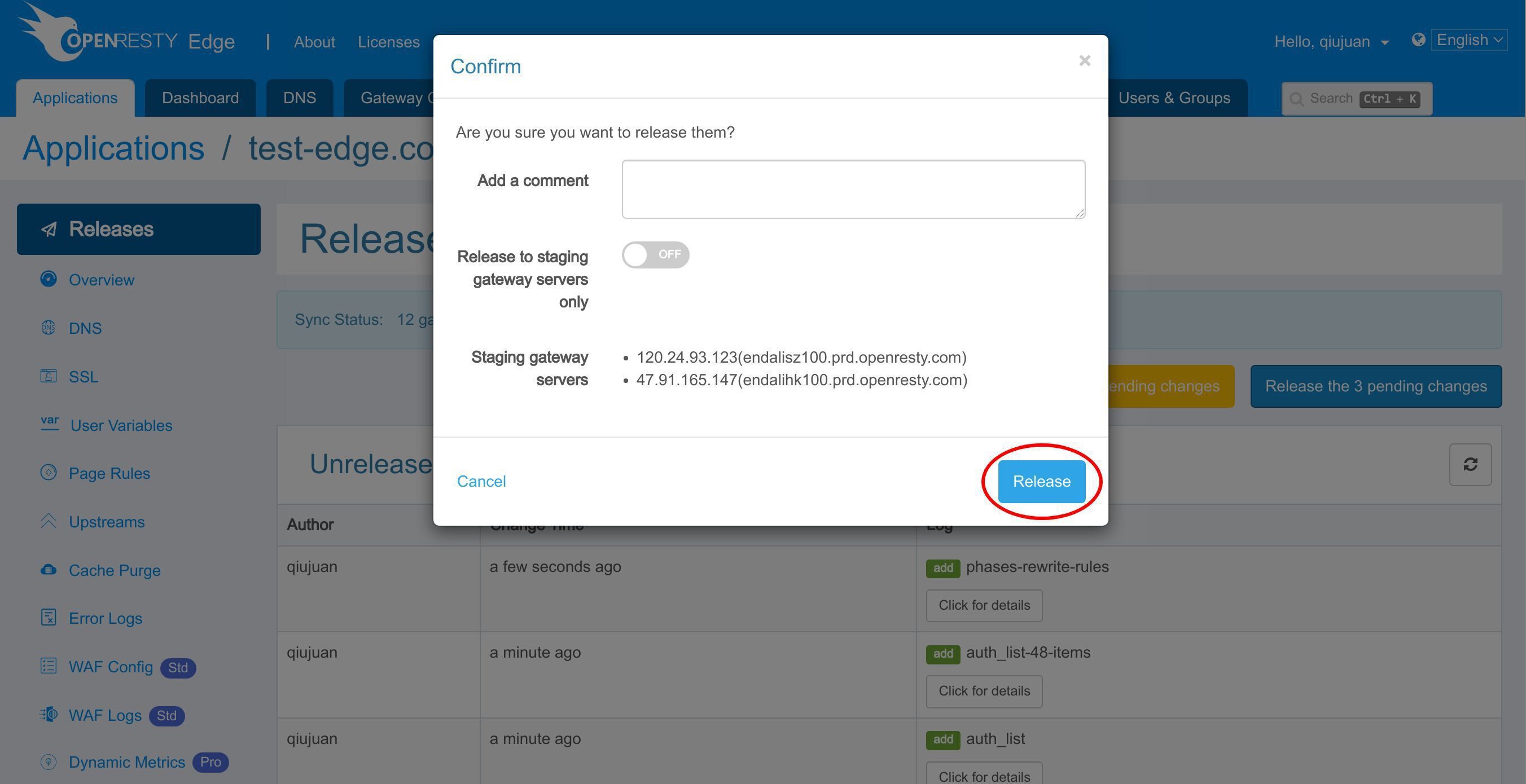
リリースします!
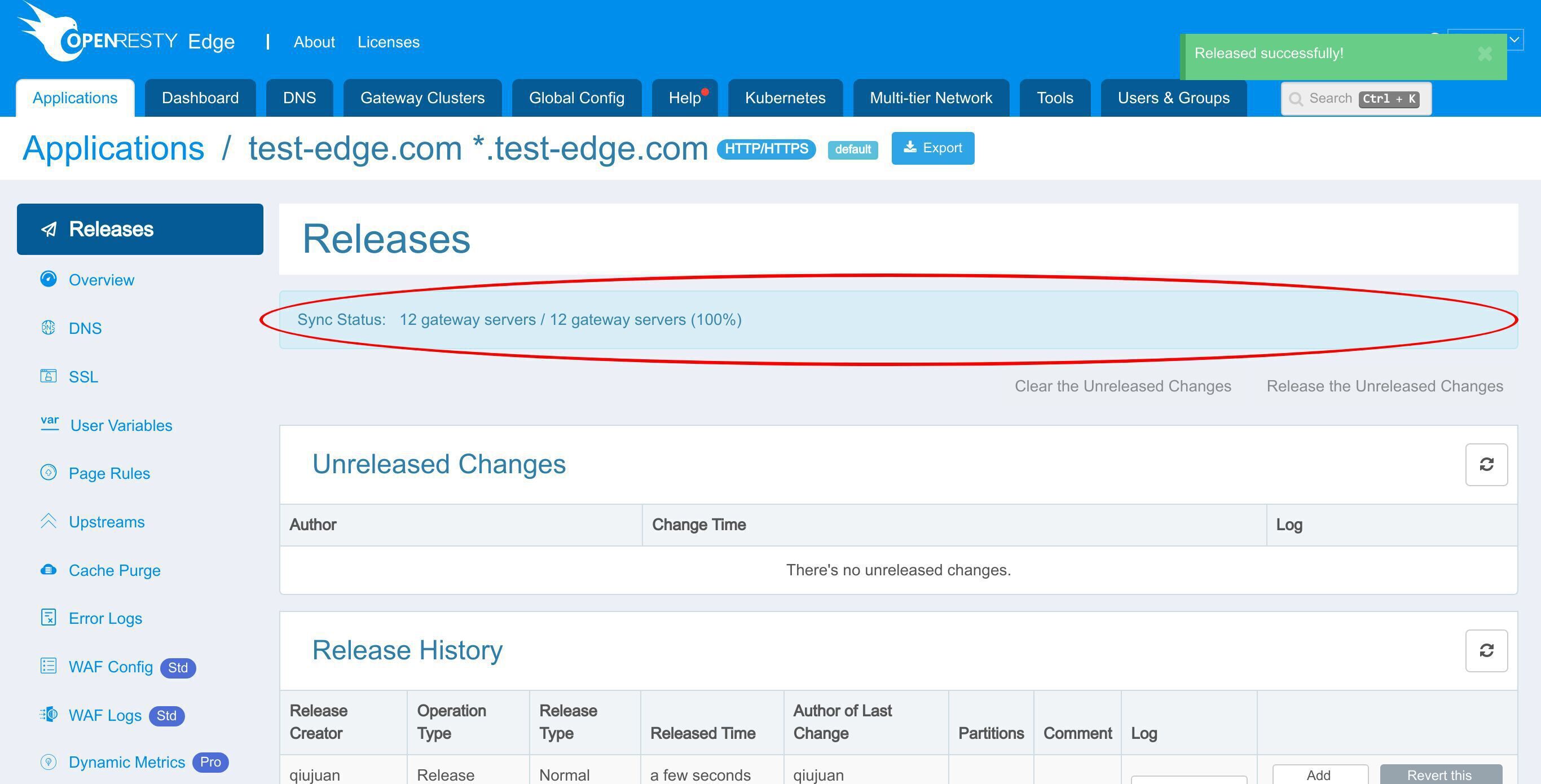
変更が全てのゲートウェイサーバーに同期されました。
新しいページルールが全てのゲートウェイクラスターとサーバーにプッシュされました。
設定の変更にはサーバーのリロード、再起動、バイナリのアップグレードが不要です。そのため、非常に効率的でスケーラブルです。
テスト
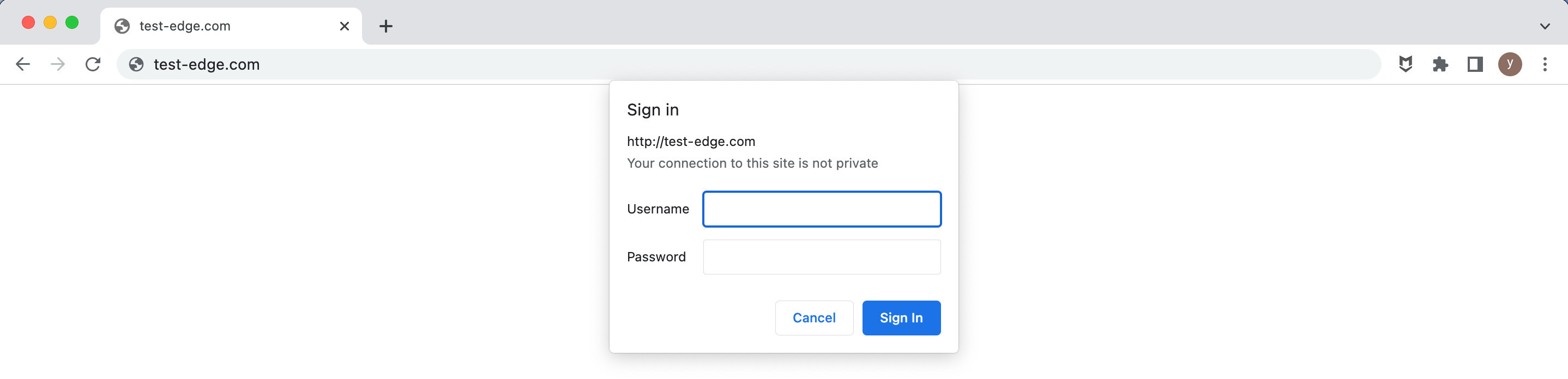
ゲートウェイアプリケーションにアクセスしてみましょう。ウェブページの内容を表示する代わりに、ウェブブラウザの認証ダイアログがトリガーされることが確認できます。
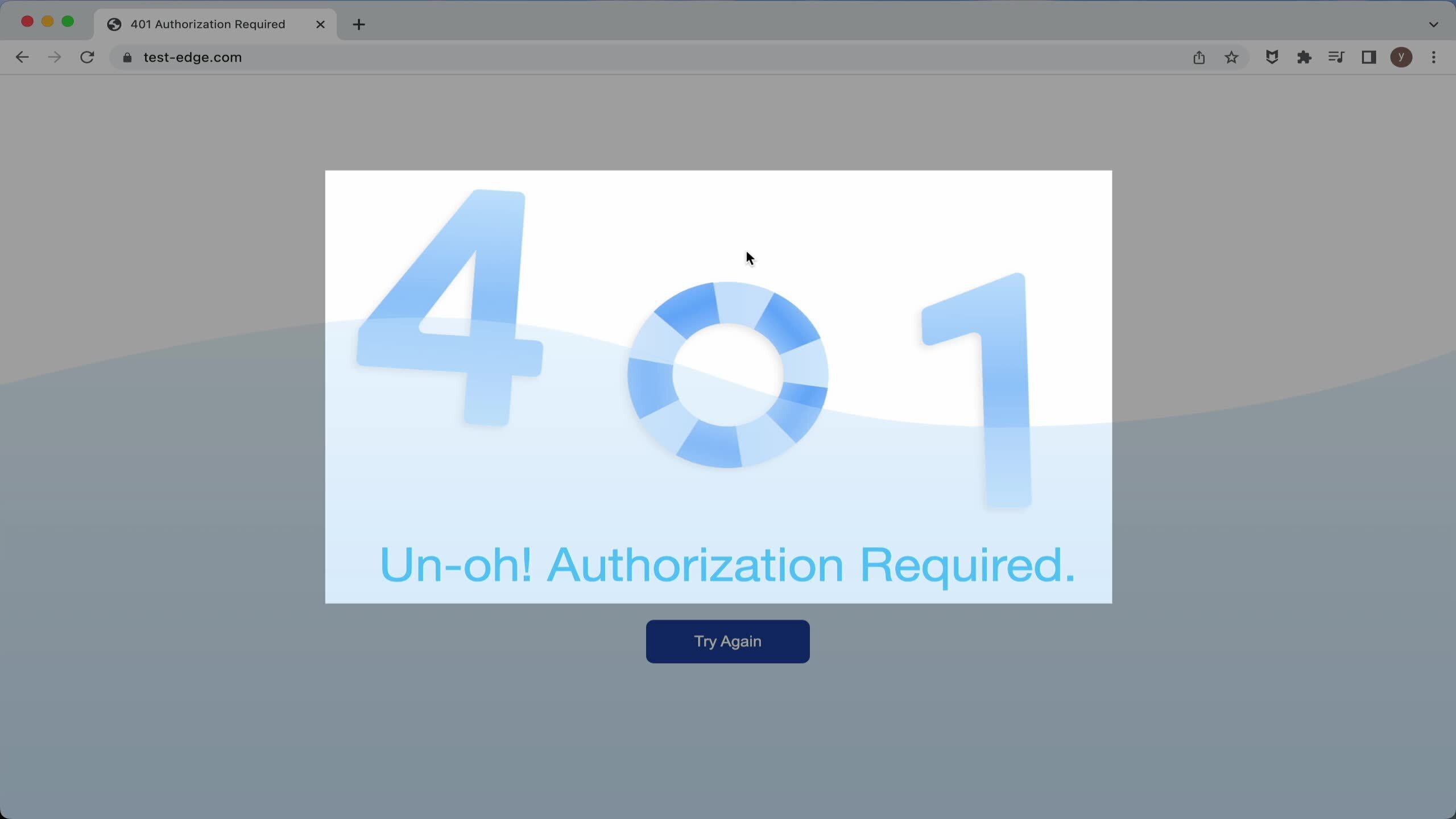
まず、「キャンセル」ボタンをクリックしてみましょう。ページが「401 Unauthorized」エラーページに変わることが確認できます。
ページをリフレッシュします。
今回は、事前に準備した正しいユーザー名とパスワードを入力します。
これでウェブページにアクセスできるようになりました。
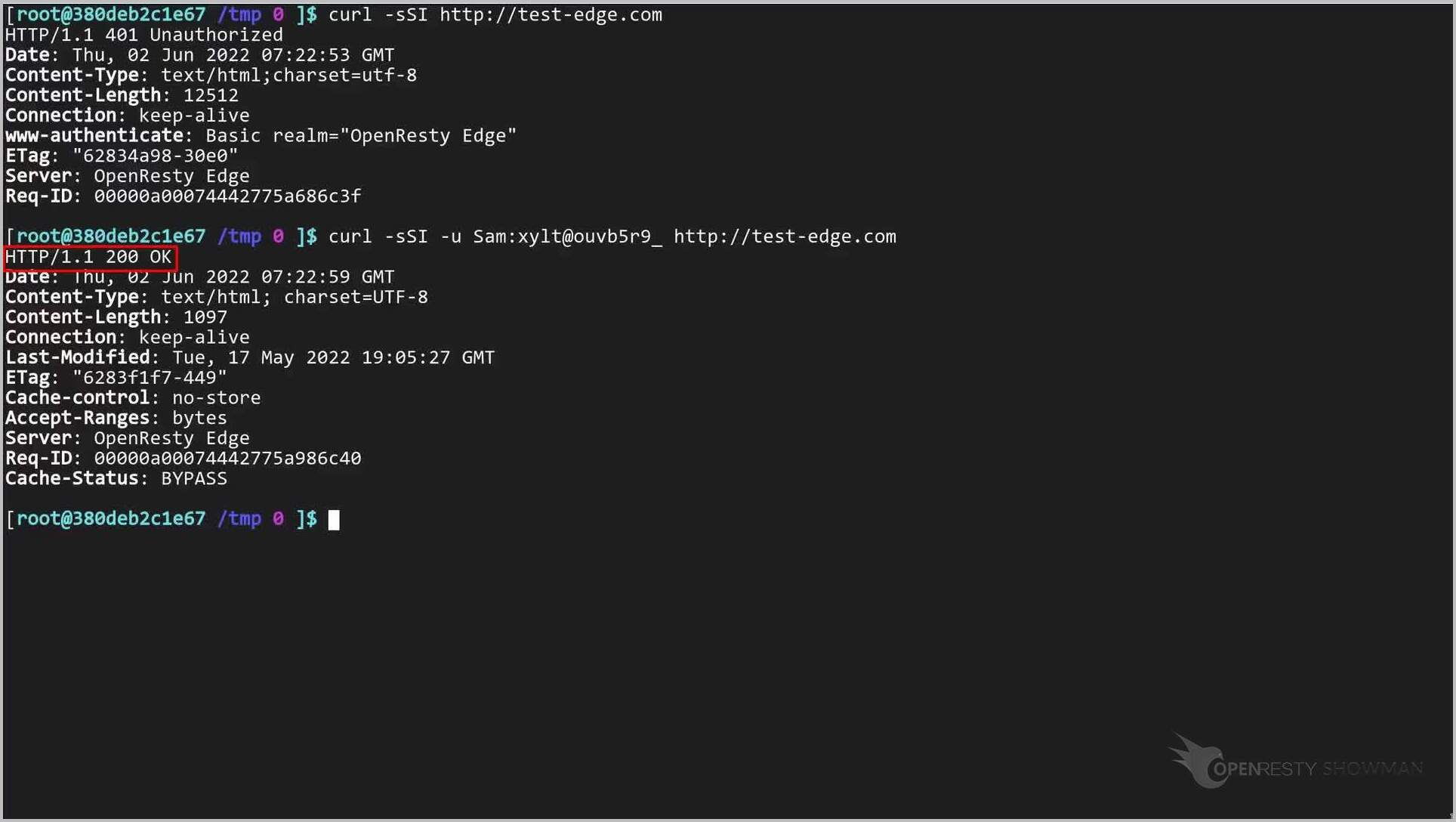
次に、curl ツールを使用してコマンドラインで HTTP 基本認証の設定をテストしましょう。
ターミナルでテストリクエストを送信します。
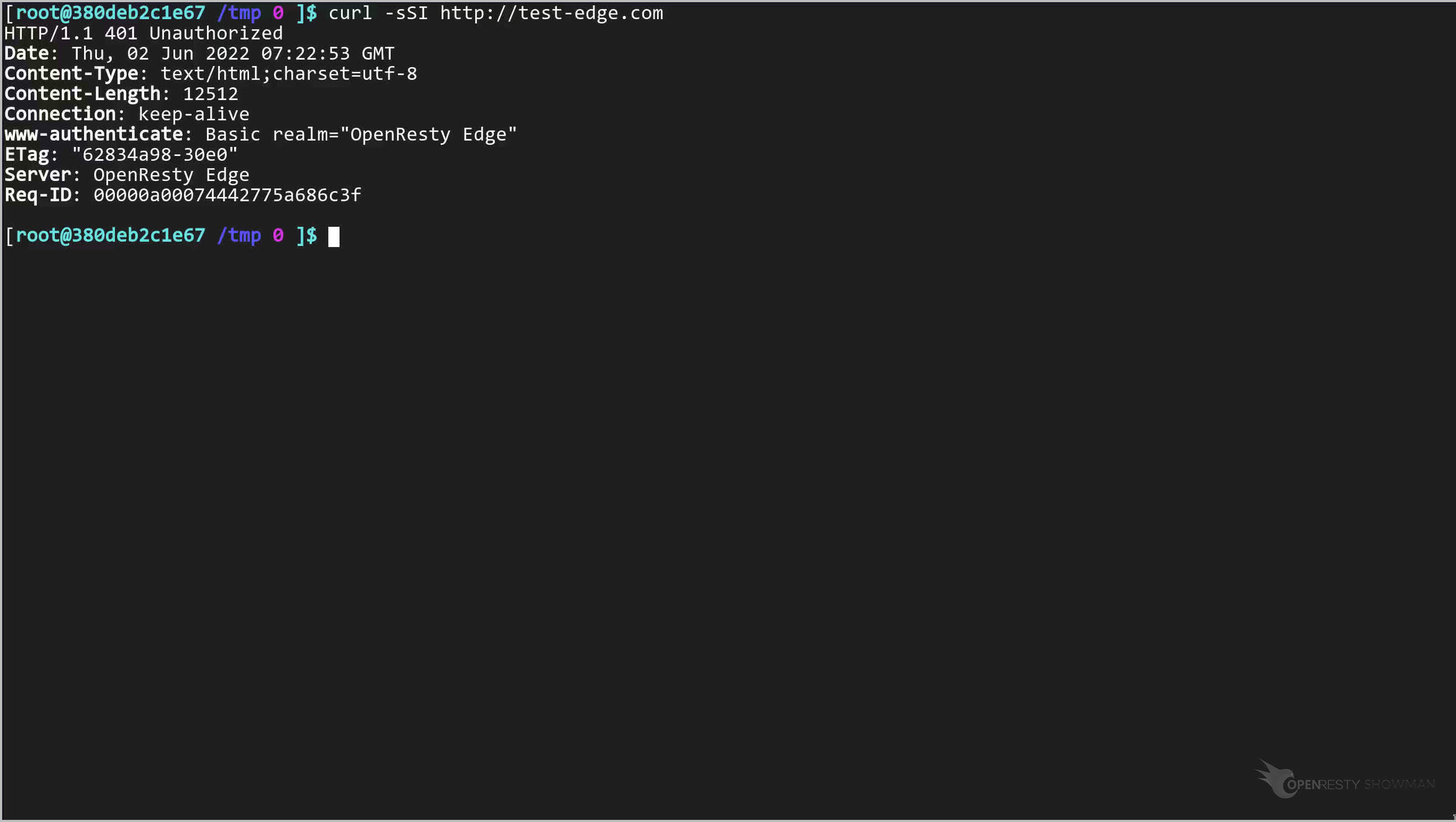
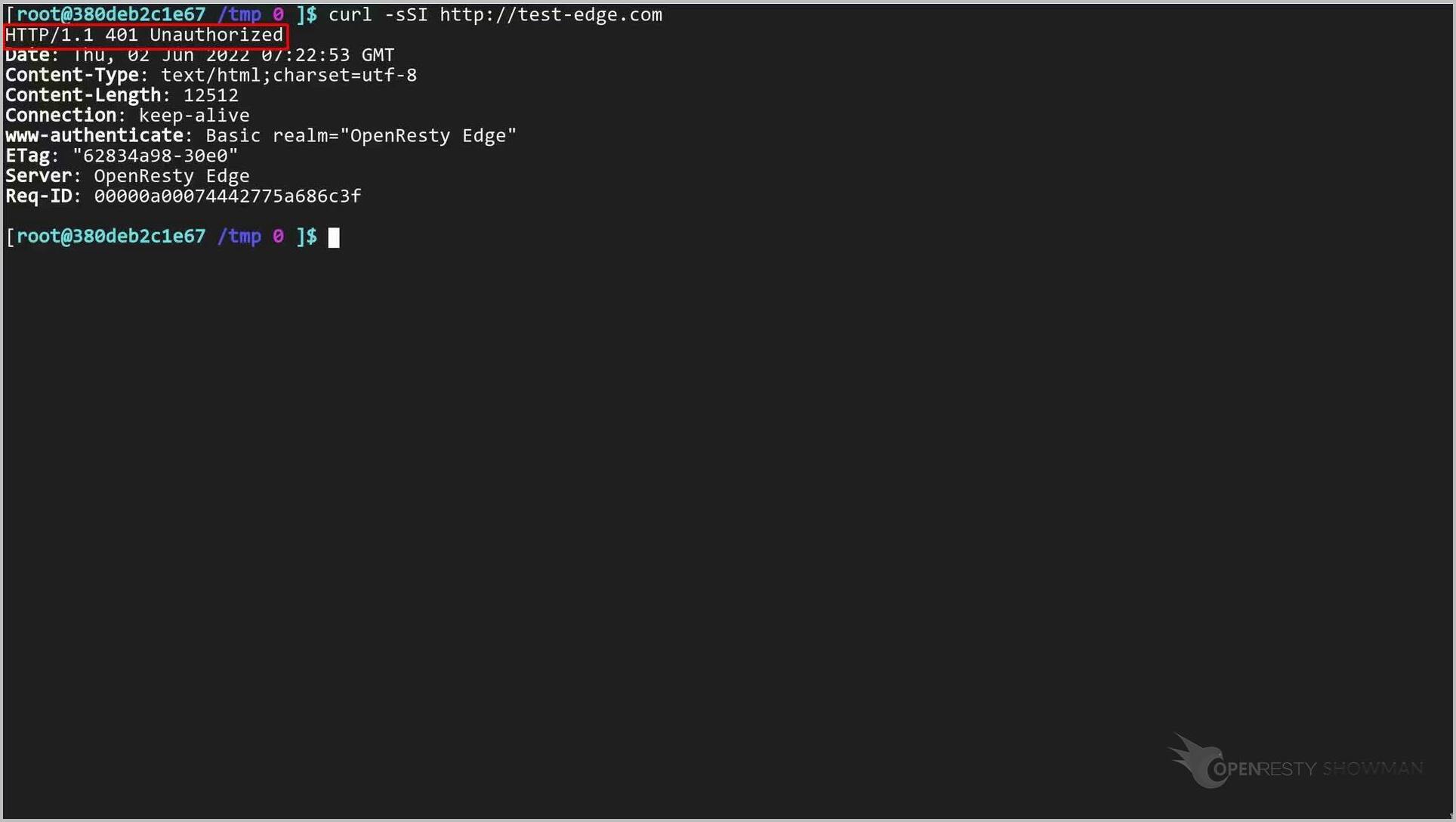
curl -sSI http://test-edge.com
レスポンスが 401 Unauthorized であることが確認できます。
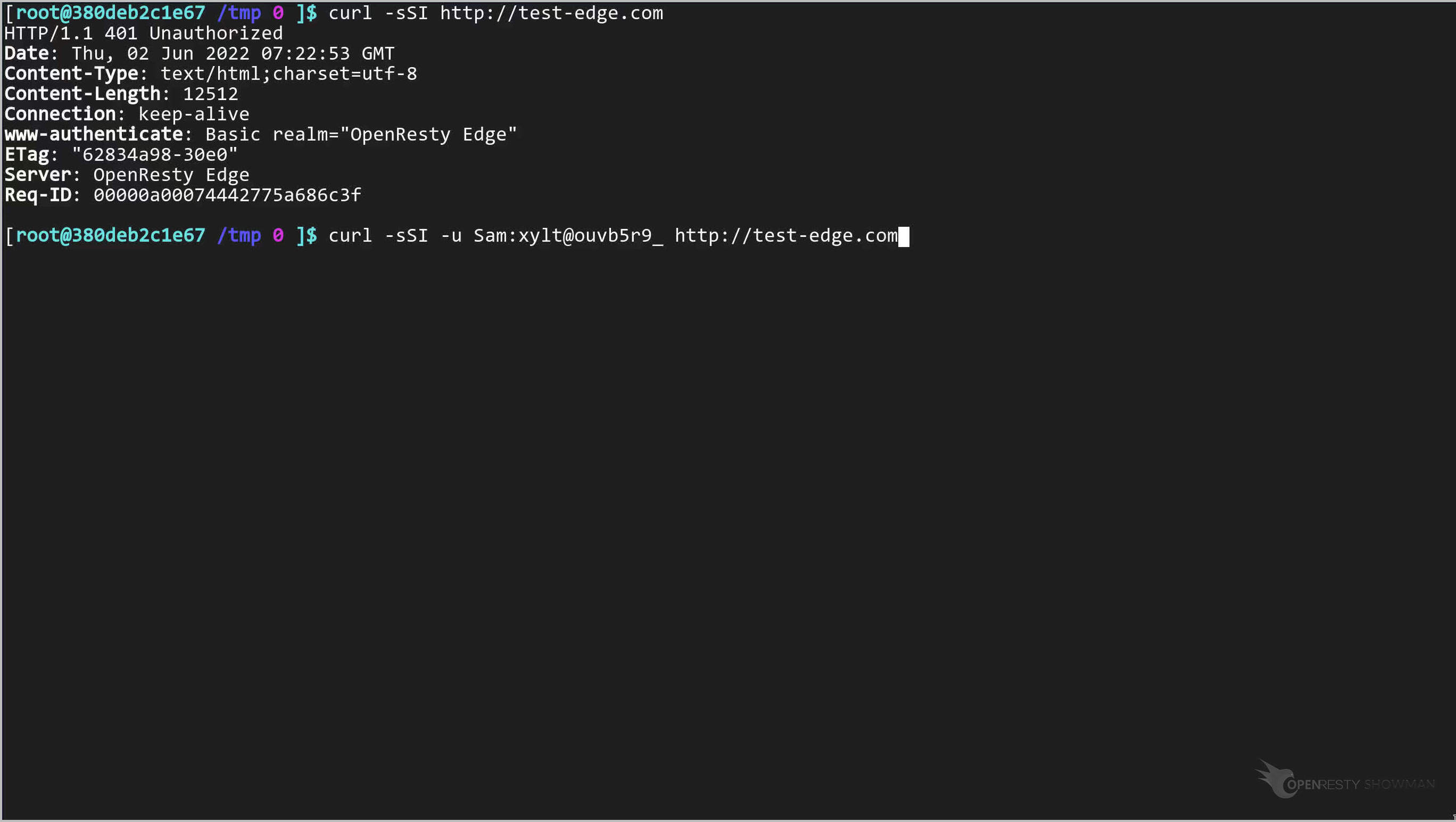
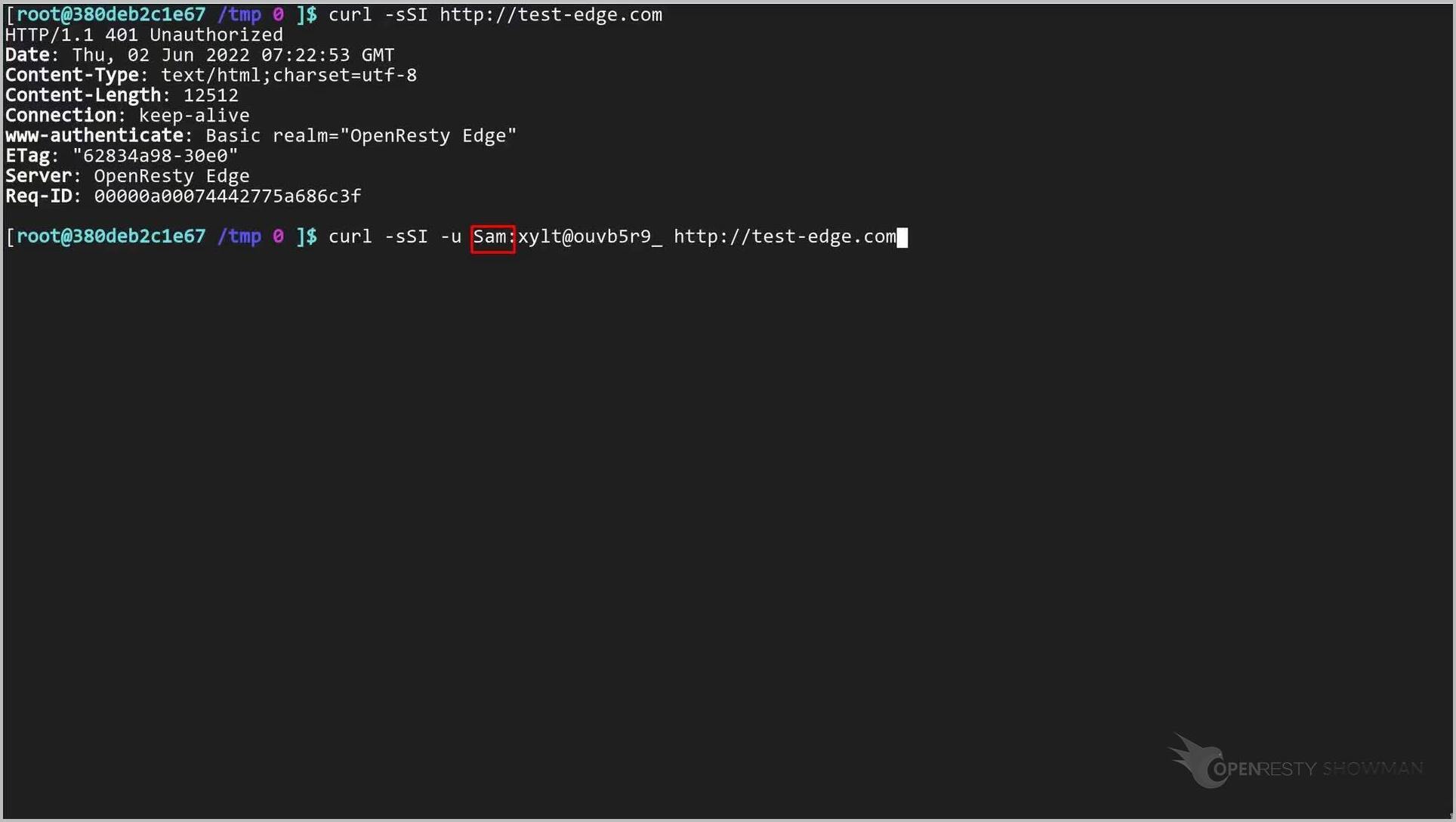
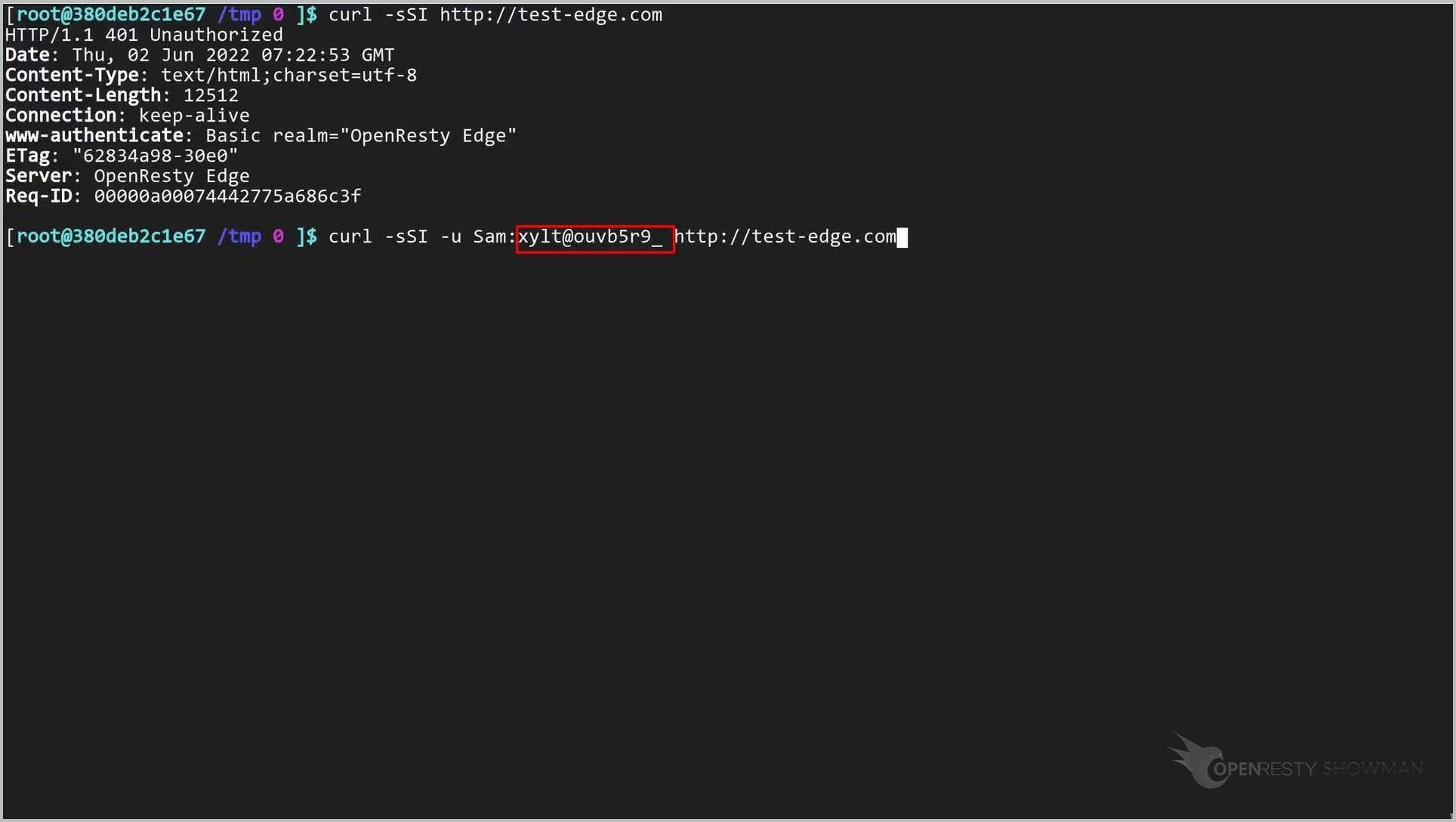
今回は「u」オプションを使用して、基本認証の資格情報を指定しましょう。
こちらがユーザー名です。
こちらがプレーンテキストのパスワードです。
このコマンドを実行します。
現在、レスポンスが 200 OK であることが確認できます。認証に成功し、サーバーが最終的なレスポンスを返しました。
グローバル HTTP 基本認証の設定
Edge アプリケーション内で基本認証を設定するだけでなく、Edge のグローバル設定でも設定することができます。グローバル認証ユーザーグループは、すべての Edge アプリケーションで利用可能です。
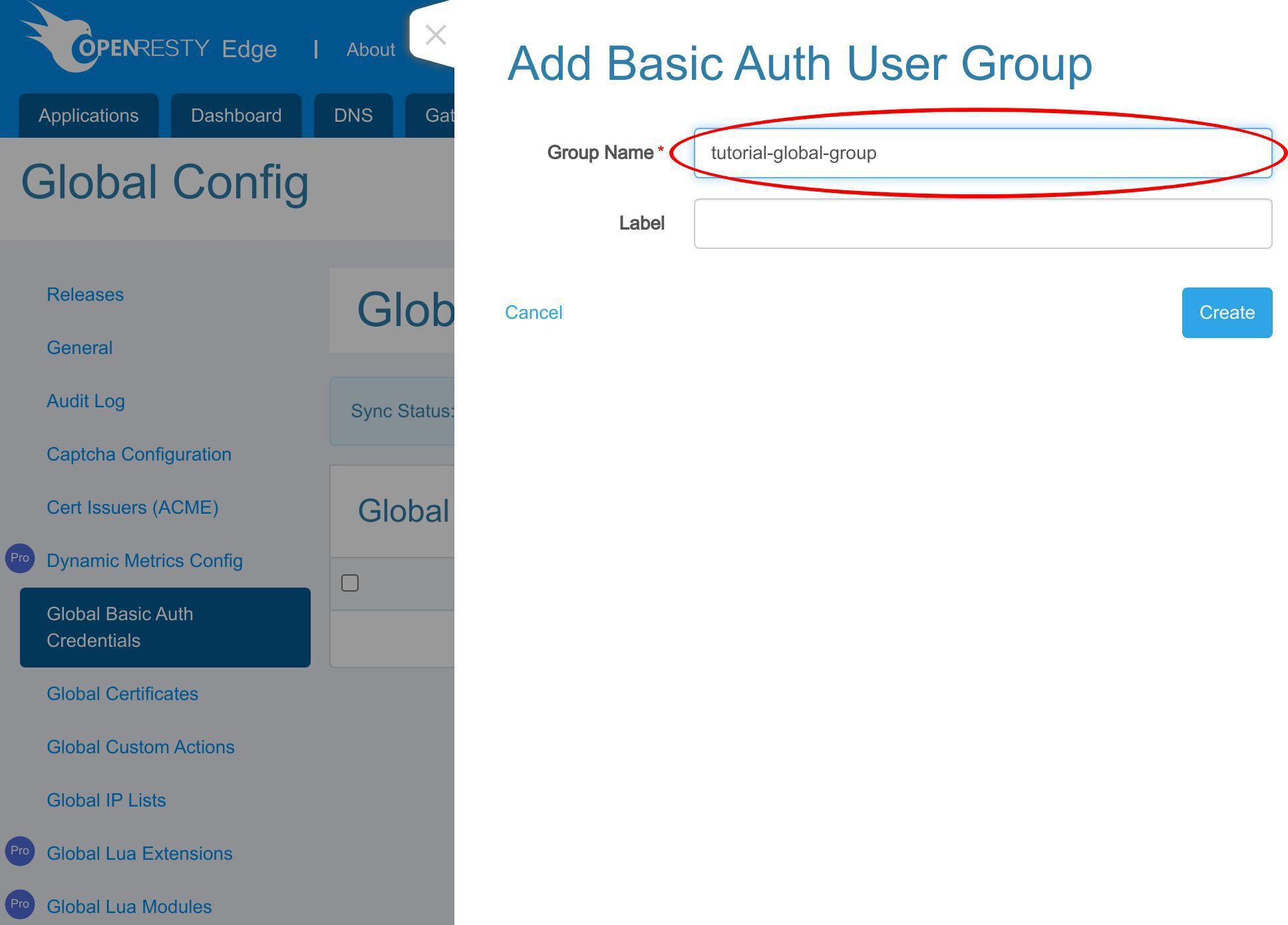
グローバル基本認証ユーザーグループの追加
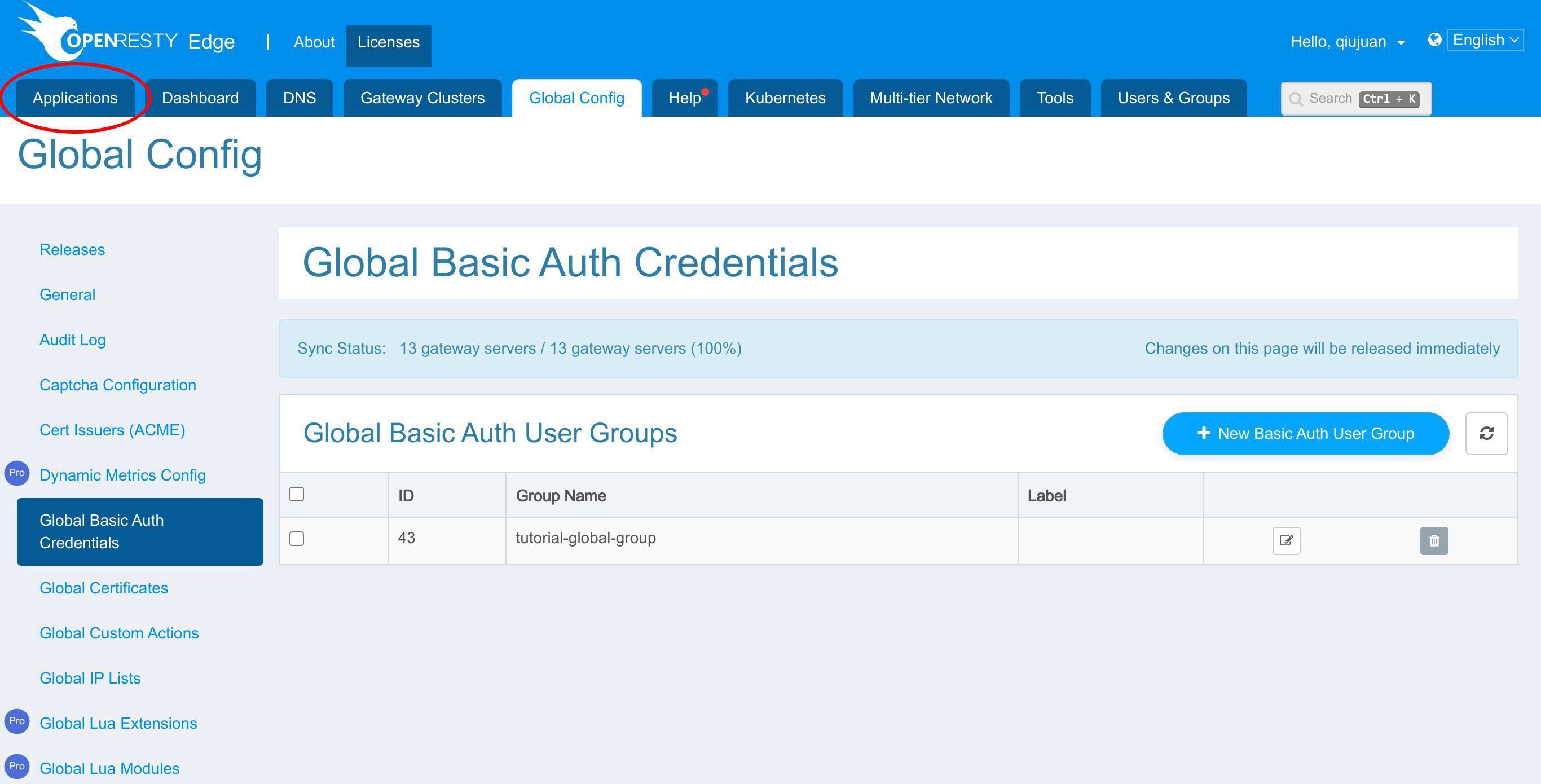
グローバル設定ページに移動します。
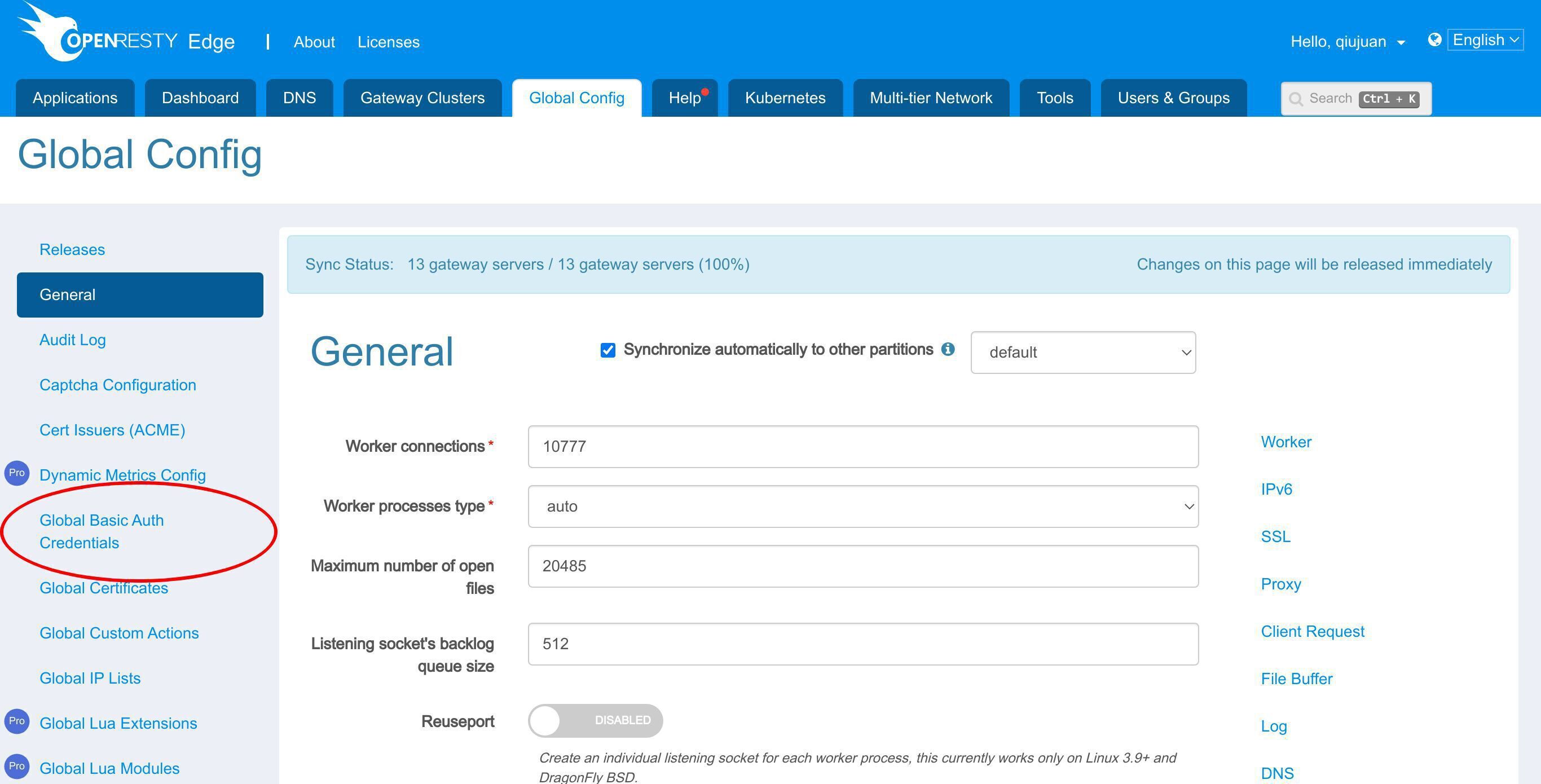
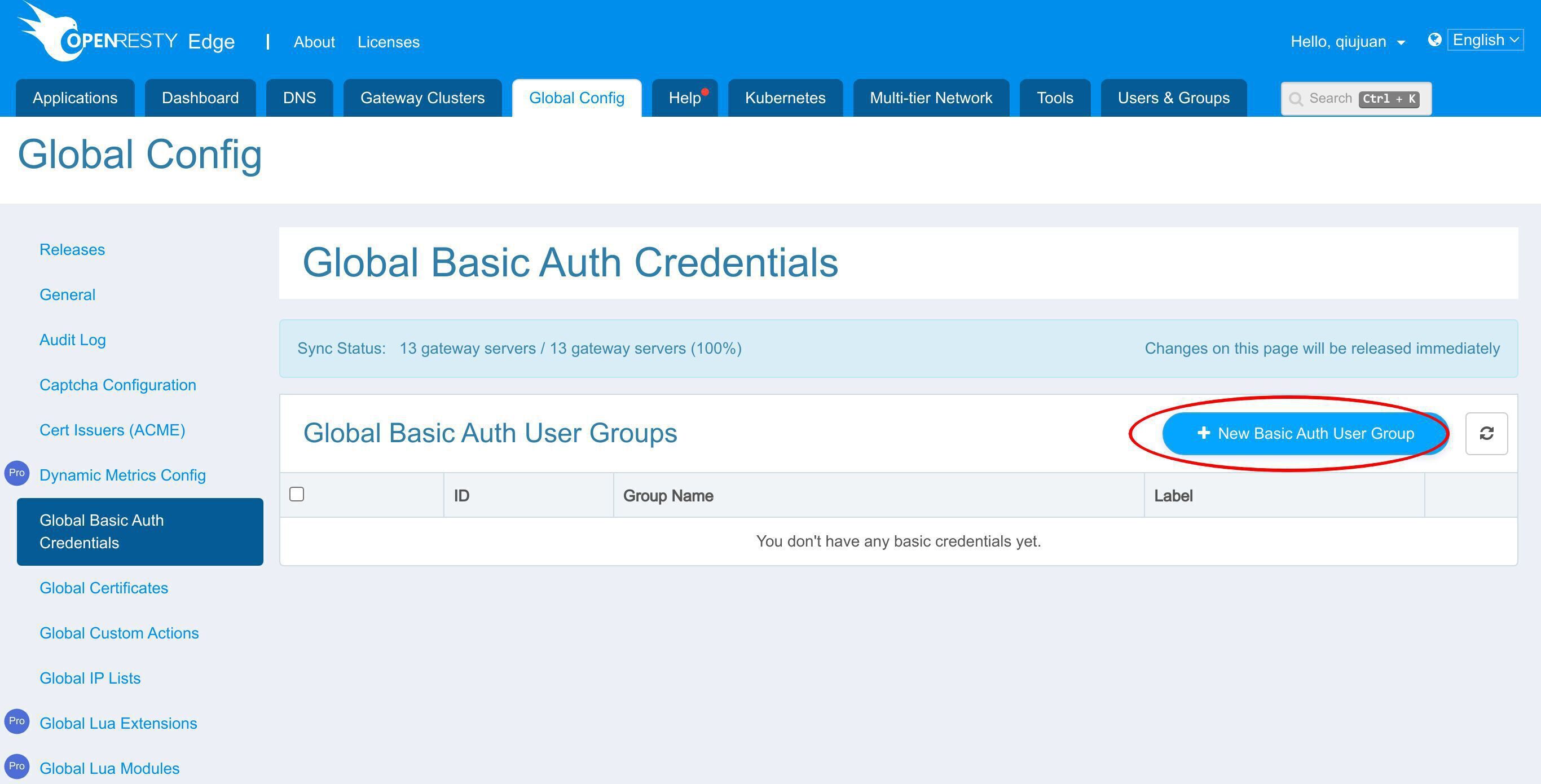
グローバル基本認証資格情報ページに進みます。
このボタンをクリックして、新しい基本認証ユーザーグループを追加します。
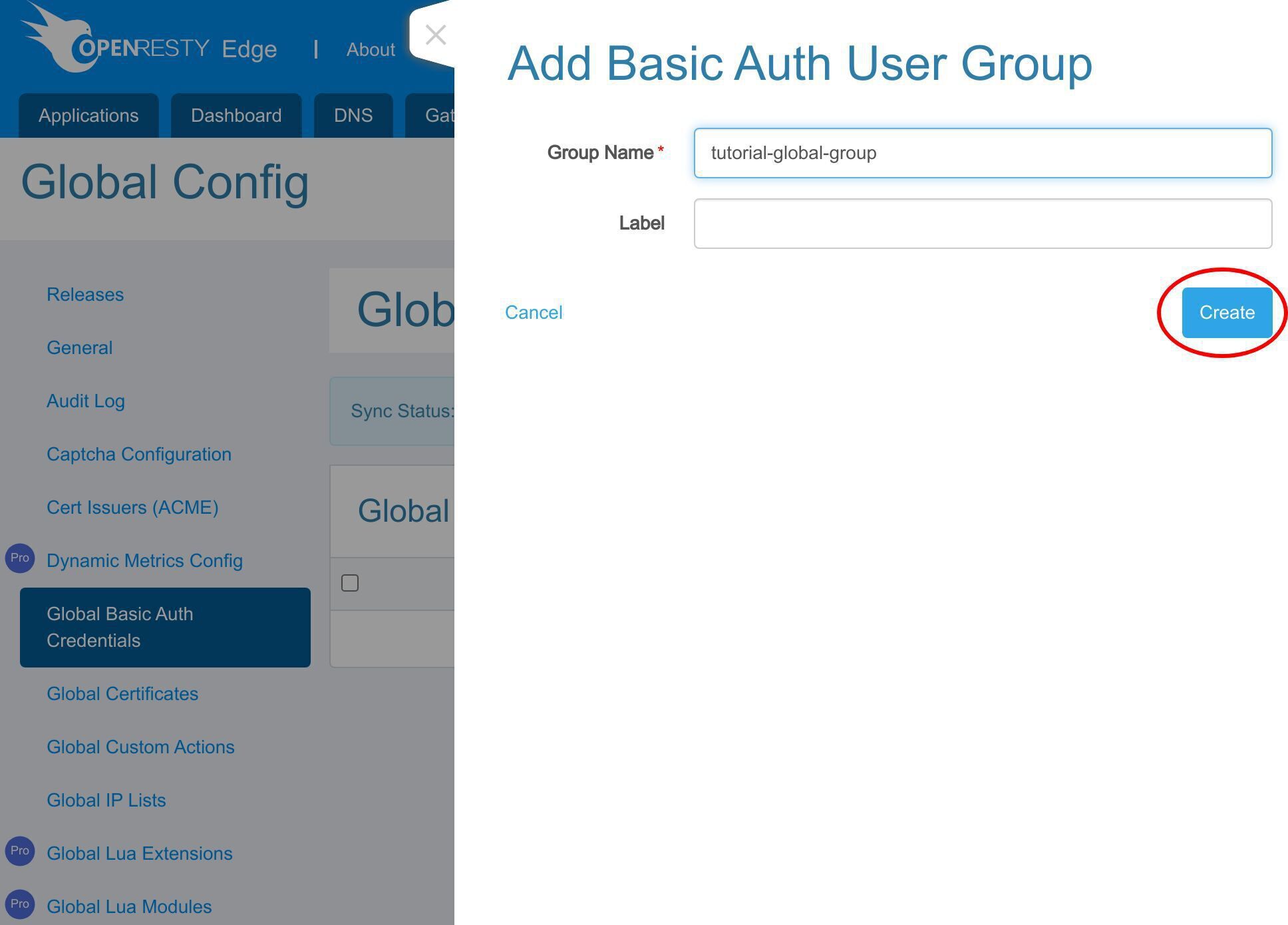
グループ名を入力します。
保存します。
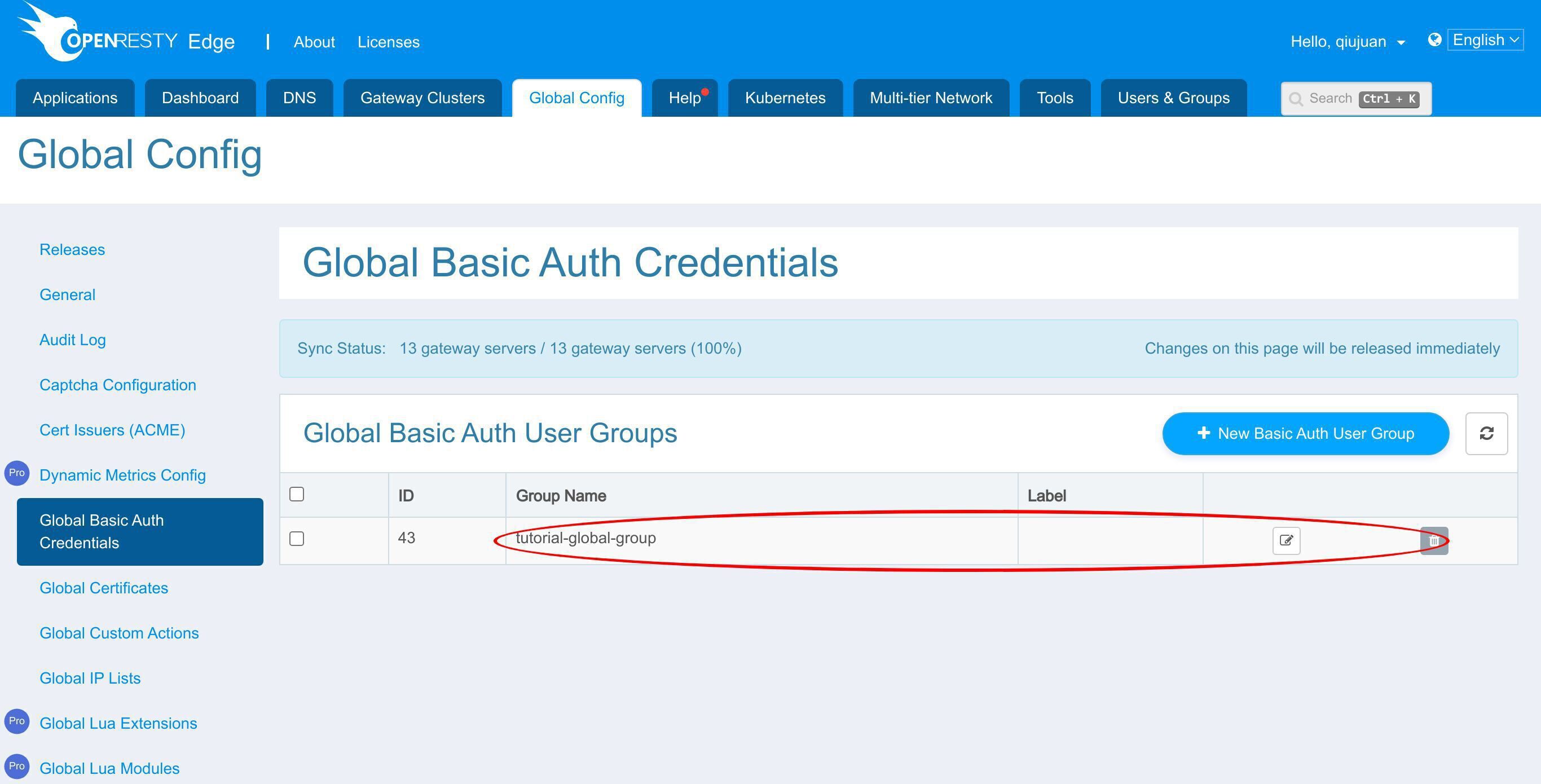
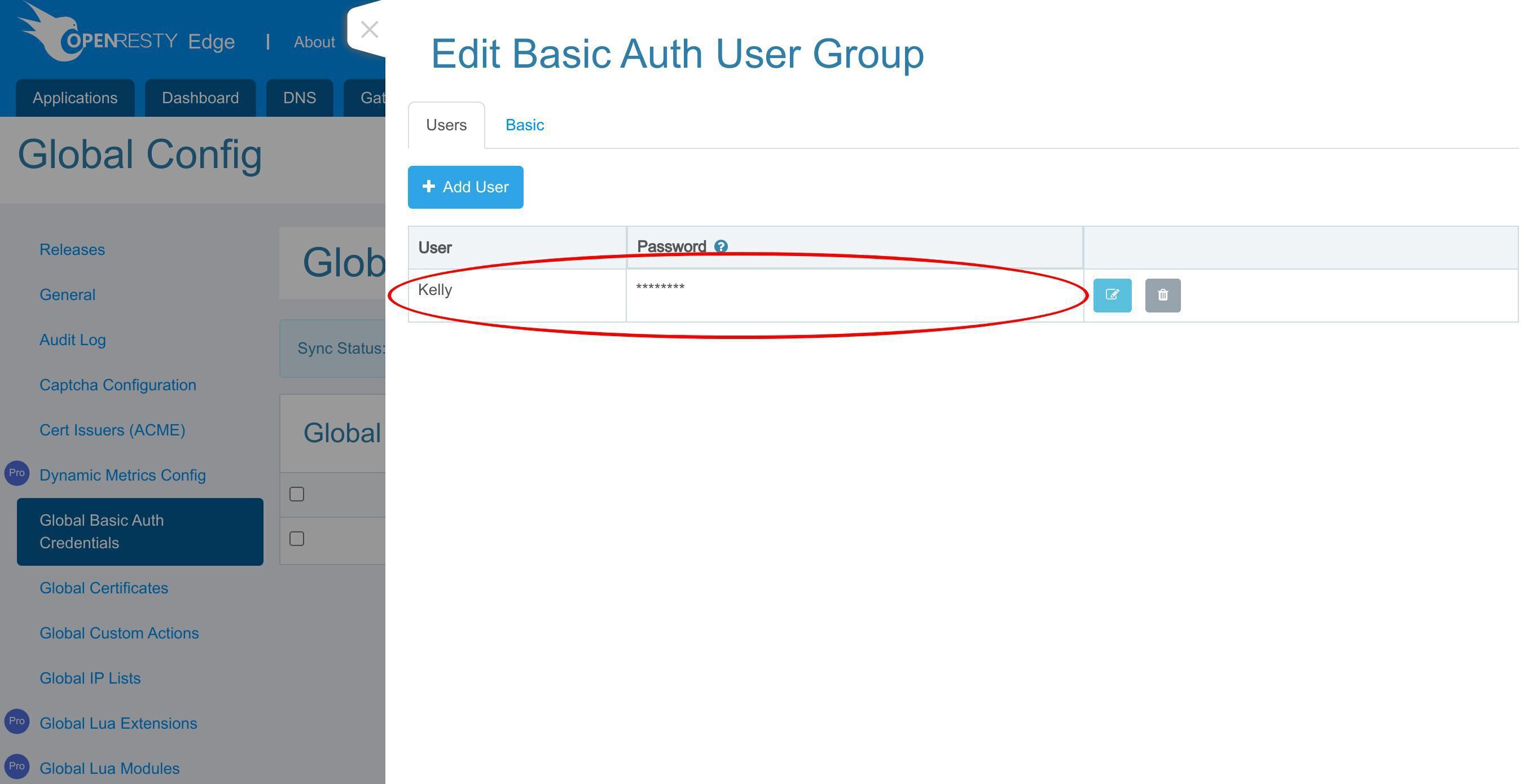
これで新しいグローバル基本認証ユーザーグループが作成されました。
編集ボタンをクリックして新しいユーザーを追加することもできます。
このボタンをクリックして新しいユーザーを追加します。
ユーザー名「Kelly」を入力します。
パスワードを入力します。
保存します。
アプリケーションへのグローバル基本認証の設定
「tutorial-global-group」ユーザーグループに新しいユーザーが追加されました。ゲートウェイアプリケーションにグローバル資格情報を設定する方法を見てみましょう。
このページを閉じます。
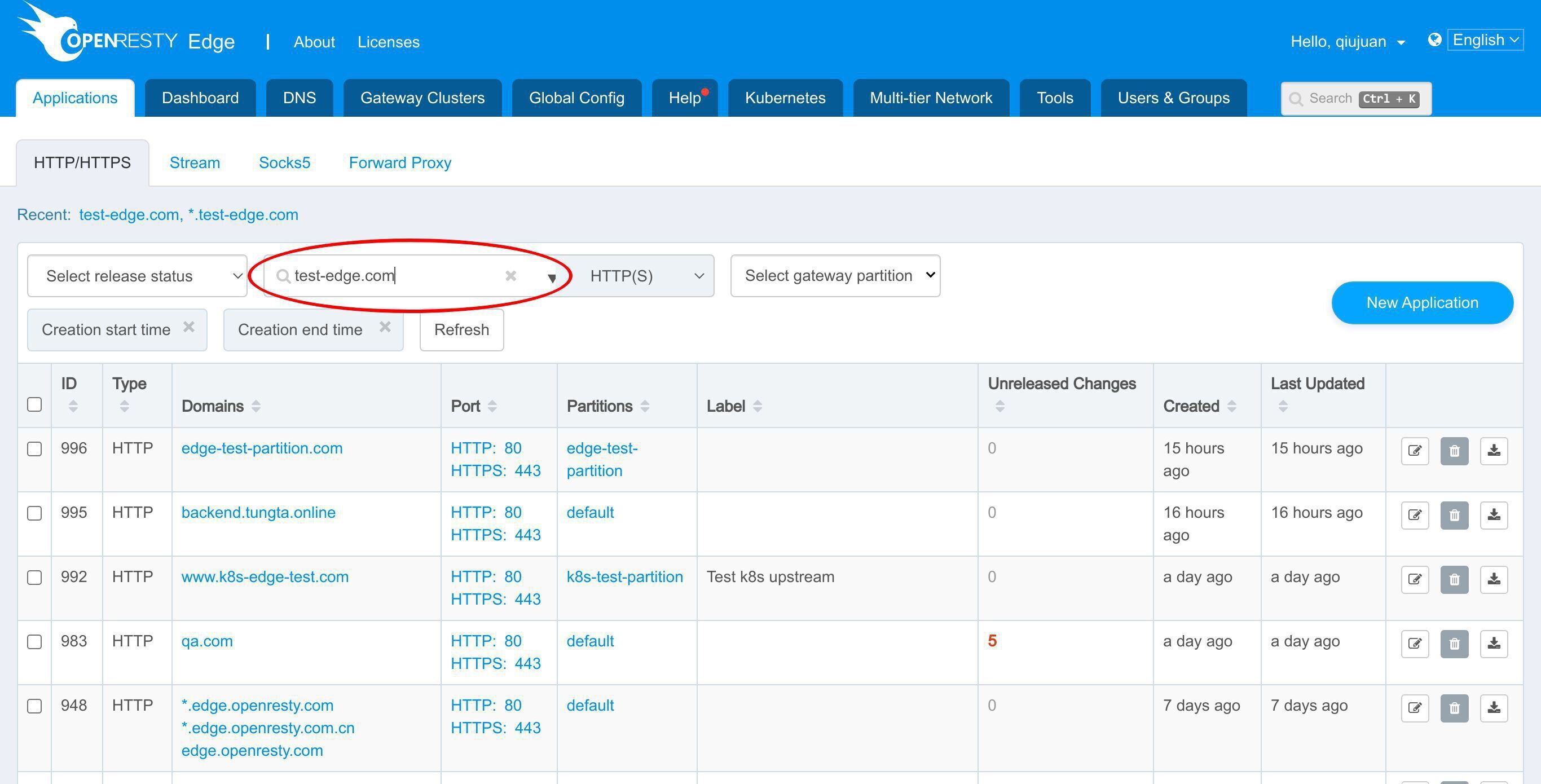
アプリケーション一覧ページに移動します。
test-edge.com ドメインを検索します。
このアプリケーションに入ります。
ページルールページに移動します。
このルールを編集します。
ドロップダウンリストをクリックして、ユーザーグループを切り替えます。
ここでグローバルユーザーグループを選択できます。この変更が保存および公開されると、そのグローバルユーザーグループ内のユーザー資格情報が使用されるようになります。
以上が本日お伝えする内容です。
OpenResty Edge について
OpenResty Edge は、マイクロサービスと分散トラフィックアーキテクチャ向けに設計された多機能ゲートウェイソフトウェアで、当社が独自に開発しました。トラフィック管理、プライベート CDN 構築、API ゲートウェイ、セキュリティ保護などの機能を統合し、現代のアプリケーションの構築、管理、保護を容易にします。OpenResty Edge は業界をリードする性能と拡張性を持ち、高並発・高負荷シナリオの厳しい要求を満たすことができます。K8s などのコンテナアプリケーショントラフィックのスケジューリングをサポートし、大量のドメイン名を管理できるため、大規模ウェブサイトや複雑なアプリケーションのニーズを容易に満たすことができます。
著者について
章亦春(Zhang Yichun)は、オープンソースの OpenResty® プロジェクトの創始者であり、OpenResty Inc. の CEO および創業者です。
章亦春(GitHub ID: agentzh)は中国江蘇省生まれで、現在は米国ベイエリアに在住しております。彼は中国における初期のオープンソース技術と文化の提唱者およびリーダーの一人であり、Cloudflare、Yahoo!、Alibaba など、国際的に有名なハイテク企業に勤務した経験があります。「エッジコンピューティング」、「動的トレーシング」、「機械プログラミング」 の先駆者であり、22 年以上のプログラミング経験と 16 年以上のオープンソース経験を持っております。世界中で 4000 万以上のドメイン名を持つユーザーを抱えるオープンソースプロジェクトのリーダーとして、彼は OpenResty® オープンソースプロジェクトをベースに、米国シリコンバレーの中心部にハイテク企業 OpenResty Inc. を設立いたしました。同社の主力製品である OpenResty XRay動的トレーシング技術を利用した非侵襲的な障害分析および排除ツール)と OpenResty Edge(マイクロサービスおよび分散トラフィックに最適化された多機能
翻訳
英文版の原文と日本語訳版(本文)をご用意しております。読者の皆様による他の言語への翻訳版も歓迎いたします。全文翻訳で省略がなければ、採用を検討させていただきます。心より感謝申し上げます!